If you lose your AirPods, AirPods Pro, or AirPods Max, you can turn to Find My to locate them. But sometimes, things don't go according to plan, and many things can go wrong. For example: Nothing happens whenever you try to play a sound through your AirPods. Their location wo ...more
Aside from being able to change the wallpaper and add shortcuts, the Galaxy S4's lock screen doesn't offer much in the department of personalization. The lock screen is efficient and practical, but it's also a little bland. To add some functionality and visual effects to the ...more
Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and sh ...more
Hello there, 'Flashers'! Welcome to my 8th Post. This tutorial will explain how to flash Kali NetHunter on OnePlus (Tested) and Nexus Devices (Not Tested-Should work) as a secondary ROM, so that none of your personnel data/ROM gets affected. NetHunter? Refer to Ciuffy's Pos ...more
If you've seen our guide on the 18 coolest features in iOS 7, you know that there's a lot to like about Apple's new mobile OS, but there's also a laundry list of grievances to go with it. One that bugs me is the lack of Home screen customization, something that has always driv ...more
Hackers often find fascinating files in the most ordinary of places, one of those being FTP servers. Sometimes, luck will prevail, and anonymous logins will be enabled, meaning anyone can just log in. But more often than not, a valid username and password will be required. But ...more
Apple's latest big software update includes an entirely new Apple app, a controversial change in the TV app, better Siri control, an improved Shortcuts app, interesting Safari upgrades, Apple Music Sing, and more. Keep reading to see what iOS 16.2 has to offer your iPhone. Th ...more
Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is go ...more
Due to its constant delays and lack of public invites, the OnePlus One is the equivalent of a unicorn in the Android community. I was lucky enough to win an invite in the OnePlus Storm of Invites promotion and have loved every minute with my new Nexus Killer since receiving it ...more
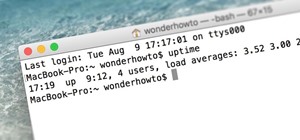
All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system. As I have mentioned nu ...more
Get the inside scoop on Wizard101 hacks, cheats, tricks, tips, and walkthroughs! Watch this video tutorial to learn how to hack Wizard101 with Cheat Engine (09/25/09). Description of the game from Wizard101: Wizard101 is an online, multiplayer, Wizard school adventure game w ...more
While there are many customization options available for the Samsung Galaxy Note 2, they aren't always easy. The large selection of custom ROMs and difficulty implementing certain hacks and mods can be a nightmare for anyone not well versed in all things Android. But the good ...more
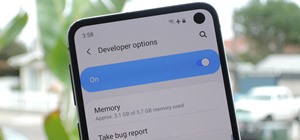
If you ever want to go beyond the basics on your Android phone, unlocking the hidden "Developer options" menu is the first thing you should try out. With it unlocked, you can change the way parts of stock Android looks, enable ADB connectivity with your computer, add visual re ...more
By now, a mobile phone that isn't "smart" is about as hard to come by as a TV that isn't high definition. As a result, members of older generations who were previously reluctant to purchase a newfangled smartphone have no other choice but to cave into the more recent trends wh ...more
Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester. On the other hand, there are many here who come to Nu ...more
With its growing popularity, it's clear that the Chromecast isn't going away anytime soon, with options for casting games, cloud files, music, and much more. But not all content providers are in a hurry to add support for the device, and SoundCloud is one of them. While My Clo ...more
Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hacke ...more
Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a mal ...more
There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer. It's puzzling to imagine about 100,000 .onion websites in existence. Readers who ...more
On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated ...more
In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hea ...more
With the holidays over, a lot of people with shiny new Google Homes are getting their first chance to explore the new Google Assistant. Before the Google Home's release, the Assistant was only available for the Google Pixel and Pixel XL, or in a text-based form with Google All ...more
In a previous softModder guide, we converted our HTC One smartphone into a legitimate Google Play Edition HTC One, but that conversion cause our bootloader to be locked once again. So, if we ever want to convert it back to a regular Sense-style HTC One, we'll need to unlock th ...more
One of the most promising avenues of attack in a web application is the file upload. With results ranging from XSS to full-blown code execution, file uploads are an attractive target for hackers. There are usually restrictions in place that can make it challenging to execute a ...more
After a few unforeseen delays, the Android Lollipop update is finally here for Google Play Edition HTC Ones. This means that if you have an official GPE M7 or M8, or if you have simply converted your HTC One from a carrier-specific, Sense-based model to a Google Play Edition, ...more
Over the years, we've seen security breach after security breach, as well as high-profile data scandals where collected personal information was misused by companies. Apple makes customer privacy a priority, so there have been few issues to worry about when it comes to its ser ...more
Grilled cheese is one of my favorite foods, ever. However, there are times in my life when I haven't had access to a full kitchen, and it's pretty hard to make a good grilled cheese sandwich without one. Don't Miss: Make Amazing Grilled Cheese Sandwiches Every Time Thankfull ...more
SAS: Zombie Assault 2 is flash game from Ninja Kiwi. Learn how to hack Zombie Assault 2 with tricks and cheats. Watch this video tutorial to learn how to hack Zombie Assault 2 with Cheat Engine (09/13/09). -Health Hack -Ammo Hack -Infinite Grenade Hack Description of the app ...more
Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a techni ...more
Welcome back, my tenderfoot hackers! Well, the first season of Mr. Robot just ended and Elliot and fsociety successfully took down Evil Corp! They have effectively destroyed over 70% of the world's consumer and student debt! Free at last! Free at last! Of course, global finan ...more
Personally, my favorite new feature in iOS 7 is the Control Center. With it, you can very quickly and efficiently access popular and much used settings, such as Wi-Fi, Bluetooth, brightness and more—all with one simple swipe. While I love the Control Center, it may not be eve ...more
Last post, the Sonobe unit was introduced as a way to use multiple copies of a simply folded piece of paper to make geometric objects. In this post, we are going to explore that concept further by making two more geometric models. The first is the truncated icosahedron, which ...more
Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, a ...more
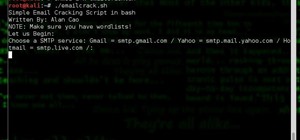
Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to ...more
When it comes to pronunciation, Siri absolutely butchers my last name. Instead of pronouncing Aguilar as ah-gew-lar, my own "intelligent" personal assistant pronounces it incorrectly as ah-gui-ler. Thankfully, Apple has added a new secret feature that allows you to teach Siri ...more
One of the most exciting features in iOS 11 was the fully revamped Control Center, which improved the overall interface visually, made it one page only, and finally made it possible to customize what controls actually appear within it. Customizable controls was previously only ...more
There are plenty of ways to customize your stock HTC One (or any Android device), from playing retro games to adding rotating live wallpapers. But to get the most out of your device, you need root access. After rooting, the floodgates open and you have free reign over the dev ...more
With the camera usually being pretty simply in the past iOS versions, iOS 7 has seen a few major changes—built-in filters, Instagram-ready square photographs, zoom-in during video recording, and more. One less obvious feature that the new iOS has is the ability to activate bu ...more
Apple just released its biggest update to iOS 17 yet, and there are 60 exciting new changes for your iPhone. With iOS 17.2, you get a brand new app, more Apple Music enhancements, upgrades in Messages, and a new security feature that was announced last year, as well as changes ...more
Make Slime! This one is easy. Just mix equal parts of glue and water and then add an equal part of liquid starch. Just like that you have gooey slime. The more you play with it the more fun it becomes. This acclivity causes the polymer chains in the glue to cross link with che ...more
Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get ...more
During today's press event at the company's headquarters in Cupertino, California, Apple announced that iOS 7 will come bundled with several new ringtones—something that has stayed relatively static the past few years. I've download the GM version of iOS 7, which is the last ...more
Back in iOS 6, deleting individual text messages in a conversation was just a matter of tapping the edit button on the right-hand corner of the thread, selecting which texts to delete, and then pressing delete. Easy enough, right? So, it comes as no surprise that people are ...more
Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeO ...more
Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons. Most hacker tools are developed in Linux (well over 90 percent). Linux offers us greater granulari ...more
So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit mak ...more
The status bar is where we get all of the important need-to-know information for our phones. At a quick glance, you can see what time it is on your Samsung Galaxy S3, how much battery power you have remaining, your current signal strength, and more. But after a while, things c ...more
In the pursuit of large displays with thinner bezels, Samsung has sacrificed some components. While the loss of the headphone jack gets all the attention, there are other victims — namely, the notification LED. Once a staple on all Android phones, this small light would blink ...more
It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you. Today, we'll make a Wi-Fi probe logger with Probemon.py to track nearby devices ...more
Minecraft was first released just a few years ago, but when a paradigm-shifting piece of media comes along the rest of the world is quick to take inspiration from it. The absolutely terrible XBLA knock-off FortressCraft was the first, and last month a much more interesting gam ...more
If you're part of the Windows 10 Insider Program, build 15048 launched this morning, and included a nice big unannounced surprise. You can now launch the Mixed Reality Portal and enable the simulation to try out mixed reality right from your PC, even if you don't have one of t ...more
Whether you're riding the subway on your way home from work, or stuck in the backseat of the car on a long road trip, there are times when you need to entertain yourself without a mobile data connection. A good mobile game would pass the time perfectly, but not every game work ...more
Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero- ...more
Rather than reaching for aspirin the next time a headache strikes, try grabbing a drink of lemonade instead. Not only can it help ease your head pain, but it can also help relieve stress, anxiety, and depression. But not just any old lemonade will do the trick—reach for the la ...more
Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker. Every once in while, though, ...more
Update (Fall 2020): Samsung's version of Android 11 is already in its testing phases! One UI 3.0 is expected to hit recent flagship Galaxy devices towards the end of this year, so check out the new list of features: New Version: All the New Features & Changes in Samsung's One ...more
You're working on your iPhone or playing an awesome game when you receive a notification. You take too long to look up from your activity, so before you get a chance to see what's up, the notification is gone. Persistent notifications won't disappear on you like the default di ...more
When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. Th ...more
Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be a ...more
Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all o ...more