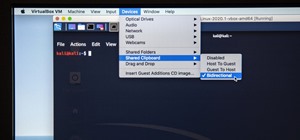
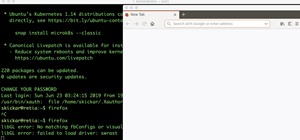
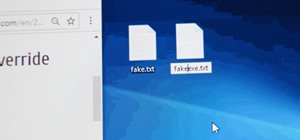
With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer. In my last series, we used a Post-it note to trick a neighbor into visiting a website that we cont ...more
Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or datab ...more
Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look ...more
With more and more phones using OLED displays, the need for dark mode is at the highest it's ever been. Since dark backgrounds reduce battery consumption on these displays, the Android community has been begging Google to include a system-wide dark mode. Instead, Google gave u ...more
Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one ...more
Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack. That's because the database—alm ...more
If bourbon is a man's drink, what better flavor to infuse it with than bacon? The combination tastes just as delicious as it sounds—a smokey, salty aftertaste lingering after each sip of deep, rich bourbon. To infuse bourbon with bacon is simpler than it sounds. All you need ...more
Just when you begin to doubt the future of humanity, advances in ice cream scooping science continue to develop. Yumi showed you some super-cool ice cream hacks just in time for summer, and we've already discussed how to use a knife to slice ice cream when it's too hard to sco ...more
Safari's advanced experimental features give you access to new browser initiatives, upcoming web tools, element changes, behavior adjustments, and other preliminary feature tests in development by Apple. If you use them on your iPhone, you can either improve your Safari experi ...more
Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, ...more
Expressing yourself during chats is much easier these days thanks to the steady rise of emoji. Now, products like emoji Minis for Gboard are taking the craft to an interesting yet familiar new level. With emoji Minis, you can automatically create stickers based off your own fa ...more
Foodborne infections often occur through the contamination of equipment, food-prep tools, and unsanitary surfaces. A recent report from the Centers for Disease Control and Prevention (CDC) reminds us that breast pump parts are part of the food-delivery chain — and they can bec ...more
Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. ...more
Check out this video on cricket bowling drills. Develop your Cricket Bowling with this video that gives good information on some useful bowling drills for cricket players and those coaching. Check out The Cricket School's sports drills and lessons. Learn new cricketing skills ...more
BlinkFeed completely changed the way I access new updates from Facebook and Twitter, but when I switched to the Google Play Edition of the HTC One, I lost access to the launcher. BlinkFeed is available in the Google Play Store, but HTC has not opened it up yet for all devices ...more
Hello readers, and welcome to Null Byte. Before we start, for those of you who may not know me, my name is ghost_; I'm a relatively active member of our community and have been around for a while. During my time here, I've seen our community cultivate into the brilliant one ...more
Random vibrations, ghost buzzing — whatever you call it, when your phone goes off for seemingly no reason, it's pretty frustrating. Finding the source of a phantom vibration can be almost impossible if there's no associated notification, especially given the myriad apps and sy ...more
In a previous article, I pointed out a few criticisms of the Google Play Store, mostly about how unpolished and inefficient it is. To give you a better idea of what I mean, here are just a few of my complaints with the Play Store: No app review process Any app can be in the s ...more
Welcome back, my greenhorn hackers! This tutorial will be the fourtenth in the Linux for hackers series and will focus on the MySQL database. Although this is not strictly a Linux tutorial, MySQL is the database of choice on most Linux distributions. In addition, it is the mo ...more
Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you ...more
Someone does't really like you. I don't know who or where they are, but they exist. If you want to change that, simply ask them to do you a favor. This trick is known as the "Benjamin Franklin Effect." The idea is that when someone who views you unfavorably performs a favor f ...more
While we shouldn't rely on it, every so often we need to hit the snooze button to get a few additional minutes of precious sleep. Depending on which OEM skin is running on your device, this could be either five or ten extra minutes of dozing. However, some of us need a differe ...more
No matter your reason, if you want to hide what's on your computer screen from prying eyes, there are plenty of ways to do it. You can get a privacy filter, install a panic button for your browser, or just develop super fast reflexes. But all it takes is the right angle or a t ...more
Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone ...more
Your brain holds a lot of precious information and is capable of great feats. However, there's one quality that doesn't lie among its strengths—memory security. Yes, that's right, your brain can be hacked, and it doesn't take a psychologist to do it. Anyone with the right know ...more
Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear ...more
Biting into a perfectly ripened piece of fruit is enough to convince you to give up baked goods and plant your own garden. The combination of flavor, juice, and sweetness in a ripe mango, apple, plum, or berry is the stuff of life itself. Alas, most people don't know how to c ...more
The fastest and easiest way to improve your handwriting is to learn to hold your pencil properly. A lot of people bypass this seemingly small step and then wonder why their writing looks like chicken scratch. This video will show you exactly how to hold your pen or pencil for ...more
Why make a flip book? Because all animation – even stick-figure Flash animation and multilayered, highly technical 3-D effects – is built on, and can benefit from, the basics of the craft first developed by artists working at the beginning of the last century. And while fancy ...more
Learn how to tell if you’re turning someone on — or off — by watching the way their body involuntarily reacts to you. Did you know? If a person you're flirting with develops pigeon feet (their toes start pointing inward towards one another), that person is both attracted to yo ...more
The CV axles (halfshafts) on your front-wheel drive car can develop a rip or leak pretty easily, leading to noisy driving and eventually axle unreliability. Watch this video for step-by-step instructions on how to remove and install a CV halfshaft.
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started. OVERVIEW: As you'll get further into the hacking community, and learn more about how it's all put together, you'll also realize very quick ...more
Three years ago, Scrabble was one of the very first 500 mobile applications to appear on the new iTunes App Store, allowing iPhone users the chance to kill their Scrabble cravings on the go. It was a smart move for Hasbro and Electronic Arts (EA), but it's been two years and e ...more
The first thing I do when I wake up in the morning is run to the kitchen to make coffee, and I know I'm not the only one. According to a survey by the National Coffee Association (yes, there's such a thing), 83% of Americans drink coffee, and I'd bet most of that consumption h ...more
The rocket stove, invented by Dr. Larry Winiarski, was developed to require much less cooking fuel than a traditional stove. The rocket stove also emits less dangerously, as most of the energy burned turns into heat. To build this rocket stove, you will need sheet metal or a 5 ...more
Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private ...more
The herpes simplex virus (HSV) can cause devastating complications for infected newborns whose mothers have genital herpes. Understanding risk and research can help you, and your baby, when the time comes. In the US, about one out of six people aged 14 to 49 have genital herp ...more
Welcome back, my nascent hackers! One of the many reasons I write this blog is to help you keep the Internet free and open. Throughout human history, whenever a government or other powerful entity has wanted to subjugate a people or group, the first thing they do is isolate t ...more
While our smartphones are many things, one of their primary functions is to make calls. Many of us try to avoid ever having to make calls, but there are situations when it's a must, such as wishing your grandma happy Birthday or calling 911 — and in those times you want stella ...more
Traditionally, if you were looking for end-to-end encrypted messaging, you'd stick with something like iMessage, WhatsApp, or Signal. However, if you already use Facebook Messenger, you have all you need for truly private chats with its built-in E2E encryption. It's available ...more
The Xperia Z1, Sony's flagship device, has been extremely popular overseas, so much so that it has made its way into the U.S. market as the Xperia Z1S, a modified version of the original. Known more commonly as the "waterproof smartphone," the Xperia Z1 packs one of the most p ...more
No matter which smartphone you buy, it will come with an internet browser preinstalled. Depending on your OEM, the default browser might be called Samsung Internet, HTC Internet, Silk Browser by Amazon, ASUS Browser, or Google Chrome—there's just so many stock browsers availab ...more
For some, the Galaxy Note 9's volume rocker doesn't have enough steps between silent and max volume. We all have different preferences for volume, and a higher number of steps would equal to more precise volume control. Good thing we can at least adjust this for the media volu ...more
Introduction The 3 major anonymity networks on the Internet are Tor/Onionland, I2P and Freenet. If you feel confused on which one is the "best" one to use the answer is simple. Use all three! Each anonymity network is designed for a different specific purpose. One network al ...more
You love the video game Tetris and you love the puzzle Rubik's Cube, then what's stopping you from attacking the Tetris Cube? This video tutorial will help you learn how to solve the Tetris Cube puzzle, from Imagination. The object is to take apart and reassemble the twelve u ...more
I've been involved in the Android scene for a very long time and have grown to develop a love/hate relationship with CyanogenMod. While I do like the stability they offer in their custom ROMs, they don't always include the flashy features on top of their vanilla Android base. ...more
Welcome back, my novice hackers! In my continuing effort to develop your Linux skills, I now offer you this eighth in my series for Linux Basics for the Aspiring Hacker. In this tutorial, we'll look at system processes and how to manage them. In Linux, a process is a program ...more
A diary or personal blog is a great way to recapture the days behind you, but to a photographer, the best way to remember the glory days is with a picture—one single photograph that best describes the day and your mood at the time. Do it everyday for a year and you'll have 365 ...more
Just days after Google released the official Android 11 update, Samsung already had a pre-beta build of One UI 3.0 available for developers to test their apps on. So this year's main OS upgrade is likely hitting Galaxy phones even earlier than we thought. Some features in the ...more
A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physi ...more
Many modern Android devices use a display technology called AMOLED. These screens differ from traditional LCD displays in that each pixel emits its own light, so a backlight is not required. Even better, when rendering a black element on the screen, AMOLED displays simply don' ...more
With the emergence of rumors that Amazon, Google, and Samsung are all making their foray into the gaming console market, it's a possibility that our Android-powered mobile devices might become tools that play a central role. As we proceed through 2014, we'll see inklings of w ...more
Well before Magisk was in our lives, the Xposed framework was where all the mods and magic happened. Magisk was built on a similar concept with the ability to customize your system via modules. We can thank Xposed for where we are today in terms of root-related mods, but it's ...more
The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practic ...more
Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of har ...more
Like taps, radiators can develop leaks. Fortunately, these are usually really easy to fix. If you are not sure how to fix a leaking radiator valve, watch this video tutorial to learn how. Step 1: Before you start - get a spanner, some paper tissue, and some PTFE tape. Step 2 ...more
Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hid ...more
Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. Whi ...more
Bitcoin continues to make chaotic waves in the finance industry, with one bitcoin currently worth about $1,250 as of this writing. What's great about bitcoin is that you don't need to shell out rent money to get in the game, because bitcoins can be bought in increments—basical ...more
It's universally known that broccoli, kale, Brussels sprouts, cauliflower, and all cruciferous vegetables (also known as brassicas) are good for you—but you probably don't know exactly how good they really are. A recent study by Johns Hopkins University and the University of ...more