This is an easy step by step tutorial how to lock your jewels in a hotel room or in a public safe. Be aware that in a public safe it is more secure to use the second method of locking by a magnetic card, not by a PIN code that can be easily seen by someone nearby. Video: . Ste ...more
There is thousands of motor driver, do you find an easy way to measure the drive current? That is what this motor shield do. The drive chip is L298N. The following steps is how to control two DC motors and how to measure the drive current. With it, you will make your control s ...more
Last week, the whole world ushered in the new year, celebrating the start of 2013 with family and friends, and of course, that little thing we like to call alcohol. But just because New Years Day is over doesn't mean the party is. And surely, there will be some assholes out th ...more
'Tis the season... for cheap (and free!) video games. THQ's Humble Bundle lets you get 7 games for any price you want, and now they're making it even better by offering fans a free Steam copy of Metro 2033 just for liking Metro on Facebook, which is gearing up for the latest M ...more
Want to take advantage of your neighbor's super fast Wi-Fi connection? If they're smart, they probably have it password protected (otherwise you wouldn't be reading this, would you?). But if you have an Android phone, you can get back at them for always parking in your spot an ...more
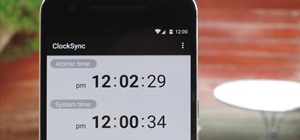
When you download files from certain apps like Safari and Chrome on your Mac, those files are tagged with the "Where from" metadata attribute. Depending on where the file was downloaded from, this attribute may refer to the host's URL, a sender's email address, or another piec ...more
According to a study done by Kaspersky, 7.6% of Android users root their phones. That may not sound like a lot, but with over 2 billion Android devices out there, the math works out to over 150 million rooted phones — more than the total population of Russia, Mexico, or Japan ...more
Lying is awesome. From a very young age, children learn that flat out denying the truth gets you out of trouble and helps keep you calm in the face of horror. But what happens when you just have to know if someone, say, used your toothbrush? You could ask them to take an expen ...more
How did it happen? How did your ultra-secure WPA password on your wireless network get broken into? Well, you might have just found yourself at the mercy of a cracker. Crackers are malicious computer users who specialize in breaking into things. Whether it be passwords, login ...more
We're officially seeking Null Byters on a weekly basis who would enjoy taking their time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (if up to par, of course). This is a job ...more
The Deauther Watch by Travis Lin is the physical manifestation of the Wi-Fi Deauther project by Spacehuhn, and it's designed to let you operate the Deauther project right from your wrist without needing a computer. That's pretty cool if you want to do all the interesting thing ...more
If you're ever in a situation where you need to take a peek at the wireless spectrum, whether it's for Bluetooth or Wi-Fi devices, there's a fascinating Python 3-based tool called Sparrow-wifi you should check out. It's cross-platform, easy to use, and has an impressive GUI th ...more
If you've spotted an unintended Ethernet connection and wondered what you could do with all of the information coursing through those wires, there's an easy way to hack into it and find out. Let's say there's a router that we need to know the password for, and we have physica ...more
When you're trying to get fit, friendly competition can go a long way towards keeping you motivated. Samsung Health has a great feature for just that, letting you challenge your friends or even complete strangers to bring some excitement to an otherwise routine workout experie ...more
With the same starting price as its predecessor and a nice list of improvements, the OnePlus 6T is a great buy for a number of reasons. But for many Android users, the main selling point for the latest OnePlus flagship is how easy it will be to root and mod the device. We jus ...more
Rooting a phone lets us install custom operating systems, known as ROMs, which replace the device's preinstalled OS. Most custom ROMs are based on code from the Android Open Source Project (AOSP), which gives them a look and feel similar to Google's version of stock Android. B ...more
No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks. Most iPhone and Android phones run on a Broadcom Wi- ...more
You're only as smart as your communication skills allow you to be, as other people will simply never know your inner genius if you can't effectively express yourself. Regardless of the medium—be it a Facebook post or even a simple text message—this fact remains true. When it ...more
Hi Message: I said quite a while ago I needed a break, and it looks like that break is over, because here I am. I dont want to ramble on unnecessary things that doesn't need explanation. I needed time off to sort something out irl, and i'll be returning slowly but surely now ...more
In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need f ...more
It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc. Kismet Although there are many tools that can grab and capture network pa ...more
Recently I've been looking around our wonderful community and I've seen some absolutely hands-down fantastic python scripting articles. But, in the end, these series weren't very extensive. I've been wanting to do a series on teaching python for a while now, and I don't mean j ...more
Hi guys, I'm gonna keep this short because I got assignments and a lot of notes to study and also other how-tos and forums to reads. lol...Since I'm keeping this short...no story time just scenario. And I want to thank n3stor for giving me the idea to post this. Scenario Let ...more
Hello fellow grey hat hackers, as hackers it becomes necessary for us to be able to send emails anonymously. Whether for whistle blowing or pranks or social engineering or whatever, it just is necessary for us to do that. So then I tried with python smtplib but then that requ ...more
Hello Hackers/Viewers, It is a new day, and you might be thinking, It is so boring, why not try to be cool with computers in front of my friends? That is why, I have made this tutorial to make fake viruses using notepad to look cool! Step 1: Requirements for the Prank First ...more
BlinkFeed completely changed the way I access new updates from Facebook and Twitter, but when I switched to the Google Play Edition of the HTC One, I lost access to the launcher. BlinkFeed is available in the Google Play Store, but HTC has not opened it up yet for all devices ...more
Mobile carriers have been the bane of my existence for as long as I've had a phone. First, they take away unlimited data, and then when you try and switch carriers, they hold your phone hostage for a up to a week before unlocking it from their network. There are services out ...more
Yesterday, the Free Software Foundation published an article written by Paul Kocialkowski. A software developer for the the Android fork system Replicant, Paul stated that his organization discovered, and later patched, a "backdoor" vulnerability that existed in older Samsung ...more
Sending and receiving files between Android devices has no shortage of options—Bluetooth, email, MMS, and Wi-Fi are just a few of the more popular ones that we use. While the choices for this functionality are plenty, problems can arise with connectivity issues and file size ...more
People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want ...more
You don't need an obsessive ex stalking you to benefit from the ability to record calls on your iPhone in a pinch. Besides protecting yourself from nefarious intent, recording important conversations like verbal contracts and agreements can help you cover all your bases and en ...more
One of the primary factors that separates an augmented reality device from a standard heads-up display such as Google Glass is dimensional depth perception. This can be created by either RGB cameras, infrared depth cameras, or both, depending on the level of accuracy you're ai ...more
There are hundreds, if not thousands, of programming languages and variations of those languages that exist. Currently, in the augmented reality space, it seems the Microsoft-created C# has won out as the overall top language of choice. While there are other options like JavaS ...more
A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials. ...more
Speakers today are a marvel for their portability and sound quality. No longer do we need giant boxes to bring down the house — a speaker that can fit in your hand can fill a room with your favorite music. This is even more important when you pair it with your smartphone, and ...more
Greetings my fellow aspiring hackers, Its been a long time and I have to confess I would not be around for long as I am not free yet. I just have some few hours to spare and decided to help out. I learnt OccupyTheWeb won't be around to help out anymore which is like a slap in ...more
Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the out ...more
Welcome back! In our last training session, we covered some advanced list topics. We'll be going deeper into the advanced list rabbit hole today with lambda and lambda operators! (And I'm not talking about Gordan Freeman) We'll start by explaining lambda and giving an example ...more
INTRODUCTION Hello dear null_byters here we go again with our third part of this serie. in this third part of our series I'd like to do a demonstration or continuation on fuzzing, but I think I should leave for later because the next tutorials about fuzzing will require from ...more
Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then. The idea is to write simple scripts ...more
Greetings My Fellow Aspiring Hackers, Its been long since I last posted a tutorial. Its vacation and since I won't be coming home, I've decided to use my day for sharing. I was browsing through old posts and found OTW's article - Hack Like A Pro: How to Find the Exact Locatio ...more
If you took a big step back and really looked at the world, you'd see how downright silly our nations look when they put up fences to separate themselves from one another. Creatures big and small roam free while respecting each other's space, but humans create borders and phys ...more
Why can't I see who is stalking my Facebook profile? There are other social networks that do let you see who's viewed your profile, mainly LinkedIn and its "Who's Viewed Your Profile" feature. Regular users can see a recent list of who has been spying on you, along with some ...more
TouchDevelop is a browser-based programming tool that allows anyone to build your own Windows 8 apps directly from any touchscreen device, including iPad, iPhone, Windows Phone, Android, PC and Macs. Once the script is created and the app proves to work, it can be placed in th ...more
Back in 2010, iOS developer Daniel Amitay developed a camera security app for iPhones that used an unlock screen almost identical to that of the iPhone. The app was removed in mid-2011 (though, it eventually reappeared in early-2013, still available in the iOS App Store today ...more
If you've never heard of geocaching, it's kind of a grown-up treasure hunt you play everywhere in the world. GPS coordinates are given as clues and the players must find the cache box. There is usually a log book to write your name and a small toy or present to collect. The l ...more
In a double-stuffed episode of Scam School, you'll learn how to fake ESP powers — a diabolical method to fake telepathy between you and a friend — and see a mind control trick from outer space with Scam School's first intergalactic student! The Setup To prove that you and yo ...more
The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user i ...more
Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of ...more
Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators. ...more
AppleScript is quite an easy scripting language to use. In this guide, I will be showing you several commands. Near the end, I will show how these can be used to create a fake virus that actually does no harm. Of course, this is only one way to use these commands—use your ima ...more
Identifying security software installed on a MacBook or other Apple computer is important to hackers and penetration testers needing to compromise a device on the network. With man-in-the-middle attacks, packets leaving the Mac will tell us a lot about what kind of antivirus a ...more
With just two microcontrollers soldered together, you can inject keystrokes into a computer from a smartphone. After building and programming the device, you plug it into a desktop or laptop, access it over a smartphone, and inject keystrokes as you would with a USB Rubber Duc ...more
Managing your busy schedule just got easier in Entourage 2008 for Mac. Using the powerful Entourage Calendar feature lets you organize your time wisely. The Microsoft Office for Mac team shows you just how to organize your schedule with the calendar in this how-to video. The ...more
The first day of Hanukkah is here, the day you start lighting the candles of the menorah. So, why not ditch the wax and light the "lights" this year? (Skip ahead to see the LED menorah) Hanukkah is a Jewish festival that lasts eight days from the 25th day of Kislev, which th ...more
Zynga games has released their ZLotto feature that you can use to get exclusive prizes for FarmVille, Mafia Wars, YoVille, PetVille, and FrontierVille! In this guide I will discuss all the aspects of this feature, how to use it, and some tips for success. Game Prizes FarmVi ...more
Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webm ...more
HipHop for PHP is a source code transformer that allows you to optimize your PHP code easily, which will allow you website to run faster on less server space. This video is a record of a seminar on using HipHop done by a Facebook employee who had a hand in it's development. If ...more
This video shows you how to use Script Assist to add ActionScript 3.0 to your FLA file. You learn about some of the core ActionScript concepts, such as events, functions, properties, and listeners, while you add code for a button. The button you create plays a movie clip after ...more
Computer viruses are terrifying. They are undetectable, dangerous, and operate constantly right under your nose. For the average computer user, there are only a few repair options. You could buy expensive antivirus software that causes more problems than it fixes, you can wipe ...more