Check out this video tutorial on how to hack into WEP encrypted wireless networks. The aim of this video is to show people how easy it is to crack a wireless network with WEP encryption. Seriously, if you know how to do it, even a little kid could if you showed them how. Now t ...more
Welcome back, my neophyte hackers! Several of you have written me asking how to crack passwords. The answer, in part, depends upon whether you have physical access to the computer, what operating system you are running, and how strong the passwords are. In this first install ...more
Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, a ...more
Telegram routinely boasts about its secure messaging for truly private conversations between two parties. However, default cloud chats in Telegram are only encrypted between client and server, not client and client, which means you have to be a little proactive in making sure ...more
Hello, fellow grey hat hackers and aspiring coders. I'm back again with another python tutorial. Just that this one is gonna be a lot cooler ;-). We gonna make an encryption program, that well you know encrypts all the files on your pendrive or hdd or whatever you want....Also ...more
You may have asked yourself, "How do hackers take my password, if the website owner can't?" The answer is simple. When a website stores your login password for the site, it is run through a cryptographic hash function before it enters the database (if the website isn't Sony). ...more
In the digital age, maintaining your privacy is a never-ending battle. All sorts of companies and agencies have access to your data, and quite a few can eavesdrop on almost every method of modern communication. In an effort to push back, Open Whisper Systems has been at the f ...more
Today, we are going to combine what we learned from the Introduction to Cryptography article with our Java programming skills. If you are new to Java, check out Matthew's Learn Java: Part One for a quick beginner's lesson, or check out some of the Java tutorials directly on Or ...more
If you have some photos, videos, and documents that you want to keep completely hidden and encrypted on your Android device, Andrognito is the app you need. We showcased this app in the past, but since then, CODEX has rebuilt it from the ground up with new and improved feature ...more
This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but ...more
Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker. FileVault, created by Apple in 2003, is a hard ...more
Let's be honest for a second; we all have sensitive material on our phones that we wouldn't want anyone else to ever see. Maybe it's to protect ourselves or someone else, or maybe it's none of your business why I don't want you to see pictures of my bachelor party. Regardless, ...more
In this article, I'll show you how to create a simplistic AES python based text encryptor. You'll need python 2.7 and PyCrypto (found here). The code is fairly simple, a user enters an encryption key (which basically tells the program how to scramble the text, using an algorit ...more
As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt ...more
This is the second episode of Full Disclosure by InfinityExists.com. This episode includes how to crack WEP encryption, and why it can be cracked so easily.
Traditionally, if you were looking for end-to-end encrypted messaging, you'd stick with something like iMessage, WhatsApp, or Signal. However, if you already use Facebook Messenger, you have all you need for truly private chats with its built-in E2E encryption. It's available ...more
Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. Whi ...more
Encryped traffic and tunneling is a must when away from home to keep you and your information safe. SSH tunnels can be slow, and are heavily encrypted. VPNs are an all port solution, and proxies are just not what we need in most cases. Then, there is Tor. Tor runs your traffi ...more
Before we dive any further into getting your Mac ready for hacking, I wanted to continue on with the concept of encryption. In the last part, we talked about full disk encryption on your Mac, but now I want to quickly cover the encryption of disk images before we dive into man ...more
Null Byte is looking for moderators. More threats to computers exist every day. Not only do we have computer viruses and malware, but we have rootkits and other nasty pieces of code that can log your keyboard strokes or even add your computer to a botnet to attack other websi ...more
One of the more talked-about features of Google's new flagship device is the fact that all of the data on the Nexus 6 is encrypted by default. At face value, this certainly seems like an added bonus for the 6-inch phablet, especially in this day and age with growing security c ...more
I love cryptography. It is like a great gigantic puzzle for me to solve. However, it is more important than that. It is also how we keep secrets safe. Not just sorta safe either, but really safe. Until recently, if you wanted to use strong encryption you had to either learn d ...more
Skype is a great service. It allows a free solution for VoIP to VoIP calls, and cheap VoIP to landline calling. However, a very disturbing, little known fact that might push you away from Skype does exist. If you closely read the terms of service agreement, it clearly says tha ...more
In this how to video, you will learn how to crack a WPA encrypted wireless network. To do this, you will need the Air Crack package for Linux. First, disable the wireless adapter and enable monitor mode. Next, identify the channel in the wireless network and Mac address. Once ...more
Greetings my fellow hackers, In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up f ...more
Welcome to Part 3 in my series on protecting your computer from prying eyes (Part 1, Part 2). In today's segment, we will be going over drive encryption using the TrueCrypt program on Windows OS. Drive encryption is a technique that masks your data with a cryptographic functio ...more
A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangib ...more
As we all know, security is a big thing here in Null Byte. We've talked quite a bit about ways to encrypt traffic and become anonymous on the internet, some of which entail using proxies, VPNs, and SSH tunnels. We've also talked about preference using SSL pages in practice for ...more
For this particular example, I will be working on Wndows (sorry X users). I might write a similar guide once I am more comfortable with programming in Linux. What You Will Need Visual C# 2010 Express (Get it here) Pirate Metal Source Code (For when you are done with the guid ...more
It can be hard to get all of your friends, family, coworkers, and acquaintances to jump on board with the more-secure email system ProtonMail, but that doesn't mean you can't still send them encrypted emails. Best of all, they won't even have to install any other apps or exten ...more
Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices. ...more
When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we'r ...more
As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures. The subject of cryp ...more
Prior to this year's WWDC, there were lots of rumors that Apple might finally be making a version of iMessage for Android. While that never came to fruition, a few big updates to a very useful app have now ensured that we can seamlessly send and receive Android texts in Apple ...more
Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed ove ...more
Archive files are great for portability and saving space, but a lot of people don't know they can also be encrypted. There are a lot of archiver programs out there, but most of them can open a file that's been encrypted using other software, as long as you're using a recent ve ...more
In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on. While the NSA's incredibly sophisticated surveilla ...more
Xeni visits the offices of the Electronic Frontier Foundation and speaks with Jake Appelbaum and Bill Paul, two of the authors of a security research paper that shows how your computer's memory can be tricked into revealing data you thought was safely encrypted, and out of the ...more
This is Null Byte's fourth part in a series about fully securing our computers (Part 1, Part 2, Part 3). In our last Null Byte, we went over how to encrypt an entire operating system to protect our data, however, this doesn't fully protect us. In the case of legal extortion, t ...more
Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of ...more
For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application tha ...more
Gmail uses TLS, or Transport Layer Security, by default for all email communications, so all of your emails will use the standard encryption as long as the recipients also support TLS. But there's a way to add even more security to your Gmail emails, and you can use your iPhon ...more
Do you need to email your wife your Social Security number? Send confidential business plans to your partner in Thailand? Send your hacker buddies the recovered hashes from last night's breach? Try using GPG, a valuable and easy to use open-source encryption program. In my fi ...more
In order to increase the security and harden the integrity of an email account and its content, you'll want to use PGP on your Windows, macOS, or Linux computer. This is usually the first thing security analysts do to protect communications with encryption, and everyone else s ...more
Have an old-school tabula recta lying around? No? Then just print out the chart below. Nothing ensures better password security than this centuries-old cipher technique. Here's how it works, via Wikipedia: "Using a tabula recta, each alphabet is shifted one letter to the left ...more
In this tutorial I will be explaining the purpose of unique encryption/decryption scripts ( I will be referring to these at "UEDS" for this tutorial). Then, I will show you how to make one. Finally I will talk about the downsides to the method I use. I will also provide links ...more
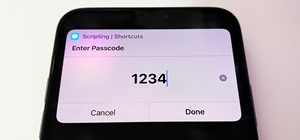
We live in a time where privacy is rare and our files can be easily accessed by just about anyone. Having your phone protected by a passcode is great, but if someone figures it out, they can easily access anything on your phone. That may not be a big problem for many of us, b ...more
For the newer generation, using a computer is now a common thing that a lot of people must know how to do. Regular things like opening programs, writing papers, and using the internet are all easy to get, but there are other things that can be a bit harder for those less exper ...more
In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent. It's been rulings like these and their call for internationally recognized rights to pr ...more
Welcome to a tutorial on XOR encryption. We'll be looking at what XOR is and how we can use it to encrypt or decrypt data. What Is XOR? XOR is a bitwise operation in which each of the bits are compared and applied with the XOR operation according to the following table: We c ...more
Some data can be very confidential. In such case you need to encrypt the data so that it does not go into the wrong hands. There are lots of encryption software available to encrypt the data. But to use them first you need to install then and this can take lot of time. You can ...more
When it comes to security, Apple is usually at the top of the pack when it comes to your personal data, minus a few embarrassing flaws here and there. However, a new iOS security concern has been discovered that protects your data less than it did before — and Apple designed i ...more
Hello and welcome to another InfoSecurity World tutorial. The intent of this article is to teach one how to encrypt sensitive files. When set up correctly with a strong password, it would be almost impossible to hack. Even the FBI have had issues decrypting this software. I'm ...more
In this clip, you'll learn how to use the VSN plug-in to encrypt email in Microsoft Outlook. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over five minutes. For more information, including detailed, step-by-step instr ...more
For years, Skype has been synonymous with video calling and messaging. However, as the industry moved toward encryption and privacy, Skype usage was discouraged by experts due to its murky encryption. To combat this, Skype has introduced true end-to-end encryption. While Skyp ...more
In this tutorial, we learn how to set and encrypt a Wi-Fi password using WPA in Netgear. First, type "www.routerlogin.net" into your internet browser. Next, a pop-up window will appear, type your user name and password into this dialog box. A new window will pop up, click on t ...more
In this Tutorial I will show you how you can use the frequency of letters to decrypt the famous Caesar cipher. I hope it is easy to understand and helpful for getting in touch with basic cryptanalysis. If you find any mistakes or have questions feel free to ask me. Finally I a ...more
Encryption is the process of converting you data in to other obscure form so that no one can read it. Encryption can also be done using batch files. Batch files are scripting programs in windows which can be used to program small automatic operations. To do this open a notepad ...more
In this clip, you'll learn how to implement simple text encryption and decryption in MS VB 6. Whether you're new to Microsoft's popular event-driven program language & IDE or a seasoned developer merely looking to improve your chops, you're sure to find benefit in this free Vi ...more
Have a super secret spy communication you'd like to send out, but don't have the funds to hire your own trusted operatives to deliver the message? Then stick to what you're used to—email it. SafeGmail is a browser extension that allows you to send encrypted emails right throug ...more