This video demonstrates a way to hack a vending machine for change. First, you should press the top selection button four times, and then press the very last button three times. Then, hold the fourth button from the top and press the last button once more. If done correctly, t ...more
A vending machine is an invaluable yet totally frustrating piece of equipment. It's a godsend whenever your tummy's growling or you need an ice-cold drink on a hot summer day. But when something gets stuck inside or the machine flat-out malfunctions, it quickly becomes your ar ...more
In this video, we learn how to buy a can of soda. First, you want to find a soda machine that accepts dollar bills or change. After this, you want to find the soda that you want to purchase and see how much it costs. Next, you want to insert your money into the machine and pre ...more
This instructional video will show you how to get all of the change out of a vending machine! Who needs Coke or Pepsi when you can have coins? Then, you can get all of the soda you want out of that vending machine. Don't Miss: 9 Vending Machine Hacks for Free Drinks, Snacks, ...more
Craving candy but have no change? Then listen closely to this hack. This con how-to video shows you how to hack a candy machine by creating fake quarters. This hack trick should also work on parking meters. Never pay for candy or meters again. Watch this video tutorial on YouT ...more
In this Computers & Programming video tutorial you will learn how to change the default Windows Remote Desktop port. It is actually a registry hack. You can check the IP address of our machine by typing ipconfig into the cmd prompt. For hacking into a machine, you should have ...more
You'd like to treat your friend to a drink from the vending machine, but you only have enough cash for one soda. What do you do? Learn this new Coke vending machine hack! It only works on the newer style vending machines, which use a conveyer belt to deliver your drink to yo ...more
A vulnerability in the design of LiDAR components in driverless cars is far worse than anything we've seen yet outside of the CAN bus sphere — with a potentially deadly consequence if exploited. The hack is also going to be hard to fix, researchers Hocheol Shin, Dohyun Kim, Y ...more
A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge. The goal in this article is to acquire a target's .plist file which contains the ...more
In 2007, Nintendo introduced the world to motion control video games with the Wii. Microsoft and Sony built on Nintendo's phenomenal success and released their own motion control products for the XBox 360 and Playstation 3 late in 2010: the Kinect and the Move. The Move is bas ...more
The days of trundling hoops, hopscotch and painted wooden rocking horses are long since past. The latest trend in toys? Biofeedback. Electroencephalography. A decade into the 21st century, the toy market is awash in products that incorporate functional neural sensors. One suc ...more
Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself ...more
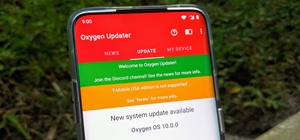
The OnePlus 7 Pro is definitely a beast on paper. With a specs page that ticks virtually every box and a price point that undercuts the competition by hundreds of dollars, it's hard to overlook this phone. But before you get too excited, know that OnePlus has repeatedly shown ...more
Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet. So no, there's no such ...more
People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people ar ...more
Whether it's a short road trip or an 18-hour flight, our phones are now essential travel companions. No longer do we need a GPS unit, maps, cameras, camcorders, or even boarding passes. However, not all phones are created equal in this regard. Some are more suited for travelin ...more
Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to ...more
Back in the Nexus days, Google's approach to hardware was very different from most OEMs. You could say OnePlus swooped in with a similar mantra a few years later, focusing on great hardware at an affordable price tag. There were compromises, of course, but even then, it result ...more
Defcon is the largest hacker conference with something for everyone, whether it be the talks, parties, villages, or any of the hundreds of events. In this guide, we'll take a holistic view at everything that goes into attending the con for the first time, from securing your el ...more
Update: The new Galaxy phones are now official! Check out all the details on the Galaxy S10 and S10+ or the Galaxy S10e. The Galaxy S9 didn't even hit shelves before fans were already musing about its followup. It's no secret Samsung's newest device, as impressive as it is, i ...more
Super Mario Brothers! No, wait... Super Meat Boy! Yep, that's right. Meat. As in "cube" steak. As in a square piece of beef with eyes and a shitty grin, who just happens to be in love with a band-aid. I have no idea why. And no matter how shocked you are to see your dinner on ...more
Most people have had the unfortunate experience of not having a washer and dryer at some point. Apartments in my area tend to charge at least one hundred dollars extra for the units with washer and dryer hookups, and even more if you want a unit with an actual washer and dryer ...more
Warnings i cant be held responsible for any illegal act done by anyone but myself and there are copyrights so notise that taken the trademarks or copyrights are strigtly prohibeted by law and will be punshied by law and i or my partners cant be held responsible for sudo camma ...more
How to get a vending machine to pay you for its goodies, instead of you paying for them. First off, find a older vending machine, and insert your dollar bill as you normally would. Once you have entered it, you can select which ever item you want. Then quickly, before the item ...more
This video explains to the viewer the advantages of replacing washing machine hoses. As well as, rather more importantly, explaining how to complete the process. According to the creator the rubber hoses that are standard to most washing machines are subjected to high pressure ...more
An iPhone-controlled drone unveiled at the recently held CES is expected to revolutionize the world of video gaming. Called the AR.Drone (AR stands for augmented reality), this new product will literally bring video games to the streets. Via Daily Mail, "The flying saucer-li ...more
Social engineering is described as the clever manipulation of the natural tendency of human trust. All of the passwords, locks, and encryption in the entire world are useless against a good social engineer who can charm or trick you into giving it up. But what once started as ...more
As a kid, my favorite thing to do at the Natural History museum was a midday stop, when my family strolled past an antiquated looking vending machine in the museum's musty basement. The Mold-A-Rama machine was oddly shaped, George Jetson-esque, and spewed out made-to-order, br ...more
Have you ever seen one of those Snapple machines with the lever coin return? I will show you how to get free drinks or snacks out of this type of machine. Don't Miss: 9 Vending Machine Hacks for Free Drinks, Snacks, & More Take your dollar and put it in the machine. Have a f ...more
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to edit Supe ...more
Their were many pedestrians in the scene as,they seen firefighters struggling with the horrifying disaster and they couldn't do much only continue to stare as bodies continued to drop.. Firefighters arrived at the Triangle Shirt Waist Company Fire minutes after the alarm was ...more
Penny pincher? A true believer in "waste not want not"? Then listen up—here's a quick tip that will save you some spare change. Scenario 1: We're all guilty of negligently abandoning a freshly bought sponge in a pot full of dirty dishes and food-littered water. Let that bad b ...more
A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vul ...more
You'll see a lot of Linux action going down here at Null Byte. We use Linux for hacking-related stuff because it provides a more relaxed programming environment, making it easy to write exploits and tools. Linux has many features Windows is lacking, such as full control over t ...more
The United States is a hierarchical country where the weak ones are at the bottom and the powerful ones are at the top. Garment workers are at the bottom of the list although they are the most important. Without them there would be no fashion industry. They sew and cut the gar ...more
In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack. Before we start hacking, let's familiarize ours ...more
In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts. In the last Hacker Fundamentals, we talked about the OSI model as well as a little on TCP/IP and the protocols that make ...more
Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use y ...more
If you're a frequenter of Null Byte, I bet you have at least some interest in information security. Furthermore, you have a hobby that if applied in certain ways, will get you arrested. I've received quite a few messages from the community here about federal cybercrime law and ...more
Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called ...more
INTRODUCTION Hello dear null_byters here we go again with our third part of this serie. in this third part of our series I'd like to do a demonstration or continuation on fuzzing, but I think I should leave for later because the next tutorials about fuzzing will require from ...more
This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the ser ...more
In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as ...more
Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, ...more
Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills. Wh ...more
Google, the company that rules the internet, is now testing a method to leverage its machine learning with its ubiquitous presence on mobile devices. The new model they're employing is called Federated Learning, and it hopes to apply artificial intelligence to Google's service ...more
In the first part of my containers series, we learned how to install Docker on our local machine, pull down "hello-world" and Ubuntu containers, SSH into containers, and install software when in a container. Now, we're going to work on building, customizing, and storing our re ...more
Check out this video from CouponCodesHero on hacking a vending machine in no time. All you need is a little packing tape and some paper money, then fool the machine to either get free stuff, or use the "change" to get free money! Video: .
QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into ...more
It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to ...more
If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module. This tool is useful if you're managing a large num ...more
Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exi ...more
A group ironically called the "Guardians of Peace" hacked into Sony Pictures' computer systems and released a mountain of internal information such as medical records, leaked scripts, work complaints, and even celebrity aliases. Why did this happen? Sure, a lot of well-though ...more
Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc. Maybe you forgot or lost the password to your Windows Admin account, this guide wi ...more
Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many roo ...more
So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - byp ...more
Kali Linux has come a long way since its BackTrack days, and it's still widely considered the ultimate Linux distribution for penetration testing. The system has undergone quite the transformation since its old days and includes an updated look, improved performance, and some ...more
The Pixel 3 XL versus Galaxy Note 9. Stock Android versus Samsung Experience. When I began this comparison, I thought the Pixel 3 XL would be unfairly outmatched. But after looking at the specs side-by-side, you'll see a different picture. This year, Google delivered a worthy ...more
Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the ...more
Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the ...more