How To : Program a random number generator in C++
How to use the rand function in C++ to create a random number generator.

How to use the rand function in C++ to create a random number generator.
Want to program your own Java games and applications but don't know beans about object-oriented programming? Never you fear. This free video tutorial from TheNewBostonian will have you coding your own Java apps in no time flat. Specifically, this lesson discusses how to genera ...more
Have an old-school tabula recta lying around? No? Then just print out the chart below. Nothing ensures better password security than this centuries-old cipher technique. Here's how it works, via Wikipedia: "Using a tabula recta, each alphabet is shifted one letter to the left ...more
If you've ever wondered how software pirates can take software and crack it time and time again, even with security in place, this small series is for you. Even with today's most advanced methods of defeating piracy in place, it is still relatively easy to crack almost any pro ...more
Individually addressable LEDs, also commonly called "NeoPixels" after the popular Adafruit product, are a bright and colorful way to get started with basic Python programming. With an inexpensive ESP8266 or ESP32 microcontroller, it's easy to get started programming your own h ...more
Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making cus ...more
Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account ...more
Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are ...more
You should feel relatively safe to watch and post videos on TikTok, but like with any online service, you're always at the mercy of hackers. It's unfortunate, but anyone can become a target for arbitrary reasons. Maybe your TikTok videos are controversial. Maybe someone has a ...more
Bring a little bit of the excitement of Las Vegas to your Minecraft world. Watch this video to learn how to build a working slot machine, based on a random number generator, in your Minecraft map. Luck be a mob tonight. Part 1 of 2 - How to Build a working slot machine in Mine ...more
Sick of losing quarters to machines that promise you toys? Wanna win the stuffed piggy once and for all? Our guy Matt has won loads of stuffed piggies and he's going to show you how! Matt's an arcade game fanatic. So obsessed, he's purchased his very own claw machine just to ...more
The Calculator app is probably one of Apple's most-used iPhone apps, yet I always meet people who don't know all the little tricks there are to using it more efficiently. You may know most of them, but there's a chance you don't or at least forget about some of them. What a " ...more
Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a " ...more
Google has a few hidden tools you might not have discovered yet, and they work in Google Search, in the Google app, and with Google Assistant — on both iPhone and Android phones. We all know smartphones do much more than make phone calls. They serve as cameras, GPS navigators ...more
When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we'r ...more
Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there i ...more
Just like the recently rediscovered Star Wars ruins in the Tunisian desert, there are tons of hidden treasures in your Samsung Galaxy Note 2 just waiting to be unearthed. Rooting enables you to install custom ROMs, exclusive features from other devices, add Wi-Fi tethering, o ...more
Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that ...more
Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an imag ...more
Social Profile Change the privacy settings on your social profile (Facebook, MySpace, Friendster, Twitter, etc.) so that the following information can't be found by a random person who you didn't accept you as a friend: Birthdate E-mail address Hometown Pictures A hacker ca ...more
In my free time, I like to program in an image programming language called Context Free. You can download it at www.contextfreeart.org for free. The first thing to know about Context Free is that there are three basic shapes to which the program will understand and respond. T ...more
A playlist is simply a list of songs which can be played in sequential or shuffled/random order. Many people tailor-make playlists to suit a particular style of music or atmosphere, so being able to share these between people is great. There are a great many places on the Int ...more
The developer community has already made some incredibly quick progress on implementing assemblers, interpreters, and emulators for the proposed virtual computer in 0x10c, Notch's latest game. But the truth is that the majority of programmers out there couldn't be bothered wit ...more
Today isn't actually Pi Day, but I was unable to get this article out in time. Pi Day was actually yesterday, March 14th (3.14), so let's call this a post-Pi Day treat! I've usually stuck to computers and security in the past, so I thought I'd toss things up a bit and give yo ...more
Introduction The 3 major anonymity networks on the Internet are Tor/Onionland, I2P and Freenet. If you feel confused on which one is the "best" one to use the answer is simple. Use all three! Each anonymity network is designed for a different specific purpose. One network al ...more
I want to write this article because in my childhood, I had experienced internet stalking which ultimately ended in physical stalking which then lead to several attempted abductions. I have now learned how to use the internet safely, who to communicate with and I've learned ho ...more
As per Alex's request, I am posting about generating word-lists in Python. However, this is my FIRST attempt with Python, so please provide me with critiques and any and all comments. I really want to know what you think as there was a little bump here and there seeing as I a ...more
Only so much data can be passed through the network and to your computer's networking interfaces. This is limited by the amount of bandwidth you have. The more bandwidth you have, the faster your network connections will be. Not only this, but your transfers will be more paral ...more
STANDP'S CUSTOM DESKTOP "ASK NOT WHAT YOUR DESKTOP CAN DO FOR YOU...". http://standp-how-to-vidzzz.wonderhowto.com/corkboard/new-post/text/ Showing newest posts with label tips-n-trick. Show older posts DEC 07 Computer Backup If you have taken good care of your computer th ...more
STANDP'S WINDOWS 7 "ASTON-2" CUSTOMIZED DESKTOP IT ROCKS COMPLETELY!. DEC 07 Computer Backup If you have taken good care of your computer then you know what you have to do to keep it running smoothly. It has to be cleaned regularly so there isn't any dirt and dust on it. It ...more
A representative from Math Problem Generator explains in this video that converting a simple fraction from its current state to a higher equivalent can be very simple. He explains the process neatly and provides a great example. To convert a fraction, you must multiply the num ...more
While Google's generative AI wallpapers for Android won't be out until the fall, you can take advantage of emoji backgrounds and cinematic wallpapers on your Pixel smartphone right now. Throughout its history, Android has earned a reputation for giving its users the freedom t ...more
If you're doing the same tasks on your Android phone repeatedly each day — like playing a specific playlist at the gym, viewing work documents, or watching your favorite music video — you can save some time by automating your routine, turning each task into a one-tap gesture o ...more
If you've recently built a Wi-Fi spy camera out of an ESP32-CAM, you can use it for a variety of things. A baby monitor at night, a security camera for catching package thieves, a hidden video streamer to catch someone going somewhere they shouldn't be — you could use it for p ...more
UPDATE: Entries are now closed. Thank you for participating! Next Reality is where we help you literally 'see' into the future of augmented reality, and to help with that mission we're offering three free pairs of Snap Spectacles 3 to three lucky readers who sign up for the N ...more
The music you listen to is often a reflection of your personality, which is why people tend to use the artwork from their favorite albums as device wallpapers. But one lonely album cover may not look right on your iPhone's lock screen, and it's not indicative of your broader m ...more
Chief among iOS 14's excellent new features is the overhauled home screen. Now, you can add customizable widgets that live alongside your traditional apps, and both first-party and third-party apps can take advantage of it. Talk about an upgrade. They even work in the Today Vi ...more
Everything you post on social media lives there forever — even if you delete it. Just ask anyone that's ever posted something stupid. Instagram does not provide built-in tools to save or download images and videos from other users, but there are workarounds. Third-party tools ...more
Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, ...more
Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wor ...more
When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular p ...more
There's a new trend on Instagram Stories: People are making viral AR filters where images of popular characters from TV shows, movies, and other mediums shuffle above your head until one sticks. The filters range from Disney and Pokémon characters to Harry Potter and Friends, ...more
What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system. Understanding the Attack Whi ...more
A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physi ...more
The OnePlus 7 Pro is definitely a beast on paper. With a specs page that ticks virtually every box and a price point that undercuts the competition by hundreds of dollars, it's hard to overlook this phone. But before you get too excited, know that OnePlus has repeatedly shown ...more
If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a ...more
There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help ...more
The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python to ...more
Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebo ...more
Think back to when you last wanted to transfer some music or videos to your friend's smartphone and how difficult and slow it was. As powerful as our phones are, the default file sharing options are limited. There are, fortunately, some better options which make moving files e ...more
You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours. The only thing that makes you pause is that ...more
There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer. It's puzzling to imagine about 100,000 .onion websites in existence. Readers who ...more
Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP wit ...more
Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting ...more
Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than othe ...more
The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user i ...more
Have you been noticing SpaceX and its launches lately? Ever imagined how it would feel to launch your own rocket into the sky? Well, imagine no longer! In this tutorial, you'll learn how to make a simple augmented reality app for iPads and iPhones by using ARKit. Specifically ...more
This year's big iPhone update, iOS 12, aims to solve many of the issues that arose during iOS 11's controversial, buggy tenure. With that in mind, it may be tempting to jump on board the new software immediately and leave iOS 11 in the dust for good. Here are some reasons why ...more
Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless ...more
Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don' ...more
 How To:
Add Website Shortcuts to Your iPhone's Home Screen for Fast Access to Web Apps and Bookmarks
How To:
Add Website Shortcuts to Your iPhone's Home Screen for Fast Access to Web Apps and Bookmarks
 News:
Apple Pencil 3 Is Almost Here — And It Comes with Squeeze Gestures and These Other Features
News:
Apple Pencil 3 Is Almost Here — And It Comes with Squeeze Gestures and These Other Features
 How To:
The Messaging Trick You Never Knew You Needed
How To:
The Messaging Trick You Never Knew You Needed
 How To:
Customize and Use Control Center on Your iPhone for Quick Access to Your Most-Used Apps, Features, and Settings
How To:
Customize and Use Control Center on Your iPhone for Quick Access to Your Most-Used Apps, Features, and Settings
 How To:
11 Features Coming to Apple News on Your iPhone with iOS 17.5 — Including Some Big Ones!
How To:
11 Features Coming to Apple News on Your iPhone with iOS 17.5 — Including Some Big Ones!
 How To:
Apple's Integrating Game Center Leaderboards into News+ Puzzles with iOS 17.5
How To:
Apple's Integrating Game Center Leaderboards into News+ Puzzles with iOS 17.5
 How To:
Apple Has a Killer New Word Game Puzzle Called Quartiles Hiding on iOS 17.5
How To:
Apple Has a Killer New Word Game Puzzle Called Quartiles Hiding on iOS 17.5
 How To:
Identify Any Song Playing on Instagram, TikTok, and Other Apps on Your iPhone Using Shazam
How To:
Identify Any Song Playing on Instagram, TikTok, and Other Apps on Your iPhone Using Shazam
 How To:
Apple News Gives You More Options for Automatic Downloads on iOS 17.5
How To:
Apple News Gives You More Options for Automatic Downloads on iOS 17.5
 How To:
27 New Features and Changes Coming to Your iPhone with iOS 17.5
How To:
27 New Features and Changes Coming to Your iPhone with iOS 17.5
 How To:
Download and Install iOS 17.5 Beta on Your iPhone — And Try New Features Before Everyone Else
How To:
Download and Install iOS 17.5 Beta on Your iPhone — And Try New Features Before Everyone Else
 How To:
Download and Install iPadOS 17.5 Beta on Your iPhone to Explore New Features Before Everyone Else
How To:
Download and Install iPadOS 17.5 Beta on Your iPhone to Explore New Features Before Everyone Else
 How To:
Update Your iPhone's Lock Screen with an Attention-Grabbing Note, Reminder, Warning, or Other Custom Message
How To:
Update Your iPhone's Lock Screen with an Attention-Grabbing Note, Reminder, Warning, or Other Custom Message
 How To:
Your iCloud Email Lets You Create Aliases to Protect Your Primary Email Address and Organize Your Inbox
How To:
Your iCloud Email Lets You Create Aliases to Protect Your Primary Email Address and Organize Your Inbox
 How To:
Use Your iPhone's Built-in Image Analyzer to Reveal the Hidden Meaning Behind Symbols, Signs, and More
How To:
Use Your iPhone's Built-in Image Analyzer to Reveal the Hidden Meaning Behind Symbols, Signs, and More
 Text Replacements:
The Secret Weapon to Typing More with Less on Your iPhone, iPad, or Mac
Text Replacements:
The Secret Weapon to Typing More with Less on Your iPhone, iPad, or Mac
 How To:
Focus Profiles Will Change How You Use Your iPhone — Here's How to Set Them Up for Distraction-Free Experiences
How To:
Focus Profiles Will Change How You Use Your iPhone — Here's How to Set Them Up for Distraction-Free Experiences
 How To:
Force Restart an iPhone 15, 15 Plus, 15 Pro, or 15 Pro Max When It's Frozen, Glitchy, or Won't Turn On
How To:
Force Restart an iPhone 15, 15 Plus, 15 Pro, or 15 Pro Max When It's Frozen, Glitchy, or Won't Turn On
 How To:
Create Unlimited iCloud Email Address Variations to Take Total Control Over Your iCloud Mail Inbox
How To:
Create Unlimited iCloud Email Address Variations to Take Total Control Over Your iCloud Mail Inbox
 How To:
Use Your iPhone to Hear the World Around You Better, Spy on Conversations, Listen to Your Heartbeat, and More
How To:
Use Your iPhone to Hear the World Around You Better, Spy on Conversations, Listen to Your Heartbeat, and More
 How To:
The Messaging Trick You Never Knew You Needed
How To:
The Messaging Trick You Never Knew You Needed
 How To:
See Passwords for Wi-Fi Networks You've Connected Your Android Device To
How To:
See Passwords for Wi-Fi Networks You've Connected Your Android Device To
 How To:
Use FaceTime's Secret Hand Gestures and Reaction Buttons to Add Animated On-Screen Effects to Your Video Feed
How To:
Use FaceTime's Secret Hand Gestures and Reaction Buttons to Add Animated On-Screen Effects to Your Video Feed
 News:
Apple Pencil 3 Is Almost Here — And It Comes with Squeeze Gestures and These Other Features
News:
Apple Pencil 3 Is Almost Here — And It Comes with Squeeze Gestures and These Other Features
 How To:
See What Traffic Will Be Like at a Specific Time with Google Maps
How To:
See What Traffic Will Be Like at a Specific Time with Google Maps
 How To:
Clone Any Android App on Your Samsung Galaxy Phone Without Using Any Third-Party Tools
How To:
Clone Any Android App on Your Samsung Galaxy Phone Without Using Any Third-Party Tools
 Hacking Windows 10:
How to Dump NTLM Hashes & Crack Windows Passwords
Hacking Windows 10:
How to Dump NTLM Hashes & Crack Windows Passwords
 How To:
Dox Anyone
How To:
Dox Anyone
 How To:
Dial These Secret Codes to See if Someone Is Hijacking Calls & Texts on Your iPhone
How To:
Dial These Secret Codes to See if Someone Is Hijacking Calls & Texts on Your iPhone
 How To:
Turn Your Gag Reflex Off with Pressure Points
How To:
Turn Your Gag Reflex Off with Pressure Points
 Android Basics:
How to See What Kind of Processor You Have (ARM, ARM64, or x86)
Android Basics:
How to See What Kind of Processor You Have (ARM, ARM64, or x86)
 How To:
The Complete Guide on How to Build a Crystal Radio—Plus How They Work
How To:
The Complete Guide on How to Build a Crystal Radio—Plus How They Work
 How To:
Stealthfully Sniff Wi-Fi Activity Without Connecting to a Target Router
How To:
Stealthfully Sniff Wi-Fi Activity Without Connecting to a Target Router
 Hacking macOS:
How to Perform Privilege Escalation, Part 1 (File Permissions Abuse)
Hacking macOS:
How to Perform Privilege Escalation, Part 1 (File Permissions Abuse)
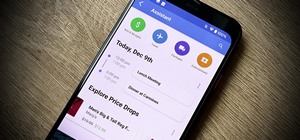 How To:
View Calendar Events & Invites in Edison Mail While Checking Your Email
How To:
View Calendar Events & Invites in Edison Mail While Checking Your Email
 How To:
Create an Admin User Account Using CMD Prompt (Windows)
How To:
Create an Admin User Account Using CMD Prompt (Windows)
 How To:
Clear Your Frequently Used and Recent Emoji from Your iPhone's Keyboard
How To:
Clear Your Frequently Used and Recent Emoji from Your iPhone's Keyboard
 How To:
Crack Shadow Hashes After Getting Root on a Linux System
How To:
Crack Shadow Hashes After Getting Root on a Linux System
 How To:
Exploit EternalBlue on Windows Server with Metasploit
How To:
Exploit EternalBlue on Windows Server with Metasploit
 How To:
Use Odin to Flash Samsung Galaxy Stock Firmware
How To:
Use Odin to Flash Samsung Galaxy Stock Firmware
 How To:
27 New Features and Changes Coming to Your iPhone with iOS 17.5
How To:
27 New Features and Changes Coming to Your iPhone with iOS 17.5
 How To:
Check if Your Wireless Network Adapter Supports Monitor Mode & Packet Injection
How To:
Check if Your Wireless Network Adapter Supports Monitor Mode & Packet Injection
 How to Hack Wi-Fi:
Cracking WPA2 Passwords Using the New PMKID Hashcat Attack
How to Hack Wi-Fi:
Cracking WPA2 Passwords Using the New PMKID Hashcat Attack
 How To:
Test Your Samsung Phone by Using Secret Code *#0*#
How To:
Test Your Samsung Phone by Using Secret Code *#0*#
 How To:
19 Harry Potter Spells Your Android Phone Can Cast Using Google Assistant
How To:
19 Harry Potter Spells Your Android Phone Can Cast Using Google Assistant
 How To:
The Best Investigatory Projects in Science: 16 Fun & Easy Ideas to Kickstart Your Project
How To:
The Best Investigatory Projects in Science: 16 Fun & Easy Ideas to Kickstart Your Project
 How To:
13 Tips Every Apple Pencil User Needs to Know for iPad
How To:
13 Tips Every Apple Pencil User Needs to Know for iPad
 How To:
The Easiest Way to Secretly Record Someone's Conversation with Your iPhone
How To:
The Easiest Way to Secretly Record Someone's Conversation with Your iPhone
 How To:
Disable the iMessage Typing Bubble Indicator So Others Don't Know You're Currently Active in the Chat
How To:
Disable the iMessage Typing Bubble Indicator So Others Don't Know You're Currently Active in the Chat
 How To:
11 Features Coming to Apple News on Your iPhone with iOS 17.5 — Including Some Big Ones!
How To:
11 Features Coming to Apple News on Your iPhone with iOS 17.5 — Including Some Big Ones!
 How To:
Make a Fire Snake from Sugar & Baking Soda
How To:
Make a Fire Snake from Sugar & Baking Soda
 How To:
Tell if Your 'Expired' Eggs Are Still Good to Eat
How To:
Tell if Your 'Expired' Eggs Are Still Good to Eat
 How To:
Use MDK3 for Advanced Wi-Fi Jamming
How To:
Use MDK3 for Advanced Wi-Fi Jamming
 How To:
3 Easy Steps to Fixing Stuck Buttons on Your Phone or Tablet
How To:
3 Easy Steps to Fixing Stuck Buttons on Your Phone or Tablet
 Hacking macOS:
How to Configure a Backdoor on Anyone's MacBook
Hacking macOS:
How to Configure a Backdoor on Anyone's MacBook
 How To:
Listen to FM Radio on a Google Android Smartphone
How To:
Listen to FM Radio on a Google Android Smartphone
 How To:
Hack WPA & WPA2 Wi-Fi Passwords with a Pixie-Dust Attack Using Airgeddon
How To:
Hack WPA & WPA2 Wi-Fi Passwords with a Pixie-Dust Attack Using Airgeddon
 Outlook 101:
How to Customize Notifications & Alert Sounds for Individual Accounts
Outlook 101:
How to Customize Notifications & Alert Sounds for Individual Accounts
 The Hacks of Mr. Robot:
How to Use the Shodan API with Python to Automate Scans for Vulnerable Devices
The Hacks of Mr. Robot:
How to Use the Shodan API with Python to Automate Scans for Vulnerable Devices
 How To:
MagSpoof Digitally Clones the Magnetic Stripe of Any Credit Card
How To:
MagSpoof Digitally Clones the Magnetic Stripe of Any Credit Card