Your iPhone is full of features, many of which you might not even know about yet. Still, Apple keeps adding feature after feature with each new iOS update, and iOS 14.5 is no exception. The latest iOS version adds at least 69 features for your iPhone that you should be happy a ...more
This six-minute tutorial shows you how to use the logical IF function with letter grades in Excel. The video features a sample table with a sample assigned grading scheme ranging from A to F, which is a common application of the logical IF statement in Excel. After the data is ...more
This video will show you how to tether your Samsung Messager 2, (the MetroPCS phone) to your PC to use as a modem for internet access. This will allow you to use your cell phone as your internet connection point, meaning you'll connect to the net for the cost of your cell phon ...more
The iOS App Store is a big place, offering over two million applications in total. However, there are actually some apps you can and should install on your iPhone that the iOS App Store doesn't include. And no, these apps do not require any difficult jailbreaking or complicate ...more
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's Excel ...more
One of the coolest features in modern smartphones is their Bluetooth connectivity. This is how two digital devices can communicate with one another—sending data like your phone call audio or your favorite song—all while using up minimal battery life. Don't Miss: Android Basic ...more
In this video tutorial, viewers learn how to calculate the standard deviation of a data set. The standard deviation of a statistical population, a data set, or a probability distribution is the square root of its variance. To calculate the standard deviation, users will need t ...more
Despite concerns with SafetyNet, Google actually cares about root. Every phone they sell has an unlockable bootloader, so you can toggle a setting and send a Fastboot command, then start flashing custom firmware right away. The Pixel 2 and Pixel 2 XL continue this tradition, a ...more
Free stuff is pretty cool. Free internet is even cooler—and free internet that is actually free is the coolest. If you would rather avoid sitting in a Starbucks and having to listen to hipsters discuss the proper length of cropped jeans, then this should be of interest. Freed ...more
Mozilla's Firefox has always been a highly praised internet browser. Since it's open-source, users know what they're getting without any secrecy. It's got plenty of features that are unmatched by any of its competitors on mobile. However, speed and performance have always been ...more
As a web developer, I often read articles about hackers (from the lowly to the knowledgeable) infiltrating websites via the dreaded 'SQL Injection' method and completely taking control, changing, gaining access, or destroying the owner's data. As a fellow web developer, I'm su ...more
Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary fl ...more
Last week, I showed you a peek at the not-yet-released Galaxy S5 Active, the more rugged version of Samsung's current flagship. The man behind those leaks, TK Tech News, has now brought another goodie from the device, and it's one we can have on the Galaxy Note 3. Dubbed Acti ...more
Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the ...more
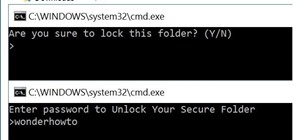
What's the easiest way to keep track of your website passwords? Maybe in a password-protected document on your computer? Makes sense. But surprisingly, this is no easy task in Mac OS X. Snow Leopard does not have an easy one-click option for password protecting files and fold ...more
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's Excel ...more
S Health is one of the biggest selling points for newer Samsung Galaxy devices. It offers a centralized place to view and manage data collected by all of the various sensors like the heart rate monitor. As wonderful as this service is, all of its features are not available in ...more
The calendar app is one of the unsung heroes found within your iPhone. It's the ultimate personal assistant that you've come to rely on to keep track of your schedule and ensure you never miss a class or meeting, all while reminding you of upcoming birthdays and deadlines to h ...more
Apple's iOS 7 is riddled with annoying features, and some of them can't be toggled off in Settings. For example, I really don't like having labels directly underneath my app icons, and there's no way to remove them. Sure, it may be nitpicky, but it's my device, and it should b ...more
While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be host ...more
Keeping your OnePlus One running smoothly can be taxing, especially if you spend most of your day looking for ways to tweak performance settings like me. Sometimes I get lucky and end up with a faster phone, but because I experiment so much, I often end up restoring it back to ...more
Making the jump from an older iPhone, or even an Android phone, to the iPhone 12, 12 mini, 12 Pro, or 12 Pro Max can be a big one. It's not just the change of a new smartphone — it may have had a huge impact on your wallet too. So whenever the device goes berserk, is unrespons ...more
Twelve-year old Rory Staunton took a dive for a basketball during gym class and came up with a cut on his arm. The school nurse applied a couple of band-aids, without cleaning the cut, and off he went. In approximately three days, hospital physicians told his parents there was ...more
In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the ...more
Since the San Bernardino shooting in 2014, Apple's been engaged in a game of cat and mouse with law enforcement. Authorities want access to evidence on criminals' iPhones, but Apple wants to protect all of its customers' personal data equally. The latest installment in this sa ...more
With iOS 12, Apple is making up for mistakes from the past, with iPhone batteries being no exception. The new update builds upon both battery health and performance throttling tools introduced in iOS 11.3 by offering users more information about your iPhone's battery usage tha ...more
Wall studs are both critical for maintaining the structure of your home and supporting items of weight and function on the interior walls (e.g. cabinets, shelves, plasma TVs, etc.). With wall studs playing such a critical role, consistently being able to find them is important ...more
Hello fellow grey hat hackers, as hackers it becomes necessary for us to be able to send emails anonymously. Whether for whistle blowing or pranks or social engineering or whatever, it just is necessary for us to do that. So then I tried with python smtplib but then that requ ...more
LG, like many other OEMs, usually locks down their bootloaders with an airtight seal. There are a few good reasons for this, the big one being that an unlocked bootloader technically compromises some device security measures. LG would also argue that unlocking your bootloader ...more
If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against ...more
In previous Android versions, you lost about an inch of screen real estate to the status bar and navigation bar. But if you enable Android 10's new navigation gestures on your Samsung Galaxy, you can regain the bottom part — and with the help of ADB, you can reclaim the top po ...more
Samsung may not be the best when it comes to redesigning their devices (hopefully that will change with Galaxy Note 4), but they do have a knack for including some pretty awesome features into their TouchWiz software. In its latest version, the one that shipped with the Galax ...more
The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from eve ...more
If you've just ditched your Android phone for a new iPhone, you're in luck, because Apple has a way to make your transition as simple as possible with their Move to iOS app for Android. To help make things even easier on you, we've outlined the process of using Move to iOS to ...more
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's Excel ...more
Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique. What Is Canvas Fingerprinting & Who Uses It? ...more
Cloud storage looks pretty good compared to the heavy restrictions that hard drives and other types of external memory carry. The cloud is not only limitless in what it can hold, but it can also easily be accessed from any device that has Internet—your smartphone, work compute ...more
Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just ...more
Apple last month released iOS 17.2, its biggest iPhone software update since iOS 17.0, with 60 new features. Now, as of Jan. 22, we have iOS 17.3. Overall, it's not the behemoth software update that iOS 17.2 was, but it has a few exciting new things you'll definitely want to k ...more
I'm sure we've all heard about MSN and Yahoo! Messenger, right? They can be useful, but the setup can be quite time consuming for those who need to use it just once or twice—and the privacy statements are a real bother. For example, we must provide our real details. You could ...more
When we look back on it, 2014 may be remembered as the Summer of Android Wear. With two new flagship smartwatches due out soon, Google's been readying its mobile OS for the wearables sector. Just recently, a test build of the firmware from the upcoming LG G Watch leaked. This ...more
Are you serious about becoming a bonafide hacker? Then you simply must learn how to hack SSL passwords using ARP poisoning. ARP poisoning, also known as ARP spoofing, involves attacking an ethernet wireless network by looking at the data frames on a LAN (local area network). R ...more
When you've exhausted your data plan, streaming isn't an option unless you want overcharges. While Apple Music makes it easy to download songs for offline listening, you need to add the music to your library first. This creates an extra step in downloading music, but it doesn' ...more
Google doesn't get enough credit for it, but they definitely make some of the best phones for rooting and modding. Heck, if you want to replace the entire operating system on a Pixel, you can do it pretty easily. It all starts with the bootloader. On Android, the bootloader i ...more
It's like magic. Creating a .LOG file has never been easier. And all you need is Notepad on your Windows PC. After creating this LOG file, Notepad automatically inserts the current date and time after the last line. Check it out. If you've ever wondered about LOG file types, t ...more
Let's say you're flush with Google Opinion Rewards credits, or you just got a Google Play gift card for your birthday. This is a perfect opportunity to remove ads and unlock new features by upgrading some of your free apps to their paid counterparts, or to finally purchase tha ...more
The main draw for Google's Pixel series is the software. It rocks a clean version of stock Android instead of a heavy OEM skin like TouchWiz, it gets frequent prompt OS updates, the camera software is downright amazing, and it has perhaps the most fluid UI of any phone. But an ...more
In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exp ...more
While autonomous vehicles are almost assuredly the future of personal transportation, we are likely many years from seeing self-driving cars become as ubiquitous as manually-driven ones, as the auto industry has a myriad of government regulations and other constraints to conte ...more
Your iPhone's Weather app received its biggest update yet. Apple finally incorporated its Dark Sky purchase into Apple Weather, so you'll see more information for each location's forecast. Plus, there are a few surprises to be excited about, such as the ability to add more tra ...more
Last Friday's mission was to accomplish solving HackThisSite, realistic 4. The fourth in a series of realistic simulation missions was designed to be exactly like a situation you may encounter in the real world. This time, we are told "Fischer's Animal Products is a company th ...more
If you ever want to root your OnePlus 6, install TWRP, get Magisk and Xposed, or flash a custom ROM, the first thing you'll need to do is unlock your bootloader. Your bootloader is a piece of firmware that loads up the operating system on your phone. Normally, it's programmed ...more
To really personalize your HTC 10, you'll need to be rooted — but that can't happen unless you unlock your bootloader. Thankfully, HTC has made it relatively easy to unlock the bootloader on their 2016 flagship. Unlocking your bootloader will make it a breeze to install TWRP, ...more
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 655th installment in their series of digital spreadsheet magic tricks, you'll learn see how to cre ...more
Re-entering contact information every time you upgrade to a newer mobile device is pain, but the Android software on the Samsung Galaxy Tab allows you to copy over your existing contact information from a SIM card. This video will show you the steps to importing that data. Go ...more
If you've ever noticed, even just for a fleeting moment, that the auto brightness on your Nexus 5 seemed to "glitch out"—you are not alone. Several Nexus 5 owners, myself included, have complained of a seemingly random spike in auto brightness levels towards the high or low e ...more
So, you snapped a great picture, but it's just a little off-center. Usually, rotating a photo requires cropping it, which will lower the overall quality of the image. That's not the case on the iPhone 11, 11 Pro, and 11 Pro Max, however. Apple's new flagships allow you to rota ...more
On the new Moto X smartphone, the only thing you have to do to activate the virtual assistant is say "Okay, Google Now." That's it. You don't have to press a button or tap on the display at all. It's always ready for your voice commands via its "Active Listening" feature, maki ...more
Introduction In the competitive world of today's video game scene, PC gamers are known to squeeze out the best possible visuals in their games. Every few months a new video card rolls out, and RAM is ever increasing; constant upgrading is the norm of staying ahead the curve. ...more
There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're conc ...more