In order to secure a PDF with a password when opened in Adobe Acrobat 9 Pro, press the secure button and go into password security settings. Here you can change on what versions of this software the file will run on, the next option asks which portion of the document is to be ...more
It's important to assist your readers as they browse through your PDF document, especially it has a lot of pages. In this Adobe Acrobat video tutorial you will learn how to create basic buttons for navigation between pages. You'll see how to create a default view state, and sa ...more
Do you want to include more pages after your file is published into PDF? Or you have accidentally included pages that are not meant to be in the PDF? In this Adobe Acrobat video tutorial you will learn how to insert and delete pages in a PDF document. Make sure to hit "play tu ...more
USE WINDOWS 7 ULTIMATE x64 w/ all the latest updates always OF COURSE AND... USE THE ASTON 2 SHELL REPLACEMENT, MENU, DESKTOP, W/ THEMES... USE EASEUS DATA RECOVERY WIZARD V5+... USE FROSTWIRE P2P FILE SHARING CLIENT... USE INCREDIMAIL 2 (LATEST)... USE SAFARI (ONE OF THE ...more
eBooks are an amazing thing, especially with Amazon's Kindle. What's irrtating about eBooks as that you have an infinite selection of books at your fingertips, but they all cost so much! Well, as always, Null Byte has a trick up our sleeves for nabbing free ebooks from Google. ...more
Apple's iPhone is considered one of the best smartphones in the world. Many cell phone makers have tried to take down the juggernaut, with some Android-based devices coming close, but in order to become an actual iPhone killer, something revolutionary needs to happen in the mo ...more
George Maestri from Lynda shows how to add interactivity in Google SketchUp Pro using a variety of tools in the program. Adding interactivity allows for added dimension and interaction with an object. The example used in the tutorial was that of a fridge, which after adding in ...more
With the mass arrests of 25 anons in Europe and South America, and the rumors of an FBI sweep on the east coast of America floating around, times look dicey for hackers. Over the past few days, a lot of questions have been posed to me about removing sensitive data from hard dr ...more
Last week, I demonstrated how to go a little deeper into your Google+ profiles, photos, and introduced cross-posting. This week, I'm highlighting a bunch of different unofficial resources that have sprung up that will help improve your Google+ experience, and give you the late ...more
Google recently unveiled the start of their new social network Google+, which is set to compete with Facebook and fix the awkward, broken aspects on online sharing they claim exist. It's currently only open to a limited number of Googlers during its "field trial," and if you w ...more
Whenever we make a homemade circuit, we use what are called through-hole components. Any components with long metal leads is a through-hole component. They are great for soldering to, but it's tough to fit enough through-hole resistors and capacitors into a smartphone. To get ...more
If you’ve never heard of the term search engine optimization or SEO, then your website probably isn’t optimized for search engines and it’s hindering your site’s ability to get all of the traffic that it should. Read on for an explanation of what this entails and how it can he ...more
To some, SCRABBLE is just a board game to play during family game night or during a casual get-together. Others think of SCRABBLE as a mere hobby. But with any activity, there will always be fanatics—the ones who would rather sell their soul than stop—the ones with a constant ...more
In this article, we're going to create an additional button in our Word toolbar which creates a PDF file of our loaded file with one simple click. We are going to use the function to create Macros, which are little 'programs' in Office applications. The Macro we are going to w ...more
Find a PDF You need a PDF file on your computer to convert, so keep the file path in mind. Visit aXmag Go the aXmag website to submit a PDF. Choose the PDF Click the "Browse" button to choose your PDF file you want to convert. Once chosen, fill out your email address in t ...more
Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look ...more
It's no secret that Apple's Notes app supports attachments such as photos, videos, and web links, as well as other file types like PDFs, word documents, spreadsheets, locations on a map, and audio tracks. While images, videos, and document scans are simple to add on an iPhone ...more
Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, ...more
File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, ...more
With an Android device left at its default settings, your location history is automatically recorded. You can view and manage this data, but the simple interface of points plotted on a map leaves a lot to be desired. Developer Theo Patt realized this, and created a tool that ...more
It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or ...more
Not many people use their phone exclusively for making calls or sending messages today. If you're an Android user, the chances are high that you're using your phone or tablet for work-related activities. However, the basic set of apps and services your device was shipped with ...more
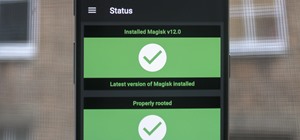
Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search o ...more
Whether you're ordering a new 2019 iPhone model online or just want to know how they look in your hand before buying in person, use these printable cutouts to see which one looks and feels best. The sizes of the iPhone 11, 11 Pro, and 11 Pro Max are almost identical to that o ...more
Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the c ...more
As a developer, before you can make augmented-reality robots that move around in the real world, controlled by a user's finger, you first need to learn how to harness the basics of designing AR software for a touchscreen interface. In recent years, the vernacular for referrin ...more
There are plenty of third-party apps for scanning documents on your iPhone, but they can all be tossed out the door since iOS 11 includes one by default now. Instead of a dedicated app, it's included as part of the Notes app, and it's fairly easy to use. After scanning, you ca ...more
If you haven't used a Samsung device in a few years, the Galaxy S20 series will be your first taste of One UI 2, the skin running on top of Android 10. Although One UI is on the heavier side, it has loads of exciting features that go beyond what's offered in stock Android. Th ...more
Apple's iOS 13 for iPhone includes new features in Safari that make browsing the web a little bit better when compared to iOS 12. Some changes are small while others add functionality that just wasn't there before. Plus, there are more security enhancements. While Safari didn ...more
Apple's new Watch models go on sale April 24th in Apple Stores everywhere, and can be preordered online starting April 10th. If you're set on preordering one, how do you know which size to choose? Whether you plan on getting an Apple Watch, Apple Watch Sport, or Apple Watch E ...more
Apple's new iPhone 6 and iPhone 6 Plus go on sale Sept. 19th, but pre-orders begin on Sept. 12th. If you're ready to trade in your iPhone 5 for one of these bigger and more iOS 8-friendly devices, you're probably going to pre-order. UPDATE: We've also created printable cutout ...more
Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all beca ...more
The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be ...more
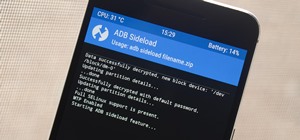
No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today ...more
Google's has expanded ARCore support to numerous Android flagships like the Galaxy S10, so if you have a compatible device, you get access to all the cool new apps that can augment the world around you. One of ARCore's most sought-after features, AR Stickers, is normally exclu ...more
Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker. While I'm definitely no black hat, d ...more
Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP ...more
With its recent acquisition of 3D gaming engine PlayCanvas, Snapchat parent Snap, Inc. appears to be preparing a challenge to the existing players in the world of game development, particularly in terms of augmented and virtual reality gaming. The acquisition appears to have ...more
If you were holding out on an iPhone X but still haven't bit the bullet on the $1,000+ price tag, it may be because you're not sure how it will feel in your hands compared to the iPhone 8 or iPhone 8 Plus, which are pretty much the same size as the last three iPhone models you ...more
Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of har ...more
If you remember last time, we successfully uploaded picture with a small hidden PHP command executer embedded in it onto a server. Now, our goal is to take this a step further and get an interactive shell. To do this, we need to upload another file that either binds a port for ...more
The moment arrives when you finally pop a shell on the web server you've been working on, only you find yourself in a strange environment with limited functionality. Restricted shells are often used as an additional line of defense and can be frustrating for an attacker to stu ...more
Lenovo has done a great job preventing leaks of their new Moto RAZR. We've seen a few images here and there, but for the most part, we knew very little about the long-rumored phone. But with the announcement date just around the corner, an FCC filing has given us a look at the ...more
Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as ...more
Welcome back Hackers! We have embed a Backdoor in to a PDF file,Android package File. In this tutorial we will embed a Backdoor in to an exe file. lets start, Open msfconsole To create the embed exe we need the executable file.I am using idm to create the Backdoor. Lets cr ...more
Amazon is currently offering over $80 in free Android apps in the Amazon Appstore, but only for Friday and Saturday, so make sure to grab them quick before they all go back to normal price. Highlights include the Fleksy Keyboard (normally $3.99), Oxford Dictionary of English w ...more
A good prank requires decent effort, creativity, and impeccable timing. If you're in the office, there are plenty of hilarious pranks to play on coworkers, and for your family and friends, there's everything from toothpaste-filled Oreos, to solid milk, to impossible-to-solve ...more
Adobe is best known for its photo and video editing software, but they also have a number of lesser-known apps that you may be interested in. Adobe Fill & Sign, available on iPhone and Android, is the best way to electronically fill out important documents on your smartphone w ...more
The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data. Apple introduced so ...more
When it comes to augmented reality apps, visually immersive experiences are plentiful, but audio experiences are somewhat underrepresented. A new app for iPhones and iPads seeks to shift the AR paradigm toward the latter. Now available via the App Store, the Fields app create ...more
It looks like Magic Leap is getting its ducks in a row to launch its Magic Leap One: Creator Edition as the company's name is once again showing up in US Patent and Trademark Office (USPTO) filings. According to a trademark application filed earlier this month, "Lumin" might ...more
In off-record discussions with AR experts, the consensus on ARKit is that it takes a software approach to the depth-sensors available on Tango devices. As a result, the toolkit has shortcomings, such as detecting walls and vertical surfaces. TapMeasure, a new app from spatial ...more
It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something. Our rush to the future is too fast to keep up with. Denying technology is ignorance, isolat ...more
On an Android device, you can download almost any file type into a neat and tidy "Downloads" folder, and those files can then be accessed with an appropriate app, shared via email, or transferred over to your computer. On an iPhone, there is no such folder, and saving files fr ...more
Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corres ...more
Converting files from one format to another can be a pain. Sometimes you have to download software that you'll only end up using once. Other times you have to use a shady third-party conversion site that's riddled with ads. Not to mention that after a while, unless you're extr ...more
Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques i ...more
Apple's latest mobile operating system for iPhones, iOS 12, was released to everyone Monday, Sept. 17, and it's the same exact build that developers and public beta testers received as the "golden master" on Sept. 12, the day of Apple's 2018 special event. Install it to start ...more
Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making cus ...more
Apple's newest mobile operating system, iOS 8, is out for the general public, and we've got a rundown on the best new features you can use on your iPad, iPhone, and iPod touch. While there's not a huge visual change as there was from iOS 6 to iOS 7, there's still plenty of coo ...more