Bad news, guys. The shelf life for liquor leftovers does not apply to your two-buck chuck. While an opened bottle of your favorite whiskey will stay respectable for ages thanks to its high ABV (which makes it inhospitable to outside elements), an opened bottle of merlot will s ...more
Link shorteners like TinyURL and Bitly are great for Twitter (or anytime you're limited on space), but they're also great for hackers. It's easy to hide a malicious link in an innocent-looking shortened URL, which increases the chances that people will click on it. Once you c ...more
In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between ...more
Recently, a user on Reddit complained that their Snapchat account had been temporarily banned because Snapchat noticed the user's account was going through a third-party service. In reality, the account in question was running on a jailbroken iPhone, and it was far from the fi ...more
For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and se ...more
Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for s ...more
The neck is one of the most important and fragile parts of the body. It has few bones and muscles and very many blood vessels and nerves, making it a natural haven for pressure points. This video will teach you how to locate and strike many of these pressure points in order to ...more
With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. ...more
With tons of titles to choose from on the iOS App Store, you'll never be lacking when it comes zombie shooters. Unfortunately, the same can't be said if you're more interested in base-building and defending against the undead. PlayStack aims to change this, and they've soft-la ...more
Personalize your League of Legends champions by altering their skins! This method will only change their appearance for you. This shows you how to obtain custom skins and apply them to your favorite champion (or one you just want to change around). Become a champion at League ...more
Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the c ...more
You walk over to your laptop, wiggle your mouse to wake up the screen, then fire up your browser to come visit Null Byte. Catching the article about Anonymous and how they presumably will not take down the Internet, you find yourself wondering... how would someone take down th ...more
Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems ...more
This tutorial is one technique to use the full functionality of your Pi. The small size makes it ideal for inside hacks, but still has the capabilities of a average desktop or computer. I should mention that a tutorial that OTW has done, but I'm gonna take it a step further. O ...more
Microsoft's built-in antimalware solution does its best to prevent common attacks. Unfortunately for Windows 10 users, evading detection requires almost no effort at all. An attacker armed with this knowledge will easily bypass security software using any number of tools. As ...more
Welcome back, my hacker novitiates! Now, and more so in the future, wars will be fought hacker v. hacker. The number of soldiers, guns, tanks, and ships will be less important in your success in warfare than the number of well-trained hackers you have. Every nation and every ...more
With the release of the Pixel 2 XL and the iPhone X, smartphones have hit a new high not just in price, but also raw processing power. These new flagships not only cost more than twice as much as an Xbox One or PlayStation 4, they have also become almost as powerful as far as ...more
Unfortunately, toxic and belligerent people are not as avoidable as we would like for them to be. They show up in our work place, schools, neighborhoods—sometimes even within our own circle of friends and family members. The best we can do is minimize our interactions with the ...more
Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positi ...more
If there's one strength of Apple's that iOS and Android fans can agree on, it's the company's dedication to user privacy. With each new iteration of iOS, Apple builds upon these foundations, enhancing and increasing each iPhone's ability to protect its user's data. In iOS 12, ...more
Making a video game requires an incredible amount of work. It requires people skilled in many disciplines to work together for thousands of hours merging visual art, computer programming, game design, sound design, and music composition into a fun game. The Indie Stone is a Sc ...more
Notes: My guides are setup like old Lego instruction booklets; picture intense/text lacking. Just remember you're building from the ground up, each step is a layer to go onto the previous layer. Any stone block can be replaced with blocks of your choice. Mycelium is used in ...more
Is that House? Built in Minecraft? Well, time to cross out one more item off my bucket list! As inspiration for this week's Minecraft-themed Tuesday Giveaway (enter here to win an awesome Minecraft Pickaxe!), I present a roundup of amazing things found in Minecraft. The great ...more
Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. M ...more
Steam has been a game-changer in the PC indie game market over the last eight years, making smaller games available to millions of users at lower prices than ever before. And few times in those eight years have there been as much indie awesomeness on sale for as little money a ...more
Dispensers are a new feature of Minecraft, and you can use about ten of them, combined with quite a lot of redstone, to build a cannon (or ballista) that can fire ten arrows at a time. Perfect for home defense!
As we've seen with other tools and utilities, administrators typically use certain things to do their job more efficiently, and those things are often abused by attackers for exploitation. After all, hacking is just the process of getting a computer to do things in unexpected ...more
So You're New to Counter Strike Source? So you're new to Counter Strike Source and you want to improve your gameplay? Great. You've come to the right place. The first step to improving your game is to admit that you are a NEWB or NEWBIE. Do not confuse this with NOOB. A "new ...more
Who says bourbon can't be a ladies' liquor? Next time you're hosting a dinner party, pick up a mix of berries at your local grocery store. The delicious fruit will highlight the earthy flavors of your favorite bourbon whiskey, resulting in a wonderfully tart and smooth aperiti ...more
When you think about it, isn't life just one big open-world RPG just begging to be conquered? We all have a set number of specific tasks or chores we must complete every single day like clockwork. Sometimes, these items on our to-do list can become tedious and cause us to lose ...more
This past weekend, one of the most notorious hacker organizations in the world, Hacking Team, was hacked by some unknown organization. The Hacking Team is an Italian company that sells it software and services to companies and governments (yes, my rookie hackers, there are leg ...more
Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to prote ...more
We often discuss the augmented reality efforts coming from the biggest players in Silicon Valley like Google, Facebook, Apple, and others, but one name that keeps coming up when you really begin to dig into the AR space is Vuzix. Since the late '90s, the company has quietly bu ...more
If it has an internet connection, it's got a huge attack surface for hackers. But what makes your phone even more dangerous is its portability and the collection of sensors it houses that can be just as good at tracking you as the camera and mic. That is why one of the first ...more
+Nik Cubrilovic discovered last week that Facebook could track your web activities even after you logged out of your Facebook account. After some blatant denials from Facebook spokespeople, Facebook decided to fix the logout issue, but not before +Michael Arrington, on his new ...more
When it comes to busted smartphones, liquid damage ranks right up there with shattered screens as one of the most common issues owners have to deal with—as well as the most embarrassing. Thankfully, though, with the rise of waterproof phones such as the Samsung Galaxy S7 and e ...more
There is a huge myth that most Americans believe, and it might be the marketing triumph of the 20th century. We pay an absurd markup (Zero Hedge says as much as 280,000% for "designer" water) on something we can get for free because most of us believe that bottled water is hea ...more
If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?" Many of the top names in the industry from the 2018 edition remain the same, but their positions have shuffled. The p ...more
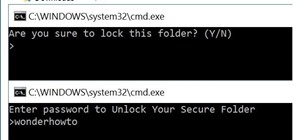
You want to put out a live web server, but you don't want to be owned in the process. An expert eye for security is not needed if you take a few basic steps in locking down the hatches. Most successful attacks today are not the complex, time-consuming tasks you might think, bu ...more
The last few months of WikiLeaks controversy has surely peaked your interest, but when viewing the WikiLeaks site, finding what you want is quite a hard task. Despite rumors of easy access via the Kindle and iTunes App Store, there currently is no way to view the leaked docum ...more
Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array o ...more
Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced. In addition to learn ...more
Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn fro ...more
Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored compute ...more
Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use y ...more
If you're a frequenter of Null Byte, I bet you have at least some interest in information security. Furthermore, you have a hobby that if applied in certain ways, will get you arrested. I've received quite a few messages from the community here about federal cybercrime law and ...more
If you love playing those WarCraft and StarCraft strategy games on your PC, chances are you've also heard of a game called League of Legends. In fact, League of Legends was originally inspired by the Defense of the Ancients map, commonly referred to as DotA, in WarCraft III: ...more
The Null Byte community is all about learning white hat hacking skills. In part, this is because I believe that hacking skills will become the most valuable and important skill set of the 21st century. This week, The U.S. Department of Defense confirmed my belief by announcin ...more
The indie game scene is constantly expanding, but in 2008, Minecraft, Braid and Angry Birds had not been released, along with all of the other indie games that established the financial viability of the format. Indie games were the all-but-exclusive purview of free Flash game ...more
Hello, everyone. My friend and I recently released a Defense of the Ancients (DotA) map that went viral and thought I should share it with Minecraft World on WonderHowTo since you guys helped me out when I first started making videos! We were featured on Kotaku, RockPaperShotg ...more
You're walking down the street, minding your own business. Then you see it—a large, bright fireball in the near distance. A tremendous heat wave speeds towards you at one thousand miles an hour, and before you can think, before you can even blink, the extremely heated wind pus ...more
You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay sec ...more
The year 2020 was a pivotal span of time during which the word "virtual" took on a brand new meaning. Instead of referring to VR or augmented reality, the term was hijacked to describe meeting across long distances through a variety of software tools, most often through video. ...more
The last iOS software update was a modest one, but iOS 17.4 has a lot more for your iPhone, including changes to emoji, Podcasts, security, Safari, widgets, Apple Cash, CarPlay, and more. Many of the exciting changes in iOS 17.4, as well as iPadOS 17.4, apply to users in the ...more
One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security. There are a number of steps you can take to i ...more
In our media-enriched world, past and present, SCRABBLE has made a name for itself, whether deliberately, subconsciously, or influentially. You may have a read a book that had the popular word game within a chapter, watched a movie that showed your favorite characters bringing ...more
After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that ...more
I don't know how many of you had this experience in your youth, but when I was a kid, I used to actively think about what would happen if I suddenly woke up in a fantasy land, or were to pass through a portal into another space and time. I knew it wouldn't really happen, but w ...more
Even if you're not a graphic artist, you can still use Photoshop to recolor the available skins for your League of Legends character. This tutorial shows you the tools and techniques to create your own skins for your favorite champion. Become a champion at League of Legends. ...more
Tonight is the night. Christmas Eve. The night where Santa Claus and his trusty reindeer soar across the skies to deliver presents to all the good little boys and girls around the world. But tell me— do you know where Santa Claus is right now? No? But you could. Santa's work ...more