Your IP (Internet Protocol) address is your unique ID on the internet. It's synonymous with your home address. Anyone in the world can contact your computer through its IP address, and send a retrieve information with it. I'm sure at one time or another you've heard that hack ...more
XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection betwe ...more
People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people ar ...more
The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac ...more
See a basic netbios hack, showing what happenes to ppl who leave files and folders shared over the Internet. Hack computers with open shares. Click through to watch this video on tricklife.com
If you're living or staying out in the middle of nowhere or a rural area outside of a big city or town — where there are no reliable cable, fiber, or wireless networks available — how can you get an internet connection? There are several possibilities, but they all come with t ...more
Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the b ...more
The USB Rubber Ducky is a well-known hacking device in the cybersecurity industry, but it needs to be preprogrammed before it can be used. That means it's not easy to issue commands to a target computer since you can't interact with it from afar after plugging it in. And if yo ...more
If browsing speed is important to you—and it should be—you'll probably be interested to know that there are ten simple flag modifications you can make in Google Chrome in order to achieve the fastest browsing speed possible. A few months ago, Dallas covered six ways to speed ...more
Formerly ipchains, iptables is a script-based firewall that's included with both Mac and Linux operating systems. In my opinion, it's the best firewall in existence. The only downfall is that it's complicated for some people to use due to its script-based nature. But this shou ...more
Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can l ...more
After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even ...more
The $35 Raspberry Pi is an amazingly useful single-board computer (SBC) with a good balance of price, performance, and connectivity options. But for some projects, it just isn't enough. Whether you need more computing power, a smaller size, or better machine-learning capabilit ...more
Need internet access and you don't have a login? Hack into a private or controlled network with this tutorial. Thefixed.org also shows you how to build a smoke bomb!
This video tutorial demonstrates a mouse-hacking simple prank sure to annoy any friend or colleague. To replicate this hack, you'll need a mouse and a musical key chain. The steps are roughly as follows: First, open up the mouse. Looking inside, find and remove the scroll whee ...more
If you ever wondered how you could make your internet web browsing faster, then this video will give you a crucial tip. The loading speed of web pages and web sites is greatly influenced by the type of web browser you are using. The narrator in this video suggests that you sea ...more
This is hardcore, serious hacking at its best. So it goes without saying that you probably shouldn't be attempting this computer hack unless you've successfully shut down your friend's computer at school using Command Prompt and sent out a fake virus to loved ones. This tutor ...more
This video provides information on how a hacker can find an vulnerability on a remote computer and exploit it to gain remote access. Also, the video shows how a hacker can raise their privileges on the remote machine to administrator. Hack a computer for remote access. Click t ...more
This video shows how to hack the computer password for Vista. We can change the computer password without knowing the actual password. First go to Start menu. Type in the Search "cmd". Then right click on that folder and run as administrator. Then we get a pop up. Type in thei ...more
This tutorial is aimed at using Cheat Engine to cheat at games that are not online, such as Need for Speed (demonstrated in this video). Change your stats, add extra inventory items or increase your amount of money or experience points!
Tinkernut demonstrates how to crack a wifi connection, as well as how to better secure your own personal connection. Also included in the video gallery is Tinkernut's previous tutorial on the same subject. LifeHacker posted a great detailed text guide to accompany the second ...more
Your BIOS, or Basic Input Output System, is the firmware on your motherboard responsible for initializing your computer's hardware when it is first powered on. It probes for video adapters, RAM, the whole works. The BIOS provides a small library of basic input/output functions ...more
Want to give yourself extra points or resources in the online game Wild Ones? All your friends will be asking you how you passed them up so quickly! Make sure you have the most recent version of Cheat Engine downloaded, first!
In this clip, you'll learn how to use VNC to remotely control an Apple desktop or laptop computer over the web. For more information, including a complete demonstration, and detailed, step-by-step instructions, as well as to get started using this trick yourself, take a look.
The new Windows 7 layout is streamlined for the occasional user to the head of human relations for Microsoft. Wall papers, system sounds, and resolution settings were covered in the instructional how to video. The evaluation specialist was knowledgeable and articulate. Transit ...more
Xeni visits the offices of the Electronic Frontier Foundation and speaks with Jake Appelbaum and Bill Paul, two of the authors of a security research paper that shows how your computer's memory can be tricked into revealing data you thought was safely encrypted, and out of the ...more
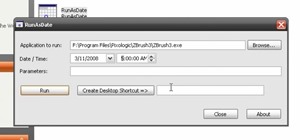
Want to be able to hack into a computer remotely? This method takes a little extra time and cunning to set up, since you will need to first install the ShowMyPc program on your target computer. Once you have installed this program, however, you will be able to go to the websit ...more
Play remotely with all your friends, stream videos and music from the Internet or even check your Facebook and email - all with your PSP. The PSP has Internet capability, but not every network will be available to you at all times. Here is how you can hack any wifi connection ...more
This is how to hack a computer for educational purposes. First you need its IP address, radmin viewer 3.3 or later, and an open port scanner. Okay so first you need the IP and scan the IP address of the computer. Now find what open port it has. Ok then open up radmin viewer an ...more
Bring harmony to your digital world by getting your iPhone and your computer to work together. Watch this video to get the scoop on RemoteMouse from Cydia, a hack that will turn your iPhone into a remote control for your computer.
Want to watch movies from your computer on a TV? What about just using your television as another monitor? Find out how to connect you TV to your computer and convert it into a monitor.
You can hack into nearly any Facebook or Flash based game on the Internet - no cheat codes or special strategies needed. All you really need is the free game hack program Cheat Engine, and a compatible browser like Firefox.
See how to hack a wireless CCTV (closed circuit television) camera to show your Windows or Linux PC desktop on your 42-inch plasma television. This is a homemade hack that's easy with good quality picture. Doing this mod can save you money, unless you don't have a CCTV camera ...more
Having the Internet on your phone is definitely handy. You can look up anything at anytime, and connect with friends in so many more ways. In this tutorial, learn how to use your PC and your Bluetooth enabled mobile phone to get free Internet on your cell phone and avoid buyi ...more
Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes ...more
Since most devices these days are mobile and wireless, a lot of people have a bunch of old hardware from a decade or two ago sitting around unused, just wasting away in dusty boxes. Look familiar? If you have an old mouse (or several) lying around, you can turn it into a wire ...more
What if you could have a secret hard drive connected to your computer that only you could activate? You can! Samimy shows you how to hack a remote controlled toy car and make a super secret hard disk drive in your computer, accessed via a secret activation key. This hidden eme ...more
In this clip, you'll learn how to extract serial data from the $80 Mattel Mindflex or Star Wars Force Trainer. For more information, including detailed, step-by-step instructions, and to get started creating your own working EEG/BCI, watch this very-neat hacker's how-to.
Welcome back, my budding hackers! Recently, I showed you how you could exploit the widely disseminated OpenSSL vulnerability that has to become known as "Heartbleed". Although the world has known about this vulnerability for over a month now, it will likely take many more mon ...more
Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue. There are a multitude ...more
Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to ge ...more
Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, a ...more
Welcome back, my newbie hackers! We've already saved the world from nuclear annihilation and covered our tracks afterwards, but the world is still threatened by a malicious, megalomaniacal dictator with missiles and nuclear weapons. We need to keep a close eye on him, so in ...more
Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"! So, by popular request, in this guide I'll show you how to install a key ...more
In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks. As web server and OS’s have become hardened and living behind significant perimeter defenses, hackers hav ...more
Welcome back, my tenderfoot hackers! So many of you responded positively to my post about using the keylogger, as well as my post regarding turning on the webcam, that I decided that you might enjoy another similar hack. In this article, we will enable the audio recording cap ...more
Warnings this only for educational use i dont take responsiblety for any use of this article if you want to use this for use at a school plz contact me at sebzy4@hotmail.com hi im a computer enginer/programmer (NOT games) but i am good at hacking and i want to help. notise th ...more
No matter your reason, if you want to hide what's on your computer screen from prying eyes, there are plenty of ways to do it. You can get a privacy filter, install a panic button for your browser, or just develop super fast reflexes. But all it takes is the right angle or a t ...more
Have a PC but hate Windows? Maybe you've just heard a ton about the new Mountain Lion OS X and want to see if it lives up to expectations. Either way, you can install Mountain Lion on your Intel-based PC in a few easy steps. All you need is a copy of the OS X and an 8 GB USB f ...more
Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use ...more
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started. OVERVIEW: As you'll get further into the hacking community, and learn more about how it's all put together, you'll also realize very quick ...more
Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, w ...more
Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself ...more
Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you ...more
Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc. Any time someone's computer seems to act ...more
The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centere ...more
There are a lot of things on your computer that can reveal information about you when you are surfing the Internet. If you are like me, then you will do anything to maintain your privacy and prevent those little leaks of information from happening. Here's a list of a few of th ...more
Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend. ...more
The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB ...more
There is a vast amount of knowledge out there on computers! In fact, it is so vast that no single person could ever possibly ever learn everything there is to learn about hacking or computers in general. People usually specialize in a certain field: cryptography, computer secu ...more