You've probably heard about Rep. Greg Walden (R-WA) tweeting in Morse code back in December. .-- .. .-.. .-.. / -.-. .... .- .. .-. / -.-. --- -- -- / .- -. -.. / - . -.-. .... / ... ..- -... / --... ...-- ... / .-- --... . --.- .. That was posted on his Twitter account, and ...more
Keeping secrets out of the wrong hands warrants desperate measures—or maybe just sensical. If you have a secret, the best way to protect it is with a code—and the best way to transfer that secret message is via an electronic telegraph system. This video will show you how to ma ...more
Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. For last week's Workshop, we decided to attempt to communicate long distance without the use of the chat bar. To accomplish this, we built an elementary redstone pulser that would a ...more
There's a feature in the Gboard keyboard that enables people who cannot talk, type, or swipe normally to still have a way to communicate in the digital age on their smartphones. While it's mainly an accessibility feature for those who actually need it, it's a good way for anyo ...more
What happens when you add a few wires and a microcontroller to your door buzzer? You can let yourself into your building from the outside!
JamesKesn teaches you how to hack a vending machine. You must use a very specific machine and an exact combination of button presses. For this it is: far left Pepsi, near right Mountain Dew, near left Pepsi, far right Mountain Dew. Then far left Pepsi, near right Mountain Dew. ...more
At the end of last year Google released Chromium OS, the source code to their soon-to-be-released operating system Google Chrome OS. This has allowed millions of people to preview the new OS and make suggestions. Do you want in on that action? This video will show you how to i ...more
Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educate ...more
You should already have the JDK installed on your computer, and you should already have optimized your computer's settings. See How to install the Java Development Kit to start programming to do that if you haven't already. After that, you can start working on your very first ...more
To go Open Source or go proprietary? There is a common conception that open-source is unsafe and insecure and therefore companies should rather go for proprietary solutions. They think that because software is termed "open-source", that the world can see the vulnerabilities of ...more
WeaponCollector teaches viewers how to make a mini survival kit using an Altoid's tin. You can get an S.A.S. guide for exact instructions and further information on what you will need in an survival kit. First, you should make sure you have rubber bands around your tin to hold ...more
Get into a menu in the Coke machine. This video offers the code for hacking into a Coke machine menu. This may not work for every machine, but should work for some.
Take a look at this instructional vidkeo and learn how to make your own computer numerical control (CNC) machine out of two old CD drives. CNC machines serve as controllers for a number of devices such as machine tools by reading G Code instructions. With a own CNC machine, yo ...more
Introduction I am currently starting to learn the Python programming language, programming languages make up all the programs that we use, that is enough for it to fascinate me if it isn't for you then maybe start reading this and you will quickly see how powerful it is. This ...more
"There are 10 types of people in the world," the old joke goes, "those who understand binary, and those who don't." In this tutorial, you'll learn how to read and write binary code. With this neat tutorial, you'll join the former group. Make sense of the 1s and 0s of binary co ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. More amazing community contributions this w ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. This week has been an exciting one. The com ...more
Here's a delicious Byte of information for you. A proof of concept program on Linux was coded to exploit a known bug in how the Linux Kernel (versions 2.6.39+) handles permissions for the /proc/pid/mem directory. /proc/pid/mem is an interface for reading and writing directly t ...more
Looking to install a physics engine for Flex or Papervision? In this video lesson, Mike Lively of Northern Kentucky University demonstrates how to install the Wow Physics Engine into Flex 3 for use with Papervision3D. For more, and to get started installing the WOW-Engine on y ...more
Don Williamson shared his real-time web-based code editor & interpreter for the DCPU-16 Virtual Machine. It makes nice use of the canvas tag for a beautiful blue console, features a real-time recompile as you type, and thanks to some custom DCPU-16 support for Marijn Haverbeke ...more
Pull up outside any construction site and you'll see tools scattered about—hammers, jigsaws, nail guns, hydraulic pipe benders—these are the tools of the trade. You would be hard-pressed to build a home or office building with just your hands! On that same page, security profe ...more
It's been an eventful week for Google+. Facebook decided to up its game and start rolling out several major updates intended to address privacy concerns. We got a glimpse into the future of Google+ via an insightful discussion between +Bradley Horowitz and +Tim O'Reilly. And G ...more
Injection is an attack vector that involves breaking out of a data context and switching into a programming context through the use of special characters. These characters are significant to the interpreter being used, but not needed for the general user input being asked for. ...more
WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most ...more
Since its inception in 2007, the Pwn2Own computer hacking contest has been challenging the vulnerability of mobile phones and web-related software. In 2010, the fruit of two full days of hacking came down to the exploitation of the following web browsers: Safari 4 on Mac OS X, ...more
Last week I reviewed Kinotopic, the iPhone app that lets you easily create cinemagraphs. While I loved the result, I found the app hugely flawed. Kinotopic forced you to use a Facebook log-in, and didn't store the finished video on your phone itself. Instead, you had to visit ...more
I may be a bit weird, but I enjoy listening to music at night as I fall asleep. Sure, you could create a playlist of songs so that it stopped after all the songs finished playing, but I have a rather extensive database of music and I enjoy listening to them randomly. Also, I l ...more
A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc. Obviously, not all places use the same methods, and not all of the m ...more
Take a look at this instructional video and learn how to build your own miniature computer numerical control (CNC) machine. A CNC machine acts as a controller that reads G Code instructions for machine tools such as drills and printers. To perform this task, you'll need some g ...more
Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I s ...more
Gboard is one of the best third-party keyboards available for iPhones, but you probably don't know everything you need to know about it to become a real Gboard pro and stop using Apple's stock keyboard for good. I've tried many third-party keyboards on my iPhone since they we ...more
Typing on a mobile device has come a long way since the days of flip phones. Today, there are awesome keyboard apps like Gboard, which integrates Google search features and makes typing a breeze. But the whole experience still stands to improve if you take some time to learn a ...more
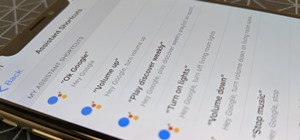
With the holidays over, a lot of people with shiny new Google Homes are getting their first chance to explore the new Google Assistant. Before the Google Home's release, the Assistant was only available for the Google Pixel and Pixel XL, or in a text-based form with Google All ...more
In the last tutorial, we learned how to make functions and how they work on the high level. This time, we will take a peek under the hood again, stare deep into its soul and see its ugliness face to face to see how it works in the lower level. The Code Segment The code segme ...more
Your Android phone could be listening to ultrasonic ad beacons behind your back. The unwelcome news comes year after app developer SilverPush promised to quit using its (creepy!) eavesdropping software. But it looks like the privacy-threatening technology — which can track us ...more
Our everyday lives are inundated with displays from smartphones, computers, tablets, TVs, and other devices, so it's important to find ways to limit your screen use wherever possible to improve your overall digital well-being. One simple thing you can do if you have an Apple W ...more
Despite a rocky start with plenty of feature disparity, the Google Assistant now provides a pretty consistent experience regardless of what device you're using it on. Be it Android, iPhone, or Google Home, the AI behind the Assistant is virtually identical — including its quir ...more
A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fort ...more
Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic An exploit is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability in order to cause unintended or unanticipated behavior to occur ...more
With over 1.5 billion people on this planet without electricity, it's hard for those of us in developed nations to even fathom how anyone can read, write, repair, or do anything else that we take for granted without any lights. While some of our First World problems pale in co ...more
While there is definitely no shortage of video game emulators in the Android Market, it lacks in modern gaming consoles. Nintendo 64, Game Boys, and Sega Genesis are all accounted for, but what about emulators for some of the gaming consoles that have come out in the, let's sa ...more
The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one s ...more
No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today ...more
Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote co ...more
Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite ...more
Just because your Samsung Galaxy Note 2 is on silent doesn't mean that the world stops spinning. Emergencies can pop up at any time, even when your phone is put away during a lecture in class, in the library, or at an important business meeting. You put your phone on silent t ...more
For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swi ...more
We've all been there. Channel surfing lazily whilst reclining on the sofa—then all of a sudden, the remote stops working. Out of frustration, you hold the remote up higher, press the buttons harder, or maybe a even give it a good smack hoping that will fix it. Right around thi ...more
Last week, I showed you a peek at the not-yet-released Galaxy S5 Active, the more rugged version of Samsung's current flagship. The man behind those leaks, TK Tech News, has now brought another goodie from the device, and it's one we can have on the Galaxy Note 3. Dubbed Acti ...more
SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to ...more
Remember the feeling you had the moment you removed your shiny new Nexus device from its packaging and booted it up for the first time? You swiped through the app drawer at lightning speed and thought to yourself, "This is the last Android phone I will ever need, they just are ...more
Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start som ...more
In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exp ...more
Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it do ...more
Third-party keyboards have been available for iPhone ever since iOS 8, but which ones are worth checking out? There have been many options over the years, and if you want keyboard features like swipe-typing and themes, you're going to have to put Apple's stock QuickType keyboa ...more
Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By ex ...more
Last week, I updated VirtualBox on my computer since I had skipped a few versions, then I could no longer copy text or paste text from my Kali virtual machine to my host OS and vice versa. Installing the Guest Additions didn't seem to do anything, and the bidirectional shared ...more
Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input ...more
QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into ...more
So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit mak ...more