Normally, you'd have to jailbreak your iPad or iPhone to play any games that aren't available in the iOS App Store, like the now-extinct Flappy Bird game. But this isn't the case if you want to play some of your favorite old school Nintendo classics. There's a web app called ...more
Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat. Most Linux distributions are highly c ...more
Your IP (Internet Protocol) address is your unique ID on the internet. It's synonymous with your home address. Anyone in the world can contact your computer through its IP address, and send a retrieve information with it. I'm sure at one time or another you've heard that hack ...more
Leaving your wireless router at its default settings is a bad idea. The sad thing is, most people still do it. Once they've penetrated your network, hackers will change your router settings so they'll have an easy way back in. This allows them to change your network into a she ...more
Welcome back, my rookie hackers! As most of you know, Mr. Robot is probably the best hacker TV show ever! This is a great show about a cyber security engineer who is being enticed to hack the very corporation he's being paid to protect. This show is so good, I began a series ...more
Jailbreaking gives iPhone users almost unfettered access to their devices, offering a slew of customizations, new features, and improved apps that you just can't get elsewise. Unfortunately, Apple has clamped down hard on the latest iterations of iOS, making jailbreaking extre ...more
For new Android users, rooting an Android phone can often be an intimidating process, especially since there are so many different ways to gain root access, depending on your model and firmware version. I've previously covered a way of doing it for the AT&T version of the Sam ...more
Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photogr ...more
If hearing the names of classic PC games like Commander Keen, Fallout, Master of Orion, and Wolfenstein 3D send you into a fit of nostalgia, then DosBox Turbo is the perfect app for your Android device. DosBox Turbo is a highly optimized and feature-enhanced Android port of D ...more
One of the most annoying things about the PlayStation 3 is its lack of backward compatibility on some models. There are several hacks out there to do this, but most of them involve extra hardware, like the Cobra-USB Dongle, or downgrading, which can cause all sorts of problems ...more
No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly! I hope you had a good Christmas and happy new year! Update1: Added the section "weaponizing your Android" where I talk about apps and fundamental Kali ...more
Yes, there is a way to play old Game Boy Advance games on your new Nintendo DSi. You just have to download the GBA DSi Emulator. Yes, it is possible to play GameBoy Advance game backups (aka GBA ROMs) on your DSi. You have to use a special DSi flash card adapter though, for Mi ...more
Much like the Pen Window feature in Air Command, Multi Window is extremely useful in its functionality, but bogged down by serious restrictions. While you can open and use two apps at the same time, you're limited to only a handful of apps that can utilize the feature, leaving ...more
Performance boosters generally get a bad rap, but that doesn't mean they should all be dismissed—particularly when they're as well thought out as the latest work from developer Danijel Markov. After recognizing a few inefficiencies in the way Android handles memory management ...more
As pentesters and hackers, we're going to be working with text frequently — wordlists, configuration files, etc. A lot of this we'll be doing on our machine, where we have access to whatever editor we prefer. The rest of it will be on remote machines, where the tools for editi ...more
The Samsung Galaxy Tab 2 (7.0) 4G LTE on Verizon has only been released for a couple months now with good reviews. It comes with dual cameras, memory expansion, and very quick 4G LTE speeds, without needing a contract. While most users are satisfied with the tablet as is, ther ...more
One of the best features on the new Moto X is Touchless Control, which lets you verbally ask the device questions or perform tasks without ever touching or turning on the display, a feature that would do quite nicely on the Nexus 7, if it could handle it. Video: . Touchless Co ...more
Archiving and compression is a great way to store and prepare files for sending. You can reduce the size of a file, turn a group of files into a single file, and even encrypt and password the contents! Just take a look at this image to see how much it compressed a 28GB text fi ...more
If I were a math major, I'd probably be rolling in dough somewhere in Silicon Valley right now, but since multiplying numbers and figuring out tangents gives me panic attacks, I went the English route... pays much better. Still, I never would have graduated if I didn't pass a ...more
While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the i ...more
With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use ...more
Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutoria ...more
Now that we've got all of our software installed, we're going to proceed with the next step in our HoloLens Dev 101 series—starting a fresh project and building it into a Holographic application. Then we will output the application to the HoloLens Emulator so we can see it in ...more
Nintendo may be developing cases that'll turn your iPhone into a gaming device like the Game Boy, but until something materializes there, you're stuck with cheap knockoffs on Amazon or a real Game Boy or Game Boy Color. But there's something else you can do to play eight-bit N ...more
The Nexus 6 is one of the few devices on the market that sports a 1440p "QHD" display. This means that the amount of pixels displayed is higher than almost any other smartphone, which sounds great on the surface, but is not without its drawbacks. For one, most apps and games ...more
Now that we've talked about encryption and managing your passwords, let's continue this series on getting your Mac ready for hacking by turning our attention to the terminal. The terminal is a key component of any pentester's setup. We're going to be spending a lot of time wo ...more
Rooting is usually the first thing on the to-do list whenever one of us softModders gets a new Android device. Unfortunately our efforts are sometimes hindered by certain obstacles; a common one is a locked bootloader. What Is a Bootloader? A bootloader is the lowest level s ...more
In the wake of its 20th anniversary, the folks over at Eltechs have released Original DOOM, a full shareware version of the revolutionary first-person shooter DOOM for Android, available for free on the Google Play Store. It's unmodded and unaltered from the original FPS class ...more
In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied togethe ...more
Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you. Rooting allows you to remove barriers and open Android to a level of unprecedented contro ...more
The Pixel and Pixel XL both use AMOLED screens, which are noted for their deeper blacks and sharper contrast ratios when compared to traditional LCD panels. However, AMOLED displays still have one fairly major downside, and that's the fact that they're vulnerable to screen bur ...more
If smartphone video games have a weakness, it's probably their inability to emulate the riveting and immersive experience that consoles offer. Sure, there are mobile gaming products out there like the PlayStation Portable (PSP), but when we're constantly lugging around tablet ...more
Welcome to part three in a series about steganography, the art of hiding things in plain sight. We are practicing steganography because it can be a useful skill if you don't have access to encryption software, or need a quick solution to make sure the sender and recipient are ...more
Want to play Gameboy, Gameboy Color, and Gameboy Advance games on your PSP? Here's how to install GPSP and RIN, two Gameboy emulator programs on your PSP. Please note that downloading video game ROMs is illegal.
Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly d ...more
Hey Everyone! Welcome to my post. We have seen a numerous GUI Tool in kali linux. Armitage, wireshark, Burpsuite etc,. Lets see an another GUI tool. GHOST PHISHER: Open terminal and type ghost-phisher and you will see various tabs ghost phisher has cool features : 1.HTTP S ...more
In this first part of my series on getting started with Windows Holographic, we are going to cover everything you need to get set up for developing HoloLens apps. There are many pieces coming together to make one single application, but once you get used to them all, you won't ...more
What if the code you are trying to reverse engineer is obfuscated or somehow corrupted? What if no way is left? Here comes what I like to call (wrongly and ironically) the "brute force of reverse engineering". Before I even start, as always, I wanted to apologize for any uncl ...more
Hello fellow Null-Byters today I will be showing you how to change from the simple but powerful BASH system to a more powerful and faster Z - Shell system. This change can be permanent if you want but doesn't have to be, and it is an extremely simple one to perform. Reasons t ...more
Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all fo ...more
Video games are one of the few items that have successfully advanced and adapted over decades, while still holding its "old school" value. So, while I eagerly await the release of Grand Theft Auto 5, I still get amped to play classic Nintendo games like Double Dragon. Luckily ...more
Encryped traffic and tunneling is a must when away from home to keep you and your information safe. SSH tunnels can be slow, and are heavily encrypted. VPNs are an all port solution, and proxies are just not what we need in most cases. Then, there is Tor. Tor runs your traffi ...more
One of the only downsides to the Pixel XL is that Google's flagship phone does not have stereo speakers. But if Android's awesome development community has taught us anything over the years, it's that limitations like these can be bypassed with some creative software tinkering ...more
How play Playstation (PSone) games on your PSP by installing custom fireware and an emulator. Play PSX games on your PSP - Part 1 of 2. Click through to watch this video on youtube.com Play PSX games on your PSP - Part 2 of 2. Click through to watch this video on youtube.com
When Google announced that it would begin supporting Android apps on its own Chrome OS, it was great news for all the folks with Chromebooks. But, as that operating system only makes up about 0.2% of the PC and laptop market share, most of us were out of luck. But that exclus ...more
It took a few months, but several major phones are finally receiving updates to Android Oreo. At this point, we've spent significant time talking about Oreo on the Galaxy S8, Galaxy Note 8, and Essential Phone. While an update to the latest OS is always great, there is one big ...more
Have a load of games you want to play, but don't want to be seen in public playing on your old school Nintendo DS system? Play them on your Samsung Galaxy Note 2! Now, I've already covered how to play N64, GBA, and SNES games on your Galaxy Note 2, so it only makes sense to c ...more
Whether it's the new iPad Killer or not, one thing's for sure—the Motorola XOOM is hackable. Just hours after its release last week, Verizon's new Android-based tablet (running Honeycomb) was rooted by hacker Koushik Dutta, which seems easy enough. "Since it’s another Google ...more
Many new developers are diving right into the Microsoft HoloLens, but augmented and mixed reality are fairly big subjects in terms of learning. There's a lot to cover and, unfortunately, very few places for someone brand new to Windows Holographic to begin lessons. Daily—and ...more
Every Apple computer running Mac OS X comes with a handy application called Terminal… MacBooks, MacBook Pros, Mac Pros, iMacs, etc. They all have Apple Terminal, and it can be found in your Utilities folder in Applications. Which means you can use it. Terminal is an emulator ...more
Recently, a user on Reddit complained that their Snapchat account had been temporarily banned because Snapchat noticed the user's account was going through a third-party service. In reality, the account in question was running on a jailbroken iPhone, and it was far from the fi ...more
File Transfer Protocol, or FTP, is a network protocol made for transferring files in a client and host fashion over a Transmission Control Protocol (TCP) network, such as the internet. FTP is integrated into most browsers, and you have probably used it before. It is a common w ...more
Creating any object you want is as simple as point and click if you have a 3D printer at home. If you don't have one handy, there are a few companies that offer printing services online. But to help services realize your design in extruded plastic, you have to make a 3D comput ...more
The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users. Even after the initial re ...more
In Linux, all password hashes are normally stored using the MD5 hashing algorithm in the /etc/shadow file, but MD5 is algorithmically weak due to collision vulnerabilities. The new recommended standard are the higher level SHA-2 hashing algorithms, SHA256 or SHA512. As a frien ...more
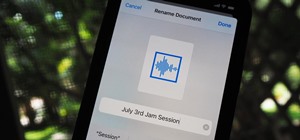
Music streaming services like Apple Music, Spotify, and YouTube Music make it easy to find and play your favorite artists and albums on your iPhone — but they cost upward of $14.99 per month. If you're more into listening to downloaded music, a shortcut can help you find free ...more
If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module. This tool is useful if you're managing a large num ...more
Thanks to Project-Infrared, there's now a pretty straightforward way to add motion tracking to the HoloLens: Connect it to a Kinect. Wavelength LLC's created a way to get the Microsoft Kinect working as a motion-tracking input device for HoloLens, which my colleague Adam Dach ...more
OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time- ...more
There is a near-infinite amount of ways a computer can be broken into. But that does not mean that there isn't a reason to secure our computers as best as we possibly can. It's like the principles of a secure house. Which are the most secure houses? The ones with locks and adv ...more