The fatal crash of Air France Flight 447 is one of the most tragic accidents in avionic history — while it also serves as a stark reminder of what can go wrong when humans rely too much on driverless vehicles. The tragic 2009 plane crash off the coast of Brazil involved an Ai ...more
Google has done it again—they've pushed another broken OTA update for the Nexus 6. Except this time, it almost completely softbricks your Nexus 6 instead of just screwing up Android Pay and SafetyNet. Apps are force-stopping left and right, making the phone practically unusabl ...more
A young child becomes very thirsty very often and seems tired all the time. A visit to the pediatrician determines she has type 1 diabetes. The onset of type 1 diabetes may seem sudden, and it can be, but the disease may actually have been triggered by common childhood viruses ...more
Greetings comrades! Great leader has ordered that we gain intel on a website owned by the opposition. For all general purposes we will be scanning nmap.org because they really don't care if Big Brother decides to perform a whois on their IP. We will be using Dmitry for the sca ...more
What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey ...more
Spills happen in the kitchen, and while every good cook knows to clean as you go, not every cook has an endless supply of cleaning materials. Besides, one spill can exhaust your entire stockpile of sponges, paper towels, and rags in a matter of minutes. Particularly egregious ...more
Beer, glorious beer! It can stop grilled meats from producing carcinogens, can make fried foods super crunchy, and it even saved civilization from total annihilation. Is there anything it can't do? Sadly, yes. While most of you know that a perfect pour makes all the differenc ...more
International, T-Mobile, and Verizon customers all share something in common—their carriers provide unlocked Wi-Fi tethering for free. Of course, you still pay for the data used, but they don't charge you extra simply for using your Samsung Galaxy S4 as a wireless hotspot. Ho ...more
Whether you like it or not, certain songs get stuck in your head. You might be driving to work or school when suddenly Cher's 1998 lead single "Believe" plays on the radio. Video: . You pay no heed to the song because you're stuck in traffic, and all you can think about is get ...more
Timely costumes for Halloween are awesome—especially really obscure ones—because they're indicative of social awareness. In 2010, I remember seeing several Chilean Miner costumes, which I thought were great. 2012 brings new stories, new characters and more importantly...new Ha ...more
I love robots. They have the potential to evolve into Asimovian destroyers of the human species, but have only just mastered the art of cleaning my rug. They have an ever increasing cool factor and a growing number of cheap and simple components that let the hobby roboticist r ...more
The Samsung Galaxy Note 8 (or Galaxy Note8, depending on how you like it) is one phone which couldn't possibly have bigger shoes to fill. Samsung's latest flagship has officially been announced, so it's time to decide whether not it's capable of filing the void left by the fai ...more
And so it begins... CES 2017 is upon us! This is a very exciting time for those who are looking out for the newest innovations and releases from the world of technology. I said this was going to be a fun week, and here we start it with a bang from smartglasses developer Osterh ...more
The coming year promises to be a good one for those of us watching the augmented and mixed reality world. And the Consumer Electronics Show (CES), starting Jan. 5 in Las Vegas, Nevada, for its 50th year, is bringing 2017 in with a bang—we're expecting a ton of great announceme ...more
It was definitely a shocker when Microsoft proposed cross-network play between the Xbox One and PlayStation 4 last month. After all, Microsoft and Sony have been competing for the same user base for more than a decade now, and this new feature might actually decrease console s ...more
Holidays are a time for good food and good drink, but more often than not, we substitute good drink for, well, cheap drink. However, cheap wine doesn't have to be bad. As the international wine industry grows, it's becoming more common to find decent bottles on the cheap, and ...more
Making a good pie crust can seem intimidating to the uninitiated, but once you master this skill, a whole world opens up to you. Not only can you make all manner of fruit, custard, and cream-filled pies once you know all the tricks, you can branch out into the world of quiches ...more
We all want to be healthy, but in practice, it can be tricky, especially from the fitness angle. Our lives seem busier and busier, which makes hitting the gym quite the challenge. What if we told you there was a real way to work on your fitness in the comfort of your own home ...more
With ultra competitive games like Fortnite Battle Royale and PUBG taking the mobile world by storm, gamers are looking for ways to get a leg up on the competition. One of the biggest advantages you can give yourself is the ability to aim and shoot while on the move, but that's ...more
While everyone was marveling at the latest drama over at Magic Leap involving employees last week, a major rumor listed in one of the reports, related to the company's flagship device, was mostly overlooked. "One current issue with the headset is battery life and charging; th ...more
With the release of the Pixel 2 XL and the iPhone X, smartphones have hit a new high not just in price, but also raw processing power. These new flagships not only cost more than twice as much as an Xbox One or PlayStation 4, they have also become almost as powerful as far as ...more
The 12.9-inch iPad Pro was released in stores on November 11, 2015, and a couple days later I went to an Apple Store and to check it out in person. I had mixed feelings about the tablet, but was intrigued overall—so much so that over the next few weeks, as I found myself heari ...more
Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in! Recap In the previous tutorial, we learned how to write a program which opened itself for reading to write to a host file, overwritin ...more
Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elli ...more
Google inconspicuously announced an Android update yesterday, and while it's not quite the overhaul that the initial Lollipop release was, version 5.1 brings plenty of bug fixes and new features. This new version is currently on a staged rollout for Nexus devices, so the upda ...more
Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely da ...more
The holiday season is almost over, bringing the year to an end, and what better way to end it than with some tonsil hockey from the dime across the room on New Year's Eve? If you missed the opportunity to snag a kiss using the awesome mistletoe trick, then this is your last c ...more
Why can't I see who is stalking my Facebook profile? There are other social networks that do let you see who's viewed your profile, mainly LinkedIn and its "Who's Viewed Your Profile" feature. Regular users can see a recent list of who has been spying on you, along with some ...more
Living in Los Angeles has given me the opportunity to attend a bunch of really cool events. I've been to Dodgers, Lakers, and Clippers games, a few concerts at the Staples Center, and a plethora of smaller joints. In all of these places, I've found a consistent annoyance—I wa ...more
In my last article, I explained why text adventure games are some of the most Steampunk computer games out there. I even shared a free Steampunk text adventure game that I'd made myself! Now, I grew up playing text-based games (which are now known as interactive fiction) such ...more
Not that long ago I wrote an article discussing what it would be like, realistically, if you were to accidentally travel back in time to the Victorian era. At the end of that article, I mentioned that the best thing you could bring with you on a time-traveling adventure is a K ...more
The new iPhone 5 was just revealed yesterday, and it's 18 percent thinner and just 1/5 the weight of its 4S predecessor. It's also taller with a larger screen, which gives you a fifth row for apps now. As far as speed is concerned, it has a speedy A6 chip and can tap into wire ...more
If you have a Barnes & Noble Nook, you may be surprised to find that your eReader can do a lot more than just display ebooks, which makes it a great alternative to those more expensive all-in-one tablets that do everything (seriously, everything). If you want to get more bang ...more
You're watching a YouTube video on your Mac, then go to check something on your iPhone. Of course, because you had a video queued on iOS, your AirPods automatically switch from your Mac to your iPhone. Now, your Mac's YouTube video is playing out loud, and you have to reroute ...more
Despite some of the biggest players in tech still lagging in terms of offering smartglasses options, there are nevertheless a number of smartglasses makers, including North and Vuzix, with consumer-grade smartglasses on the market right now. Startup Form now joins the ranks o ...more
Thanks to numerous smartwatch deals this holiday season, many people are receiving their first one. But what exactly can they do? In regards to fitness, quite a lot. With a growing list of sensors and software updates, these small devices can be the very thing you need to ulti ...more
There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help ...more
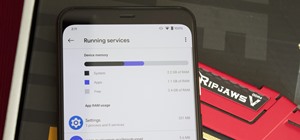
Battery drain is a major pain point for Android users, though that promises to change thanks to Android Pie's new Adaptive Battery feature. But Google hasn't said much about the inner workings of this feature, only publicly stating that it uses AI to boost battery life. So we ...more
Every once in a while, we find ourselves in a predicament where we need an inexpensive smartphone. Whether we're finally upgrading from that feature phone we held onto too long or we dropped our current smartphone, sometimes we need a quick replacement to get back on track. Th ...more
Because augmented reality is still so new to so many people, there are a number of would-be experts opining online, often repeating basic facts anyone with a spare 15 minutes can find on their own. That's why it's important to point out when someone delivers what could be cons ...more
It looks like the dust is finally starting to settle on Google's POLED PR nightmare. The Pixel 2 XL — one of the most hotly-anticipated phones of the year — has been plagued by screen issues and worries. While it is certainly not without its faults, Google has created several ...more
When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we'r ...more
By connecting the dots between theory and real-life effect, two new studies offer more proof that neonicotinoid insecticides are causing extensive damage to honeybee colonies. Research studies have linked neonicotinoid insecticides to damage to honeybee colonies, while agricu ...more
Right now is that magical time of year when the general public decides to embrace their inner fattie and get baking in the kitchen. Hello, pies and cakes and cookies and everything carbs. Goodbye, diets—see you in the next year, when you cripple us with unbridled guilt and lon ...more
Most of you lot would be aware what WPA/WPA2 is so I won't bang on about the encryption or protocols a great deal. In short WPA and WPA2 both have a maximum of 256bit encrypted with a maximum of 64 characters in the password. The encryption is really only 64bit but x 4 because ...more
Hello NullByte! This will be my first How To series. In this tutorial you'll learn what SQL is, what SQL injection is and how it benefits you as a hacker. I strongly recommend learning at least the basics of PHP before attempting to learn/use SQL Injection. list of reference ...more
Ask 100 chefs what the most important tool in their kitchen is, and you'll get 100 chefs saying the exact same thing: their set of knives. For home cooks and professional chefs alike, nothing is more important (or exciting) than a good knife. A good knife allows you to work mo ...more
French toast is one of those things that everybody kind of knows how to make, but few people know how to do really well. And while the dish originally does hail from France (its original name, pain perdu, means lost or wasted bread), it has become a beloved American breakfast ...more
I grew up in a household where bacon was considered its own necessary food group. My mom saved the bacon fat in a jar and reused it in other dishes, which my friends considered vile, unless they were also from immigrant families or the American South, where saving bacon fat ha ...more
Most of us have conducted an investigatory science project without even knowing it, or at least without knowing that's what it was called. Most science experiments performed, from elementary to high school students and all the way up to professional scientists, are investigato ...more
We see Steampunk props all the time and wonder where the maker found all their pieces. In fact, for some people it's almost like a game to examine each prop and see if they can name all of the original parts. However, for a newcomer (or a novice at prop-making), it may be rea ...more
War leaves a lot of stuff behind. Torn families, delegitimized institutions, mass graves, and unexploded ordinances litter the post occupation landscape. Whether or not you have driven the imperialist out, or are still in the phase of armed resistance, you will need the abilit ...more
You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information i ...more
So far, iOS 13's major point updates have all been pretty exciting for iPhone. We've seen iOS 13.1, 13.2, and 13.3 come and go, offering more than 60 new features and changes combined to that very first version of iOS 13. While iOS 13.3.1 was a minor update, its successor, iOS ...more
People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the out ...more
Facebook really wants your phone number, nagging you for one as soon as you join. This isn't all bad since it can help secure your account with two-factor authentication. On the flipside, this makes it easy to reveal the private phone numbers of virtually anyone on Facebook, i ...more
Our smartphones are full of personally-identifiable information. So much of what we do with these devices is tracked and recorded to make our experience more streamlined and personalized. For many users, that's a fair trade — but for privacy-minded folks, it's a raw deal. And ...more
If you're an Android fan, you're probably familiar with Qualcomm's Quick Charge technology or, at the very least, what it can do. Quick Charge 3.0, the third generation of Qualcomm's fast-charging technology, is built into most Snapdragon SoCs and it's what lets you charge you ...more
The software released in the 2015 iterations of the Samsung Galaxy line of devices—the S6, S6 Active, S6 Edge, S6 Edge+, and Note 5—have some pretty neat camera features that give these devices arguably the best smartphone camera on the market today. Out of the box, Samsung's ...more
Telemarketers can be as terrifying as a villain from a horror film. Your phone rings with an unknown 800 number, and you immediately fill with a sense of dread. There's no way to get them to stop calling; you imagine the number appearing on your phone at all hours of the day a ...more