In this how to video, you will learn how to speed up your Azureus Vuze program. First, open up Azureus Vuze. Next, go to advanced, option, and click preferences. Select preferences and change the port to a number between 49152 to 65535. Once it is changed, go to transfer and m ...more
Here the New Boston shows you some tips about using the Spry Validation Text Field. To begin you will go to the Spry Validation Text Field, on Dreamweaver CS4. Looking at the bottom of the page notice the various options that are available for Properties. You find drop-down bo ...more
This video demonstrates how to setup a printer on a Macbook Pro.Open the document you wish to open. Go the File menu on the top bar menu and select Print. On the Print dialogue box, you will notice that no printer is selected. Click on the drop down menu to select Add A Printe ...more
This video presents how to connect to your iPod Touch or iPhone using SSH (Secure Shell) without using Wi-Fi connection. 1 Step. Presuming you have Internet connection in your iPhone, click Cydia. Wait for it to load. Type "OpenSSH" without quotes into the search engine. When ...more
If you don't have a Wi-Fi network, you can still easily SSH into your iPhone. Just follow the steps outlined in this video tutorial. First, you will need a Mac or iPhone along with Fuju. Just download the program. Once you have all of this, click on the Wi-Fi bar and click on ...more
Before you get started exploring a big new city or even just getting reacquainted with the one you live in now, make sure you aren’t putting yourself in any unnecessary danger. Memorize good traveler habits that will keep thieves and scam artist off your back. Don’t let your ...more
So you want to party with celebrities. Whatever you do, don’t cry. You won’t just look silly—you’ll look unstable. Follow these steps to get you one step closer to hanging with the stars. You Will Need: • Self-restraint • Composure • Discriminating taste Step 1: Be cool B ...more
TCP/IP Client / Server Application Hello! Today's blog post will be about coding a very rudimentary Client and Server application duo, which will communicate by using TCP Sockets. It is, as illustrated, in principle, just two cans and a string that ties them together. The se ...more
There are a lot of things on your computer that can reveal information about you when you are surfing the Internet. If you are like me, then you will do anything to maintain your privacy and prevent those little leaks of information from happening. Here's a list of a few of th ...more
As someone who’s entering a time of life that involves weddings, reunions, and generally running into people I haven’t seen in awhile, I find myself being shocked by how much people have changed over the years. A lot of times, people will have dropped a bunch of weight, or hav ...more
The Fake Adult Website Prank is an incredible trick if you happen to have the necessary access and work in the internet industry. Luckily, I had both. The objective of this prank is to fool your boss or co-workers into thinking you've accidentally sold out the site to a adult ...more
Learn how to use more English phrasal verbs with this instructional English language lesson. get...over with To do or finish an unpleasant but necessary piece of work or duty so that you do not have to worry about it in the future. I'll be glad to get these exams over with. ...more
Grab your thinking caps and get your hack on. Null Byte is officially seeking contributors on a weekly basis who are willing to take the time to educate the Null Byte community on anything, from hardware hacks to life hacks. Contributors that write tutorials will be featured o ...more
Only so much data can be passed through the network and to your computer's networking interfaces. This is limited by the amount of bandwidth you have. The more bandwidth you have, the faster your network connections will be. Not only this, but your transfers will be more paral ...more
Big name individual hackers and hacker groups everywhere in the news are getting caught and thrown in jail. Everytime I see something like this happen, I won't lie, I get a little sad. Then I wonder, how are these guys getting caught? If a group like LulzSec, with all the fame ...more
XSS stands for cross-site scripting, which is a form of web-based exploitation that uses client-side vulnerabilities in a web page to execute malicious JavaScript codes. JavaScript is referred to as "cross-site" because it usually involves an external website containing the ma ...more
We're ending the week with a lot of big announcements and updates. To date, Google+ has updated its name policy, but is still forbidding pseudonyms. Blocking people on Google+ became even easier, and yesterday, games on Google+ launched. Google+ Name Policy Changes Google+ h ...more
Yesterday, Electronic Arts had a nice sale on Steam for 40-60 percent off some of their Sims titles, which included The Sims 3 (along with its DLCs) and SimCity 4. I've never been a big Sims fan, especially with the slew of virtual people games in the last decade, so I didn't ...more
You've probably seen those deep-web images floating around on the Internet. Usually, it goes something like this: There is a towering iceberg and the deeper the underwater portion extends, the more “hidden” and “exotic” the content is described to be. Sometimes these images ar ...more
This Null Byte is the first part in a mini-series on the art of Social Engineering. I will be teaching you how to effectively defend yourself against it. What is Social Engineering? Social Engineering is the art of hacking humans. It's when a person is manipulated into doing ...more
In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack. Before we start hacking, let's familiarize ours ...more
You walk over to your laptop, wiggle your mouse to wake up the screen, then fire up your browser to come visit Null Byte. Catching the article about Anonymous and how they presumably will not take down the Internet, you find yourself wondering... how would someone take down th ...more
If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! mo ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. This week has been an exciting one. The com ...more
INTRODUCTION In this world of Internet era, almost everyone wants to create theirs own web presence by either hosting their own blog, articles, photos, videos, reviews, etc etc . But some people choose their own way and decide to have something bigger! What is it? Its a websi ...more
If one of your is really messy then you can try this prank on them. It actually happened with me and believe me it works!! If the person concerned just doesn’t clean up his or her mess and from table or bed and you really find it irritating since that is the situation with mos ...more
How to track an email address. Useful if you meet someone who says they are from somewhere e.g. LA as given in the video and you don't believe them. Go to the Rate a Bull site type in their email address and then hit return or 'find them'. The site will give you options to see ...more
Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks. The goal of this project was to locate a known and easily detectable macOS payload, then ...more
Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning ...more
While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are al ...more
Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target. Thanks to a pair of recon tools coded in Python, it takes just seconds to research how a website or server might be vulnerable. No matter what platform ...more
A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, m ...more
Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself ...more
Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And ...more
Though you can use the Social Engineering Toolkit to clone websites, this way is much more customisable. For example, you could send the credentials your victim enters to a script that mails you notifying you of new data someone's just entered, or automatically store them in ...more
Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the ...more
Welcome back, my budding hackers! One of the keys to being successful as a hacker, pentester, or cyber warrior is the ability to find vulnerabilities or flaws in the target system, which are what we exploit when we hack. We have looked at several ways to do that including var ...more
Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks. Sparta, authored ...more
Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands. RapidScan does an excellent job of automating the deployment of vulnerabili ...more
Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know. Possibly the most popular and well-known reconnaissance tool currently ava ...more
Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life. Imagine arriving home one night after work and there's a Post-it note on your apartment door with the website "your-name- ...more
Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see wh ...more
Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language ...more
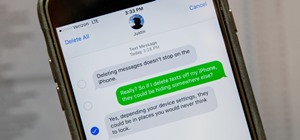
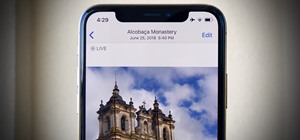
Clumsiness is the great equalizer when it comes to smartphones — it makes no distinction between the most expensive flagship handset and cheaper mid-range models. A hard drop onto pavement will usually result in a shattered screen, regardless of how pricey your device is. And ...more
Aircraft equipped with ADS-B are constantly shouting their location into the radio void, along with other useful unauthenticated and unencrypted data. In this guide, we will make an ADS-B receiver using a Raspberry Pi with a software-defined radio (SDR) dongle, which we can us ...more
The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centere ...more
NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of ...more
If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well. Please d ...more
It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploi ...more
UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - at my blog, here - https://techkerne ...more
Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes ...more
When attending networking events, a LinkedIn exchange is a common occurrence. Equally common is the awkward fumbling dance with how to add each other. Fortunately, we have the solution: the ultimate way to add LinkedIn contacts. You no longer need to spell names with non-typi ...more
So, at first, I miss everyone :( and i missed playing minecraft a bit... sooo i found inspiration and i went on for the search for a server as amazing as wonderhowto... OFCOURSE i did not found one wich was better, or wich could even get close to what he had... But i found one ...more
Welcome back, my budding hackers! Recently, I showed you how you could exploit the widely disseminated OpenSSL vulnerability that has to become known as "Heartbleed". Although the world has known about this vulnerability for over a month now, it will likely take many more mon ...more
Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from ...more
Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what appli ...more
Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone ...more
If you're using or need to use Zoom, the popular video teleconferencing service, you've almost certainly heard about "Zoombombing" by now. While Zoom has been adding security measures to address the problem, there are other things you can do to prevent or stop Zoombombers in t ...more
You get a snap from a friend, per usual, but what's this? The lens they're using is actually really cool. Of course, you want to try it out for yourself, but don't bother searching Snapchat's enormous library of lenses to find the AR effect. Instead, there's a simple way to in ...more
Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machi ...more