The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for ...more
If you've spotted an unintended Ethernet connection and wondered what you could do with all of the information coursing through those wires, there's an easy way to hack into it and find out. Let's say there's a router that we need to know the password for, and we have physica ...more
We happen to use an 802.11n AirPort Extreme as our router, so we put today's new firmware upgrade to the test to see if TIme Machine really does work with AirPort Disk. As expected, it works and only requires a few simple steps... First we updated our firmware using the AIrpo ...more
This video tutorial shows you how to improve the performance of your Windows XP PC by freeing up disk space. This is done by running xp's Disk Clean up utility this deletes all temporary and unwanted files that get collected on your disk. Run this utility and clean up your di ...more
In this video tutorial, viewers learn how to eject and recover a stuck CD or DVD on a Mac computer. There are several ways to eject a disc. The first method is to click on File and select Eject. The second method is to press the Command and E buttons on the keyboard. The third ...more
The guy in this video shows us how to permanently delete files on a Mac. First one would click on your desktop so the finder pops up and one would go to "utilities" and click "disk utilities". Next, one would click on the disk which they would like to clear, then click "erase" ...more
This is a tutorial video on how to use a virtual CD/DVD drive software tool called Furius ISO Mount. Furius ISO Mount is an .ISO, .IMG, .BIN, .MDF, and .NRG image management utility, that allows you to automatically mount and unmount disk image files. This utility application ...more
This is a tutorial of how to burn games to a DVD for playing on a flashed Xbox 360. Burning Xbox 360 discs will allow you to have an infinite amount of copies of the game that you love. This video makes use of several utilities which will be needed in order to follow along: ...more
This technical video will show you all about the Rohos Mini Drive. See how you may work with an encrypted partition on a PC without admin rights using this free portable encryption solution. It securely protects your portable data on any USB device. Portable utility Rohos Disk ...more
This video demonstrates how one might be able to successfully create an Ubuntu Bootable CD-ROM. The procedure described involves downloading the Ubuntu Desktop Edition Operating System image off the Ubuntu web site. In order to successfully create a usable disc, one needs to b ...more
If you're interested in bypassing Windows and Linux passwords, there is a great tool from the good people at Kryptoslogic. Have you ever forgotten your administrator password? Have you ever bought a used computer with a password on it? Well, Kryptoslogic have created a boot-di ...more
In this tutorial, we learn how to eject a CD from a Mac computer through a terminal. Now, go to the finder and click on the applications folder. Scroll down to the bottom and open up utilities, then the terminal. Once you are inside this new screen, type in "drutil tray eject" ...more
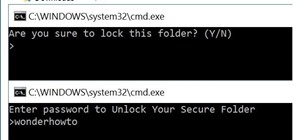
In this tutorial, we learn how to password protect a folder in Snow Leopard on your Mac. First, go to the finder and click on "utilities". Now go to "file, new, disk image from folder". Now, you can select the folder you want and then click "image". Make it a read/write folder ...more
In this Video Games video tutorial you will learn how to convert PSone games to PSP. For this you will need a 5.03 firmware update. It is capable of running ChickHEN enabler. After you upgrade, run the firmware. You will need a utility called magic ISO for ripping the discs. P ...more
If your computer is acting funky, you may need to run a full Checkdisk or chkdsk. Chkdsk is a program that is included with your Windows operating system and is meant to find and diagnose any potential problems with your PC. Check disk will find errors in your boot sector and ...more
In order to install Windows 7 from a USB drive, while you are running XP, you will need a pen drive. You will also need a Windows 7 DVD and a pen driver. Download a replacement utility. Google “MbrWiz”. Download it. Place it in a non-Windows drive. Look up the disk number ...more
STANDP'S WINDOWS 7 "ASTON-2" CUSTOMIZED DESKTOP IT ROCKS COMPLETELY!. DEC 07 Computer Backup If you have taken good care of your computer then you know what you have to do to keep it running smoothly. It has to be cleaned regularly so there isn't any dirt and dust on it. It ...more
With a lot of Null Byters playing around with Linux because of its excessive use in the hacking world, some of you are bound to run into some trouble with the installation at some point or another. If you make a mistake, or you're intimidated by the wonky-looking installation ...more
This video tutorial from bobby93macboy shows how to install Mac OS Leopard operating system and make it bootable. Hard drive partition - it's a logical sector of your whole hard disc which can be used as a separate hard disc. To make partitions, open Disc Utility using Spotl ...more
Is your SD memory card getting a little too full? Is it not working? Try reformatting it. It's the first and sometimes last step to troubleshooting card problems. So, if your SD card has become too cluttered, this guide will restore it to a like-new condition with a simple for ...more
How to Fix Windows 7 Slow Start Up Is your Windows 7 slower on start up? Wondering how to make Windows 7 super fast? There are various reasons why this operating system performs slower but one common reason is that mostly it happens because of too many start up programs and s ...more
This tutorial will be based on creating a partition in Windows Seven. I have seen so many people attempt to do this themselves without guidance. Ultimately, they end up with a corrupt system. The aim of this tutorial is to make sure you don't corrupt your system. What does th ...more
Flash memory can be a tad unpredictable at times. I have had 4 flash drives die out on me over the last few years, and they usually die without warning. When a flash memory based device dies, the data is likely impossible to recover. Adversely on an HDD, or Hard Drive Disk, ev ...more
USE WINDOWS 7 ULTIMATE x64 w/ all the latest updates always OF COURSE AND... USE THE ASTON 2 SHELL REPLACEMENT, MENU, DESKTOP, W/ THEMES... USE EASEUS DATA RECOVERY WIZARD V5+... USE FROSTWIRE P2P FILE SHARING CLIENT... USE INCREDIMAIL 2 (LATEST)... USE SAFARI (ONE OF THE ...more
If you thought the last post on Two Circle Wobblers was wild, then wait until you see what happens when you build wobblers out of two half circles or two ellipses. In both of these cases, the center of gravity still remains constant in the vertical direction, allowing them to ...more
One of my favorite simple projects is building two circle wobblers. I love how such a simple object amazes with its motion. The two circle wobbler is an object made out of two circles connected to each other in such a way that the center of mass of the object doesn't move up o ...more
Computer crashes, fried hard drives, red rings of death, delinquent memory cards... nothing is worse than dysfunctional technology. In just a minute, your favorite and most used device has become the biggest headache of your life, frustrating you to the brink of madness. But w ...more
STANDP'S CUSTOM DESKTOP "ASK NOT WHAT YOUR DESKTOP CAN DO FOR YOU...". http://standp-how-to-vidzzz.wonderhowto.com/corkboard/new-post/text/ Showing newest posts with label tips-n-trick. Show older posts DEC 07 Computer Backup If you have taken good care of your computer th ...more
Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pen ...more
It's officially the holiday season, which means everyone will soon be traveling home to spend time with loved ones. And anyone who has any knowledge whatsoever of computers knows what else that means—family members left and right asking you to fix their various technical woes. ...more
The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already bu ...more
Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the prev ...more
Hello, my fellow hackers. My name is cl0ck. I am a senior majoring in Computer Engineering with an emphasis is Security. I have been lurking the site for a while now reading and learning from the great minds that reside here. I, too, have some knowledge that I would like to s ...more
OS X is built upon a UNIX foundation, which grants you access to the benefits that UNIX offers, including the standard toolkit (make, gcc, clang, git, perl, svn, size, strings, id, and a lot more) via the command line developer tools, which are an essential if you're a develop ...more
Just recently, I was experimenting with a dual-boot Windows setup, and somehow managed to wipe my primary Windows installation in the process. "Why," I asked myself, "Why didn't I make a backup before I started this?" Still to this day, I'm going through the painstaking proces ...more
While it hasn't gotten as much attention as iOS 10, Apple's big 10.12 update to their Mac operating system is finally out for all to enjoy—and you can download it for free from the Mac App Store right now. Don't Miss: 60+ Cool New Features in iOS 10 Siri is definitely the m ...more
If you've been around computers long enough, you've probably heard the phrase "have you tried turning it off and on again?" This trick usually works because it forces your computer to empty out the contents of its RAM and disk caches when you restart. When you run programs an ...more
Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of har ...more
Apple's iOS 18.2, iPadOS 18.2, and macOS Sequoia 15.2 updates are here, packed with enhancements that take device intelligence to the next level. New Apple Intelligence features lead the release, offering smarter tools for creativity, productivity, and everyday tasks. However, ...more
Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. T ...more
OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time- ...more
This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but ...more
Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... ...more
Hello, Null Byte! Mkilic here. I doubt anyone knows I even exist on Null Byte, so hopefully this post will allow me to become more involved in the community and also help me learn even more. This project is somewhat similar to OTW's article here, and pry0cc's here, in which b ...more
The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant b ...more
A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge. The goal in this article is to acquire a target's .plist file which contains the ...more
Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker. FileVault, created by Apple in 2003, is a hard ...more
In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied togethe ...more
Now that we've talked about encryption and managing your passwords, let's continue this series on getting your Mac ready for hacking by turning our attention to the terminal. The terminal is a key component of any pentester's setup. We're going to be spending a lot of time wo ...more
Welcome, in this tutorial we shall we looking at creating a safe(r) way to back up your important files. The contents we will be covering are as follows; Creating a partition Updating the /etc/fstab file Mounting a file system with Python Copying the contents of a file system ...more
Windows 10 is officially here, and frankly, there's a ton of new features in Microsoft's latest operating system. From the return of the Start menu to the new Edge browser, Windows 10 can take some getting used to. Luckily, we've done a lot of the leg work for you, and what f ...more
Chief among iOS 14's excellent new features is the overhauled home screen. Now, you can add customizable widgets that live alongside your traditional apps, and both first-party and third-party apps can take advantage of it. Talk about an upgrade. They even work in the Today Vi ...more
Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering. One such distribution is Pentoo, a Gentoo-b ...more
A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data. The ...more
Kali Linux is the go-to Linux distribution for penetration testing and ethical hacking. Still, it's not recommended for day-to-day use, such as responding to emails, playing games, or checking Facebook. That's why it's better to run your Kali Linux system from a bootable USB d ...more
At first, it may look like it's mostly a behind-the-scenes update, but iOS 14 public beta 6 is more than just that. The biggest addition to iOS 14 for iPhone in this version is the beginning of Spatial Audio, an AirPods Pro feature. Other notable changes in beta 6 appear in Ma ...more
At first, Apple's six developer beta for iOS 14 isn't much to look at, but there wouldn't have been an update if there weren't some important issues to address. Most of the serious updates in build number 18A5357e revolve around SwiftUI, which even has a few new features, and ...more