At first, it may look like it's mostly a behind-the-scenes update, but iOS 14 public beta 6 is more than just that. The biggest addition to iOS 14 for iPhone in this version is the beginning of Spatial Audio, an AirPods Pro feature. Other notable changes in beta 6 appear in Ma ...more
At first, Apple's six developer beta for iOS 14 isn't much to look at, but there wouldn't have been an update if there weren't some important issues to address. Most of the serious updates in build number 18A5357e revolve around SwiftUI, which even has a few new features, and ...more
The response to the COVID-19 pandemic means that social distancing has become the new normal. It also means that more Americans are using video conferencing to connect with colleagues working from home or friends and family in quarantine because of the new coronavirus. In gen ...more
In the iOS 13.4 update, Apple added folder-sharing capabilities in the Files app. That means you can share multiple documents at the same time instead of doing it one by one. But that's not all — you can share folders with numerous contacts and even enforce access and permissi ...more
Things are a bit more organized in Apple Reminders, so the cluttered mess that it once was is no more in iOS 13. The slapped-together feel in older iOS versions was the main reason I never used it that much, but the updated version for iPhone has finally got me hooked. Aside ...more
Apple's Reminders app has always been an underrated yet useful productivity tool for iPhone. It's not as powerful as many third-party to-do apps, but it makes it easy to keep track of a few basic tasks, and it's integrated deeply with iOS, macOS, and watchOS. In iOS 13, it's e ...more
Although Mail didn't get a massive update in iOS 13, the new formatting and attachments toolbar makes it easier to stylize your messages and get quick access to files you'd like to send. It even includes the excellent document scanner built into iOS, so you can use your iPhone ...more
Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through UR ...more
Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to ...more
If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while i ...more
When your iPhone goes missing, it's serious business. Depending on your usage, your whole life might be connected to your iPhone, not the least of which includes debit cards, credit cards, and Apple Pay Cash stored in Apple Pay. While it's nearly impossible for someone to use ...more
Every photo you take is brimming with metadata such as iPhone model, date and time, shooting modes, focal length, shutter speed, flash use, and geolocation information. Share these pictures with friends, family, or acquaintances via texts, emails, or another direct share metho ...more
Apple may pride itself on its commitment to user privacy and security, but it isn't invulnerable. We now know there is a bug in the latest version of iOS 12 and iOS 12.1 beta that allows those in the know to bypass your passcode and access contacts and photos. This applies to ...more
You don't need an obsessive ex stalking you to benefit from the ability to record calls on your iPhone in a pinch. Besides protecting yourself from nefarious intent, recording important conversations like verbal contracts and agreements can help you cover all your bases and en ...more
The next big iOS version for iPad, iPhone, and iPod touch was revealed by Apple at WWDC 2018 and dropped for everyone on Sept. 17, 2018, less than a week after Apple revealed the new iPhone lineup. We've rounded up all the big picture items and secret features and changes we c ...more
We're nearly there — Apple released the seventh iOS 12 beta to developers Monday, August 13. While not totally unexpected, beta testers understand the struggle of predicting the next update, as Apple has switched haphazardly between two-week, one-week, and irregular release sc ...more
Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we ...more
You've protected your Ubuntu system from physical attacks, annoyed network hackers, and sandboxed potentially malicious applications. Great! Now, the next logical steps to locking down your OS include thoroughly auditing Ubuntu for weak points, using antivirus software that re ...more
There's a lot more to your iPhone's dialer screen than just entering phone numbers and hitting the green call button. It's not very obvious, but there are secret codes that you can enter on the dialer to find out information about your device, help troubleshoot issues, and mas ...more
Your email inbox is a treasure trove of personal data. The people you contact, your writing style, which messages you flag as spam — all of this information and more can be used to paint a clear picture of you. Google knows this as well as anybody, so they use this data to con ...more
Sure, emojis are all the rage, but there's not an emoji for every emotion or feeling just yet. That's where emoticons come into play, emoji's older typographical sibling. Unfortunately, emoticons can be hard to type out, easy to forget, and ASCII art, in general, can be pretty ...more
As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your sec ...more
When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your de ...more
So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use o ...more
In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or mis ...more
The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through ex ...more
When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was ...more
The coming year promises to be a good one for those of us watching the augmented and mixed reality world. And the Consumer Electronics Show (CES), starting Jan. 5 in Las Vegas, Nevada, for its 50th year, is bringing 2017 in with a bang—we're expecting a ton of great announceme ...more
When Microsoft release an update to the HoloLens Development Edition at the end of May, there were a bunch of cool new features added in. Among them: New voice controls that make working in the HoloLens operating system much easier. There are tons of new ways to interact with ...more
Hello friends. This is actually my first how to. In this tutorial I'll be teaching how to simply copy someone's WhatsApp pictures gallery into your computer, in an automated way. It is just an example of how easy is to steal data from someone's smartphone. I am covering Whats ...more
Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have ...more
Nice people finish first—or is it last? Though you may have been told throughout your life that being kind pays off, there are some obvious advantages to getting mean. So whether you're driving towards a goal at work, or need to attack a task in your personal life, acting like ...more
If you use Google Chrome as your default desktop/laptop browser, then Chrome OS will be pretty easy to get up and running if transitioning from Windows or macOS. Google has created an operating system that is fast, lightweight, and versatile enough to be adopted by pros and no ...more
If your iPhone can't last a full day without being recharged multiple times, something's wrong—but it might just be working harder than it needs to. So before you take a trip down to the Genius Bar, try some of the tricks out first to conserve your battery power throughout th ...more
Welcome back, my hacker apprentices! A you know, Mr. Robot is my favorite TV show this year, and not just for the realistic hacking. Rami Malek, the actor who plays Elliot, is incomparable in his depiction of a young man with social anxiety who is alienated from a superficial ...more
Update My sincere apologies guys, but I just got a call from Rackspace to set up my "managed account". After a long discussion, there is no longer an "un-managed" option. This means that there is a minimum support fee of 50 dollars USD tacked on to every account. The instruct ...more
hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack. ...more
No one wants to appear stupid. Whether you rely on lengthy, complicated vocabulary to show your smarts, or enjoy highlighting your speedy mental math skills, everyone prefers emphasizing intelligence over hiding it. Yet even the smallest, most normal behaviors in our day-to-d ...more
Apple prides itself on simplicity, but the company makes downloading video and music files onto your iPad or iPhone an overly complicated process, requiring iTunes and/or iCloud. You can listen to songs sent to you via email, but you can't download them onto your iOS device l ...more
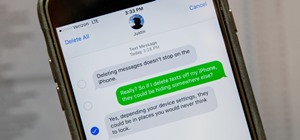
We've already shown you how to free up internal space on your iPhone, and now it's time to tackle another problematic storage issue—your iCloud account. Having an iCloud account is great for keeping backups of your iPad, iPhone, or iPod touch, and it's also handy for freeing ...more
The autocorrect feature in Apple's default iOS keyboard is anything but perfect. Sometimes it can't autocorrect things on your iPhone to want you want, while other times there's a software bug that just flat out gets it wrong. These autocorrect issues can get even worse thanks ...more
When I see the words "free trial," I know I'm probably going to have to whip out my credit card and enter in the number to "not get charged." Then I end up forgetting about the trial and want to kick myself in the ass when I see my statement at the end of the month. In order ...more
Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive. End ...more
If you've never heard of geocaching, it's kind of a grown-up treasure hunt you play everywhere in the world. GPS coordinates are given as clues and the players must find the cache box. There is usually a log book to write your name and a small toy or present to collect. The l ...more
A little-known setting on your iPhone gives you the power to change the color of certain contact names and email addresses when drafting an email. Customizing the color works well for visually separating contacts at a glance, and it can even help you from sending an email to t ...more
With the release of Object Capture this fall, Apple is giving everyone with a Mac and a camera the means to create their own 3D objects. But what about volumetric video, which currently requires multi-camera rigs like those at Microsoft's Mixed Reality Capture studios? One de ...more
Apple released the latest version of its iPhone OS, iOS 14.6, today, Monday, May 24. This latest update (build number 18F72) introduces new features like unlocking your iPhone with Voice Control after a restart, Apple Card Family support for up to five people, and subscription ...more
One of the best reasons to enter Apple's ecosystem is iMessage, where you can communicate more securely with other Apple users and send and receive chats across all of your connected iPhone, iPad, iPod touch, and Mac devices. While those blue bubble conversations sync across d ...more
One of the biggest bummers about Netflix is the inability to create different lists for your favorite movies and TV shows. Instead, you're only able to lump titles into the single default "My List," and that can be impossible to browse. It doesn't separate titles into categori ...more
We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, ...more
Apple added the option to install custom fonts and use them in different apps on iOS 13. The rollout has been a bit confusing, with Apple announcing partnerships with vendors such as Adobe, but also limiting the feature to work with only certain apps. Nonetheless, you can now ...more
Who needs a pen when you've got an iPhone? If you have a form, agreement, or contract that you need to quickly sign, you do it directly from iOS without the use of a third-party app. Using Markup, which is available in several native Apple apps, you can sign and send important ...more
My autistic son loves music. One afternoon, when he was nine, I downloaded GarageBand to his iPhone to help with the boredom of a long wait at a doctor's office. Instead of pacing or escalating into a meltdown, he spent the entire hour and a half practicing, learning, and comp ...more
Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attac ...more
You would think that recovering your smartphone or another important item that you leave behind in an Uber ride would be a simple process, but it can actually be a pain in the ass. You have to find out how to report it to the driver, hope the driver is honest, pay a fee, and c ...more
So, you're on the way back from a restaurant and realize you left your iPhone there, but you're late for a meeting and can't go back yet. You may as well kiss that iPhone goodbye, right? Not yet, as long as the right person gets their hands on it first. But that potential do-g ...more
Instagram has extensive tools built in for creating and editing posts and Stories, but there could always be more. Third-party apps can help you add photo and video effects for even more visually stimulating content, as well as create announcements, text-based images, and ever ...more
The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years. Now, as the story of the company draws to a close, we finally have some deeper insight into what exactly ...more
Cinemark may not be as big as AMC Theatres, but it also has a subscription if you want cheaper access to movie tickets. There aren't as many theaters, but if there's no AMC around you, there will likely be a Cinemark to save the day. But is the price of its Movie Club plan wor ...more
Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudul ...more