Confidence A key ingredient to building any relationship is having the confidence to ask any given woman out in the first place. Women find confidence in a man more attractive than his looks, and at first, even his personality (you will, however, have to have a good personali ...more
So, at this time of the year, everyone seems to be going through a lot of stress - and by “everyone,” I mean, “anyone who has any contact with people who are in schools of any kind.” Still, stress can hit you at any time of the year, whether it’s right before Christmas, or whe ...more
Skyrim is an enormous RPG recently released by Bethesda. After many long years of waiting (I had 1000's of hours clocked into its predecessor, Oblivion, way back in 8th grade) the game is finally out and it surpasses everyone's expectations—save for removing custom spell craft ...more
Hey, hackers! Now that you've hacked/owned your first "box" in my last article, let's look a little closer at another great feature of Metasploit, the Meterpreter, and then let’s move on to hacking a Linux system and using the Meterpreter to control and own it. Why Meterprete ...more
SSH is what is referred to as the Secure SHell protocol. SSH allows you to do a plethora of great things over a network, all while being heavily encrypted. You can make a remote accessible shell on your home computer that gives you access to all your files at home, and you can ...more
No game is perfect. Well maybe except for Super Mario Brothers 3. In the last two posts I've been praising Tera but it's not without its shortcomings. Basic quest system: Playing the game in Korean and without understanding a single world I’ve managed to complete 95% of the ...more
I've decided to write this post so some of the fledgling street artists who may or may not follow this world in the future are informed about two things in the urban art world that are either not discussed at all, or distorted (intentionally or otherwise) to the point of misin ...more
to be honest with everyone, this is probably the first thing ive written about magic the gathering, but i figured i might as well start somewhere. in the game of magic the gathering there are countless different keywords, some being common, like trample, or rarely used or seen ...more
It could be said that the World Cup really starts during the knock-out stages. What was going on for the last couple of weeks was more like the "World's Soccer Fair." At least I'd like to think of it this way after watching games like Slovenia vs. Algeria, New Zealand vs. Slov ...more
In this video from nmsuaces we learn how to identify problems with weevils and leaf cutter bees. Weevils attack all kinds of plants in a J shape on leaves. To tell a difference between a weevil and leaf cutter bee is the bee will make a perfect round cut, whereas a weevil make ...more
Get ready for car throwing in this Shadow Arena Challenge in the Drowned Pass on the Xbox 360 game Darksiders. You need to enter the Shadow Realm and defeat four portals to free Vulgrim. For World of Pain, you must kill 15 enemies using environmental weapon attacks within the ...more
Play Along: At the start of the mission, you simply need to follow the leader through the city. Do your best not to bump into anyone, as Ezio will drop the chest if you do. Eventually, you read the end of the trail and a cut scene takes over. Now the mission gets serious. You ...more
People sometimes ask me about the IT industry here in the states. These folks are usually either trying to get into a certain field, or looking to switch or move into another one. Right now, you may currently be a Computer Science major that will be graduating shortly and are ...more
Imagine you're in Paris and you need to get to Versailles. Looking around for directions, you come to a cold realization—you do not speak a lick of French! How are you going to get to Versailles and what happens if there is a detour? It will be a difficult struggle, and you'd ...more
Story, Characters, and Structure Note: The first half of this review is spoiler free. There are spoiler warnings once you approach the later parts of the review. If you’re curious of the game but don’t want to be spoiled, just read the first half. For those of you that have f ...more
Who hasn't gone mad trying to fix his/her computer, trying to delete all of the harmful software? It may not be funny with a real virus, but a fake one is. Or course, you can make a simple virus just with Notepad. There's no need to download applications to fool others; in les ...more
Our mission for this week's Community Byte was to create a Python program to crack web-based passwords, like the ones you would see on an email or router login. I wanted it to be universal in the sense that it could be easily modified and adapted to another website just by cha ...more
There is a near-infinite amount of ways a computer can be broken into. But that does not mean that there isn't a reason to secure our computers as best as we possibly can. It's like the principles of a secure house. Which are the most secure houses? The ones with locks and adv ...more
This is the first of a multi-part series on steganography techniques. Steganography, the art of hiding things in plain sight, has existed for a long time, and in many forms. When you manipulate the alphabet to have your own cipher and decipher, this is considered steganography ...more
Behavioral ad targeting companies are diving deeper into the realms of your subconscious with a new approach to serving adverts to you online—and they're using your television. Many web surfers peruse the internet at home while they're watching television. You might even be d ...more
Any time a feature is introduced in an MTG set and not replicated in subsequent sets, balancing issues are surely forthcoming. You wind up with one set that can do things the others can't, forcing players to counter that set with other cards from it, and generally limiting the ...more
Identify the proper time to throw a knee kick. If you are grappling with an opponent, look for an opening where you can knee-kick him in the ribs or side of the thigh. If an opponent is trying to tackle you around the waist or take you down by grabbing your legs, introduce his ...more
Battle Temperantia is this episode of the Xbox 360 game Bayonetta. In Chapter 7 - The Cardinal Virtue of Temperance, prepare for a fight. This chapter consists of a boss fight. You'll start on a platform. Temperantia will punch the platform with his fists and they will stick i ...more
Battle in verses 1-12, killing Fairness and Angels, in the Xbox 360 game Bayonetta. In Chapter 3 - Burning Ground, you have to make sure you know what you're doing. In verse 4, the creature is called Fairness. A soon as it appears it will shoot a fireball at you, be sure to do ...more
There's a lot of fighting to endure in the Xbox 360 game Bayonetta. In Chapter 1 - The Angel's Metropolis, it's your first real battle. Central Station Platform - Go to the far side of the platform and go through the security gates. The door on the far side of this hall is loc ...more
In Boca Al Lupo: The end is almost here. This is the last mission you will need to complete. Talk to Mario and he'll send you on your final mission, to assassinate Rodrigo Boriga in the Vatican in Rome. The mission is more linear than any other you've done up to this point, an ...more
Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use y ...more
Synopsis: Tell one guy that a girl that one of the other guys knows just had some sketchy demonic encounter/satanic experience at some Wicca gathering she went to last night while she was trying to get answers from the past. Then say she’s incredibly creeped out right now and ...more
Kick Ass Review Part 3: Conclusions [Spoiler Alert! Plot points are discussed from the movie and comic in this section!] Big Daddy as a selectable character presents problems for the story in the game. In the movie and in the comic, Bid Daddy dies. As a playable character th ...more
Minecraft just wouldn't be the same without all of those pesky monsters trying to break into your house and jump on you until you die. But that gets tiring after awhile, and sometimes you just want a safe place to go where you don't have to worry about being eaten, shot, or bl ...more
In the last article, we left off with the Tor network and its hidden services. As I mentioned, Tor is not the only option in the game, and I want to offer a general introduction to I2P. For a web browsing proxy and hidden services host, Tor gets the job done well. But if you ...more
What is Google Dorking? Well, simply put, "Google Dorking" is just an efficient way to utilise keywords in order to perform very specific searches on a given subject. In this case, one would look for websites/servers that are vulnerable to attacks or are configured improperly ...more
When it comes to social engineering, Null Byte is here to show you how it's done. Social engineering is the key fundamental to unlocking tons of possibilities and opportunities in your everyday life. So, what is social engineering? Social engineering can be called many things. ...more
Cross-Site Request Forgery (CSRF, pronounce "sea-surf") is a common web exploit. However, for unknown reasons it's not used very often. It plays on a given website's trust in a web browser by executing another website's form action, for example, sending money to another person ...more
Video games were blamed in the death of Chris Staniforth last May, but now things have gotten worse as video games take the blame for a more recent tragedy... Ten days ago, a man who'd lost his mind committed an atrocity, perpetrating more evil in one day than most can even f ...more
World of Warcraft has been on top of the world for seven years. No other MMO has come close to challenging its dominance of the genre, and it has generated billions of dollars for Blizzard. They have spent a lot of money adding more and more content, to the extent where the fu ...more
Tera Online is a beautiful Korean MMO with real time combat. The game is coming to the states towards the end of the year. Unlike other MMOs were combat is target specific (lock on target) and dependant on skill timers and macros, Tera Online focuses on fast area of effect act ...more
Fads, Fiascoes and Good Stuff in FrontierVille This Week The second in a series of weekly columns. Fads first It’s still St. Patrick’s Day in FrontierVille, but it looks as though its days are numbered. I give it 'til the end of the month. Trees are in full summer leaf and ...more
Posted with permission via HereComeTheYanks.com Have you recovered from that heart attack inducing, hell of a game?? I am still riding high and, as such, may ramble a bit on here. But stay with me...I'm a die-hard fan!! What else do you expect?? Another goal taken away?! Real ...more
Chi gyo ichi nyo is a familiar expression in the dojo. The word chi means knowledge. Gyo means doing, or action. Ichi nyo means inseparable. Action and knowledge are one! Acting without adequate knowledge or understanding is a constant source of frustration and problems. In ou ...more
A November release week in May It used to be that games marked to be blockbusters (expected to sell more than a million in their first month) would always be released during the holiday September to December season. November was always the month companies chose to release the ...more
We've talked about the deep web before, but we never really covered the details of what's out there. It occurred to me that a nice list of resources would be very helpful to all of you anons out there. Think of this like a helpful brochure to the hidden web. However, I should ...more
This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing p ...more
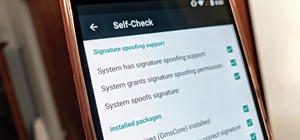
There are so many hackers around these days, and they are becoming very smart. So smart that they have successfully taken down many government websites. The most recent attack was on the Department of Justice (DOJ). To read about the history of these hackers, check out Wikiped ...more
Bluffing is one of the key components of poker. You may have a horrible hand, but if you can play it cool and raise the bet, you might just be able to convince your opponents otherwise and induce a few folds. But if you can't handle a little subterfuge, then you shouldn't be p ...more
Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called ...more
Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Sometimes it's easy to get overwhelmed with the sheer scale or complexity of a build or group project on your favorite server. Too much stress from any creative endeavour can lead t ...more
SSL stands for Secure Socket Layer. It's an encryption standard used on most sites' login pages to avoid their users' passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an "https" connection. So, w ...more
Is game play king? Or was it that graphics is king? or maybe the story? Arghhh... well, regardless from which school of thought you come from, Tera online has bet most of their chips on game play. Tera's game play separates this game from the rest. The ability to deal damage ...more
Real-time strategy (RTS) was the most popular genre in PC games at one time. It put Blizzard on the map—one of the biggest game developers in the world. And it buried the once venerable turn-based strategy genre, the only survivor being the Civilization series. But like hair m ...more
Scott Pilgrim vs The World: The Video Game was released on Tuesday August 10th for the PS3 (Download only, $9.99). It will be released for the Xbox 360 on August 25th for 800 imaginary points. We spent a few hours yesterday on co-op and single player and here are our initial i ...more
What's your training about? Would any of it matter if your life depended upon it? If not, what is your training providing you with? These are fundamental questions and your answers to them will determine how you train. Above all, your answers will reflect or require a particu ...more
How do we really come to the decisions that we make? Is it just flip a coin and hope for the best or is there some underlying procedure that we go through, consciously or unconsciously, that guides our course of action? Gary Klein is the author of "Sources of Power: Real Life ...more
Posted with permission via HereComeTheYanks.com Ok, so my prediction of a 3-1 USA victory didn't come true. But I can honestly say that I am extremely happy with a 1-1 draw!! There were times where we looked shaky (first 15 minutes). But there were also times when we were tak ...more
Update: New Trailer (7/9/10) In July of 2008, Fawaz Al-Matrouk, director of "To Rest In Peace", brought me on to shoot his USC graduate thesis film. Two years, 3 cameras, and over 15,000 miles later, the film is in its last week of post, having completed our final color correc ...more
In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the ...more
Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server! Several new block types were introduced to Minecraft when 1.2 was released, expanding the potential for builders throughout the world. Actually, so many new ...more
If you've been reading, watching or listening to the news, you sure know about the Trayvon Martin case. If you visit this site often, you may also have noticed that I've not put up any news on this case. I have my reasons. And this post will describe why. Before continuing, I ...more
Introduction The 3 major anonymity networks on the Internet are Tor/Onionland, I2P and Freenet. If you feel confused on which one is the "best" one to use the answer is simple. Use all three! Each anonymity network is designed for a different specific purpose. One network al ...more
If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC a ...more