Apple just released the third public beta for iOS 14 today, Thursday, July 23. This update comes one day after the company released iOS 14 developer beta 3, and two weeks after the release of iOS 14 public beta 2. Apple released this update at 10 a.m. PDT. While we expected t ...more
Apple just released iOS 14 developer beta 3 for iPhone today, Wednesday, July 22. The update comes 15 days after Apple released the second developer beta for iOS 14, and 13 days after the release of iOS 14 public beta 2. Apple released this update at 10 a.m. PDT, the company' ...more
It seems like each day our phones become more integrated into our lives. School, work, shopping — so many tasks either require a phone or heavily benefit from one. But our phones are a double-edged sword that can easily distract us and harm our mental health as well. This is ...more
You don't need an obsessive ex stalking you to benefit from the ability to record calls on your iPhone in a pinch. Besides protecting yourself from nefarious intent, recording important conversations like verbal contracts and agreements can help you cover all your bases and en ...more
Two years ago, Facebook founder and CEO Mark Zuckerberg kicked off the F8 Developers Conference keynote with augmented reality and the introduction of Facebook's AR camera platform, now known as Spark AR. Since then, Facebook has faced an avalanche of controversy on its appro ...more
Silence spreads over these mountains like nothing I've ever felt. If I didn't have Moby blasting in my earphones, there'd probably be no other sounds around. Well, except for someone, Phil probably, murmuring in a nearby tent just low enough to make his words indiscernible. W ...more
If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding. Today we are going to explore some of the inner workings of Bitcoin. As we previously learned in th ...more
If you're using or need to use Zoom, the popular video teleconferencing service, you've almost certainly heard about "Zoombombing" by now. While Zoom has been adding security measures to address the problem, there are other things you can do to prevent or stop Zoombombers in t ...more
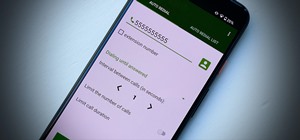
With so much of our personal data floating around the web, it's nearly impossible to get away from spam calls, texts, and emails. Unfortunately, this isn't just limited to the online world — filling in your contact information in a raffle ticket with the hope of winning that s ...more
Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all beca ...more
This year's big iPhone update, iOS 12, aims to solve many of the issues that arose during iOS 11's controversial, buggy tenure. With that in mind, it may be tempting to jump on board the new software immediately and leave iOS 11 in the dust for good. Here are some reasons why ...more
Electrical impulses course through our heart and keep it beating. That's why a jolt from an automated external defibrillator can boost it back into action if the beating stops. But new research says there may be more to keeping a heart beating than just electrical impulses. T ...more
The first sneak peak of Android O is finally here. The developer preview promises more features, stabilization, and better performance, according to the Android Developers Blog. Furthermore, there's speculation that the latest operating system will be code-named "Android Oreo, ...more
Startup promises to catch 100% of network attacks - Techworld.com. Startup TrustPipe is announcing a security platform that categorises network-based attacks and blocks them. The ...more
Trying to figure out which music streaming service to subscribe to can be a difficult task when the playing field is so crowded. Each has its benefits, as well as downsides, so finding the right one for your needs and wants can take a lot of overwhelming research. But we've do ...more
The problem with HIV is that it attacks and kills the very cells of the immune system that are supposed to protect us from infections — white blood cells. But a new technique, developed by scientists at The Scripps Research Institute (TSRI) in La Jolla, California, offers a di ...more
Welcome fellow Null-Byters! Sorry for the delay, this time of the year can be hectic for all of us. Hopefully this will not happen again. In this "tutorial" we will go over more styling and make our page look even better! In this "tutorial" we will be learning: Divs Aligning ...more
NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!! Hello Guys, Welcome to my first tutorial and in this tutorial we are basically going to create a port scanner in python ( I guess without external librarie ...more
Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself ...more
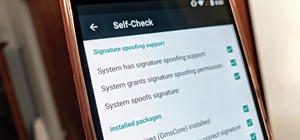
Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet. So no, there's no such ...more
Apple's scheduled to show off the first look of iOS 13 at WWDC 2019 on June 3, but what will the new operating system hold for iPhone? Rumors suggest that many features initially planned for iOS 12 will show up in iOS 13, codenamed "Yukon," and dark mode will be the big ticket ...more
Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of sk ...more
Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than othe ...more
Specialized cells in the lining of the gut may provide a key to preventing an infectious brain disease caused by misfolded proteins. Don't Miss: Syphilis: An Old Disease Returns with a New Drug Resistance We can easily imagine white blood cells attacking foreign germs in th ...more
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain. I figured, the more tuts the better, as I had trouble learning assembly in the beginning and had to read alot of tutori ...more
In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up. What Are Pointers and Addresses? A pointer is a type of variable which as been combined with the dere ...more
Signal is one of the best end-to-end encrypted messengers on the market. It offers robust security, keeps minimal information about its users, and is free to use. Switching to it as your main messenger can be a bit daunting, so to help, we created a guide to walk you through t ...more
Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers a ...more
Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear a ...more
With iOS 7, Apple is finally fighting back against spam, offering the option to block certain phone numbers from sending you text messages or iMessages (plus, phone calls and FaceTime too). With this new feature, you can block telemarketers, spammers, and their ilk from spamm ...more
It's September 1st, 1859, and the Earth looks more or less like something out of an apocalyptic movie or Sci-Fi novel. All communications have failed, it's so bright outside at midnight that people are getting up and making breakfast, and people all over the world are seeing a ...more
The Internet has had a huge influence on many areas of our lives, but, in particular, has resulted in nothing short of a revolution in the way we work. The web has offered the sort of flexibility to the individual that few people would have dreamed of just a couple of decades ...more
Apple's iOS 13 has been available for beta testing since June, and the stable release pushed out to everyone on Thursday, Sept. 19. To help you make the most out of iOS 13 for iPhone, we've rounded up everything you'll want to know, whether a colossal feature, small settings c ...more
While new features in Safari, Camera, Photos, Notes, Weather, Messages, and other Apple apps may steal the show on iOS 17, there are some impressive new features you need to know about when it comes to FaceTime audio and video calls. A step beyond mere upgrades, Apple nudges ...more
Apple's iOS 15.4 update for iPhone is out after 46 days of beta testing, and it has some exciting features you won't want to miss. Here's everything you need to know about the new software. The iOS 15.4 software has been available to developers since Jan. 27, 2022, and public ...more
Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-2 ...more
Infections with group A streptococcus, like Streptococcus pyogenes, claim over a half million lives a year globally, with about 163,000 due to invasive strep infections, like flesh-eating necrotizing fasciitis and streptococcal toxic shock syndrome. Distinctive substances on ...more
Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access ...more
Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time. FTP is a very important protocol. It's not only importan ...more
While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers di ...more
LP Smart Side Panels may seem like an easy product to install, and it is but there are some important thing to know and the best way to start these panels. Henry shows you how to do this and use blocking to ensure they are square and level. In some cases, building yards may ca ...more
You saw our post on the 18 coolest new features of iOS 7, but now that you've had a chance to play around with your updated iPhone, it's time to lock it down. There are a surprising number of new privacy and security-related issues in iOS 7's default settings, from allowing A ...more
The idea of a perfect phone is a myth. There are lots of pros when it comes to OnePlus devices, but there are also a few things that could be better. And even if there were a phone without flaw, there are still things that you might want to customize for personal preference. T ...more
There's a lot more to your iPhone's dialer screen than just entering phone numbers and hitting the green call button. It's not very obvious, but there are secret codes that you can enter on the dialer to find out information about your device, help troubleshoot issues, and mas ...more
Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to activ ...more
As our cells age, they eventually mature and die. As they die, they alert nearby cells to grow and multiply to replace them. Using a special imaging process that combines video and microscopy, scientists have observed the cellular communication between dying and neighboring ce ...more
Yep, Google just put in place a new thing called the dun dun duuuun .... "Device Catalog!" No, not like the Macy's catalog of your smartphone dreams. This is quite the opposite. After all those very exciting updates announced at I/O 2017, Google grandly let you all know that ...more
We all know we shouldn't be using our smartphones while driving. But we also know many people do it anyway. Soon, however, the addicts among us may not have a choice but to kick their habit. A new app announced today by Samsung will block all calls and texts while you drive, s ...more
Traditional root ad-blockers like AdAway and AdBlock Plus have no effect on YouTube anymore. Until now, if you wanted to get rid of the commercials that play before your favorite videos, there have only been two ways—either by paying for a YouTube Red subscription, or by using ...more
Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there i ...more
These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred. We vigilantly remember to lo ...more
So, here we are with the second part to whats going to happen to Minecraft in 1.7 (you can see the first part here). Let's start off with the new biomes. Biomes Roofed Forest: This biome is filled with short trees that are close together, forming a canopy. The trees have 2x2 ...more
Cases and stickers are always great, but they aren't the only way to customize an iPhone. The software on your device is full of customization options, from a better-looking home screen and cooler lock screen wallpapers to app icon changes and a system-wide dark mode. There's ...more
If you have a modern iPhone, you have an excellent video recorder at your disposal. Every iPhone since the 6S has the ability to shoot in 4K resolution, and each new iteration has brought new capabilities to the table. But even the best mobile shooter can use a little extra he ...more
Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website w ...more
In the last decade, the number of people working remotely in the US has increased dramatically, and so has their need for technology and software to supplement that remote work. Whether you work from home or a coworking office space, the requirement for highly compatible and h ...more
Some of the Pixel 3's coolest features are software related, which means you can get many of them on non-Pixel devices. "Flip to Shhh" is a perfect example of this. It lets you quickly put your phone into do not disturb mode by placing it face down, and this can be replicated ...more
The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python to ...more
Aircraft equipped with ADS-B are constantly shouting their location into the radio void, along with other useful unauthenticated and unencrypted data. In this guide, we will make an ADS-B receiver using a Raspberry Pi with a software-defined radio (SDR) dongle, which we can us ...more
By looking for the mechanism that allows influenza A to invade lung cells, scientists also discovered a treatment that might block the virus from taking hold there. An infection of the lungs is called pneumonia, which is caused by bacteria, viruses, and fungi that target alve ...more