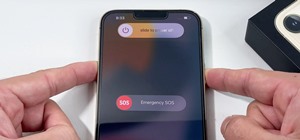
The moment arrives when you finally pop a shell on the web server you've been working on, only you find yourself in a strange environment with limited functionality. Restricted shells are often used as an additional line of defense and can be frustrating for an attacker to stu ...more
For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been ...more
A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of ...more
Sitting at home alone on Friday night, I'm often in the mood to watch something more recent than the offerings on Netflix, Hulu, or Amazon Prime Video. And since the demise of video rental stores, that leaves me with browsing through the Redbox catalogue, then strolling down t ...more
One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but lu ...more
It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time. Both Facebook and Gmail ...more
If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment. Using a directional Wi-Fi antenna and Wireshark, we can create a display filter to target any device in range to plot the signal strength on a gra ...more
A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts f ...more
In the case of Apple Watch v. Fitbit, the winner comes down to the judge at hand. Apple currently offers two smartwatches — the Series 5 and the Series 3 — while Fitbit offers three models — the Fitbit Versa 2, Fitbit Ionic, and Fitbit Versa Lite. Whatever your assumptions abo ...more
You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours. The only thing that makes you pause is that ...more
If you're looking to acquire the newest iPod model or latest Xbox without breaking the bank, your first stop would probably be eBay, maybe even the Amazon Marketplace, or any of the other reputable online marketplaces and auction sites. But you probably haven't hit up the penn ...more
Windows 10 has proved to be immensely popular (free upgrades certainly don't hurt), and with back to school time, there's a good chance you have a new computer running Microsoft's latest OS. You maybe you decided to go with a clean installation rather than an upgrade, or just ...more
The iPhone X was released in November 2017, and the iPhone 8 and 8 Plus dropped right before it, but the hottest news right now revolves around the 2018 iPhone releases. The rumor mill regarding the iPhone X's successor started churning out speculations on names, cameras, disp ...more
By combining years of web search advancements, natural language processing, and even DeepMind's artificial intelligence, Google Assistant hopes to change the way you interact with your devices. If you're familiar with Google's previous services, Google Assistant is like Google ...more
In many urban areas, GPS doesn't work well. Buildings reflect GPS signals on themselves to create a confusing mess for phones to sort out. As a result, most modern devices determine their location using a blend of techniques, including nearby Wi-Fi networks. By using SkyLift t ...more
There are a few different types of Apple iPhone and iPad users: general household users who largely consume media—e.g. surfing the web, watching movies, listening to music. Other iPhone and iPad owners use their device(s) to produce stuff—written documents, edited movies, blog ...more
Your iPhone is full of features, many of which you might not even know about yet. Still, Apple keeps adding feature after feature with each new iOS update, and iOS 14.5 is no exception. The latest iOS version adds at least 69 features for your iPhone that you should be happy a ...more
Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopp ...more
Eating flowers is a time-honored culinary tradition, from nibbling on nasturtiums to grazing on candied violets. And why not? They look beautiful and lend a unique floral flavors to salads, desserts, and anything in between. Don't Miss: Weird Ingredient Wednesday—Zucchini Blo ...more
In this post-3.5 mm world, Bluetooth is the most universal option. But a lot of older electronics still don't support wireless audio. Welp, now there's a dongle for that. The AirFly dongle (from $34.99 on Amazon) plugs into any 3.5 mm headphone jack (mini jack) and provides a ...more
The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to ...more
Even though the Music app took a backseat during Apple's initial iOS 14 announcements, there's a lot going on in the updated app. Some of the new features and changes apply only to Apple Music subscribers, while others apply to your own music library, so there's something for ...more
Popcorn Time is an app that streams movies directly from torrents on to your computer, and it's seen its fair share of publicity, being lauded as a free Netflix alternative and chastised as an illegal file-sharing network. After a brief legal scuffle influenced the original d ...more
So, you've got your new iPhone 5 from Apple, but wait—where do you get a case for it? Since its launch, Apple Stores across the country have been carrying absolutely zero iPhone 5 cases. In fact, the only thing they seem to be carrying right now as far as iPhone 5 accessories ...more
Essentially, the Anti-Griddle does exactly what its name promises: it turns things almost instantaneously cold when you drop them on its "grilling" surface. Unlike home methods of flash freezing, its staggeringly low temperatures (-30°F/-34.4°C) allows ingredients that normall ...more
Here at Food Hacks, we're very fond of finding ways to regrow food. That means taking things like carrot tops and leftover bits from garlic, onions, chives, and other herbs and aromatics to create mini reusable herb gardens. Don't Miss: Vegetables & Herbs You Can Eat Once & R ...more
If you had a phone in 2004, there's a pretty good chance it was a Motorola RAZR. The iconic phone is the tenth highest-selling of all time, and it marked the height of the flip phone era. Now that the technology has caught up, Lenovo (Motorola's parent company) is bringing it ...more
While obvious, it's a lot more difficult to hack into a locked computer than an unlocked computer. As a white-hat hacker, pentester, cybersecurity specialist, or someone working in digital forensics, there's an easy solution — make it so that the computer won't fall asleep and ...more
Its official: On May 8, T-Mobile finally released the Android Oreo update for the LG V30 and V30+. Now, every major US wireless carrier has pushed the update. For me, this update is a big deal. Not only does Android Oreo bring some new tools and features, but LG has also inclu ...more
While it's easy enough to ask websites not to track your browsing activity in Safari, they do not have to honor your request. Plus, some of the third-party content providers that websites use can actually invasively track you across other websites. Thankfully, iOS 11 includes ...more
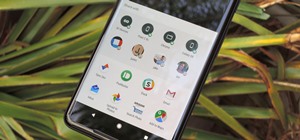
While there aren't as many ways to customize your iPhone like there is on Android, there are still a lot of apps out there that can help streamline and enhance your experience beyond Apple's own default options — and we've hand-picked over 100 essentials. No matter if you've ...more
The OnePlus 7 Pro is definitely a beast on paper. With a specs page that ticks virtually every box and a price point that undercuts the competition by hundreds of dollars, it's hard to overlook this phone. But before you get too excited, know that OnePlus has repeatedly shown ...more
To share a song or album to family and friends, it's as easy as copying its link in the app and pasting that into a message. However, not everyone uses the same music streaming service, so a link to an Apple Music song won't do a Spotify, Tidal, Pandora, Deezer, or YouTube Mus ...more
You've all probably heard about Apple's attempts to thwart iPhone 4 users from opening up their own devices, thanks to their sly maneuvers in switching out everyone's screws with those funky pentalobular screws. But one thing Apple will never learn— they will never have comple ...more
It's nearly impossible to comfortably lay down on your bed or couch with headphones on. Sure, you can position yourself so that your headphones don't touch anything, but that usually means facing up at the ceiling, which is a huge no if you're watching something on Netflix or ...more
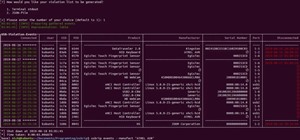
File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, ...more
A rather exciting development has recently surfaced in the jailbreaking scene for iPhone. The Checkm8 bootrom exploit was shown off to the public by axi0mX, which made way for the undefeatable Checkra1n jailbreak tool. With it, you can freely jailbreak a variety of older iPhon ...more
So, you've finally scored the coveted upgrade to chocolaty KitKat deliciousness, or you've managed to get your hands on a Nexus 5, the freshest thing from LG and El Goog. Satisfied with your new lease on life, you direct your phone's web browser to catch up on your Amazon Inst ...more
You have an assignment due, whether it's homework for school or a project for work, but you've only got a few hours left. There's no way you're going to finish in time and do a good job, and you don't want to turn in anything incomplete or half-assed. While it may seem you're ...more
If you use a wireless mouse or keyboard, you could be leaving yourself open to attacks from hackers. Researchers at Bastille had discovered in January 2016 that attackers could make use of a cheap $15 antenna to sneak into your computer through a wireless mouse or keyboard don ...more
Our smartphones have outlived the Walkman, iPod, and even stereo systems, to some degree. So it makes sense to treat your iPhone or Android device to a quality pair of headphones, whether you're a hardcore audiophile or just an everyday music lover. This doesn't come cheap, of ...more
Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite ...more
There are many ways to calculate basic math problems and solve algebraic equations, geometric expressions, and trigonometric functions on your iPhone, but Apple just came out with one that will blow you away. With the upcoming iOS 18 software update, released on Sept. 16, you ...more
The manual that's included with the Canon EOS 5D Mark II is a great starting point for learning the camera, but it's definitely not the only place you should be getting your information from if you intend to master your 5D Mark II. If you don't have the manual, you can downloa ...more
Mac owners— life just got a little easier. No longer do you have to wait in line for the newest version of iLife. No more searching Amazon or eBay for the best price on Aperture. And no more Angry Birds on your mobile device's small touchscreen! Yes, the new Mac App Store wa ...more
Before, eReaders were only used to read eBooks. Not anymore. As tablet computers become more and more advanced, eReaders like Amazon's Kindle, Sony's Reader and Barnes & Noble's Nook are forced to expand their capabilities beyond the basic bibliophilic needs. And the first to ...more
Do you remember when video games came on tiny chips in plastic cartridges? When the CD and 3D graphics just meant ugly games with long load times? Before epic cinematics, spoken dialog, or cordless controllers? Do you still have all of your old games and lament that the consol ...more
AirPods are not only a great way to listen to music on your iPhone, but you can also use them as a headset for phone calls, videoconference, Siri, voice memos, audio messages, and more. While each 'Pod has a built-in microphone, they aren't used simultaneously, and your AirPod ...more
Automation has been a buzz word for quite some time now, but the principles behind it are as strong as ever. For a hacker or pentester, Bash scripting is one form of automation that cannot be ignored. Virtually any command that can be run from the terminal can be scripted — an ...more
Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, ...more
It isn't a new gadget, but the EyeClops Mini Projector still makes a great stocking stuffer for Christmas Day. It's great for kids to play with, but for techies— it's sure to be something fun to hack and mod this holiday season. The EyeClops Mini Projector looks more like Wal ...more
Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listenin ...more
For some, one of the coolest new features in iOS 14 is the Picture in Picture mode, which had previously only been available on the iPad. With it, you can continue watching a video from an app in an interactive floating overlay window on the home screen or within other apps. B ...more
The fact that this guide even exists is a downright shame, but that's neither here nor there. The truth of the matter is the iPhone 7 and 7 Plus don't have 3.5 mm headphone jacks, and since they use the Lightning connector to output audio, it's hard to charge your phone while ...more
Digital distribution games are already firmly established on the PC, and they've infiltrated every present and next-gen console to some degree. Whether you like to play DOS, AAA, PC or indie games, there's a way to purchase most of them without leaving the comfort and warmth o ...more
Apple's latest big update to iOS 14 has a lot to be excited about. While iOS 14.2 had some fun new features, such as new emoji and wallpapers, People Detection in Magnifier, and a Shazam control, iOS 14.3 brings on the heat. There are new Apple services and products that are s ...more
Nothing makes my stomach growl and my mouth water quite like the smell of roasting chicken. It's a pretty universal reaction, too—there's a reason every grocery store places its rotisserie grills and delis near the entrance, after all. The appeal of the grocery rotisserie chi ...more
Another year, another Oscars. This year's red carpet coverage kicks off Sunday, March 4, at 6:30 p.m. EST, while the ceremony itself starts at 8:00 p.m. EST. Finding a stream online isn't always the most straightforward endeavor, especially if you want it to be free. To avoid ...more
Apple's first big iOS 17 point update for iPhone just came out, and it includes some of the features initially planned for the iOS 17.0 release last September. But there's much more to iOS 17.1 than that — exciting new features and changes are hiding within Books, Music, Stand ...more
Last year, many were caught off guard when Google released a midrange Pixel device. It was quickly crowned the best value-buy phone on the market, as it brought most of the camera tech people loved in the flagship Pixel for almost half the cost. Google's 2020 entry in this ser ...more