The signal bars in your iPhone's status bar are great visual indicators for knowing how good your cellular reception is, but they're not very accurate. Instead of showing the actual amount of signal you're receiving, they just give you a general range, and you'll have no idea ...more
The gesture navigation introduced with Android 10 worked wonders by giving you more of your screen and less tapping. Android 11 offers the option to fine-tune the back gesture sensitivity for your screen's left and right sides. However, the issue still stands for people who li ...more
Knowing just one or two programming languages is no longer sufficient if you want to make serious money in the lucrative world of web design and development. But the good news is that you don't need to spend an excessive amount of time or money on a traditional coding educatio ...more
How much screen time is too much for a child? Should you let your children have a smartphone or tablet? What age is appropriate to introduce them to technology? These are just a few tough questions parents face. Research has shown that kids age 8-12 spend up to six hours a da ...more
Those of us who've taken the time to learn how to code are relatively well-suited for shakeups in the economy. Despite the recent and notable disruptions caused by the COVID-19 outbreak, demand for talented and trained programmers and developers is still high, and it will like ...more
It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks ...more
We've shared a capture-the-flag game for grabbing handshakes and cracking passwords for Wi-Fi, and there are some upcoming CTF games we plan on sharing for other Wi-Fi hacks and even a dead-drop game. While security-minded activities and war games are excellent ways to improve ...more
For developers and makers getting started with augmented reality, Intel is lowering the barrier to entry for its RealSense line of sensors. On Tuesday, Intel revealed the RealSense SR305, a short-range depth sensor available for pre-order at just $79. Don't Miss: Mimesys Bri ...more
Google has recently been pushing to replace the decades-old messaging technology we've been stuck with. SMS was never meant to handle the high-quality multimedia content we consume with our smartphones today, so in comes RCS, which is a universal platform that aims to change o ...more
It's no secret that the enterprise sector is hot for augmented reality, but the move into the enterprise AR software market by one of the biggest names in industrial engineering announces the technology's arrival loud and clear. On Monday, Siemens Digital Industries, the indu ...more
One of the biggest advantages of the front-mounted ultrasonic fingerprint sensor found on the Galaxy S10 and S10+ is that you no longer have to physically pick up your device and reach around the back to unlock it. Instead, you simply place your finger on the screen for easier ...more
Our national month-long celebration of all things creepy and crawly comes to a climax on Wednesday with Halloween and will end with Día de Muertos on Friday, so now is the ideal time for the The New York Times to publish a mildly chilling augmented reality story for children. ...more
Adding another arrow to its quiver of augmented reality acquisitions, Apple has reportedly acquired Spektral, a computer vision company with technology for real-time compositing (otherwise know as the "green screen" technique in broadcast TV and film). According to Danish new ...more
A new app for iPhones and iPads gives developers a sandbox for testing their AR experiences and sharing them with the world. Available now in the iOS App Store, wiARframe, a free app with no in-app purchases, enables developers to create their content via a web-based tool des ...more
As we predicted earlier this week, the focus has already begun to move from Magic Leap back onto Apple's rumored augmented reality smartglasses. The latest credible whispers come from none other than longtime Apple-focused analyst Ming-Chi Kuo. Boasting a long track record of ...more
The augmented reality and VR arm of Verizon, Envrmnt, wants to make it really easy for anyone to create AR apps. AR Designer is a web-based tool with a drag-and-drop interface that enables non-developers to import 3D assets, build ARKit and ARCore apps, and publish them to th ...more
Netflix currently lets parents block content based on maturity rating, but it isn't a perfect system. Not all titles rated PG-13 are equal, for instance. That's why it's good news that Netflix is adding more controls for parents, by allowing account holders to bar individual m ...more
Oreo, the latest and greatest Android OS, lets you enjoy a ton of new features such as app shortcuts and an improved keyboard. But thanks to a feature that's required of all phones that ship with Android Oreo out of the box, your S9 may be the first Galaxy phone to finally rec ...more
In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM ...more
The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnera ...more
From Instagram bot farms in China all the way to vending machines in Moscow that promise to sell you fake followers — the Facebook-owned empire is attracting the attention of the world around. When it comes to Russia especially, the country seems to be developing a little crus ...more
The Augmented World Expo (AWE) is upon us, and that means it's time to get excited about all the awesome next reality things to come. AWE is the world's largest AR and VR conference, and this year the event is dedicated to "Superpowers to Change the World." Pretty cool to thi ...more
Firefox Focus has been out for iOS for a while now, so it's about time Mozilla began porting the app over to Android. It's an amazingly private browser that protects you from trackers and ads when you're surfing the web. It blocks a wide range of online trackers, erases your b ...more
In the nascent AR/VR race, any release news is big news. For augmented reality, those invested in the new technology eagerly await the release of Microsoft's Hololens and any inkling of information that comes with it. If you're one of those folks, you're in luck, as new inform ...more
HTC is working on another flagship device that's expected to be released in mid-April. After the disastrous reception of the recently released HTC U Ultra and HTC U Play, this new model could be the true HTC 10 successor we've all been waiting for. VentureBeat reports that, a ...more
This morning, in an early morning session at GDC 2017, Brandon Bray, a senior program manager lead at Microsoft, revealed a mixed reality headset made in collaboration with Acer—a different headset than the one we saw from Acer at CES 2017 earlier this year. Also at the event, ...more
Snapchat has already found a compelling way to create advertisements in augmented reality with their branded filters, but they continue to experiment with new ways to monetize the bridging of the real and digital worlds. Their latest idea, which requires users to "snap" an ima ...more
As most of you know, I am a strong advocate for using Linux for hacking. In fact, I would go so far as to say that you cannot be a hacker without knowing Linux well. I laid out various reasons for this in my "Why Every Hacker Should Know & Use Linux" article, and I even have a ...more
Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow. Scenario Let's say, that we have done all the recon(both passive and active) and we have scanned the web serve ...more
Starting in Android 4.3, Google added some code to AOSP that tagged your internet traffic when you were running a mobile hotspot, which made it incredibly easy for carriers to block tethering if you didn't have it included in your plan. But as of Android 6.0, this "tether_dun_ ...more
What's up guys! It's time to discuss strings in more detail. Review Just a revision in case you have forgotten about what buffers (arrays) are. A buffer is a container to hold data which are adjacent to each other in memory (we have seen this in the previous tutorial on memo ...more
Hi Folks. This is my first post. I will teach how to create a server and client python reverse shell using sockets and python language. The script i'll post here is going to be very simple, and from here you'll have the possibility to adapt to your own purpose. For example, my ...more
When security firm Zimperium discovered Android's biggest security risk in years, it sent shock waves through the ecosystem. As a result, Google, LG, and even Samsung decided to change the way they issue updates to their devices, by pledging to release monthly security patches ...more
One of the many additions that appear on Android 5.0 Lollipop is a handy menu that lets users correct for or simulate different types of color blindness. While Google didn't flip the switch on this new feature until Lollipop was released, it turns out they had been working on ...more
Most custom ROMs are built from the freely-available source code of AOSP, so they share a lot of common ground with stock Android. The difference, though, is the fact that Google adds many minor tweaks and finishing touches to AOSP while creating the version of Android that ul ...more
If you're like me, then you've got an incredibly complicated Wi-Fi password with uppercase and lowercase letters, numbers, and special characters. When friends or family come over, it can be really hard to relay the password correctly. Repeating it out loud is usually hit or ...more
Apple is bringing one of the biggest updates ever to its Messages app, including a feature that will allow users to send audio messages back and forth with the press of a button. Goodbye, voicemail. While we've reached the third beta version of iOS 8 already, the official con ...more
In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent. It's been rulings like these and their call for internationally recognized rights to pr ...more
Confirming a lot of what we already knew, now we have a physical walkthrough video on HTC's new flagship, the M8. Or, maybe the "New HTC One", but let's hope that's not the name of the final product. Before we get to the video, here's what we already know: Dual rear cameras w ...more
Having instant access to monitoring your battery level is critical, especially when you're traveling or forget your charger at home. You need to know how much juice you have so you can adapt accordingly. If you have the featured enable on your Samsung Galaxy S3, you can quick ...more
It was just released a few days, but Facebook Paper has already taken the world by storm. CNET said it was a better way to use Facebook. TIME said it's the future of Facebook. The Verge called it the best Facebook app ever. There's one problem, though... It's only available f ...more
Ever since its introduction back in iOS 6, AirPlay has been helping us iOS and Mac users stream content over to an Apple TV or third-party speaker system. It's an incredibly useful feature. However, it's also severely limiting. The few compatible products out there are extreme ...more
The Xbox One is the quintessential jack of all trades. It can be your browser, music player, gaming system, and cable box, but in order to benefit from all of these goodies, you're going to have to set it all up. The below instructions are for setting up your TV and cable box ...more
Thousands of history files, cookies, other unwanted files stored in your system as logs and other formats. To manually check each one is difficult. New computers are too fast by processor behavior, after some times of working it comes to slow performance. After browsing it is ...more
Even if you have the fastest internet connection in the world, it's not going to be fast if your Android device isn't optimized to use all of the bandwidth. I have pretty fast speeds at home, but every now and then my web surfing on my Nexus 7 tablet is halted in its tracks—fo ...more
The new Samsung Galaxy S4 has something no other phone has ever had before—weather sensors. Older devices like the Galaxy Nexus, S3, Note, and Note 2 do have a atmospheric pressure sensor, aka a barometer. However, they do not have a thermometer or hygrometer like the GS4 does ...more
Even though iOS 6.1 was only released a couple of weeks ago, hackers released evasi0n a couple days after. Evasi0n, the only iPhone 5 jailbreak currently on the market, is the most popular jailbreak in history—with nearly 7 million iOS devices already hacked in the mere four d ...more
If you've ever logged on to the popular music application Pandora, your password is saved onto that computer in the local storage...for good. So for everyone reading this article, you should change your password to a throwaway one that's only used for Pandora, because if you ...more
The latest iPhone update introduces big features like Live Activities and Clean Energy Charging, but those aren't the only things you'll notice different on iOS 16.1. If you build your own shortcuts in the Shortcuts app, there are a few things you'll definitely want to know ab ...more
Spoofed phone calls originate from one source that's disguising its phone number as a different one, and you probably get these calls all the time. Maybe they're numbers from your local area code or for prominent businesses, but the callers are just hijacking those digits to f ...more
Apple's iOS 15.4 update for iPhone is out after 46 days of beta testing, and it has some exciting features you won't want to miss. Here's everything you need to know about the new software. The iOS 15.4 software has been available to developers since Jan. 27, 2022, and public ...more
Most websites and apps support two-factor authentication (2FA), which adds an extra layer of security to your accounts by requesting another form of identification beyond username and password. The second factor can be a recovery code, physical security key, or one-time passwo ...more
When smartphones were first getting popular, apps were much more limited in scope. Because of that, it was easier to find better programs to do what was needed. Now, in the App Store alone, there are nearly two million apps for you to choose from. When you're just looking for ...more
Apple released the fourth developer beta for iPhone today, Monday, Mar. 15. The update (build number 18E5178a) comes 13 days after Apple seeded developers the third 14.5 beta, and 12 days after public testers received their third 14.5 update. Apple released this update at 10 ...more
You take a photo or video, send it to a friend, and they say, "Hey, I can't open this." More often than not, your friend won't be using an iPhone, iPad, iPod touch, or Mac. Instead, they're likely trying to open the file with a non-Apple device. But this problem can be avoided ...more
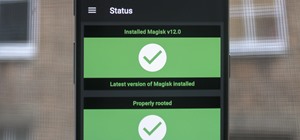
ADB and Fastboot are powerful tools that have always required a computer. But with the right setup, you can now send commands to a phone using another phone. The ADB and Fastboot Magisk module, by osm0sis and Surge1223, will turn your phone into an ADB terminal using root acc ...more
Yes, that's right: Instagram has a sneaky, inconspicuous, cryptic, hush-hush way to change its iconic, colorful icon on your Android's or iPhone's home screen and anywhere else it shows up throughout iOS. The app really outdid itself too, with 12 alternative icon designs from ...more
Identifying security software installed on a MacBook or other Apple computer is important to hackers and penetration testers needing to compromise a device on the network. With man-in-the-middle attacks, packets leaving the Mac will tell us a lot about what kind of antivirus a ...more
Wearing masks and social distancing doesn't sound like a fun movie night with friends, but you can still be comfortable and watch films together remotely. Services like Discord and Netflix Party make it possible to watch movies simultaneously from different parts of the U.S., ...more
Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the or ...more