Yes, that's right: Instagram has a sneaky, inconspicuous, cryptic, hush-hush way to change its iconic, colorful icon on your Android's or iPhone's home screen and anywhere else it shows up throughout iOS. The app really outdid itself too, with 12 alternative icon designs from ...more
The Galaxy Note 20 series has one of the largest screens on any smartphone. Such a massive display not only makes it easy to enjoy videos, but it also makes split-screen mode more viable, as each half of the screen is large enough to enjoy the content — including two different ...more
Apple released the first beta for iOS 14.2 to iPhone developers on Thursday, Sept. 17. A significant new feature that iOS 14.2 brings to the table is a new Control Center tile for Shazam music recognition. A simple tap of the tile will launch the operating system's built-in Sh ...more
Dreaming up the next big business is easy. Running day-to-day administrative tasks is not. The tedious nature of entrepreneurship is the barrier that holds many people back from realizing their full potential. Sellful was created with you in mind. The powerful platform comes ...more
If you've ever received an email only to focus on the sender's signature — the hi-res image, the sharp design, the vibrant colors — you're not alone. Humans are visual creatures, and with something as ubiquitous as emails, it helps to stand out. Up-level your email game with ...more
If you're an aspiring or even well-established web or app developer, the good news is that there's a virtually limitless number of lucrative opportunities waiting for you, regardless of whether you're looking to work for a company or as a freelancer. The bad news is that comp ...more
Not including playback speed controls in a video app is a design flaw. These controls are useful tools that let you speed up or slow it down a video. Want to catch all the Easter eggs in Avengers: Infinity Wars? Slow it down. Want to rewatch the last season of Strangers Things ...more
Google's 2020 Pixel Buds are one of the hottest true wireless earbuds of the year. With their unique, circular design, they stand out from the long-stemmed AirPods look you get from other wireless earbuds. The design is also sleek and minimal, making them the perfect candidate ...more
If you're in the market for a new smartphone, there are some pretty fantastic options for $400 or less. Both Apple and Google have unveiled budget smartphones with high-end specs in 2020, so you no longer have to suffer from subpar quality to save a few bucks. Low prices no lo ...more
I've been steadily making my way through the series Hannibal, which arrived on Netflix in June. I've just now made it to the back half of the third season, which introduces us to a new villain who (spoiler alert) seeks to become the Great Red Dragon. So, imagine my delight up ...more
Apple just released the GM (golden master) for iOS 13.6 today, Thursday, July 9. The update comes nine days after Apple released the third developer and public betas for 13.6, and the same day as the release of iOS 14 public beta 2. Apple released this update at 10 a.m. PDT, ...more
Since its original release as a spreadsheet program called Multiplan in 1982, Microsoft Excel has become the world's premier business software. If you think that it's only good for spreadsheets, you haven't been paying enough attention. The Complete Excel Pro Tips Certificati ...more
It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement. Whether you are a journalist, a protestor, or a hi ...more
As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfor ...more
With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating dat ...more
In 2009, 4G LTE networks rolled out in Stockholm and Oslo, replacing 3G as a better upgrade to the mobile data technology that gives us the broadband speeds we have on our mobile devices. Over a decade later, and we have the latest, next-generation wireless network technology ...more
It's open season on Zoom, the video conferencing platform that has grown in popularity during the COVID-19 pandemic but has come under fire due to privacy issues. First, Google has opened up Meet, its video conferencing services for G-Suite subscribers, as a free service for ...more
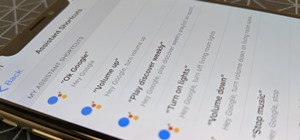
With more digital content than ever, the search feature on smart TVs is essential. But typing is such a terrible experience when you're forced to use voice dictation or peck around with the remote control. Thankfully, there's a better way. Most smart TVs support using your ph ...more
For the last three years, Apple has hosted its Worldwide Developers Conference at the San Jose Convention Center, but thanks to the COVID-19 pandemic, WWDC 2020 is now an online-only event. So what can you expect from the new virtual format and when and how can you watch the k ...more
While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups a ...more
If you're quarantining with other people, consider yourself lucky — but it's not always easy. Staying in one space for so long with too many people can be challenging, so you need to find things to do to make the time go by (and to keep everyone sane). Our advice? Try out thes ...more
It's finally here. After years of rumors and speculation, Apple unveiled the new iPhone SE on April 15. While it doesn't have a 4-inch display like the original SE, it's the smallest new iPhone you can buy today, with the chipset of the iPhone 11, 11 Pro, and 11 Pro Max. So, w ...more
We're glued to the news now more than ever, but our "free press" isn't necessarily free of charge. Cable news outlets like CNN and MSNBC are locked behind expensive cable TV packages and cord-cutting streaming subscriptions such as Sling TV and Hulu + Live TV. Luckily, there a ...more
It's not so difficult to stay at home during the coronavirus lockdown when there's so much free entertainment to take advantage of. That seems to be the M.O. for many studios and streaming services, as they've made so many shows and movies available to the public for free. Tha ...more
One of the benefits of Blu-ray and DVD is the ability to share discs with friends and family without any hassle. Want to show off your favorite movie? Just lend them your copy. A digital movie isn't so kind, as it's typically locked to the account that purchased it. But now th ...more
Your smartphone is likely full of COVID-19 news and coronavirus panic. These are scary days, and there doesn't seem to be any end in sight. If you're having trouble coping with the stress and anxiety the virus brings with it, know that your iPhone or Android device can actuall ...more
The landscape of podcasting has exploded in recent years, with everyone from dedicated longtime podcasters reaching the mainstream spotlight, to traditional media personalities moving from TV, radio, and newspapers to grab a slice of the listening pie. The good news is that th ...more
The top five apps of the 2010s were all social media apps of some kind, and the fact that's not surprising to you says a lot. We may use them for other reasons here and there, but our phones are social media machines at their cores. The thing is, some make better machines than ...more
Despite some of the biggest players in tech still lagging in terms of offering smartglasses options, there are nevertheless a number of smartglasses makers, including North and Vuzix, with consumer-grade smartglasses on the market right now. Startup Form now joins the ranks o ...more
Choosing a movie to watch at home can be incredibly difficult when you don't already have one in mind. But there's a shortcut for your iPhone that can make it easier to browse your streaming media services for something good to play. More specifically, it lets you browse Netfl ...more
The words of three of tech's most important executives in the last 48 hours are providing some valuable insight into the near term future of augmented reality and the cloud infrastructures that support it. Apple CEO Tim Cook, Google CEO Sundar Pichai, and Snap CEO Evan Spiege ...more
If you made a resolution for 2020 to get healthier, it's essential to concentrate on your mental health just as much as you do on physical fitness. Running and exercising is great, but a sound mind is integral to a healthy and balanced life, and you can improve your emotional ...more
We all want to be healthy, but in practice, it can be tricky, especially from the fitness angle. Our lives seem busier and busier, which makes hitting the gym quite the challenge. What if we told you there was a real way to work on your fitness in the comfort of your own home ...more
It seems like each day our phones become more integrated into our lives. School, work, shopping — so many tasks either require a phone or heavily benefit from one. But our phones are a double-edged sword that can easily distract us and harm our mental health as well. This is ...more
Sending Christmas cards via snail mail is so passé. Why spend the time and money for a bougie photoshoot, saccharine card design, and postage when you can use augmented reality to instantly dress up photos and videos to send to friends and family instead? Luckily, there is a ...more
One of my favorite perks of this job is the opportunity to try out all the big flagship phones each year. Whether it's rating their suitability for a particular use-case or just entering their specs into our comparison tool, we have to get our hands on all major phones release ...more
One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform t ...more
After facing reports of financial troubles over the past month, Magic Leap came out swinging this week with a big push for the enterprise segment of AR, including a repackaged Magic Leap 1, a suite of enterprise apps, and updates to Lumin OS and its supporting development ecos ...more
This week's Magic Leap Lumin OS update contained a number of goodies, including iris authentication, and a way to stream to Twitch from the device. But one new feature really stood out to me, and that's voice control of the system's interface. Don't Miss: Magic Leap Used to ...more
Along with rebranding Magic Leap 1 for enterprise customers, Magic Leap has gifted its developer community with some new toys with a tease of more to come in 2020. On Tuesday, the company not only introduced a consolidated package of new and existing developer tools that it c ...more
Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can e ...more
By now, you've probably been inundated with enough Baby Yoda memes to last you a lifetime. But if you don't have the new Disney Plus streaming service on your TV, you're probably wondering where all this is coming from. Well, lucky for you, just in time for the holiday season, ...more
This Black Friday, there are a lot of smartphone deals. Whether you're picking up a new phone or already have one, one of the first purchases you'll want to make is a protective case. And just like nearly every other item, there's plenty of money to be saved on some great phon ...more
Apple hasn't refreshed its text tones on iPhones since iOS 7. That's six years of the same sounds. And while text tones like Bamboo and Hello have undoubtedly aged like fine wine, that's still too long to live with the same old sounds day after day. Let's take matters into our ...more
In a bold move, Samsung has decided to forgo the Galaxy S11 moniker and jump straight to the S20. Perhaps it's marketing for the new 20:9 aspect ratio and 120 Hz display, or maybe it's just the fact that it's releasing in 2020. Besides the number, Samsung is borrowing from Ap ...more
If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed. Spooky Action at a Distance If you need to prove you've got remote ...more
Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target. Thanks to a pair of recon tools coded in Python, it takes just seconds to research how a website or server might be vulnerable. No matter what platform ...more
Indian startup Dimension NXG is launching augmented reality headsets into India's consumer market with a bold idea: focusing on immersive computing in education on the high-end. The plan is to give a new kind of AR headset to schoolchildren in remote Indian villages, starting ...more
The Galaxy Note 10+ is the pinnacle of Android hardware. You won't find many phones with a better combination of specs and design. But you may not love the software. Even with One UI on board, some users still want a more "stock" feel. Thanks to apps from third-party develope ...more
So you can't figure which one to buy. It's understandable. Apple released three iPhones, each designed for a different segment of the market. But which one is right for you? The iPhone 11, iPhone 11 Pro, or iPhone 11 Pro Max? That's a good question. We recommend checking out ...more
So the new iPhones have arrived. Like last year, Apple released three iPhones in three different sizes that vary in price and specs. There's the base model iPhone 11, and then there are the real deal, premium models, the iPhone 11 Pro and Pro Max. The iPhone 11 Pro and 11 Pro ...more
They're finally here. Apple revealed the brand new iPhone 11, 11 Pro, and 11 Pro Max on Sept. 10, and despite the questionable names, these are the best iPhone models money can buy. If you're looking to get your hands on one of these devices as soon as possible, there are few ...more
In our comparison of the best gaming phones in 2019, the winner actually surprised us. A phone that most people don't know about from a brand you probably haven't heard of ended up as the clear winner. But how? Well, it ticked so many flagship boxes despite its midrange price ...more
The idea of a world without passwords used to be a pipe dream. But as we inch closer to making that a reality, we have services now that securely store all of our passwords under a single master password. It's a convenient way to keep our accounts safe and sound without having ...more
If you like the "Street View" feature in Google Maps, you'll love "Look Around" in iOS 13's Apple Maps. Overall, Look Around has more details than Street View and the animations are super smooth as you navigate down streets and pedestrian areas. While Look Around isn't availab ...more
Whenever the name Magic Leap comes up, the talk inevitably seems to turn to the company's big-name backers and "unicorn-level" amounts of cash poured into the venture. And if it's not that, observers tend to focus on the company's market strategy and overall prospects. These ...more
What if, back in 2013, Google Glass had launched not as a Star Trek Borg-like eyepiece, but as a pair of seemingly normal shades, with the augmented reality lens and camera hidden within the frame? Google Glass has been almost permanently tagged with the "glasshole" moniker, ...more
We've already shown you our favorite new action games that have come out this year, but now it's time to share our all-time top ten list. These games are available for both Android and iPhone, they don't have intrusive ads or freemium schemes, and most importantly, they're all ...more
Nintendo may be developing cases that'll turn your iPhone into a gaming device like the Game Boy, but until something materializes there, you're stuck with cheap knockoffs on Amazon or a real Game Boy or Game Boy Color. But there's something else you can do to play eight-bit N ...more
Why do you need augmented reality? Because enterprise, they say. And while that's certainly true for several disciplines, there's still that mainstream use case hanging out there waiting for users to discover beyond the realm of enterprise and gaming. After much thought — and ...more