When you click a link from Google search, the link itself turns purple to let you know you've already visited this page. But let's say you're searching for something similar a few weeks from now and you see one of these purple links—you'll probably think to yourself, "What was ...more
The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data. Apple introduced so ...more
On earlier Android versions, you were able to hold down on an app's icon in the recent apps menu (aka app switcher) and jump straight to the app's info page. From there, you could easily uninstall the app, force-stop its activity, or clear its cache and data. If this was some ...more
URL tracking codes: you'll see them on almost every link you copy online to share with friends and followers. It could be tens or hundreds of extra characters appended to the end of a URL, which websites and marketers use to tell how you got to the link in the first place. The ...more
The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other device ...more
You're probably sharing a ton of information on your iPhone with other people, apps, and services without really realizing it. Now there's a new tool to show you just how much, and it can be an eye-opener as well as a fast way to manage sharing permissions and review your acco ...more
In the wake of the recent tragedy in Japan, Southern Californians have been hyper alert to any news regarding dangerous levels of nuclear radiation drifting over from Fukushima. At this time, official statements from the California Department of Public Health and the EPA are a ...more
Apple just announced the iPhone 6, and no matter whether you've been with Android for a few months or few years, there's a good chance you're enticed by the idea of switching over to the other side. As a diehard Android user, I can't blame you. A bigger screen, better camera, ...more
The "Sign in with Apple" service lets you create accounts with third-party apps and websites more easily using your Apple ID. More importantly, it can hide your personal email address using auto-generated disposable email addresses. However, it's easy to lose track of the acco ...more
Android 7.0 Nougat has finally arrived—well, technically, it's in the process of arriving on Nexus devices across the globe. Google uses a staged rollout system to prevent excessive server load when issuing Android updates, which means even though Nougat has made its official ...more
Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay a ...more
To make sure your car is healthy and up to par with required maintenance, you can use Ford's new SYNC system to get vehicle health reports for you car. It gives you vehicle diagnostics, scheduled maintenance, recall information, and more. You just need to go online to your own ...more
Need to sort a ton of data in Excel? Why waste time cutting and copying cells? In this tutorial, learn how make Microsoft Excel automatically sort columns or rows alphabetically. You Will Need: • Microsoft Excel • Data to be alphabetized Step 1: Select a row or column Click ...more
Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy i ...more
Mobile scanning applications are nothing new in the world of Apple, except that the majority of them usually come with pesky in-app purchases that stifle the entire experience and render some features useless until you pay for them. Thanks to Apple dev ABBYY, you can now down ...more
MicroPython is an exciting language to use on ESP8266 boards and ESP32-based microcontrollers, but it doesn't always include all of the libraries you'll need for a specific project. This issue is less of a problem, thanks to the upip package manager. Upip lets you download an ...more
Do you own an HP printer? If so, it may be vulnerable to malware attacks. Researchers at Columbia University discovered that 25% of Hewlett-Packard printers have significant vulnerabilities that put your printer in danger from hackers—even your home. With a budget of just $2,0 ...more
After a two-month delay, Apple has finally released iTunes 11, which was initially slated to be released alongside iOS 6. Video: . The new highly revamped music player is a substantial upgrade from the old version, but that isn't really saying much; iTunes has never really had ...more
The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll ...more
The limitless applications of 3D data visualization will enable a more efficient approach to many of life's problems. Each day, developers exploring this technology are finding new ways to solve these problems in mixed reality; 3D modeling, easier house management, spinal surg ...more
If you hate matching images, typing letters and numbers, solving math problems, and sliding puzzle pieces for CAPTCHA human verification, you'll love Apple's newest privacy feature for apps and websites. Generally, CAPTCHAs can be a massive nightmare on mobile devices. They a ...more
In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately ...more
Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker. While I'm definitely no black hat, d ...more
In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on. While the NSA's incredibly sophisticated surveilla ...more
Does this man look vaguely familiar? A neighbor or former co-worker, perhaps? You might think you recognize him, but this individual is actually the face of 7 billion. Composited with endless photos taken from the world's massive population, he represents an analytically dedu ...more
So you're finally ready to head out on that big trip you've been planning for months, huh? It's an exciting time, but there are plenty of things you'll need to prepare before you head out. For instance, it's hard to imagine life without a smartphone these days, and with useful ...more
Right on the heels of the iOS 11.4.1 beta 3 release, Apple pushed out iOS 12 beta 2 to registered developers on Tuesday, June 19. Public beta testers received the same version, labeled as iOS 12 public beta 1, six days later on Monday, June 25. Last year, the iOS 11 public bet ...more
Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn ...more
Not all threats to our privacy come from hackers thousands of miles away. Often, we just want to keep our data safe from those around us, who may snoop in our phones or demand we reveal our secrets. That's where BlackBerry Locker comes in. Starting with the BlackBerry KEYone, ...more
Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries. And while those films hav ...more
Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemm ...more
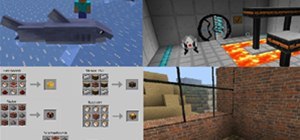
This technique is a simple way to get easy, perfect circles when trying to build in MineCraft. You can make a good template or stencil just by using the circle tool available in MS Paint. Then transfer the pixel data from Paint to MineCraft!
Previously, we talked about how to secure Firefox. Today, we will talk about securing a Chromium based Browser. Why? Because Chrome recently beat Firefox in holding more customers. It is obvious that Google Chrome tracks our every move online, so what alternatives is out ther ...more
We've shown you the best augmented reality headsets, and now it's time to show you the rest. These are the AR headsets you've probably never heard of or even seen. The AR headsets that, in some cases, have a shot at the big time, and may one day reach widespread adoption, and ...more
Now that the transfer tool for migrating your Google Play Music library to YouTube Music is rolling out, more fans of the former, which will meet its end in 2020, are giving its replacement a try. New converts will find three newer features front and center. Your Mix, Discove ...more
If you use iCloud Photos, Apple's iCloud link feature is meant to make sharing multiple photos and videos faster and easier, but it's not as great as you might think. Luckily, there's a way to stop your iPhone from creating them automatically, as long as you're running iOS 13 ...more
Overall, Plex is a great service. You just install the server on your computer, then you can stream your media library to wireless devices with the Plex app for iPhone or Android. But it does have one annoying feature that's enabled by default: Theme music plays automatically ...more
Eric Abrahamson, a professor at Columbia University, writes in to Forbes on how to be the Michelangelo of work shirking. The article is intended to help managers better understand their team's lack of productivity, but it also provides 10 simple tactics for all the lazy asses ...more
Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health). In this tutoria ...more
Pinterest, a worldwide catalog of ideas shared by over 175 million users every month, is dominated by Android users, who are now the app's fastest growing group. Pinterest has since taken notice, and has started to incorporate handy home screen shortcuts for users with Android ...more
f you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's Excels ...more
Microsoft's HoloLens is certainly a leap into the future of mixed reality interfaces, but it's not without drawbacks. Its most notable drawback is its small field of view, cutting off objects you feel like you should be able to see. But there's good reason for that limitation ...more
Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying vario ...more
Have you guys seen this yet? Ben Purdy used projection mapping to create a "real life" Minecraft block. If you don't know what projection mapping is, it works like this: "There’s a piezo element taped to the box and hooked up to an arduino. The arduino senses the physical im ...more
APOLOGIZE Hello my masters and colleagues, first of all I would like to apologize for my absence during the past month, to say that i was busy with some projects and decide to leave the white-side for a while and made some visits on the dark-side(every good COP has a dealer f ...more
In this Software video tutorial you will learn how to make a basic bar graph in Microsoft Excel. You will also learn how to give your chart a title and how to label the axes. First you put in all your data in to an Excel spreadsheet. Then you highlight the data you want to put ...more
We're ending the week with a lot of big announcements and updates. To date, Google+ has updated its name policy, but is still forbidding pseudonyms. Blocking people on Google+ became even easier, and yesterday, games on Google+ launched. Google+ Name Policy Changes Google+ h ...more
Most streaming platforms have seen a huge viewership increase in the past few months. As a result, wireless carriers and ISPs are struggling to provide the necessary bandwidth for everyone, resulting in some customers being limited to DVD quality. The same applies to YouTube, ...more
TCP/IP Client / Server Application Hello! Today's blog post will be about coding a very rudimentary Client and Server application duo, which will communicate by using TCP Sockets. It is, as illustrated, in principle, just two cans and a string that ties them together. The se ...more
Despite its fifth-place finish in our ranking of the best transcriber apps on iOS, Voicera is still worth highlighting due to numerous factors that set it apart from the crowd. Besides being completely free to use on both iPhone and Android, the app's AI-based transcription se ...more
By now you’ve heard about the iPhone 4S announcement, possibly through our article about Apple’s newest smartphone. However, the star of the show was not the only announcement, so here are a few other announcements that were served along side the main entrée this morning. Let’ ...more
Steve Lee Ignacio explains the procedure to be followed to build a Bart PE Professional Rescue CD. He says that the basic requirements for completing this process is a Windows XP Pro or Home CD, a Bart PE builder, a Windows Computer, a program to burn .ISO files and a CD burne ...more
One major iOS 11 improvement that Apple skimped out on during its WWDC presentation was the redesigned storage management system, which makes it easy to view storage consumption in greater detail on your iPhone — and even easier to free up storage space with surgical precision ...more
Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and ...more
It might be time to move those Instagram photos to another service. It seems that Instagram has never heard of the phrase, "If it ain't broke, don't fix it." In a very big WTF moment, the extremely popular photo sharing and editing app decided that it has the right to sell its ...more
Dropbox lets you store anywhere from 2 GB to 18 GB of data for free, but if you want more cloud storage you're going to have to pay. Even if you do, Dropbox only gives you 500 GB for a pro membership. So how do you get more cloud storage without paying a dime? Start using Flic ...more
Since the introduction of the Nexus 4 to the Google Play Store last November, the phone's been in constant demand thanks to the low price and sleek design. Even today, the phone is still listed as sold out. LG's Nexus 4 is also the only smartphone in circulation that can run a ...more
While Apple's reputation for privacy and security is nearly unmatched, it'll never be perfect when Hey Siri is always listening. Aside from iOS devices, Hey Siri always listens for questions and commands on the HomePod and HomePod mini smart speakers. If you rarely use Hey Sir ...more
Whether you're looking to add a substantial coding foundation to your hacking skill set or want to get a job in programming and development, knowing one or two programming languages just isn't going to cut it. If you're a regular Null Byte reader, you know that a lot of the h ...more
Want to transfer all of your data from an old phone to your new HTC Desire HD? Learn how with this quick, official guide from HTC. Whether you're entirely new to the HTC Desire HD Google Android cell phone, interested in picking one up, or just out to learn a few new tips and ...more