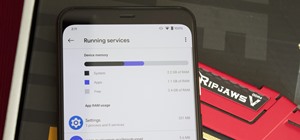
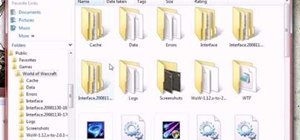
Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key. Now that all of the data on Evil Corp's serv ...more
Trojans, viruses, and malware can be more than a simple nuisance to your computer--they can destroy data and ruin your system. This video tutorial shows how to get rid of malicious software on your computer. When combating a virus, it's best to use multiple applications to ins ...more
With the mass arrests of 25 anons in Europe and South America, and the rumors of an FBI sweep on the east coast of America floating around, times look dicey for hackers. Over the past few days, a lot of questions have been posed to me about removing sensitive data from hard dr ...more
Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimat ...more
The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you n ...more
No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the In ...more
As a web developer, I often read articles about hackers (from the lowly to the knowledgeable) infiltrating websites via the dreaded 'SQL Injection' method and completely taking control, changing, gaining access, or destroying the owner's data. As a fellow web developer, I'm su ...more
Dual booting Ubuntu 10.10 Maverick Meerkat and Windows 7 is fairly easy. If you don't believe me, just read on! Get Windows 7 First thing's first! Ye can't install Windows 7 without an installation disk, can ya? So if your PC did not come with Windows 7 pre-installed, grab a ...more
Destroy Black Ops Noobs First of all, these tips are great for any consoles that run Black Ops. Whether it be your Sony PS3, Nintendo Wii, XBox 360 or your PC. Internet Connection Before you put the game in to your console, make sure that your internet connection is consist ...more
Tetherd Cow Ahead posts an interesting science experiment. All you really need is a little bit of iron powder and a magnet, and you can unveil the info behind the magstripe on a credit card. You will need: A small amount of fine iron powder or iron oxide A magnet An old cre ...more
Oh no! You've just accidentally deleted an important computer file! Have no fear. When you delete a file on your computer, it is not necessarily destroyed. This video will show you how to search for and restore your file before it is lost forever. You Will Need * A PC or Mac c ...more
By now, you probably know that your iPhone secretly tracks and stores the locations you've visited in a backup folder on your computer's hard drive. The files are unencrypted, which means anyone with access to your computer or device can retrieve the information, which is down ...more
New to Windows? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to protect Windows from viruses without an antivirus software. There are many different ways to classify viruses, and each of t ...more
About Today's topic Today we will talk about diagnosing and fixing connection problems. Let's face it - the truth is everyone who uses a computer and has an internet connection will have to deal with this at some point. Connection problems often occur at the wrong time and it ...more
Since the day of the Xbox 360 release, storage space for the device has been overpriced beyond belief. OEM 250GB HDD models still cost $110 USD! A 250GB hard drive should not destroy my wallet, Microsoft. Storage space, especially on HDDs, is cheap. You can buy a removable 2TB ...more
Warnings i cant be held responsible for any illegal act done by anyone but myself and there are copyrights so notise that taken the trademarks or copyrights are strigtly prohibeted by law and will be punshied by law and i or my partners cant be held responsible for sudo camma ...more
Nobody likes it when a prank gets taken too far. Friendships are ruined, material possessions destroyed, even bodies broken. This video offers four perfect examples of pranks that go entirely too far and that you SHOULD NOT DO to your friends and neighbors. We're being serious ...more
Welcome to the final tutorial of the series on standard C. This article will cover the linked list abstract data type (ADT). There will be a lot of abstraction to try to deliver the understanding in the most basic way for easiest interpretation of what they are and how they wo ...more
In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that A ...more
What's up readers? We have ever so slightly touched upon this concept of scope with variables but still don't really know what it means. In this tutorial we will learn the behaviors of variables existing in our programs and within functions. What Is a Variable Scope? A scope ...more
In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberw ...more
There are two types of bad USBs out there. One lets you trick the computer into thinking it's a keyboard or other USB device, and the other goes straight over malicious into computer killing territory. Last year, Russian security researcher Dark Purple designed a USB stick th ...more
It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the ...more
Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privac ...more
Google's former driverless car boss Chris Urmson raised considerable funds to get his new startup company Aurora Innovation up and running. Axios initially reported that Urmson raised over $3 million to fund his brainchild in the wake of his Alphabet exit, according to an SEC ...more
Welcome back Hackers\Newbies! Hey guys first of all I would like to explain my absence here in NullByte. I got a little "occupied" with "other things". When I got back, I saw all these HowTo's, articles, Help Questions, I decided, I need to share more of what I have, to you g ...more
Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc. Maybe you forgot or lost the password to your Windows Admin account, this guide wi ...more
One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a les ...more
Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker. FileVault, created by Apple in 2003, is a hard ...more
The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practic ...more
Google Maps, once considered superior to Apple Maps, has contributed to a terrible mistake for one woman. A group of demolition workers in Texas were using the service to find a worksite, and to the dismay of homeowner Lindsay Diaz, Google was entirely inaccurate. The home sc ...more
No one likes in-app advertisements, especially in mobile gaming, but they're necessary because they offer developers a way to make revenue without having to charge you to play. In some games, in-app purchases give you the chance to remove ads, but what can you do about apps th ...more
With the news that Cambridge Analytica obtained over 50 million Facebook users' information without their consent, there are no doubt many of us considering that terrifying yet alluring endgame — deleting Facebook. While difficult to figure out, deleting your Facebook account ...more
A virus easily spread among trout and salmon could make it harder to keep your favorite fish on the menu. The image of dead and dying fish below is from a fish hatchery in the middle of an epidemic of infectious hematopoietic necrosis virus (IHNV). The easily transmitted viru ...more
A young child becomes very thirsty very often and seems tired all the time. A visit to the pediatrician determines she has type 1 diabetes. The onset of type 1 diabetes may seem sudden, and it can be, but the disease may actually have been triggered by common childhood viruses ...more
Microsoft's HoloLens is certainly a leap into the future of mixed reality interfaces, but it's not without drawbacks. Its most notable drawback is its small field of view, cutting off objects you feel like you should be able to see. But there's good reason for that limitation ...more
You can beef up the security on your Mac all you want, but all the firewalls and antivirus apps in the world mean nothing when that can of soda tips over on your Macbook, destroying your laptop and all its data forever. You may have some of your data backed up to a cloud serv ...more
Most mobile games have moved to an online-only format, meaning you need to be connected to the Internet in order to get any kind of multiplayer action going. This is great when you're at home on Wi-Fi, but when you're out and about, slow and inconsistent data speeds can cause ...more
Okay, so you're rooted and need to return your Nexus 5 to its stock firmware. Whether it's because you need to send your phone in to the manufacturer to fix a defect or you just want to use the device's over-the-air updating feature, unrooting and returning your Nexus 5 back t ...more
As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers. While companies like Facebook, Snap, and Twitter do a formidable job against the waves of attacks they receive daily, they are no ...more
It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploi ...more
Firefox Focus has been out for iOS for a while now, so it's about time Mozilla began porting the app over to Android. It's an amazingly private browser that protects you from trackers and ads when you're surfing the web. It blocks a wide range of online trackers, erases your b ...more
Oh no... your precious iPhone is in shambles. Maybe you shattered your screen after a crazy night of celebrating, or maybe your two-year-old jabbed a toy into your iPhone's charging port, completely destroying it in the process. Now what? Do you take it to a repair shop, or go ...more
Welcome to a tutorial explaining functions. This article will help clarify some things we have already been exposed to such as function prototypes, function calls, return values, etc. What Is a Function? A function is a type of routine which has its own defined set of proced ...more
For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application tha ...more
It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept. In bot ...more
Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don' ...more
It looks like Chris Urmson has spent the six months since he left Google's Self Driving Car Project trying to build a get-rich-quick self-driving unicorn, along with Sterling Anderson, formerly with Tesla Motors. At least that is one of several scandalous accusations in a Tesl ...more
Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show. What Is a Buffer Over ...more
It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography. In this article, I will ...more
So you've been playing Call of Duty Mobile for some time but can't seem to get MVP at the end of the battle. Well, since the game is a competition of players and bots, you're in an uphill battle. But you don't have to languish at the bottom. With the help of these tips, you mi ...more
In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux. With each Pi more powerful and cheaper than the last, the addition of the Pi Zero in 2015 too ...more
Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop. Today's Topic Today we are going to complete t ...more
Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering. One such distribution is Pentoo, a Gentoo-b ...more
We've worked hard to reduce the flow of toxic chemicals into our waterways, which means no more DDT and other bad actors to pollute or destroy wildlife and our health. But one observation has been plaguing scientists for decades: Why are large quantities of one toxic chemical ...more
Transmitted by a sandfly one-third the size of a mosquito, parasitic Leishmania protozoa are responsible for a flesh-destroying disease that kills an estimated 20,000 people per year. Two new studies offer understanding of how the parasite provides immunity through persistence ...more
Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in! Recap In the previous tutorial, we learned how to write a program which opened itself for reading to write to a host file, overwritin ...more
Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them ...more
A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts f ...more
Regarding foodborne pathogens, eating fish is not as hazardous as it was a few years ago — but if fins are on the menu, it's good to have a heads-up about what's good and what's bad these days. Fish are typically considered a healthy, recommended food — except when they aren' ...more