This tutorial shows you how to break into a digital safe. The technique uses a design floor in the safes often found in hotels or homes. Turn the Dial the Wrong Way The first step is to find out which way the dial should be turned. It is usually clockwise. Then turn the dial ...more
If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unus ...more
Learn how a Master Lock known as a "safe" lock can be opened using a few simple items.
Safecracking is something that most of us will only come in contact with in the movies, where strange men and women stick their head against safes and twist dials until the safe magically opens. If your interest in gaining entrance to safes that aren't yours goes beyond that, ...more
Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital ...more
We've reached the point in the trajectory of augmented reality's growth where AR advertising experiences are becoming commonplace tactics rather than rare experiments. Some of the more impressive examples of AR ads to emerge recently come from Hulu, Coinbase and Ray-Ban via S ...more
Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to ...more
Mechanical locks have been around since ancient Egypt, with the oldest known artifact found in the ruins of Nineveh, an ancient city in Assyria, Mesopotamia, which is just across the Tigris River from what is now Mosul, Iraq. It was a forerunner to our modern-day pin tumbler ...more
This video won't show you how to crack a safe but it will show you the next best thing: cracking a combination lock or master lock! We do recommend only trying this on a lock you have forgotten the combination to and not other unlawful purposes. Watch this video tutorial and l ...more
First of all, please DO NOT attempt to open any power supply and tweak what's inside unless you know what you're doing and/or are a professional. With that said, this circuitry video will teach you how to crack open a wall transformer power supply without destroying the transf ...more
There's nothing more tedious, yet exciting, than watching surveillance cameras at work. They prey on the innocent and the unknowing. They protect businesses, workplaces, and homes. They catch criminals in the act, find hilarious anomalies, and are just darn cool when you're no ...more
Whenever we make a homemade circuit, we use what are called through-hole components. Any components with long metal leads is a through-hole component. They are great for soldering to, but it's tough to fit enough through-hole resistors and capacitors into a smartphone. To get ...more
When you don't have time to do it the right way, here's a short-cut: poach an egg in the microwave, courtesy of The Kitchn. You Will Need: 1 egg 1/3 cup water Approximately 1/2 teaspoon vinegar (optional) Microwave Microwave-safe mug or small bowl Microwave-safe small plate S ...more
Extend the life of your camera battery and keep yourself safe from a damaged battery by following these tips. Check the condition directly through your camera, monitor how long it will be until your battery needs replacement, and always charge your battery before it runs compl ...more
Your car needs care and maintenance to run properly. Let Firestone Complete Auto Care teach you the basics about keeping you automobile running smoothly. Check out this video tutorial for some helpful hints on maintaining the windshield wipers on your vehicle. Over time, wind ...more
In this tutorial, we learn how to make a safe password. Passwords are essential, and need to be safe for when browsing around the internet. Other people aren't meant to be able to nose around your information, so protect your information with an indecipherable password. Don't ...more
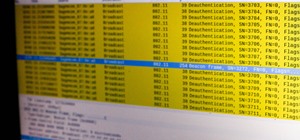
A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vul ...more
What if your computer just crashed and you've suddenly lost of your personal photos? Those are memories you can never get back in the digital world, unless... This video gives a brief demonstration showing you how to copy digital photos from your iPod or iPhone to your comput ...more
RobertMe shows viewers how to cook eggs in the microwave. First, you need to crack the eggs and put the yolk in a bowl. Next pour melted butter on a microwave safe plate. The best idea is to use a paper plate and pour your egg in the plate. Now, cover this with another paper p ...more
I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to rememb ...more
Chain locks are hardly highly secure to begin with, but a fun MacGyver-style trick nonetheless. Add it to the lock picking vault. Crack a Master Lock - Mathematically, No Shim. Open a Locked Door With a Credit Card. Wooden Combination Lock Demonstrates Inner Workings. DIY Digi ...more
You may have asked yourself, "How do hackers take my password, if the website owner can't?" The answer is simple. When a website stores your login password for the site, it is run through a cryptographic hash function before it enters the database (if the website isn't Sony). ...more
This Null Byte is a doozey. On Sunday, September 19th, an exploit for the latest Mac OS X 10.7 "Lion" was discovered by Patrick Dunstan. This exploit allows for an attacker, even remotely, to request to have the root user's password changed without knowing the password to the ...more
How to Crack Passwords Faster by Putting Your GPU to Work with HashcatSecurity on the internet is always changing. Not too long ago, having a 10 character password meant that you were safe from all forms of hash cracking. Hash cracking is when you take a string of characters t ...more
Gone are the days when you had to carry a clunky DynaTAC to make phone calls, pocket phone book for you contact list, Sony Discman for your tunes, and wallet for you cash and credit cards. Today, all you need is your smartphone. To be specific, Google's Nexus S 4G on Sprint. ...more
Since the invention of the printing press, books have been a dominant and iconic paradigm in our culture and throughout the world. During my years in elementary and high school, the digital world was on the rise sparking the conversation: Are Books Obsolete. Over the last year ...more
SentrySafe puts all sorts of measures in place to protect your valuables and important documents. This particular SentrySafe has an electronic lock, four 1-inch bolts to keep the door firmly in place, pry-resistant hinges, and it's able to withstand drops of up to 15 feet. Tha ...more
It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement. Whether you are a journalist, a protestor, or a hi ...more
Welcome back, my greenhorn hackers! In many cases when a computer, phone, or mobile device is seized for evidence, the system will have graphic images that might be used as evidence. Obviously, in some cases these graphic images may be the evidence such as in child pornograph ...more
Get your holiday shopping done early with these deals on software, e-learning classes, and gadgets. These Cyber Monday goodies include something for everyone at a can't-miss additional 20–70% off sale prices. 1. The Official Cyber Monday Mac Bundle ft. Parallels Pro & Luminar ...more
Greetings fellow hackers. This tutorial is about creating "safe" passwords. This is different from strong passwords. Safe passwords is just creating a password that is not used by someone else or colleague, my definition. But how do you prevent something like this from happeni ...more
Let's say you forgot the code to your Master Lock combination padlock. What can you do besides buy another one? Well, there's a surprising abundance of ways to open a combination lock other than with just the combination, some of which will even let you reset the code. Of cour ...more
Welcome back, my budding hackers! Digital forensics is one of IT's most rapid-growing disciplines. All hackers should be familiar with digital forensics if for no other reason than to protect themselves. More than one hacker has been apprehended because they were unaware of t ...more
When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android ...more
You can send and receive money from your iPhone using Venmo, Square Cash, Facebook Messenger, and even Snapchat. There's also Zelle, which offers quick-pay solutions in major banking apps such as Bank of America, Chase, and Wells Fargo. However, Apple has a built-in system to ...more
Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password ...more
CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer. Head of Security: Well let me tell you something my good friend. Many companies we have today they are still getting attacked from hackers ...more
You don't need to be a hardcore audiophile to know that Dolby is pretty much synonymous with rich and immersive sound. While we often associate them with home theater systems, Dolby has brought their surround sound processing to the mobile phone arena with Dolby Digital Plus b ...more
Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator. In earlier posts in this series, we examined registry fi ...more
Chances are that you've been using your microwave just to nuke leftovers, but they can do so much more than heat up last night's dinner—microwaves can help you peel garlic more quickly, get more juice out of lemons, disinfect your kitchen, dry out herbs, give beauty products n ...more
Toyota is testing blockchain and distributed ledger technology (BC/DL) for data sharing for driverless cars and other applications. This could eventually reassure buyers of its upcoming high-end cars by making sure their sensitive data is secure. As vehicles modernize, they b ...more
With the explosion of food blogs in the last couple of years, there are more recipes available at the tip of your fingers than ever before. Craving chocolate chip cookies or Sriracha-flavored anything? You're guaranteed to have several thousand versions to choose from. So that ...more
In the past, to see a pre-constructed state of the house that you would one day live in, you had to be able to read blueprints or hire an artist to sketch it out. Later came the ability to have a 3D rendering of that house on a screen, but you'd still have to work hard to envi ...more
Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on. Those are just the big ones that get reported in the news. Millions ...more
At the recent DefCon conference in Las Vegas, researchers opened many of the top commercially available gun safes with simple tools like a straw or a paper clip, and in one case, just by shaking it a bit. The investigation began after the researchers, Toby Bluzmanis, Marc Tobi ...more
Butter can be even more delicious than it already is. While that may be a shocking claim, it's most definitely true. Many new cooks and even seasoned chefs don't realize this, but the few minutes it takes to do these things will pay you back exponentially when it comes to that ...more
Welcome back, my hacker apprentices! A you know, Mr. Robot is my favorite TV show this year, and not just for the realistic hacking. Rami Malek, the actor who plays Elliot, is incomparable in his depiction of a young man with social anxiety who is alienated from a superficial ...more
Give an 18-month-old a shoe, check back 10 minutes later, and it's a very big maybe he will have it on his foot. But give him your smartphone, and in a mere five minutes, he can take 100 pictures of the carpet, send weird messages, and delete essential apps. Imagine what your ...more
Coinbase is the primary go-to for many users when it comes to investing in Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), Ripple (XRP), and more, due to its user-friendly interface. But before you join them, know that the ease of use comes with a price. Coinbase charges fees f ...more
I don't know how many of you had this experience in your youth, but when I was a kid, I used to actively think about what would happen if I suddenly woke up in a fantasy land, or were to pass through a portal into another space and time. I knew it wouldn't really happen, but w ...more
Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?" As the hacker is among the most skilled information technology disciplines, it requires a wide knowledge of IT technologies and techniques. To truly be a great h ...more
We all know them, and many of us despize them. And some might support them, regardless many have different opinions. NSA: Who Are They? They are people who believe in them having access to everybody and all data that exists in the digital world. (In a nutshell) They work wi ...more
Welcome back Hackers\Newbies! Hey guys first of all I would like to explain my absence here in NullByte. I got a little "occupied" with "other things". When I got back, I saw all these HowTo's, articles, Help Questions, I decided, I need to share more of what I have, to you g ...more
So, you scratched up your $500 Adobe CD and now it's unreadable. You could go buy a new one, but you already purchased it! Searching The Pirate Bay and downloading some Adobe software can usually be easy enough, but what should you watch out for? And what about your movies? W ...more
Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life. Imagine arriving home one night after work and there's a Post-it note on your apartment door with the website "your-name- ...more
For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application tha ...more
I have an absolutely wonderful time making projects and writing articles for all of you mad scientists! Today, I will bring you behind the scenes for a look at the workbench, tools, and software that make the Mad Science World possible. Above is my beautiful workbench! My who ...more
Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself ...more
On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you nee ...more
The last iOS software update was a modest one, but iOS 17.4 has a lot more for your iPhone, including changes to emoji, Podcasts, security, Safari, widgets, Apple Cash, CarPlay, and more. Many of the exciting changes in iOS 17.4, as well as iPadOS 17.4, apply to users in the ...more