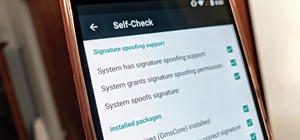
The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix ...more
Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet. So no, there's no such ...more
We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us be ...more
One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security. There are a number of steps you can take to i ...more
This quick tutorial runs you through a fast and easy way to make your iPhone or iPod Touch more secure. However the best security is abstinence. Just don't run the programs that leave your devices vulnerable unless you need them. The first half of this tutorial is for those w ...more
Previously, we talked about how to secure Firefox. Today, we will talk about securing a Chromium based Browser. Why? Because Chrome recently beat Firefox in holding more customers. It is obvious that Google Chrome tracks our every move online, so what alternatives is out ther ...more
Starting with the Priv, BlackBerry's become an Android manufacturer. This move gives BlackBerry's phones access to Google's sizable app store, but it also presents several hurdles to keeping the security brand they've built intact. For example, Android encryption still lags b ...more
The first step to getting your life together? Getting your online security together. After all, security when you're shopping, video calling, and more means more than ever in a digital age when anyone can copy your info or try to pose as you on the web. This Premium Privacy Bu ...more
When you first set up an iPhone, you'll be prompted to create a six-digit passcode to unlock your screen and access certain system settings. If you skip this step, you can always go back and create one, which we highly recommend. Without a passcode, everything on your iPhone i ...more
As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers a ...more
The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server. Shodan has been called the "hacker's search engine" because it's literally a searchable ...more
Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebo ...more
Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you ...more
If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs ...more
One of the best things about Android is the ability to customize every aspect of your device to make it your own. However, unless you have prior knowledge or experience with every single setting available to you, you might have missed a few critical features without even knowi ...more
There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help ...more
Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself ...more
Don't want one of your Facebook "friends" knowing your status updates? Prefer to keep a few of those "friends" out of your photo albums? Would you like to prevent a few "friends" from accessing your address? The simple answer would be to remove all of those so-called friends— ...more
We’ve all been there before. Relentlessly refreshing Ticketmaster and filling in those CAPTCHA codes only to receive the miserable “No tickets are available at this time” message. That’s because ticket brokers with a dozen screens and God knows how many browsers snatch up anyt ...more
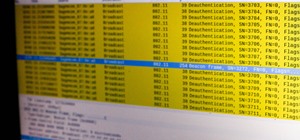
Does your network begin to crawl right around the time your sinister-looking next-door neighbors get home from work? Do you harbor suspicions that one or more of them may be stealing your Wi-Fi? It's easy to find out. And equally easy to give freeloaders the boot. In the guide ...more
You've all probably heard about Apple's attempts to thwart iPhone 4 users from opening up their own devices, thanks to their sly maneuvers in switching out everyone's screws with those funky pentalobular screws. But one thing Apple will never learn— they will never have comple ...more
Fire. It’s everywhere— always has been. From the Ordovician Period where the first fossil record of fire appears to the present day everyday uses of the Holocene. Today, we abundantly create flames (intentionally or unintentionally) in power plants, extractive metallurgy, i ...more
Nothing on the web is ever private. If you thought you can control your privacy, you were wrong. Websites may give you security options to better hide your information from the world, but ultimately your privacy resides in the hands of the website itself. We've seen how websit ...more
Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does ma ...more
Facebook is at it again. First they invaded your privacy with Instant Personalization, now they plan to take it a step further with their controversial plans to share users' home addresses and mobile phone numbers with third-party developers and websites. Due to user feedback ...more
Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to build a firewa ...more
This how to demonstrates how to use your Apple iphone as a spy camera to spy on others. If you're suspicious, paranoid or just downright creepy, this video can show you how to convert your Apple smart phone into a device for surveillance on others. Temporarily turn your iPhon ...more
Spammers are the bane of every email user. No matter what you do, junk mail always breaks through the spam filters. And some of the best ones seem to come from legit companies, and that's because they aren't legit companies— they're spammers masquerading as legit companies. W ...more
Do you remember "The Heist" from episode 21? Well, the sequel is even more unfair than the original! Check out this video if you want to stump people with a trick called "The Heist II." For this trick, you need only a few simple supplies: a match, a cup, and a nickel. From Re ...more
Social Profile Change the privacy settings on your social profile (Facebook, MySpace, Friendster, Twitter, etc.) so that the following information can't be found by a random person who you didn't accept you as a friend: Birthdate E-mail address Hometown Pictures A hacker ca ...more
According to Amazon.com, Kindle was their best-selling item this year, which means many, if not all of you are playing with a brand new Kindle on Christmas Day. Of all of Amazon's Kindle models, the Kindle 3 (6") will be the most common eReader in everyone's hands, either the ...more
The Motorola XOOM was just released last week to Android-hungry fans waiting the next best thing to Apple's iPad. But should it have been released, considering Verizon's switching to the 4G LTE network soon? From what I saw across Android forums, yes—because most could not wa ...more
What's the easiest way to keep track of your website passwords? Maybe in a password-protected document on your computer? Makes sense. But surprisingly, this is no easy task in Mac OS X. Snow Leopard does not have an easy one-click option for password protecting files and fold ...more
Health, safety and security are three main issues which determine if your cruise is a successful vacation. Health Health is a big issue because if one person gets sick, the entire ship can become infected. Gastrointestinal illness is the most common illness aboard cruise sh ...more
Someday, maybe not today, maybe not tomorrow, but someday, you'll find yourself on the road in your car, maybe on the highway, and you'll hear something. With your air conditioning on full blast and your stereo so loud your ears feel like they are bleeding, you normally would ...more
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to secure re ...more
For a moment, picture a situation where you want to host some files or images, but you do not want it traced back to you. Perhaps you're working on a project with others and need secure data storage. Anonymity is the new shield of the 21st century—and you best protect yourself ...more
You don't want anybody to have access to your cell phone. Nobody. Well, instead of the standard unlock mechanism, the one anybody can unlock your cell phone with, the Motorola DROID, and Android enable mobile device, allows you to create your own unlock pattern, secret to anyo ...more
iPhone and Android both have a lot of great features. Enjoy the best of both worlds when you install Android lock on your iPhone. This is a great way to secure your iPhone. Use Android lock to get an extra layer of security.
Not a great lock picker? Well, get some help figuring out how to break into padlocks and high security locks -- check out this video tutorial on how to open locks with comb picks. Comb picks are one of the best ways to hack into these common everyday padlocks. It's not a foolp ...more
In this how-to, Gary Rosenzweig of MacMost.com takes a look at best practices for making and storing passwords. You should have a different password for every account, for example, use secure passwords and store them in using a security utility. Learn how to store your passwor ...more
There is a vast amount of knowledge out there on computers! In fact, it is so vast that no single person could ever possibly ever learn everything there is to learn about hacking or computers in general. People usually specialize in a certain field: cryptography, computer secu ...more
Welcome to another Community Byte announcement from Null Byte! The goal of the Community Bytes is to teach people in a co-operative, hands-on manner. Learning from experience and immersing yourself in a subject is the best way to learn something foreign to you, so that is exac ...more
Dactyloscopy isn’t going anywhere. Forensic science has much relied on fingerprinting as a means of identification, largely because of the massive amount of fingerprints stored in the FBI’s biometric database (IAFIS), which houses over 150,000 million prints. And thanks to the ...more
This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing p ...more
This tutorial will let you hack into a wide selection of web cams and online security cameras. The hack is actually quite easy, and is best done with a browser like Mozilla Firefox. Navigate to Google in your browser, and then type in "inurl:viewerframe?mode+refresh". This pie ...more
You have an online store ready to go… almost. You still have to deal with getting the perfect shopping cart to go along with your e-store. Matt Winn from Volusion walks you through what to consider when choosing a shopping cart software for your online store. From what type of ...more
Having security setting on your web browser is a pretty important tool. It keeps you safe from potential hackers and makes sure you don't visit unsafe sites that could lead to a virus. But sometimes the security settings on a web browser can be a pain and the best choice would ...more
This video talks about protected mode for internet explorer 7 and Windows Vista. The person tells you that protected mode helps protect your computer from types of spyware. It is not the best solution and they tell you one should not rely on this alone. By default protected mo ...more
In this tutorial, we learn how to find an IP address in Hotmail. First, open up your Hotmail in box and right click on the email you want the IP address of. Now, select "view source" and find where it says "received: from" or "X-Originating IP". This will give you the exact IP ...more
AntiVirus Live is a fake antivirus software which comes onto your system and asks you to buy it. It doesn't provide any security to the computer. Here is the procedure to remove it: (1) disable the proxy server for your LAN in Internet Explorer. 2) download the process explore ...more
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to backup Wi ...more
A Self-Protection Guide 1) You can help protect yourself from violent crimes. Self-protection involves:Avoiding crime * Without a doubt prevention is your best prevention against crime.Knowing what to do in case of an attack* An attack can happen despite your best efforts to p ...more
You're sitting in front of your grandmother's Windows XP machine that has the worst infection you've ever seen. Safe mode? No dice. Restore points? They're compromised. Even worse, all of the files are hidden and none of the executables will run! This leaves her computer in a ...more
If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! mo ...more
Social engineering is described as the clever manipulation of the natural tendency of human trust. All of the passwords, locks, and encryption in the entire world are useless against a good social engineer who can charm or trick you into giving it up. But what once started as ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. More amazing community contributions this w ...more
This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last fo ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. Thanks to all of our active moderators and ...more
Introduction The 3 major anonymity networks on the Internet are Tor/Onionland, I2P and Freenet. If you feel confused on which one is the "best" one to use the answer is simple. Use all three! Each anonymity network is designed for a different specific purpose. One network al ...more