Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, a ...more
With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone. Virtual Network Computing, be ...more
People have asked: "Here is an IP address. Can you hack this? Can you hack me right now?" Hacking takes time and skill. You can't just get an IP or an email and hack it in ten minutes unless the password is 1234. I say, "No. I can't really do what you want me to do like this ...more
Most of you probably heard about Rasberry Pi and if you haven't; what is wrong with you? But nothing less a Rasberry Pi is a computer a very small computer. Despite these size limitations, the Rasberry Pi is to not be underestimated. Not only can it do anything like a normal l ...more
Recently, there have been some questions regarding networking popping up and we have decided to put together this series to try and cover this gap. In this guide, we will cover the basics of IP addresses, both internal and external, and begin to have a a look at how this wond ...more
The NSA's massive internet spying efforts will continue. In President Obama's latest press conference, he went public to (in so many words) say that the NSA's spying efforts will continue uninterrupted. This, coming just weeks after the Amash Amendment which would have defund ...more
Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified. This attack assumes the Wi-Fi password to the ...more
The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be ...more
Hello ladies and gentlemen, welcome back to the Part 2 of our UDP & Wireshark adventure as I promised. Last time we discussed about what DNS is and how it uses UDP as its transport protocol but we left some unexplained parts behind and I'm about to investigate those with you. ...more
This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Pa ...more
Samsung's One UI 3.0 skin is built on top of Google's Android 11 open source code base, which means you get all of the standard features, plus some cool bonus stuff from Samsung. However, it's one of those standard AOSP features that you might find most useful if you send a lo ...more
It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to interce ...more
Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with ...more
Screen mirroring software has been around for ages, allowing you to mirror your iPhone to a projector, laptop, TV, or another device. It's useful to have during lectures, presentations, and meetings, so it's no wonder why Apple created its AirPlay technology. However, AirPlay ...more
Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website w ...more
Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself ...more
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account? WARNING - geeky stuff ahead! Quit now if sleepy :D You cannot imagine how much of hidden stuff happens when you press your login ...more
You need a good microphone on your computer in order to make audio recordings, voice chat, or use speech recognition. However, not every computer comes with a built-in mic, and not every built-in mic works great. You can purchase a cheap computer microphone on Amazon for as l ...more
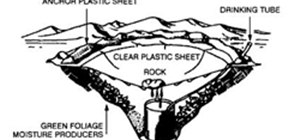
If you took a big step back and really looked at the world, you'd see how downright silly our nations look when they put up fences to separate themselves from one another. Creatures big and small roam free while respecting each other's space, but humans create borders and phys ...more
It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept. In bot ...more
In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the ...more
Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensi ...more
There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take c ...more
The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centere ...more
If you need to do some hardcore multitasking on your Windows PC, a second monitor can go a long way towards getting things done. If you opt to "extend" your Windows desktop across a dual monitor setup, it's as if you have two computers side by side, with each display getting i ...more
Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machi ...more
Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on ...more
As a hacker or an aspiring one, You need to be careful and anonymous if your doing anything illegal. But you slipped up. Now someone is tracking you! Well luckily you read this post ahead of time and have a backup plan! The first step in remaining safe is to remain anonymous. ...more
Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter ...more
The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, ...more
APOLOGIZE Hello my masters and colleagues, first of all I would like to apologize for my absence during the past month, to say that i was busy with some projects and decide to leave the white-side for a while and made some visits on the dark-side(every good COP has a dealer f ...more
PirateBox is a great way to communicate with others nearby when cellular and Wi-Fi networks aren't available. With it, you can anonymously share any kind of media or document and even talk to one another by voice — without being online. However, it needs a Raspberry Pi, which ...more
Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your sys ...more
The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python to ...more
In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greetin ...more
Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wou ...more
Welcome back my fellow hackers. Today I'm going to teach you how to preform an Idle Scan. You may be asking what is an Idle Scan. Its a very stealthy scan because you don't use your own ip you use a zombie (in computer terms). Heads up. If you are root you don't need the sudo ...more
Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?" As the hacker is among the most skilled information technology disciplines, it requires a wide knowledge of IT technologies and techniques. To truly be a great h ...more
For the most part, transferring files from your computer to your Nexus 7 (and vice versa) is a simple process. Just hook up your tablet to your computer with the USB cable and transfer. However, most of the time you'll need additional software on your computer to do this, and ...more
Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone ...more
Five Phases of Hacking:- The five phases of Hacking are as follow: Reconnaissance Scanning Gaining Access Maintaining Access Covering Tracks The Five Phases of Hacking Reconnaissance:- This is the primary phase where the Hacker tries to collect as much information as possib ...more
From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run AD ...more
Hi there, Elites Welcome to my 6th post, This tutorial will explain how to hack windows, using a program (No-IP) and windows's inbuilt Task Scheduler. Meanings... Task Scheduler: It is a program, inbuilt in windows, which allows us to create some tasks and execute them at s ...more
I still remember when I had to get up from my comfy spot on the couch to change the channel on my old television. So for me, the remote control may be one of the most underrated inventions of the last century. These days, remotes take on all sorts of shapes, not just the typic ...more
Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the b ...more
One of Android's most glaring weaknesses is its lack of an iMessage equivalent. That is, of course, until now. There's one app that will allow Android users to experience iMessage on their non-Apple phone, complete with end-to-end encryption, message effects, and group messagi ...more
Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn ...more
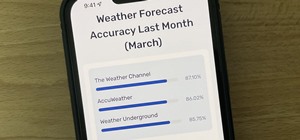
These days, if you're having friends over, they'll probably ask to log into your Wi-Fi network before asking for a drink. But if you've forgotten your password, it can be quite hard to find, since most devices obscure the characters with asterisks. But it honestly doesn't tak ...more
Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you ...more
Part 1: What is Popcorn Time? Part 2: What is a torrent? Part 3: Why am I at risk? Part 4: What is a VPN? Part 5: Are all VPNs the same? Part 6: How do I stay protected? Part 1: What Is Popcorn Time? Popcorn Time is, essentially, a torrent client (look to Part 2 for further ...more
NFC, or near-field communications, is a hardware feature that has been built into most Android phones for the last four years. It's essentially a low-power data connection that can be used to initiate a quick command by bringing your device within range of a compatible receive ...more
Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can l ...more
Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an a ...more
With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network. After exploiting a system, penetration tester's and hackers will ofte ...more
With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative. Ruby is just one wa ...more
While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on y ...more
Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elli ...more
Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will. Torrent clients like uTorre ...more
The release of iOS version 8.1.1 brought some much needed bug fixes to Apple's mobile operating system, but with it came a patch for Pangu's jailbreak method, which worked on iOS 8.0 to iOS 8.1 using a Mac or Windows computer. Luckily, it didn't take very long for a new team o ...more
There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture hands ...more