The video demonstrates the way of calculating the interest rates for payday loans using MS Excel. The person presenting the video has got his MS Excel sheet with all the formulas and data ready. He first starts with the nominal & effect & future value tab. He gives us an examp ...more
Imagine you're in Paris and you need to get to Versailles. Looking around for directions, you come to a cold realization—you do not speak a lick of French! How are you going to get to Versailles and what happens if there is a detour? It will be a difficult struggle, and you'd ...more
In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then a ...more
Briefing Playing cards are used to play Killer but Killer is not exactly a card game. You cannot play this game if you do not know how to wink. I do not recommend that you go about winking at men and women to practice for this game. A minimum of 4 players are required to pla ...more
Sergio Peralta Advisor: Jessica Davis ER/QR incorporation 18 January 2012 Workshop plans My senior thesis is creating a poetry/autobiography writing workshop. I will help develop my student’s autobiographical skills through poetry. My target group is mainly 9th graders be ...more
Facebook unveiled a lot of changes last week, and, as usual, it's causing a lot of consternation and controversy. People within my Facebook, and on Google+, keep asking how to remove the ticker, and are trying, and mostly failing to make sense of the changes. I've decided to ...more
Let's say today is your birthday. You've just put those boisterous, vicenarian times behind you, reaching the first big step to your upcoming midlife crisis—30 years old. Maybe this is your midlife crisis. After all, if you're not where you want to be in life when you join the ...more
The DIY industry is booming, despite the desperate blackmailing of society by finance capitalists. Companies like Adafruit and Makerbot are grossing well over a million dollars a year, and Evil Mad Science Laboratories just recently dedicated themselves to running a full-time ...more
The video shows us how to find the area of triangles and other geometric shapes. First, before starting to find the areas, we need to know the basics of what do those shapes actually mean and we need a little bit of vocabulary to back us up. First, the parallelograms are four ...more
Everyone has used a ruler at some point in their life, whether for art sizing, blueprint plans, or sizing up your widescreen television on your living room wall. But there's a lot of little ticks on the ruler that you may not be aware of. Your ruler shouldn’t be used only to d ...more
In this five-part video, learn the art of stair-making. If your deck or porch needs a new set of steps, why not do it yourself? The StairGuide makes it easy to figure the rise and run of steps, and the nubbier of steps needed for a staircase. Building outdoor staircases is a ...more
When it's time to calculate a tip at a restaurant or bar, I usually try some mental math at first, but sometimes I resort to opening the Calculator quickly from the Control Center on my iPhone and doing a quick calculation. But with Apple's Shortcuts app, there's an even easie ...more
You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discove ...more
A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials. ...more
|Choose Your View: Quick Bullet Points | Detailed Descriptions Android's newest major update is a special one — it's the tenth full version of the world's most commonly used operating system. The latest release, dubbed simply Android 10 (codename Android Q), was first showcas ...more
When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we'r ...more
There is no iPad version of Apple's Calculator app, so you won't find it on your Home Screen, in your App Library, or as a shortcut in the Control Center. But that doesn't mean your iPad doesn't have an official calculator. Before the first iPad in 2010, Apple's development t ...more
Hello again, and welcome back to another tutorial on functions, this time, covering recursion. What Is Recursion? Recursion is the calling of a function within itself so that it repeats the process, kind of like a loop. Recursive functions are used in situations where a prob ...more
One of the most exciting additions to iOS 12 for iPhones is called Shortcuts, a tool integrated with Siri to help you get things done faster. While there are a few recommended shortcuts available to you in Siri's settings in iOS 12, the Shortcuts app brings the functionality o ...more
Whether it's for health reasons or just to look better, many of us want to get in shape. It's a long process that starts with nutrition, and dieting is never easy. Fortunately, there are some great food-tracking apps that will make it a lot easier to become a healthier version ...more
Hey there, reader! In this tutorial we are going to explain how values are stored in variables as either signed or unsigned. Try to not get lost! Everything is made up of bits in the computing world, like the atom makes up the basic building blocks of everyday materials such ...more
A hemisphere is sphere that has been cut in half. When you cut the sphere in half you are left with the great circle, plus half of a sphere. This fact can be used to find the area, and the volume of a hemisphere. The video works several example problems in which the area and v ...more
You can brew your own beer on the stove, in a keg, or even inside a pumpkin, but those all look boring next to The Wobbly Boot Pico Brewery, the most sophisticated home-brewing system you'll ever see. Built by Ben_B, an engineer at National Instruments, the brewery sits on a s ...more
It hasn't been long since Apple released iOS 16.0 with over 350 new features, but iOS 16.1 just came out with even more cool updates for your iPhone. While some of the recent upgrades were expected, others are somewhat surprising — and there's even one that you may not even th ...more
When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. Th ...more
A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hash ...more
While there are many ways to see the exact battery life left on your iPhone, you can take all the work out of it by making your iPhone verbally tell you the current percentage every time you start or stop charging it. Best of all, this trick works whether you use wired or wire ...more
How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a ...more
2 + 2 = 4. That's about as much math as I can handle without a calculator on a daily basis. I literally hate doing math more than anything in life, mostly because I'm not good at it—and I hate doing things I'm not good at. So, when I come across a cool math trick online that ...more
Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highl ...more
Google Lens can perform many different tasks with your smartphone's camera thanks to advanced machine learning, such as foreign text translations, landmark identification, and business cards to contacts conversion, to name a few. With this year's Google I/O conference, we have ...more
With iOS 12, Apple is making up for mistakes from the past, with iPhone batteries being no exception. The new update builds upon both battery health and performance throttling tools introduced in iOS 11.3 by offering users more information about your iPhone's battery usage tha ...more
In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM ...more
Tofu has been a staple food in Asia for over 2,000 years, but due to the health craze of recent years, it's enjoyed a surge of popularity in the Western world. Derived from the milk of soy beans and typically coagulated by calcium or magnesium salts, tofu can be found in consi ...more
Video: . IF function This article describes the formula syntax and usage of the IFfunction in Microsoft Excel. Description The IF function returns one value if a condition you specify evaluates to TRUE, and another value if that condition evaluates to FALSE. For example, the ...more
Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you. Rooting allows you to remove barriers and open Android to a level of unprecedented contro ...more
An invaluable button on your iPhone can do hundreds, even thousands, of amazing things, but most iPhone users don't even know it exists. You can't push it. You can't click it. You can't press it. But it's the largest button on your iPhone, more powerful than the versatile Side ...more
When people work out, they want to get the absolute most out of their routine. Going on a run is great exercise, but finding an optimal route that works best for you can be difficult. Luckily, Apple's ARKit has the capability to make it much easier to get the most out of your ...more
Learn to Zoom to page, drawing, selection, previous, 100% and scale by numerical factor using zoom tool in Xara Web Designer. The zoom to page option is great for when you need to see all the web design elements that are shown on your web page at once. For example, imagine th ...more
How much you've actually spent and how much you think you've spent are usually two completely different results, and is especially true on Amazon when it's so easy to click and buy. You might think you've given Amazon a couple thousand over your lifetime, when the fact is that ...more
Hello again, reader! In this post, we are going to cover some data types and how to declare variables. It shouldn't be too hard so just sit back, relax, grab some popcorn and enjoy the ride (while you still can!). What Is a Variable? For those who do not know, a variable is ...more
Eating healthy poses a challenge nowadays with so many options that taste great but aren't really good for you. Nutritionists have made it their life's work to understand what actually does a body good. Here's how you can follow their example. Cut Back on Added Sugar I spoke ...more
It may not seem like it, but the Status bar at the top of your Samsung Galaxy Note 2 is one of the most important and heavily utilized features. From checking the time, to finding out your battery percentage, to viewing Wi-Fi and cellular connections, the Status bar is critica ...more
Phones these days are expensive. The iPhone 11 Pro is presumed to start at $999, following the iPhone XS and iPhone X's leads. One way to bring down that cost is to trade in your old iPhone, but there isn't one clear-cut way to do that. You could trade your iPhone into a parti ...more
It's official — the newest version of Google's mobile operating system is called Android 8.0 Oreo, and it's in the process of rolling out to many different devices. Oreo has plenty of changes in store, ranging from revamped looks to under-the-hood improvements, so there's tons ...more
If you're a PC gamer, you know the value of performance metrics. These graphs and charts overlaid on top of a game give you real-time information about how well your system performs. And for the first time, Galaxy users running One UI 3.0 will get access to similar information ...more
It's a magical time of year for basketball fans, with the NCAA Tournament in full swing and NBA frontrunners in the midst of their push to clinch spots in the playoffs. To capitalize on the season, Magic Leap is making its own push, highlighting new features in the NBA app fo ...more
Business hours and addresses change, but they're not always updated on Yelp by business owners for the rest of us to see. Showing up when a business is closed or going to the incorrect address is a major annoyance, which is why the company allows us, the customers, to help upd ...more
Election Day is like the Super Bowl for network and cable TV news, so ABC News is breaking out the big guns with a new augmented reality experience to win over eyeballs of viewers. With all 435 seats in the House of Representatives, 35 seats in the Senate, and 36 governor off ...more
Gestures are a big deal on an iPhone X, XS, XS Max, XR, 11, 11 Pro, and 11 Pro Max. Without a Home button on Apple's super-premium smartphones, several actions had to be mapped to gestures instead, which impacts other areas of the system such as the Control Center. One exampl ...more
Most carmakers now agree with Waymo that piloting driverless cars is best left to the machine — with no meddling from the human. In Waymo's case, this assumption dates back years ago. More recently in 2014, Google's driverless arm (before it became Waymo) shocked Detroit when ...more
It seems like everyone is getting in shape these days (or at least trying to improve their fitness), and as a result, there's an endless supply of fitness trackers and smartwatches hitting the market. This is all very wonderful, unless of course, you're broke and can barely af ...more
Emojis have transformed the way we laugh and cry, tell stories, give responses, and express excitement to get a drink after work — without any actual text required. Heck, in an incredibly meta move, the Oxford Dictionary even named the "Face with Tears of Joy" emoji as their w ...more
Automation is everywhere in our daily lives. Faucets and hand dryers that turn on for you when they detect your presence. Automated teller machines to handle your bank account. Timed sprinklers to water your lawn every morning. DVRs to record your favorite TV shows when you're ...more
The integration of technology into automobiles is becoming more and more widespread each year. Tesla's Model S features a 17" display in the middle of the dash with navigation, music control, and even an Internet browser. Mercedes is working on incorporating Google Glass into ...more
You've just picked up your new Samsung Galaxy S20, S20+, or S20 Ultra — but wait. After you turn it on and restore your data, there a few apps you should install to get the most out of your updated phone. Installing these eight apps right away will help maximize your experienc ...more
The LG G7 ThinQ will likely be lambasted for its notch and awkward name, but one thing they seem to have gotten right is the new display. The G7 ThinQ will give many a first look at a new type of panel with lots of promise. While it was previously limited to TVs, from what we ...more
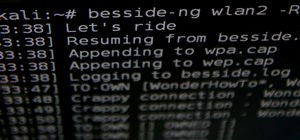
While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show y ...more
When a dead body is discovered, finding out when the person died is just as important as finding out how the person died. Determining the time of death has always involved lots of complicated scientific detective work and less-than-reliable methods. However, a study by Nathan ...more
Welcome to a tutorial explaining functions. This article will help clarify some things we have already been exposed to such as function prototypes, function calls, return values, etc. What Is a Function? A function is a type of routine which has its own defined set of proced ...more