A long time ago, we recommended the Hover Zoom extension for Chrome as an easy way to blow up small image thumbnails without actually have to "click" on the images themselves. Over the past year, there have been reports that Hover Zoom now collects and sells your browsing data ...more
When you can't reach your iPhone or don't have it on you, how do you get help from emergency services? Unless you have one of those life-alert mobile triggers, someone nearby, or some amazing telepathy skills, hope might be the only answer — unless you wear an Apple Watch, tha ...more
We're glued to the news now more than ever, but our "free press" isn't necessarily free of charge. Cable news outlets like CNN and MSNBC are locked behind expensive cable TV packages and cord-cutting streaming subscriptions such as Sling TV and Hulu + Live TV. Luckily, there a ...more
To say that I am disappointed with the new Maps application in iOS 6 is an understatement. And it seems like the rest of the world is with me, so I needed to find a solution—and quick. Installing the Google Maps web application is a nice quick-fix, but those looking for a beef ...more
A Jedi does not seek adventure or excitement, but Star Wars fans can seek Jedi with the Find the Force augmented reality scavenger hunt promoting the launch of merchandise for Star Wars: The Last Jedi. Between Sept. 1 and 3, participants are tasked with finding Find the Force ...more
The moment arrives when you finally pop a shell on the web server you've been working on, only you find yourself in a strange environment with limited functionality. Restricted shells are often used as an additional line of defense and can be frustrating for an attacker to stu ...more
The North remembers...that smartglasses are the future! Game of Thrones jokes aside, the smartglasses startup opened its doors, and we visited its Brooklyn store to get our hands the consumer-focused Focals smartglasses. While North is just getting off the ground, Microsoft a ...more
What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may. Pre-requisite information: For those ...more
If you're having a "Netflix and chill" night, the last thing you want to worry about is finding something to watch—after all, you have better things planned for the night. With so much streaming content now available for cord cutters, settling on just one title to watch can b ...more
Apple released the second Release Candidate for iPhone on Friday, May 21. The new update, build number 18F72, comes four days after the company seeded the first 14.6 RC to developers and public testers, and two days after the first beta for iOS 14.7. Apple released this updat ...more
Apple pushed out the Release Candidate for iOS 14.6 on Monday, May 17. The 18F71 build includes new features and bug fixes, including an option to unlock your iPhone with Voice Control. It comes just hours after Apple announced Spacial Audio and Lossless Audio playback for App ...more
Kali Linux is known as being the de facto penetration-testing Linux distribution but can be a pain to use as an everyday OS — even more of a pain if that means carrying around a second laptop or the constant frustration of using the finicky Wi-Fi on virtual machines. But there ...more
Hello there! This will probably be the final tutorial on functions where we will be looking over a method called pass by reference. This technique allows us to modify large amounts of data without the overhead and return multiple values. Let's go! Passing by Value Until now, ...more
I obviously do a lot of Steampunk projects, but there are a ton of things out there that I haven't tried yet. So, in an effort to broaden my horizons, I recently taught myself how to use Arduinos, which I plan to incorporate into some of my future Steampunk builds. Since ther ...more
NFC, or near-field communications, is a hardware feature that has been built into most Android phones for the last four years. It's essentially a low-power data connection that can be used to initiate a quick command by bringing your device within range of a compatible receive ...more
Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetch ...more
Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. On ...more
Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions. Second i want to say sorry for the series i left in stand by m ...more
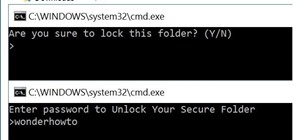
As a hacker or an aspiring one, You need to be careful and anonymous if your doing anything illegal. But you slipped up. Now someone is tracking you! Well luckily you read this post ahead of time and have a backup plan! The first step in remaining safe is to remain anonymous. ...more
It's always a pain to make sure you have enough storage on your smartphone. Pictures and videos occupy a lot of space, so your music library has to take a back seat—otherwise, you might see that pesky "Storage Full" notification at any time. If you have a large music library, ...more
Dirty, malformed, and outright mischievous text strings have long been the enemy of interactive website developers. Strings contain any combination of letters, numbers, spaces, and punctuation, and are entered into text boxes on websites by users. These strings in particular c ...more
Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in ...more
You'd be hard-pressed to find a working Super Nintendo in someone's house nowadays, but back in my adolescence it was gaming heaven. But now there's no reason to have an SNES console at home, because there are so many ways to play those retro games without one. All it takes is ...more
Chrome, Firefox, and Safari all provide built-in features that allow you to save your username and password for your favorite sites, making the process for entering your credentials a breeze when you revisit them. While this automation does make your life a little easier, it ...more
Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to se ...more
While browsing the web on a computer, most of us are familiar with using Ctrl + F (or Command + F) to search for a specific word on a page — but what if you want to do that on mobile? If you're using Google Chrome, there's a simple way to search for specific words on iPhone or ...more
Step 1: First in first, you have to install a Chrome browser, and download Ballloon from official site You can also download it at Chrome Web Store Step 2: Authorise your cloud storage after Ballloon is installed. Step 3: You will find the hover icons on each clip of Vimeo ...more
There are so many things in place that make browsing the internet difficult. From geographical walls to malicious software and spying — there's a lot to consider any time you do the most basic of functions online. VPN.asia: 10-Year Subscription is a VPN that can streamline you ...more
URL tracking codes: you'll see them on almost every link you copy online to share with friends and followers. It could be tens or hundreds of extra characters appended to the end of a URL, which websites and marketers use to tell how you got to the link in the first place. The ...more
If you don't have any home Wi-Fi, like to watch videos on public transportation, or just always find yourself streaming Netflix when there are no hotspots available, your cellular data is probably gobbled up fairly fast. For limited data plans, watching the next episode of you ...more
Fullscreen isn't always fullscreen, especially on your smartphone. As screens get taller and bezels get slimmer, more phones end up with an aspect ratio that doesn't match most YouTube videos. Luckily the video-sharing app has a nifty workaround to fill your screen. First, op ...more
I can't tell you how many times I've force-closed or restarted Chrome due to it freezing or loading pages incorrectly. And don't even get me started on that obnoxious "Aw, Snap!" error. I guess you could say I have a love-hate relationship with my most used browser. But, it t ...more
It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement. Whether you are a journalist, a protestor, or a hi ...more
I read a ton of articles online and I am always looking for a way to make the experience a little better. Reading long articles can be tiresome, and if an article has multiple pages, I will most likely skip it. With the ability to endlessly scroll, no site should have multiple ...more
On-screen navigation buttons offer many distinct advantages over physical buttons—they can change orientation along with your device, they're capable of visually morphing to indicate secondary functionality, and the user experience is more consistent when buttons and app eleme ...more
When you're a writer with work published across various online platforms, building a portfolio of your work can be pretty time-consuming. That's where Authory comes in. A writer's portfolio is extremely valuable when you're applying for a new position as a staff writer or try ...more
Web applications are ubiquitous in the modern online world, and knowing how to attack them is an increasingly valuable skill. But the key to a successful attack is good recon since it's easier to be focused and efficient with the more information you have. There are many finge ...more
Twitter can be a wonderful place for people to express their emotions and chat with each other in brief. However, it can also be a breeding ground for hateful comments, foul language, and a whole lot of political talk. If you're tired of seeing certain content on Twitter, you ...more
Having your home and work addresses set in Apple Maps makes them incredibly easy to navigate to no matter where you're located. If you move to a new house, stay in a hotel or resort while vacationing, report to a different office, or have multiple job sites to visit regularly, ...more
What do Leo Tolstoy (writer), Beethoven (composer), Paul Gaugin (artist), and Adolf Hitler (politician) have in common? They are all considered to have suffered from the sexually transmitted disease syphilis. With the incidence of sexually transmitted infections (STIs) and se ...more
Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or se ...more
Everything you post on social media lives there forever — even if you delete it. Just ask anyone that's ever posted something stupid. Instagram does not provide built-in tools to save or download images and videos from other users, but there are workarounds. Third-party tools ...more
Pot, weed, bud, herb – whatever you want to call it, the green earthy treat makes everything way more fun. Now that marijuana is legal to some extent in more than half of all US states, we thought it was high time to showcase some apps that enhance your experience with the con ...more
If you like to listen to popular songs from huge musicians and hard-to-find music from obscure indie artists, SoundCloud is for you — and you don't have to pay a dime. When you find a song you really love and want to play it back even when you're not connected to the internet, ...more
With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skille ...more
Since getting our hands on the Magic Leap One last week, we've been methodically delving into each feature and reporting our findings step-by-step. Earlier this week, we took a look at the Screens app (a video viewer) and the Helio app (an AR web browser). This time around, we ...more
If you're looking for an alternative iOS keyboard for your iPhone, look no further than Gboard. The Google-made keyboard is bursting with features like web search, Google Maps, GIFs, and more. Now, Gboard is adding a new feature that'll make it easier to find the perfect emoji ...more
Security researcher Ravi Borgaonkar from Berlin has discovered that hackers can hide an 11-digit code in a webpage that can wipe out all of the information on your smartphone—contacts, photographs, music, applications, and anything else of importance. The attack takes no more ...more
The Google Chrome browser does mostly everything well and integrates nicely with other Google services, but it's not exactly renowned for speed. With a rooted device and the aid of an app called Kernel Adiutor, however, you can make Chrome as nimble as some of the fastest brow ...more
Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long ...more
For anyone who uses computers regularly, the screen can become cluttered with different windows, tabs, and applications in no time. One solution to that mess is dual monitors, which allow users to be more organized and divide their work into two halves. The problem is that not ...more
If you have a Barnes & Noble Nook, you may be surprised to find that your eReader can do a lot more than just display ebooks, which makes it a great alternative to those more expensive all-in-one tablets that do everything (seriously, everything). If you want to get more bang ...more
The 2020 iPhone SE had been through the rumor mill for a long time, but Apple finally unveiled the second-generation iPhone SE on Wednesday, April 15. While it doesn't sport the 4-inch design of the original SE, it combines a small form-factor with modern specs. The big questi ...more
Tired of playing old-school Game Boy Advance, Game Boy Color, Nintendo, and Nintendo DS games on your iPhone? We've got another retro video game system for you to add to your arsenal of emulators—Super Nintendo. Yep, that's right. Thanks to Lucas Menge, you can now play Super ...more
On your iPhone, your phone number and Apple ID email address are the default ways in which somebody can contact you on FaceTime. While you can't remove your phone number as an option, you can withdraw your Apple ID email account. More importantly, you can add any other email a ...more
Android's copy/paste menu and text selection options have traditionally been downright terrible, but things are starting to get better with some recent improvements made in Marshmallow. That being said, there's still a lot left to be desired, and there's always plenty of room ...more
Apple released iOS 13.5 for iPhone on Wednesday, May 20. The update came just two days after the company seeded beta testers iOS 13.5's GM (golden master), the build everyone would get if all went well. While only available to beta testers, the GM is the same software as iOS 1 ...more
The Master System, more popularly referred to as the Sega Master System, or SMS for short, is a video game console that was released in the mid-1980's as a direct competitor to the original Nintendo (NES). While it was given credit for playing a role in the development of its ...more
In these times of social distancing, video calling is becoming the technological substitute for face-to-face connections. For those who carry an iPhone, the art of video calling defaults to FaceTime, the native app on iOS that is exclusive to Apple devices. But what do you do ...more
Apple's iCloud is a fantastic way to ensure that all of your photos, messages, notes, and other important data are backed up and appear on all of your connected devices. However, you may have information like reminders attached to accounts other than iCloud, which won't appear ...more