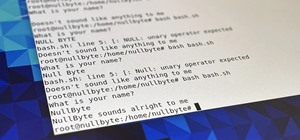
Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, ...more
Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network. Whe ...more
Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to activ ...more
The older I get, the more my Friday nights involve watching Netflix at home with a bottle of Maker's Mark and a box of Oreos. Netflix is a big part of my life, and I'm not alone. YouTube and Netflix make up over 50% of all activity on the Internet, so it might be worth your ti ...more
If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for ...more
Withstanding an attack from a motivated hacker is one of the most important responsibilities a system administrator must undertake. This is especially true for websites that may contain sensitive customer information and a high volume of users. So it's important for a sysadmin ...more
Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highl ...more
Apple's iOS 16.6 software update for iPhone was released on July 24, with iOS 16.7 following on September 21. While Apple is currently focused on improving iOS 17, we may see iOS 16.8 pop up. When it does, you can try out all the upcoming new features as long as you're OK with ...more
If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs ...more
Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you ...more
There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer. It's puzzling to imagine about 100,000 .onion websites in existence. Readers who ...more
Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to d ...more
Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tra ...more
Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google. Google offers ...more
A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simpl ...more
Supercell's highly anticipated Brawl Stars has soft launched in Canada, with gamers worldwide salivating at the prospect of a full debut around the corner. Unbeknownst to many, this game can be played on your iPhone right now, regardless of where you live. As a testament to t ...more
You see the status bar nearly everywhere on your iPhone, and it almost always looks the same. But you can use a few tricks to spice things up a bit — without jailbreaking your iPhone. The status bar's background on iOS is transparent, so you'll see different colors and gradie ...more
While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show y ...more
Apple's iOS 16.3 update for iPhone had impressive new features, but iOS 16.4 might impress you even more. The latest iPhone update was released on Monday, March 27 — a day earlier than Apple Music Classical, Apple's new classical music streaming service — has at least 30 more ...more
Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and r ...more
NetGuard is a well-established app known for its highly secure firewall, which blocks unwanted web activity from individual apps that can take up both precious bandwidth and battery life. Not quite as well known, however, is the fact there's a second official version of NetGua ...more
Having the ability to stream music or video from practically any internet-capable device is a thing of wonder—especially at the airport. I don't know how many times Netflix has saved me from watching something like CNN for 5 hours straight at the gate during long layovers. But ...more
A man-in-the-middle attack, or MitM attack, is when a hacker gets on a network and forces all nearby devices to connect to their machine directly. This lets them spy on traffic and even modify certain things. Bettercap is one tool that can be used for these types of MitM attac ...more
You can view battery information in the Today View, you already know what carrier services you, and you can quickly figure out with normal use whether your display orientation is locked, so what do you need the status bar at the top of your iPhone? If you don't find much use f ...more
Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full ins ...more
Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website w ...more
The idea of a perfect phone is a myth. There are lots of pros when it comes to OnePlus devices, but there are also a few things that could be better. And even if there were a phone without flaw, there are still things that you might want to customize for personal preference. T ...more
This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/ In this post we will explore more about finding hacked accounts online, w ...more
The Pixel and Pixel XL come with an awesome data-saving feature called Wi-Fi Assistant that automatically connects to open internet hotspots, then creates a secure VPN on your device to keep your data safe. When you're connected to a Wi-Fi network, internet speeds are general ...more
These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred. We vigilantly remember to lo ...more
Your Galaxy's lock screen already lets you know there's no SIM card installed if it's missing on your device, so there's really no need to have a persistent icon for it on the status bar. If you want to hide the pesky symbol and accompanying notification for good, there's a ni ...more
Okay, so you rooted your Android phone .... now what? There are a few ducks you need to get into a row, like backing up your stock boot image, getting SafetyNet sorted, and improving security with biometrics. But there are also awesome root mods waiting for you — just don't ge ...more
The internet is a scary place, and if you're like me, you don't want anyone tracking you or learning your search habits. It's a blatant invasion of privacy for companies to do this, but at least we have methods of fighting back—one of which is Tor. Tor stands for The Onion Ro ...more
Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you. Rooting allows you to remove barriers and open Android to a level of unprecedented contro ...more
Out amongst the ether of the internet lies a completely different version of the Netflix library you've come to know and love. Because of licensing and rights fees, the streaming media giant maintains separate libraries for each country it services. Ultimately, this means that ...more
Updating your Galaxy to the latest software version is optional, but you wouldn't know that from the persistent notification and status bar icon that are constantly reminding you to. Thankfully, you're just an app away from hiding these eyesores without the need to update your ...more
Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacki ...more
Defcon is the largest hacker conference with something for everyone, whether it be the talks, parties, villages, or any of the hundreds of events. In this guide, we'll take a holistic view at everything that goes into attending the con for the first time, from securing your el ...more
If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to co ...more
When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Crea ...more
It hasn't been long since Apple released iOS 16.0 with over 350 new features, but iOS 16.1 just came out with even more cool updates for your iPhone. While some of the recent upgrades were expected, others are somewhat surprising — and there's even one that you may not even th ...more
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started. OVERVIEW: As you'll get further into the hacking community, and learn more about how it's all put together, you'll also realize very quick ...more
I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to rememb ...more
It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default ...more
This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me. Introduction:Internet has commonly three parts as per my knowledge 1st:surface web,2nd :Darknet and 3rd :Deep web Surface web:We use surface ...more
If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streamin ...more
After reviewing the international plans for major US wireless carriers, it became obvious they're all pretty bad. Your data is heavily restricted, requiring a daily fee which can cost an extra $100+ on a seven-day vacation. That's when I learned about Google Fi, and how for mo ...more
Slowly but surely, Microsoft is pushing more and more options out of the Control Panel and into a new menu simply called Settings. This new Settings menu debuted with Windows 8 and mainly focused on touchscreen-related options, but starting with Windows 10, you'll find quite a ...more
Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself ...more
Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their c ...more
Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private cha ...more
Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, w ...more
Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go. ...more
Google's new Pixel and Pixel XL flagships are some very powerful smartphones, but as with any high-tech gadget, they're only as capable as the user allows them to be. So if you're a proud new Pixel owner, it's time to bone up on a few new features to help get the most out of y ...more
Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP wit ...more
So far, iOS 13's major point updates have all been pretty exciting for iPhone. We've seen iOS 13.1, 13.2, and 13.3 come and go, offering more than 60 new features and changes combined to that very first version of iOS 13. While iOS 13.3.1 was a minor update, its successor, iOS ...more
Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue. There are a multitude ...more
MLB.TV is a great service that lets you watch most Major League Baseball games in North America, as long as you're a subscriber, of course. While I personally love it, blackouts can ruin the ability to watch my favorite teams. Fortunately, MLB At Bat Android users have an easy ...more
The next time you need to build some IKEA furniture or assemble a shelf in the bathroom, bring your Samsung Galaxy S20. It has a hidden feature that replaces one tool you will need for the job. While it's not exactly this feature's intended purpose, the stock camera app can v ...more
After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimiz ...more