In a previous tutorial, we were able to measure horizontal surfaces such as the ground, tables, etc., all using ARKit. With ARKit 1.5, we're now able to measure vertical surfaces like walls! In this tutorial, you'll learn how to make your augmented reality app for iPads and i ...more
With the reveal of Magic Leap's developer documentation last week, many questions have been answered—and several new ones have been raised as well. But since the Magic Leap One (ML1) isn't simply called the "Leap One," these are questions that the company probably has no inter ...more
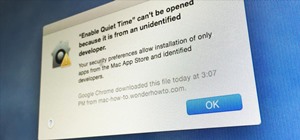
Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it i ...more
While the world is only recently becoming aware of its existence, augmented reality has been around in some form or another since the '90s. In the last decade, with the advancement and miniaturization of computer technology — specifically smartphones and tablets — AR has becom ...more
Reddit user Mr. Squishy recreated the entire Game Boy Pokémon Red Version game in Vanilla Minecraft, i.e., a Minecraft server without gameplay modifications. Instead of using mods, he used 357,000 commands blocks—blocks that execute commands in the popular sandbox game. How lo ...more
Why can't I see who is stalking my Facebook profile? There are other social networks that do let you see who's viewed your profile, mainly LinkedIn and its "Who's Viewed Your Profile" feature. Regular users can see a recent list of who has been spying on you, along with some ...more
In the recent hit movie Furious 7, the storyline revolves around the acquisition of a hacking system known as "God's Eye" that is capable of finding and tracking anyone in real time. Both the U.S. spy agencies and an adversarial spy agency (it's not clear who the adversary is, ...more
We've already shown you how to dunk a regular-sized Oreo cookie while keeping your fingers pristine, how to upgrade Oreos into different desserts, and even make them into lazy ice cream sandwiches. Now we're going to introduce you to a few other essential Oreo hacks that will ...more
The most genius summertime snack hack that we've come across recently is, without a doubt, the campfire cone. Astounding in its simplicity and ease of preparation, yet brilliant in its execution, the campfire cone has something for everyone: parents and children, expert and no ...more
When building anything of a social nature, be it a local roller derby or softball team, a club dance night for chiptune, or building new technology markets, the community around those ideas are an important factor in helping these things not only come into existence but to gro ...more
Anyone who knows me well is aware that I am a cyberpunk junkie. The conflict between lowlifes, corporations, and the government, flavored with dystopian future, high technology, transhumanism, artificial intelligence, and noir storytelling, just does something for me. Since I ...more
Hash browns are a breakfast staple and for good reason: they're simple, salty, and crispy, and so delicious that you can easily down several servings of them in one sitting. Basically, they're the French fries of breakfast. Despite their simplicity, hash browns can be difficu ...more
Facebook just keeps coming up with more and more diversions to help you ignore your responsibilities. At least this diversion is a little more intellectual than most of the other things that can easily distract you on Facebook. Facebook Messenger has a secret chess game, and ...more
So, Nintendo's never really been good at the whole online thing. Most of the time, we forgive them, because they are masters at creating games meant for solo play or local multiplayer. Sometimes, though, that doesn't fly. Take a game like Splatoon, for instance. Although it re ...more
Maybe you've had a long day... or maybe you just want to treat yo' self. So you head to your local watering hole for some tasty, tasty liquor. Your current fave on the cocktail list is a drink of something strong with bitters; you don't know what bitters are, but damn if that ...more
Often, the most frustrating part of crafting the perfect dinner is feeling like you have to clean every single pot and pan in your kitchen after cooking just one meal. With so many components, it can feel like each step of a single dish requires its very own pot. Yet there ar ...more
It only takes a minute for something well intentioned to turn into something sinister. Facebook created 'memorial pages' as way for friends and family to share their thoughts and feelings for those that are no longer with us. As written in a company blog post, "We created the ...more
What does mainstream augmented reality look like? I'm not talking about the stuff you see in concept videos and science fiction films. No. What does it really look like? If you ask anyone working within the AR space today, the future of AR is wherever the immediately realizab ...more
If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for ...more
Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for expl ...more
T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the ...more
Throughout this NR50 series, we have talked about the incredible growth the augmented and mixed reality space has seen in the last year. More devices, software, developers, and use-cases seem to arrive daily. For this growth to have occurred, it took the work of many people, f ...more
Bitmoji has experienced explosive success this year thanks to Snapchat. The app allows users to create their own personal emoji and send responses to other friends, and even though it's only two and a half years old, this customizable emoji app is growing at an impressive pace ...more
Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers w ...more
Move over, Hype Williams, it looks like Snapchat is about to take some of your music video-making business, and pop rock group Maroon 5 is the proof. On Wednesday, the group released a music video for its latest single, "Wait," and it's shot entirely in Snapchat. (Travis Schn ...more
I spent just about my entire weekend trying to break the 800, 900, and 1,000 levels of Instagram — because it's a game, y'all — by playing around with my follower count. I shamelessly manipulated my IG account in such a way that was extremely time consuming and left many of my ...more
While most of Hollywood and its celebrity class are enthralled by virtual reality, a new augmented reality experience featuring some of the music and film world's top talent is preparing for virtual liftoff. Masters of the Sun is a graphic novel that was released this summer ...more
As a hacker or an aspiring one, You need to be careful and anonymous if your doing anything illegal. But you slipped up. Now someone is tracking you! Well luckily you read this post ahead of time and have a backup plan! The first step in remaining safe is to remain anonymous. ...more
As with any new releases, full updates that completely revamp the look and feel of your iPhone's operating system will have teething problems that eventually get ironed out with incremental updates. iOS 11, with its issue of not being able to connect to the App Store on some i ...more
Leave it to some lazy college kids to attempt to figure out a way to brew a pot of coffee without leaving the couch. Actually, this project wasn't lazy at all—quite the opposite, in fact. Created by Ohio State University students Carter Hurd and David Frank during HackOHI/O 2 ...more
When it comes to a perfect summertime dessert, lemon meringue pie is the ideal contender with its rich lemon filling and light-as-air meringue topping. In my humble opinion, the meringue is the true star of the dessert, instantly elevating what is simply a lemon pie to somethi ...more
Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history. Using a type of malware dubbed “KeyRaider,” hackers hav ...more
God, chili is amazing this time of year. It's hearty, filling, freaking easy to make, and it warms you from the inside out. My favorite part about chili is how none of its ingredients are set in stone. For example, maybe you don't have the Worcestershire sauce you usually dou ...more
Imagine you have mastered the perfect cherry pie for your annual work picnic but, upon taking it out of its airtight pie carrier, your heart sinks as you realize the crust has turned to mush thanks to the moisture from the filling. Sound familiar? Well, I have news for you: i ...more
As a child, you probably spent some time trailing an adult at the grocery store. You lovingly eyed the aisle with brightly colored fruit snacks, reaching for the tempting boxes, placing them discreetly in the cart only to be told, "No! That's JUNK FOOD. You can't have it." Do ...more
Making pizza at home is fun and easy—until you get your creation into the oven. Then all of a sudden, your crust gets soggy and your toppings ooze off into one big mess. A home oven just can't cook a pizza the same way as a professional one built specifically for pizzas. But ...more
Zenge came to my attention as a free game on the Google Play store — it will remain free until midnight, so anyone catching this review on the 25th, download it ASAP — but I imagine it would be worth the typical $0.99. While it can be mentally-frustrating to purchase a game — ...more
The bacteria Klebsiella pneumoniae is a bad actor known for being antibiotic-resistant and causing a variety of serious infections in hospitals, including pneumonia, surgical site wounds, and meningitis. K. pneumoniae is something you do not want to encounter if you have a com ...more
What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl. A user with the handle @blanket found out the hard way that Twitter's security is atrocious when his a ...more
Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listenin ...more
A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials. ...more
Ah, butter—the (literally) heart-stopping star of the dairy world. Everything tastes better with it, from pie crusts and cookies to veggies and steaks. Hell, you can even fry things in butter if you want the best-tasting fried foods of your (short) life. Don't Miss: Compound ...more
BlinkFeed completely changed the way I access new updates from Facebook and Twitter, but when I switched to the Google Play Edition of the HTC One, I lost access to the launcher. BlinkFeed is available in the Google Play Store, but HTC has not opened it up yet for all devices ...more
As a company, Facebook is not shy about talking up its AR smartglasses plans. The latest missive comes from two executives in charge of developing AR software and hardware. As far as we know, Amazon doesn't have plans to make AR smartglasses yet (and audio-only smartglasses d ...more
The development of virtual reality at Facebook has been evolving lightspeed in the last few years. But while a relatively small group of VR enthusiasts and gamers are enjoying the social media giant's dedication to immersive headsets, it is the augmented reality space and its ...more
While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups a ...more
The words of three of tech's most important executives in the last 48 hours are providing some valuable insight into the near term future of augmented reality and the cloud infrastructures that support it. Apple CEO Tim Cook, Google CEO Sundar Pichai, and Snap CEO Evan Spiege ...more
Over the past year, Magic Leap has teased its cross-platform vision of the AR cloud, which it dubs the Magicverse. While the company shared a timeline for its debut next year, it also served up new developer tools for the present. Facebook is also looking to the future of aug ...more
An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manuf ...more
Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for ...more
Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password ...more
Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access ...more
If you salivate at the idea of waking up to the Jarvis-powered smart window from the opening minutes of Marvel's Iron Man, then connected home appliance maker CareOS is here to make your playboy billionaire philanthropist dreams come true. At CES 2019, the company unveiled th ...more
When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. Th ...more
Users are often the weakest link when probing for vulnerabilities, and it's no surprise they can be easily fooled. One way to do this is called clickjacking. This type of attack tricks the victim into clicking something they didn't mean to click, something under the attacker's ...more
To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purch ...more
Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks. The goal of this project was to locate a known and easily detectable macOS payload, then ...more
People say that money makes the world go 'round. And it's no different in the world of augmented reality. If there are any doubts about the future of the AR industry, it doesn't seem like many venture capitalists or corporate investors share those doubts. According to Digi-Ca ...more
Facebook is preparing to make augmented reality experiences for brands more visible in its mobile app with Tuesday's introduction of augmented reality ads in its News Feed. News Feed AR ads will enable advertisers to insert AR camera effects, from virtual product try-ons to p ...more
With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer. In my last series, we used a Post-it note to trick a neighbor into visiting a website that we cont ...more