Considering how often many of us fly on commercial airlines, the idea that a hacker could somehow interfere with the plane is a very scary thought. It doesn't help to learn that at Defcon, a researcher found that the Automatic Dependent Surveillance Broadcast (ADS-B), transmis ...more
This instructional video shows how change traffic lights from red to green, using science, and without actually having to know anything about magnetic fields or properties! Save gas, time, and frustration in your car and during your commute! Works great! See the test results! ...more
Games are always more fun when you have someone to play them with, but if you're not always logged in to your Xbox LIVE account, how do you know when your friends are online? You can always log in and check, but where's the fun in that when you can hack together a traffic ligh ...more
Scenario: it's late at night, the roads are completely empty and you are stuck at the longest light ever. Solution: don't run a red- change it to green yourself. Avoid a ticket, save yourself some time (and perhaps a little gas). Many of you may have already seen Kipkay's ins ...more
These are a series of clips to show you how to deal with the different situations when turning right at traffic lights. In the U.S. or countries that drive on the right, these principles will apply to left hand turns. Deal with right turns at traffic lights - UK. Click through ...more
This is a video for children to learn about the traffic light for pedestrians use. It is an interaction game where the children can push the proper light to answer questions pertaining to the traffic light. Teach children about traffic lights. Click through to watch this video ...more
General Electric isn't known for their Christmas lights, but maybe they should be, because their GE Color Effects are pretty awesome. Especially the LED Color Effects G-35 String sets. And especially when someone named Darco hacks them. Darco, whose real name is Robert Sun Qu ...more
Nobody likes having to stand at the crosswalk waiting for the light to change so you can cross. This seems to happen more times then not these days. A way has been discovered to eliminate this problem with ease. The first thing you are going to want to do is go to the pole tha ...more
Christmas is the time to splurge— not just with presents and food— we're talking decorations. It's that time of year when verdurous fir trees take up half of your living room, when waving elf figurines silhouette your front windows, when Rudolph flies from the rooftops, Santa ...more
Normally, when standing outside your local regional airport, you'd need a special radio or scanner to pick up the transmissions coming from that Air Traffic Control tower. Well, not anymore. Kip Kay from Make Magazine will show you how to take an old vintage AM/FM transistor ...more
Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue. There are a multitude ...more
Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful. Many novice hackers focus way too much energy on cracking passwords (which should be a last resort unless you have spec ...more
Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targe ...more
Record stealthily, in the dark. This hack is simple and will turn any LED flashlight into an infrared night vision light you can use with any video camera. Infrared light is invisible to the human eye, but it will illuminate any area you are shooting. IR radiation is electrom ...more
Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of onlin ...more
It's a given that if you're driving, you or someone you know has Waze as a go-to on their smartphone. The Google-owned crowdsourced navigation app is one of the best for avoiding traffic, roadblocks, and even cops. But a new academic study and report from Fusion suggest that ...more
If you hate matching images, typing letters and numbers, solving math problems, and sliding puzzle pieces for CAPTCHA human verification, you'll love Apple's newest privacy feature for apps and websites. Generally, CAPTCHAs can be a massive nightmare on mobile devices. They a ...more
Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem. ...more
In this clip, learn how to make a fast, cheap and super easy mount for your your bicycle to display safety lights. Wearing bike lights at night will help you stay safe in the dark and if you want to avoid the cost of getting lights custom fitted, this hack is perfect for you. ...more
Want to stop wasting energy charging your USB devices? Transform some cheap solar-powered garden lights into your very own solar USB charger. For step-by-step instructions on replicating this hack yourself, watch this video tutorial. Just watch to see how to build your own sol ...more
XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection betwe ...more
They are after you from all over the globe. Looking for ways to exploit you. Ways to hurt you. Not political terrorists, but rather "info terrorists." Each month thousands of websites get hacked into and have hidden links inserted into the pages by people wanting their spam si ...more
This clip shows a large double roundabout with traffic lights and how to negotiate the lights as you turn right and then straight. Some keys are: keep your speed down, don't speed up to 'beat the lights', and be ready to stop, especially if the lights have been green for some ...more
Panasonic announced an interesting concept today that could advance millimeter-wave radar technology for automotive safety uses in detecting pedestrians, bicyclists, and other motorists. Regardless of how attentive one person is while driving, it's impossible to see everythin ...more
Sometimes it can be annoying to have to put in a cd in the dark. No worries, this tutorial video will help you to illuminate that CD port with a few LED lights. This totally cool hack is easy to do and won't take long and the funky effect is totally worth it.
Haven't you ever wanted to live in a futuristic home? I think that homes are headed towards an era where they will be controlled by our computers and smartphones. No longer will you have to find your keys to unlock your door, or wait until you get home to monitor your security ...more
Kip "Kipkay" Kedersha is known for his intriguing and clever how-to and prank videos, even when he teams up with MAKE Magazine. He will show you how to tweak, hack, mod, and bend any technology to your hacking needs. No electronic device, gadget, or household item can stand th ...more
Accidents are the worst. They're costly, time consuming and an all around pain in the butt. Rear-end collisions are among the most common types of accidents on the road. Take these simple precautions to avoid a rear-end collision. You Will Need: • A well-maintained vehicle ...more
In some places, it's illegal to ride your bike at night without lights or reflectors, so if you plan on going for a joyride on your street bike, then you need to be prepared to share the road with vehicles and be seen. Appropriate gear and lighting are essential for safety whe ...more
As you may have seen in your city or town, red light cameras are on the rise in the United States. In many instances in my area, these cameras have sprung up seemingly out of no-where, and mostly without any reason. Over use of these systems can make privacy (even on the road) ...more
Halloween just isn't Halloween without Jack O'Lanterns. Below, anything and everything you need to know on the art of pumpkin carving. 1. Prepare a Pumpkin for Carving Serious Eats' video demonstration is for true novices: "This video is for you unlucky souls who never got t ...more
Cyclists and unknowing vehicle participants "collaborated" on a public guerilla graffiti art piece in Berlin this last week. Abitare reports: "A group of cyclists dumped 13 gallons of paint on the road at Berlin’s busy Rosenthaler Platz, creating a series of colorful lines a ...more
Hack a car photo to be a really awesome decorative object for your home or office at a very low cost. It's also really fun to make! All it takes is a few LED lights and a 9V battery.
It's the most wonderful time of the year. Christmas lights are up, stores are crowded, tacky knit sweaters are making an appearance, and there's the constant smell of something delicious baking in the oven. In this week's Phone Snap Challenge, spread some holiday cheer by show ...more
Speeding tickets are one of the worst things a driver fears on the highway, aside from wrecking, of course. But you can get home safe without getting a ticket. You just need to keep your vehicle off the radar by following these stealthy driving techniques. You Will Need * A w ...more
At first, it seemed like a clever art installation housed on the web, but now we're not so sure... the Newstweek hack may indeed be legit. Earlier this year, Newstweek claimed to have developed a way to hack into webpages on a local Wi-Fi network using a homemade device that ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. Thanks to all of our active moderators and ...more
Black lights come in all shapes and sizes, and they're useful in a variety of ways. They can help you spot fake currency, urine stains, interesting rocks, and deadly scorpions, and they can even help you view cool fluorescent artwork. Most black lights work using a filter or ...more
In the driverless race, technological advances can sometimes just add more tension to an already heated competition, if Waymo suing Uber over their allegedly stolen LiDAR technology is any indication. Now, Sony is offering a new camera sensor, one that should help self-driving ...more
Waymo has done a lot of things over the course of their driverless journey, but their solution to little birdies pooping all over a self-driving car's LiDAR system is definitely our favorite. The sensors on Waymo's autonomous vehicles, as well as any other self-driving car br ...more
Tesla says the new version of Autopilot is now as good as the previous one, after having completed over-the-air updates of the driverless software during the past few days. Model S and Model X Tesla models the electric car firm began to make October 16 last year lacked certai ...more
The US driverless market has become a competitive – and crowded – arena, with big names like Google, Apple, Uber, and even Intel intent on leading the pack. Not to be outdone, the EU is also getting in on the automated car action with self-driving fleets launching in both the ...more
Stratford may soon become Canada's answer to Silicon Valley as the driverless car industry arrives. Potentially changing the character of the Ontario town known for hosting the Stratford Festival, a celebration of all things Shakespearean and stage-related. Last Thursday, the ...more
LEDs have slowly become the standard for DIY lighting projects because they consume less power and last way longer than regular light bulbs do. Light-emitting diodes have no filament, meaning they generate their light solely by the movement of electrons in a semiconductor mate ...more
The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server. Shodan has been called the "hacker's search engine" because it's literally a searchable ...more
Cruise Automation, the driverless car startup General Motors (GM) bought for $1 billion in 2016, is readying a formidable fleet of robo-taxis for rollout in cities throughout the US. But when it comes to details about how the company plans to realize these lofty goals, it's be ...more
The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized ...more
Video: Add LED lights to avoid speed detection while driving.
Welcome back, my hacker novitiates! Recently, I demonstrated a hack where you could redirect traffic intended for one site, such as bankofamerica.com, to your fake website. Of course, to really make this work, you would need to make a replica of the site you were spoofing, or ...more
Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic. The first a ...more
Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA d ...more
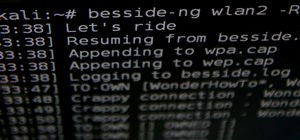
Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords t ...more
Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the ...more
Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on h ...more
It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time. Both Facebook and Gmail ...more
Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend. ...more
So, according to Sprout Social, mentioning an Instagram handle in the caption of your posts increases audience engagement by up to 56 percent. If true, that's pretty impressive. (Like anything with Instagram, what works today might not work tomorrow, so you have to stay vigil ...more
Welcome back, my hacker novitiates! Now, and more so in the future, wars will be fought hacker v. hacker. The number of soldiers, guns, tanks, and ships will be less important in your success in warfare than the number of well-trained hackers you have. Every nation and every ...more
Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, ...more
Want to take advantage of your neighbor's super fast Wi-Fi connection? If they're smart, they probably have it password protected (otherwise you wouldn't be reading this, would you?). But if you have an Android phone, you can get back at them for always parking in your spot an ...more