Your freezer is no one-trick pony. While it does excel at keeping your food fresh for as long as possible, it has a few secret talents it doesn't want you to know about. Like making soda slushies and pyro-friendly smoke mix, as well as reviving dead hard drives. Even better—it ...more
UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - at my blog, here - https://techkerne ...more
Have you ever wondered how credit card numbers work? I mean, how they really work? How do they come up with the numbers? Credit cards actually follow a very specific pattern. Let's take a look at how they're set up. Example of a Credit Card Number 4485 3151 5882 2849 These ...more
Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa d ...more
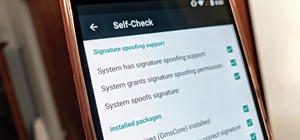
Carrier-branded Galaxy S9 models come with a ton of bloatware that you usually can't get rid of without rooting. With a little digital elbow grease, however, there is a way to disable bloatware on your S9 or S9+, and it's a lot safer that attempting to root and modify you prec ...more
Whisking liquids seems somehow quaint, especially since there are good, cheap devices out there like immersion blenders and hand mixers that can whip cream, turn egg whites into meringue, and mix batters for you. However, I still love my whisk and use it often, and here's why ...more
Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exi ...more
There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer. It's puzzling to imagine about 100,000 .onion websites in existence. Readers who ...more
This is a tutorial showing you how to easily hack flash (.swf) games! You only need two things: A flash game (in .swf format) and Flasm (an amazing flash disassembler). Getting Flasm Download Flasm Flasm can be downloaded from the no|wrap.de website. Save & Extract Save ...more
Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a smal ...more
It's always tempting to grab yesterday's shirt and toss it on in a fit of laziness, but before you do and venture outside, it's probably wise to freshen it up a bit first. The most obvious way to do that is with some Febreze, but if you don't have any around, your liquor cabin ...more
If you have a modern iPhone, you have an excellent video recorder at your disposal. Every iPhone since the 6S has the ability to shoot in 4K resolution, and each new iteration has brought new capabilities to the table. But even the best mobile shooter can use a little extra he ...more
The app formerly known as Google Experience Launcher is now officially called the Google Now Launcher in honor of its most prominent feature, Google Now. Only problem is, this launcher is still exclusive to the Nexus 5 smartphone. Thankfully, "exclusive" in the world of Andro ...more
When you know how to cook it, tofu is a delicious dish in and of itself—truly. Too many people have been subjected to poor quality or badly cooked tofu and told to eat it because it's a "healthy alternative" to meat. Usually what they bite into is a bland, rubbery mess coated ...more
Rooting your Samsung Galaxy S4 has many advantages; theming, free wireless hotspots, deleting system apps, and generally being ahead of the curve when it comes to updates. It's also great for simple things like centering your clock or freezing apps. Today, I'm going to cover ...more
Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll ...more
The produce section is full of fruits, both familiar and quite strange. Depending on the season, you may see giant, bright-green bananas on display next to the normal bananas that you know and love. No, those aren't super-unripened bananas—they're plantains, and they are defin ...more
If you have a good food processor or blender, there's no reason not to make your own nut butters, whether you like almond, cashew, sunflower, or the perennial classic, peanut. Not only can you control the taste, sweetness, crunchiness, and oiliness of the butter, you can also ...more
We've already shown you how to dunk a regular-sized Oreo cookie while keeping your fingers pristine, how to upgrade Oreos into different desserts, and even make them into lazy ice cream sandwiches. Now we're going to introduce you to a few other essential Oreo hacks that will ...more
You don't need to delete an entire thread in the Messages app to get rid of a couple of texts on your iPhone. With a few taps, you can remove unwanted iMessages and texts, as well as storage-hungry photos and videos, to de-clutter a conversation. And in iOS 13, the process is ...more
No matter what word game you're playing, whether it's Scrabble or one of its near-homogeneous counterparts like Lexulous, Wordfeud or Words with Friends, one of the easiest ways to stay on top of your opponent is knowing all of the legal two-letter words you can play. You're n ...more
One of the best things about Android is the ability to customize your phone to your liking. From changing the layout of icons to finding the perfect wallpaper to reflect your current mood, there's a wide range of tools to make your phone yours. One of the easiest ways is to t ...more
Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting ...more
First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect. I've read quite a few books and ...more
For many of you, the carving fork only comes out at Thanksgiving as an essential turkey-slicing aid. Perhaps you pull it out of the knife block to slice up the occasional roast. But the carving fork (also known as kitchen fork) can be used for many more tasks around the kitche ...more
Watch to learn how to say the names of things you use in the kitchen, like plates, colanders, and the stove, in French. un espirateur de table - small vaccuum une assiette creuse - a plate with a dip in the middle une assiette plate - a flat plate une balance - balance un batt ...more
It can be pretty tough to fall asleep when your brain is thinking nonstop or anxiety has gotten the best of you, and it seems to only get harder when you're lying in bed listening to yourself breathe. Yet paying attention to that breathing may be exactly what you need in order ...more
I often read ebooks on my iPhone while I walk, but being glued to my screen is a good way to get run over or cursed at. To save my physical and social hide, I use this trick to get my iPhone to read ebooks and articles out loud, turning my whole text library into de facto audi ...more
Moles can be a problem. You can identify Moles as a problem if when you stick your finger down a hole you can feel a tunnel. There is a safe way to rid your lawn of Moles without harming other pests, insects, pets or family. Castor Oil produces an odor that Moles don't like. G ...more
Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities app ...more
The Xposed Framework is an incredibly powerful tool. But because of this power, there's a chance that something could go wrong when installing a broken or incompatible module, which can cause bootloops or even soft-brick your phone. Depending on how bad the situation is, the ...more
Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client. Although the most valuable information to the hacker ...more
There are so many kitchen gadgets that only do one thing. You can buy a special tool to strip the kernels off an ear of corn, de-stem your strawberries, or cut bananas into perfectly uniform slices, but that's all it'll do. It's easy to get carried away, and before you know it ...more
Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different appro ...more
Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pen ...more
I'm sure that there are plenty of people out there who have no idea what a plague doctor is/was, so I'll start with an explanation. Despite what we now consider to be their relatively fearsome appearance, they were originally just doctors, and they have existed for as long as ...more
The next time you're feeling tired and stressed out, pull down on your earlobes firmly for a few seconds, or apply firm pressure to the indentation on your nose bridge between your eyebrows using your thumb for several minutes while breathing deeply. Sometimes a little acupres ...more
If you're anything like me, you probably think it's borderline sacrilege to even think about a sandwich or a burger that doesn't have a layer of smooth mayonnaise. But I don't just keep a jar of it in my fridge for lunch—it's also there for practical purposes. I learned this ...more
Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic An exploit is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability in order to cause unintended or unanticipated behavior to occur ...more
Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, su ...more
Wireshark is the world's foremost network protocol analyzer, and is the de facto (and often de jure) standard across many industries and educational institutions. This video tutorial demonstrates how to get the Wireshark packet sniffer up and running to do a capture as well as ...more
Dutch filmmaker Anthony Van der Meer published his 2015 thesis short from Willem de Kooning Academy in South Holland online in December 2016. It's a brilliant piece of work that managed to be touching, alarming, and informative at the same time. His documentary, which already ...more
One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform t ...more
As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt ...more
Who am I? First let me introduce myself. I am Th3skYf0x, an -well lets call it experienced- hacker and i recently found this site and right after that i found this Null Byte "world" soo i thought... Why not teaching instead of doing nothing with my knowledge. Let me get one ...more
Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills. Submit your best shot to our weekly competition for a chance to win an awes ...more
It's common knowledge that certain foods foster brain development, health, and memory. Fish almost always makes the list, as do any foods that are loaded with antioxidants like blueberries, nuts, whole grains, green tea, and dark chocolate. Spices like turmeric are being studi ...more
Want to get the Wii Opera Browser for free? This will not work with a USB, only a SD-card. Steps according to corradostyler94 listed below. 1.) Downloading and unpacking the browser on your Computer: Download the browser for your Wii-System Download link for USA: http://ul. ...more
Pickles are one of those rare foods that most people love, but never even think of making. Most home cooks shy away from making pickles because they take time and patience, and because the grocery store option is both cheap and delicious. I'm very much one of those people who ...more
Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself ...more
Sometimes the idea of cooking fish, especially for a group of guests, can be intimidating. There's the fear of the fish not cooking right, or sticking to the pan or grill. And even if you cook it right and the fish doesn't stick, you're left with the inevitable fishy-smelling ...more
Cooking spray is something of a gross necessity. The slimy, oddly-scented grease is perfect for keeping casserole dishes crust-free, but the oil splatter does a number on clean kitchen counters, and the lecithin ingredient can ruin nonstick cookware if not careful. Despite th ...more
This video tutorial from IndyMogul shows you how to make the quick-draw sleeve gun from "Taxi Driver". Robert De Niro built it in Scorsese's "Taxi Driver," but Erik Beck from INdy Mogul builds it for cheap! In this episode, Erik builds the infamous Quick-Draw Sleeve Gun that ...more
WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling. First, U.S. Senator Joe Lieberman swayed Amazon's decision to stop hosting WikiLeaks. Then, Tableau Software removed graphs from th ...more
Wedding themes are no rarity, but a SCRABBLE wedding? I never would have guessed, until I came across "10 Ways to Incorporate Scrabble Into Your Wedding" at CasaSugar. Now, I'm one of the biggest SCRABBLE nerds out there, but I could never see myself getting hitched amongst SC ...more
I recently posted a Tutorial about setting up Dendroid: http://null-byte.wonderhowto.com/how-to/setup-dendroid-android-rat-0167299/. I have worked the last 5 days on getting the Dendroid Binder, given with the Dendroid Source, working. This solution only works on Windows syste ...more
Cleanliness is next to godliness. My interpretation of that age-old adage means that keeping your house clean is just as un-fun and boring as being a goody two shoes. That's why they call things like laundry and doing dishes "chores," I assume. Yuck. Lucky for you, though, we ...more
It's universally known that broccoli, kale, Brussels sprouts, cauliflower, and all cruciferous vegetables (also known as brassicas) are good for you—but you probably don't know exactly how good they really are. A recent study by Johns Hopkins University and the University of ...more
When your opponent throws down "AA", you tell them no abbreviations, but alas... it's not. They build "ZA" on the board for 64 points, and you say it's slang, but it's in the dictionary. Next is "EF", and you let them know that spelling out letters is not allowed and ridiculou ...more
Nothing about living in a snowy climate is easy, but life with a snowy, frozen car doesn't have to be the worst part of your day. With a few clever hacks and some anti-weather tactics, you can fight off frozen windshields, icy locks, and even stubborn car doors, while keeping ...more