In the first part of this series, we looked at the surface detection that is provided by the ARKit. We looked at how it worked and covered some of the tools that could help us determine what is not working; when it doesn't. Now let's take this to the next step. Before we can ...more
Aspiring engineers, your challenge, should you choose to accept it, has been issued by Jaguar Land Rover. Prove yourself and you can be the next in line for greatness. — Jaguar That is the challenge posed by Jaguar as they attempt to find the next generation of the best and ...more
WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still! The messaging giant added an encryption to iCloud backups to prevent a data privacy breaches loophole. This coul ...more
Your Android phone could be listening to ultrasonic ad beacons behind your back. The unwelcome news comes year after app developer SilverPush promised to quit using its (creepy!) eavesdropping software. But it looks like the privacy-threatening technology — which can track us ...more
UPDATED 5/4/17: SI has stated that they won't be augmenting its Swimsuit Edition. Although, this could be a sign that the company may do so in the future. If they already have all the tech set up for the latest feature, then they are already half way ready to augment other SI ...more
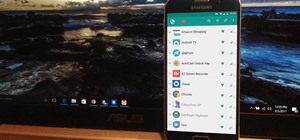
Before the release of the Galaxy S8, Samsung quietly uploaded one of their core TouchWiz apps to the Google Play Store as a beta. Samsung Internet, as it's called, has been a staple on all Galaxy devices for years now, but you can now try the browser on any Android phone. Aft ...more
This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document: Step 1: Creating the Payload For this tutorial, I'll be using a pyth ...more
Note: a bug was found in the Insertion Sort implementations. The bug was corrected in each language. Please refer to the pastebin links for the most up-to-date versions of the sample code. Any screenshots may be behind. More about the bug can be found here. Hello World! Today ...more
Welcome back, NB community, to my series on sorting. I introduced in my last article the concept of complexity. When I say complexity, I'm talking about time complexity. What Is Time Complexity? You can view the Wikipedia article here, but I'll be speaking from my heart and ...more
Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hid ...more
Welcome my aspiring hackers and programmers! Today i will introduce you to a programming language that as a hacker you should have in your set of hacking/programming skills (except if you're only interested in web hacking/programming...then you should go learn some html or PH ...more
How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implicati ...more
Hello again, and welcome back to another tutorial on functions, this time, covering recursion. What Is Recursion? Recursion is the calling of a function within itself so that it repeats the process, kind of like a loop. Recursive functions are used in situations where a prob ...more
So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - byp ...more
Hello readers, in this tutorial, we will be discussing how to perform file operations such as reading and writing. Types of File Access There are two methods of accessing files: file descriptors and file streams. We will be learning about file streams because it is a higher ...more
I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I ...more
Hello again! In this tutorial, we are going to go over something called "operators" which will help us build upon conditions of control structures and also some variable manipulation. Without further ado, let's dive in! What Is an Operator? Operators are special symbols whic ...more
If your smartphone is ever lost or stolen, it's a terrible experience. If you file a police report, chances are the responding officer will need your device's IMEI or MEID number if you want to stand a chance of getting it back. Same goes for making an insurance claim on a los ...more
Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post. Let me introduce myself first ! I am from Greece, I am working as a network engineer and I am into system and network administration but definitely ...more
Microsoft's "Fall Update" to Windows 10, code named Threshold 2, has a lot of new tricks up its sleeve. It's the biggest update we've seen since Windows 10 was released this summer, and it's rolling out to all users right now. Don't Miss: All of Our Windows 10 Coverage If yo ...more
Want the next level security? Well then take a read here because this is some next level stuff. Heard of It? There's a new app called Signal that has just been released, and people are shockingly surprised over its features. It is said to keep prying eyes including NSA & Gov ...more
Manufacturers like Samsung and LG have added their own implementation of multi-window features to Android for years now, but with the release of version 6.0 Marshmallow, Google has finally gotten around to working the same feature into stock Android. Don't Miss: How to Enable ...more
Hello dear friends! I'm jgilhutton and I want to show you guys a Python wrapper I made a few months ago. It's name is Pyxiewps and uses pixiewps, reaver and airodump to retrieve the WPA password in at least 9 secods! (Best case scenario) It takes advantage of the pixie-dust v ...more
It's been a while, since I have just started High School. I have put a hiatus to my pentesting for a few weeks, and now, I am making a return. I have taken time to read about code, (even did a research article analysis on how humans can write "beautiful" code and something li ...more
Video: . Being one of the most popular DIY/maker projects around, Musical Floppy Drives are nothing new. However, myFloppyDriveOrchestra includes a few unique features, which separate it from the crowd. FPGA - by implementing the drive control on an FPGA, I have effectively c ...more
If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achi ...more
Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If th ...more
Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop. Today's Topic Today we are going to complete t ...more
YouTube's main player interface got a pretty big makeover recently, but chances are, the new UI hasn't made it your way just yet. Google has a habit of slowly testing the waters as they roll out new features, so cool tweaks like this can take some time to reach all users. But ...more
With Apple's Yosemite build of Mac OS X came Continuity, a feature that has allowed us to connect our mobile devices to our computers, letting us access apps, send text messages, answer phone calls, and more while seamlessly switching from one device to the other. Pushbullet, ...more
First, I want to give credit to the author where I first found how to do this: Astr0baby's Blog. This article was dated, so I took the script on his page and reworked it to make it work today. (I also included the way to make it hide the cmd line popup.) Requirements Kali (or ...more
The Snapdragon 801 processor inside the OnePlus One puts the device on par with other phones like the HTC One M8 and LG G3 in terms of power and speed. While the OPO is just as fast and responsive as many of the flagships currently available, there's no reason why we can't try ...more
With all of the different websites we use in our day-to-day lives, keeping track of our numerous login credentials can start to become a hassle. This has created a market for password managers that aim to centralize these account credentials and generally streamline the proces ...more
Losing your phone is a much bigger ordeal today than it was just 10 years ago. Our smartphones carry with them lots of sensitive data that, in the wrong hands, is capable of being used for identity theft and fraud. One of the smartest things you can do to help avoid such a di ...more
I don't know of a pain greater than of the one felt after cracking the screen of your phone. After I managed to crack my screen, rendered unusable, I immediately began to panic as to how I was going to recover all of the photos, videos, and documents stored on my device. After ...more
In 2012, VideoLan published a beta release of their wildly popular desktop media player, VLC, for the Android platform. However, because the non-profit development team did not have access to popular North American Android devices, they opted to exclude the USA and Canada from ...more
Unless you've been living under a rock for the past few weeks, you're probably well aware that the Android world has been buzzing with excitement over the recently debuted Android L preview build that was released for the Nexus 5 and Nexus 7 at Google's I/O conference. This i ...more
While some mobile sites have built-in text-resizing tools, many do not. A lot of those that don't won't even let you pinch-to-zoom. That makes it difficult for people with low vision to read small fonts on their iPhones. In some cases, like with photo captions, even those with ...more
We got a fairly extensive look at the newest version of Android at Google I/O yesterday. The "L" version, which we're betting stands for "Lollipop", brings Google's new design philosophy to Android, and one of the main aspects of that design are new "heads up" notifications. A ...more
Whether you're a celebrity or someone with something to hide, Facebook allows you to keep your "friends list" private so you can protect the identities of your Facebook friends. But it only kind of protects them. There's a simple Facebook hack that lets you unravel entire net ...more
A few days ago I finally finished my 2 week journey into trying to get OpenVas to work properly. You all may have noticed that you can't just click the setup openvas in kali and have it working properly. I scoured the Web till my finger's bled and I no longer had fingernails ...more
Google's new camera, aptly named Google Camera, has been all the rage since it was released onto Google Play last Friday. The main reason is the amazing Lens Blur feature that adds depth-of-field Lytro effects to photos, without the use of any expensive accessories or extra ha ...more
Samsung's TouchWiz skin gets a lot of flak for its appearance, namely the garish colors on the quick settings toggles. The bright green on dark blue scheme is definitely an eyesore compared to the ones in stock Android, and even other manufacturer skins like HTC's Sense. It a ...more
Fresh off the heels of their latest agreement, Google and Samsung may soon be further aligned in their mobile technology outlook. The two tech giants signed a cross-licensing patent agreement, but that doesn't mean that Samsung was just going to start putting out stock Android ...more
Keeping unwanted clowns off on my Samsung Galaxy S3 is priority number one. I've shown you how to snag a picture of people opening your apps and how to lock your screen for whenever you hand off your phone, allowing them to access only the page you left open. Well, with App L ...more
I know it's a very first-world problem, but I really can't stand it. Email was invented to speed up communications between people across the world, even just across the office, yet when I'm on my super awesome iPhone running iOS 7, I have to go back and forth between my galler ...more
Most hardcore Android fans loathe carrier or manufacturer additions to the Android operating system. Whether it's bloatware or changes to the user interface, many enthusiasts prefer the clean look of stock Android. However, you have to admit that some of these additions are a ...more
Recently, I wanted to share a large video file from my Nexus 7 to my friend's Samsung Galaxy S3, and even though he was standing right next to me, it was an extremely difficult and frustrating thing to do. Every single Nexus 7 tablet comes NFC equipped, so it can share files w ...more
I'm not lying when I say that my iPhone is at my side at all times, and is really one of the best devices I own. My second favorite gadget would be my PlayStation 3, however, when it comes to browsing apps like YouTube, it's pretty terrible. Thankfully, I can take the awesome ...more
You've probably noticed how we like to stress the importance of a strong password. After all, there are still people out there who continue to use passwords like 123456 and even just "password". But passwords aren't the only barriers that protect your information. According t ...more
It can be extremely frustrating when you've forgotten the pattern you use to lock your smartphone, and even more so if someone has managed to prank you by changing it. Luckily, there's an easy fix if you know the username and password for the Gmail account you used to set up t ...more
There is something special about a secret knock. It gets you into secret super villain meetings and is a surefire way to test for rotating bookcase passages. Secret knocks usually work with an intimidating drug lord and for policeman listening at the door for the correct patte ...more
Since 2020, you've been free to set your preferred web browser and email app as the default on your iPhone or iPad. Now, four years later, Apple is expanding this flexibility in the U.S., allowing even more apps to be set as defaults for specific actions. Plus, there's now a c ...more
Android has a new security feature that every Android smartphone user needs to start using — even you. It won't change how you use your phone, but it will make life harder for nearby thieves. One of the oldest tricks in the book of smartphone thieves is watching someone withi ...more
There's only one thing keeping hackers, thieves, law enforcement agencies, and maybe even the people you thought you could trust from breaking into your iPhone should they ever get possession of the device. Their odds of bypassing that thing are pretty good, but there's an eas ...more
The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this ine ...more
Your iPhone just went missing, and now you're panicking. You need it for work, to get around, to contact your friends and family, and pretty much everything else in your life. So, what are the chances you might get it back? The odds may be stacked against you unless it's just ...more
MoviePass was once the best subscription service on the market for getting cheap movie tickets. For the price and the number of films you could see and save money on, it was unbeatable, but recent changes to the service have made it less enticing. While it still works well for ...more
Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, w ...more
While hackers adore the command line, working with the GUI (graphical user interface) of an operating system has some advantages. This is especially true when it comes to post-exploitation. When we can control the mouse and keyboard of a remote computer, we can truly say we ha ...more