Welcome to this short and easy tutorial on hacking and DDosing (is that even a word I don't know) anyways lets get started First of all DDos means distributed denail of service attack, and yes i don't know what the HELL it means either. but anyway DDosing is where you spam a ...more
Welcome back my fellow hackerians, Today i'm going to tell a bit more about the famous DDOS thing. And on top of that we're going to DDOS a website. What is DDOS? Distributed denial-of-service attack, or just DDOS for short. Let me start with just one computer and a bank sit ...more
WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling. First, U.S. Senator Joe Lieberman swayed Amazon's decision to stop hosting WikiLeaks. Then, Tableau Software removed graphs from th ...more
Hello Guys, Today I have made a script for ddosing sites with VBScript! And I don't know how you guys do it, but I've made a script that refreshes the page in a chosen amout of milliseconds. And if you want it a number of times or if you want it to go on and on. And this is a ...more
This is a live map feed to current DDoS Attacks globally. Live DDoS MAP Thought I would post this to give you an idea of the size and scope of DDoS Attacks at any given moment. Plus it looks k00l. Some of the sites on this list are mis-configured BGP, Servers, Sync Traffic. ...more
Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind. While 620 Gbps is impressi ...more
In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the re ...more
Recently the newly famous ProtonMail service was under attack by DDoS attack. This attack was believed to be the hacking group Armada Collective. ProtonMail: The new anonymous email service many know from the known hacking serious Mr. Robot. Well, maybe you knew or you read ...more
This is a tutorial video for the video game Dungeons and Dragons Online (DDO). In his first tutorial video, the cleric Zomm Lightfinger takes you through the quest "Relic of the Sovereign Host" in order to obtain 15 adamantine ore in less than 30 minutes and for less than 1000 ...more
Interested in flooding a Runescape player's website? Watch this video to learn how to download, install, and use DDoseR. Flood any Runescape player with this ddos. Using DDoSeR on your Runescape opponent will freeze them, giving you a huge advantage.
Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. I ...more
It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen ...more
Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks. For those of you who are new here, a denial of service is basica ...more
A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer ...more
Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called ...more
Withstanding an attack from a motivated hacker is one of the most important responsibilities a system administrator must undertake. This is especially true for websites that may contain sensitive customer information and a high volume of users. So it's important for a sysadmin ...more
Hello guys, I recently made a how to about whatsapp but the problem with that script is that it is way to long and you need to copy and paste it so many times so I made a new one that works just fine and is more easy to use lets get into it (Here Is How The Code Supposed To Lo ...more
For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in Vir ...more
With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use ...more
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started. OVERVIEW: As you'll get further into the hacking community, and learn more about how it's all put together, you'll also realize very quick ...more
Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself ...more
Bitcoin continues to make chaotic waves in the finance industry, with one bitcoin currently worth about $1,250 as of this writing. What's great about bitcoin is that you don't need to shell out rent money to get in the game, because bitcoins can be bought in increments—basical ...more
First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the ...more
Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?" In this tutoria ...more
Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. A ...more
Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the inf ...more
The last few months of WikiLeaks controversy has surely peaked your interest, but when viewing the WikiLeaks site, finding what you want is quite a hard task. Despite rumors of easy access via the Kindle and iTunes App Store, there currently is no way to view the leaked docum ...more
I'm sure that many of us have heard of that nasty Shellshock vulnerability, but not very many people know how to exploit it. Try these few tricks on vulnerable websites! Background Information So, what is Shellshock? Shellshock is a vulnerability in Bash shell (v1.1 to v4.3 ...more
If there ever was a time for Null Byte to need people to contribute, it's now. Let's make Null Byte a place where anyone, from novice to master computer user, come and learn. It has been sometime since the last "Call to Arms" for Null Byte, and even longer since the last "Week ...more
ProtonMail has long been the favorite of journalists and security-conscious professionals, with Edward Snowden the most famous example. But these days, everyone cares about anonymity, so it's no surprise that ProtonMail currently has over 2 million users. And now the service i ...more
Hello everyone. I'm Calypsus and i've been around for a while learning from various tutorials, expanding my knowledge and this is one of the best platforms for newbies to sharpen the skills. Today i decided to register myself and contribute to this wonderful community. Since t ...more
Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In ...more
Before I start this tutorial, no, this is not that "Effective. Power." text that is going around. With that being said, let's talk about this attack. Hello, my hacker friends! Today we are going to look at how hackers can take advantage of the system, and repeatedly crash the ...more
Anybody who spends most of their day on the internet should know all about lulz. Lulz are most often jokes made at the expense of web users, as popularized on 4Chan. Today, a consortium of hackers called LulzSec is attempting (and in some cases succeeding) in efforts to shut d ...more
Welcome back Hackers\Newbies! Hey guys first of all I would like to explain my absence here in NullByte. I got a little "occupied" with "other things". When I got back, I saw all these HowTo's, articles, Help Questions, I decided, I need to share more of what I have, to you g ...more
As you all know, Anonymous have declared cyber war on ISIS and have already proven what they are capable of and whats to come. ISIS: I don't even want to go over this section because you all know who they are, what they can do, and what they have recently done. sadly. Anony ...more
Many people think antivirus apps are useless — why pay a subscription fee when most malware can be avoided with common sense? But the thing is, there were an estimated 3.5 million malicious Android apps discovered last year, with many of them making their way onto the Play Sto ...more
Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use ...more
Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks. At the beginning I must stress that this article is not technical - in other words if you wanna hands-on exercise, this is not article for ...more
Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this. Anonymous - What/Who Are They? A Quick introduction in case someone doesn't know what they are and who they are. Anonymous is an idea. An idea of anybody who w ...more
For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for bot ...more
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law. In the United States (Where I live), the government will get involved in almost ...more
Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the co ...more
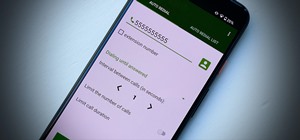
Here on nullbyte we always hear mention of hacking being used to shut down power grids or attacking SCADA and other such cyber warlord activities, but ive never seen a TDos post come up. Telephony Denial of Service involves saturating call centers or carriers, especially emer ...more
Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers. How? The attackers used a wid ...more
As you may or may not know, MegaUpload - one of the largest file sharing services has been taken down by the feds. To us - this means no more 1gb free downloads. And we move onto MediaFire and Rapidshare. - But more importantly, this means that our inherent freedom to share f ...more
PacketStorm member Ben Schmidt has found dozens of 0day's in Multiple WordPress plugins. Just another reminder to look over code yourself, because plugins are bug prone, and they are not developed by the WP authors!
Learn about the weapon effects in Dungeons & Dragons Online (DDO).
Change the appearance of the user interface for your Dungeons & Dragons Online game. This is a completely free tutorial. This site shows you where you can get the code for custom skins, and then demonstrates how to install it to customize your DDO gameplay experience.