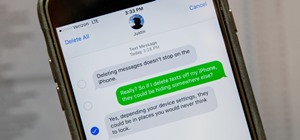
You don't need to delete an entire thread in the Messages app to get rid of a couple of texts on your iPhone. With a few taps, you can remove unwanted iMessages and texts, as well as storage-hungry photos and videos, to de-clutter a conversation. And in iOS 13, the process is ...more
Being organized is a big part of being productive. Keeping your important documents where they need to be is key to an optimized workflow. When using Google Keep, sometimes a note may outgrow its note status and you may want to upgrade it to a full on Google Doc. Thankfully, t ...more
For those with small hands, smartphones have gotten out of control as of late. Nearly every flagship phone is over six inches in length, so many are forced to use phones that are too big for them and hope they don't fall. Well, thanks to one developer, using these phones can b ...more
While you can now apply a dark theme to Samsung Messages thanks to One UI, you may want to further personalize your texting app. A great way to do this is by applying a custom font, which not only enhances the app aesthetically, but can also go a long way towards making your t ...more
Video calls are not only awesome for socializing, they're also handy for demonstrating a process or showing people what you're currently working on with your phone or computer's screen. Skype lets you do just that on both Android and iPhone in just a few taps. Besides having ...more
Does your iPhone always ring off the hook, with each call nothing more than a robocall, spammer, or scammer? It's not just you. Auto-dialing systems and phone scams are a growing issue that anyone with a phone number is likely experiencing throughout the United States. But App ...more
Typography is an important aspect of the video editing process. You deal with it when adding captions to news clips, giving on-screen recipes in food videos, creating burned-in subtitles for short films, making no-sound-needed videos for social media, and so much more. Enlight ...more
Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimat ...more
Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private cha ...more
With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network. After exploiting a system, penetration tester's and hackers will ofte ...more
If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a ...more
Android 9.0 Pie moved the status bar clock from the right corner to the left to accommodate phones with notches, but there's one major downside for Samsung users: since no Galaxy phones have a notch, all this did was take away space for the notification icons that would otherw ...more
Open TikTok, and you might find yourself spending hours watching video after video. While each video is usually pretty short, it's highly possible to binge-watch hundreds at a time. It's even more fun to create your own. But as a parent, you may not want your children falling ...more
While many of Facebook's tools are well received as they enhance the experience, one which is often complained about is the Marketplace. The Craigslist-like feature which offers a way to facilitate transactions between users can be a little overbearing with its alerts. However ...more
On Bumble, you only have 24 hours to connect with a match. If no message is sent, your match disappears and your chance of a connection is gone, but that doesn't necessarily mean that the other person isn't interested. If they lose their phone or don't receive notifications, t ...more
Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are ...more
As Samsung's very own take on Android 9.0 Pie, the newly-dubbed One UI (formerly Samsung Experience, and TouchWiz before that) comes with a slew of new features and redesigned elements for the Galaxy's interface. Many of the changes, like the redesigned native app icons, are r ...more
Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, ...more
With new iPhone models out, you'll have updated cameras to try out, a faster processor, and new colors to choose from. The only thing that could stop you from picking one up yourself is, well, your current iPhone. Here's how to check if you're eligible to upgrade to iPhone 11, ...more
For the second time in a row, Apple pushed out a new iOS 12 developer beta on a Monday, and for the first time this round, they've done it only one week after the last one. While the August 6 release of iOS 12 developer beta 6 doesn't contain a wealth of updates, there are sti ...more
Apple released the fifth developer beta for iOS 12 on Monday, July 30, only 13 days after the release of dev beta 4 and 12 days after public beta 3. Until this release, Apple kept a consistent two-week schedule for developer beta updates, so we were a little surprised to see t ...more
One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines conn ...more
As the official release of iOS 12 nears closer each day, Apple continues to update its betas. The company released the fourth beta of the upcoming software to developers Tuesday, July 17, exactly two weeks after the release of the third developer beta which came out just a few ...more
Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than othe ...more
When it comes to modding Android, there's no better tool than Team Win's TWRP custom recovery. You can use it to root your phone, flash mods like Magisk or Xposed, and even replace the entire operating system with a custom ROM like LineageOS — honestly, there's not much this u ...more
Apple removed the Wish List feature from the App Store when iOS 11 was released, which was a huge disappointment, to say the least. While the Wish List still remains in the iTunes Store, it seems gone for good for apps, but that doesn't mean you can't still keep a wish list of ...more
On April 3, 2018, Snapchat announced that the phone and video calling feature that's long been a feature of one-on-one calls would be coming to group chats. Well, late on Monday, April 17, the feature was finally pushed out to everyone for Snapchat groups on Android and iPhone ...more
There's a fine line between order and chaos in group chats. With all the cross-talk, threads can easily devolve into a random mess that has nothing to do with the original discussion topic. WhatsApp group chats certainly aren't immune to this problem, but they've recently take ...more
When you don't want somebody you're calling to know the real phone number associated with your iPhone, whether it's for privacy reasons, to avoid being called back, or to prevent being ignored, there are multiple things you can do to block it on their caller ID. Some of the b ...more
Recently, many manufacturers have started offering phones with a clean, stock Android UI. Motorola, Essential, Nokia, and OnePlus are probably the biggest names that have listened to user feedback and shifted more towards AOSP. But if your phone still has a bloated OEM skin, t ...more
Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website w ...more
The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems ...more
The iPhone X was released in November 2017, and the iPhone 8 and 8 Plus dropped right before it, but the hottest news right now revolves around the 2018 iPhone releases. The rumor mill regarding the iPhone X's successor started churning out speculations on names, cameras, disp ...more
Root, TWRP, Xposed, Magisk, custom ROMs — before you can have any of these, the first thing you should do is unlock your bootloader. Thankfully, the Pixel 2 and Pixel 2 XL are some of the most modder-friendly phones out there, so you only need to send a single fastboot command ...more
While unveiling various other gadgets, Google announced the Pixel Buds at their October 4th event in San Francisco. These wireless earbud-style headphones are particularly interesting thanks to their ability to offer real-time language translation via Google Translate when pai ...more
Typos are a constant annoyance that we all deal with thanks to the cramped touchscreen keyboards on smartphones. For many, nothing beats the feel of a good old physical keyboard when it comes to typing fast with minimal errors. Fortunately, WhatsApp has an awesome feature whic ...more
One of the most anticipated new Maps features in iOS 11 for iPhones is live and ready to keep you safe on the road. Right now, Do Not Disturb While Driving is opt-in, but if you missed Apple's on-screen prompt to enable it and want to turn it on, or if you accidentally enabled ...more
A fairly hidden feature in iOS 10 let you turn websites and documents into PDFs, but thanks to the new Markup function in iOS 11, this process has become a lot more streamlined. Not only can you save webpages, notes, and other files as PDFs for easy sharing, but iOS 11 even l ...more
The Instagram Explore page is one of the most useful tools available to users. It's also one of the easiest ways to discover new content and, if you use it right, to increase your own follower count. There are a couple ways for you to dominate the Explore page. One way is to ...more
As we've said before, Siri has some major competition moving into its own playground, and Google just announced at its I/O event that Google Assistant is available on the iPhone, starting today. It will be fascinating to see how Google Assistant's iOS variant fares on a syste ...more
Kik is an extremely popular messaging app, but it has a few annoying features that we all just sort of put up with. You can't turn off read receipts, nor can you hide when you're typing, and the photos you take with Kik's camera show up differently than ones you send from your ...more
Pot, weed, bud, herb – whatever you want to call it, the green earthy treat makes everything way more fun. Now that marijuana is legal to some extent in more than half of all US states, we thought it was high time to showcase some apps that enhance your experience with the con ...more
With smartphone makers ditching the headphone jack in the hopes of a truly wireless future, we're having to rely on Bluetooth devices like earbuds and headphones more and more. But the downside here is that these devices aren't physically connected to your phone in any way, wh ...more
Thanks to live-streaming video and social media apps like Facebook, Instagram, and Snapchat, we're all on camera nowadays. Unfortunately, though, we don't have a script to work with when we're shooting selfie videos, so it's hard to come off as perfectly eloquent when you're j ...more
With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Pyth ...more
As we reported first here on Gadget Hacks, the Google Pixel and Pixel XL have unlockable bootloaders, with the exception of models purchased from Verizon. This means that once the TWRP custom recovery is installed, you can flash ZIPs and even root your device in a few taps—as ...more
If you have any group chats going, you're surely familiar with this scenario: One person sends a picture, then, within 30 seconds or so, all other participants chime in with one-word responses like "Cute," or "Awesome." It's a social nicety, so you have to expect this behavior ...more
With certain apps and games, it's all about the settings. In order to get your money's worth with one of these, you simply have to take the time to tweak and adjust various options, which is something a lot of users don't necessarily want to do. Take GravityBox for example—th ...more
Greetings my fellow aspiring hackers, Its been a long time and I have to confess I would not be around for long as I am not free yet. I just have some few hours to spare and decided to help out. I learnt OccupyTheWeb won't be around to help out anymore which is like a slap in ...more
While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers di ...more
Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-d ...more
In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need Apache web server with PHP An image (included bellow) An email Account (I use gmail) Step 1: Setting Up Make a folder called "image.jpg" in your ...more
A lot of things have been changing over at Microsoft recently. Not only did they acquire the ever-popular Android keyboard SwiftKey and give away Windows 10 for free, but they've started a Google X-like experimental division called Microsoft Garage, and they've actually releas ...more
OK, In my last Tutorial we made a Server for sending Instructions to a Client. This time we will build the Client. Fire up your favourite Python environment and get the Code here. The Server Code ---Imports--- -socket is again for the connection -time is for pausing the Clie ...more
The stock Camera and Photos apps are great for taking basic pictures and doing some quick edits, but if you're serious about making your iPhone photos the best they can be, you can't stop there. The iOS App Store is filled with tons of great third-party alternatives with adva ...more
If you somehow forgot the pattern, PIN, or password that locks your Android device, you might think you're out of luck and are destined to be locked out forever. These security methods are hard to crack by design, but in many cases, it's not entirely impossible to break into a ...more
When you think of Terminal, you probably imagine some hacker sitting in front of their computer in a dimly lit room trying to break into an FBI database. In reality, it's just a simple tool that can make using your Mac much easier. Now, I'm not saying that learning Terminal c ...more
The telecommunications industry has come a long way since Ma Bell opened the first telephone exchange in the late 1800s. With the advent of fiber optics and wireless broadband technology, we no longer have a need for a dedicated phone connection, as today's data networks can c ...more
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started. OVERVIEW: As you'll get further into the hacking community, and learn more about how it's all put together, you'll also realize very quick ...more
Some third-party keyboards, like SwiftKey for example, include a convenient feature that suggests emojis as your type based on the content of what you're saying. Unfortunately, many keyboards, including most stock ones, don't include this function. It's often not a convincing ...more