Hackers often find fascinating files in the most ordinary of places, one of those being FTP servers. Sometimes, luck will prevail, and anonymous logins will be enabled, meaning anyone can just log in. But more often than not, a valid username and password will be required. But ...more
While the Reminders app has been largely ignored by Apple for years, iOS 13 finally makes it a force to be reckoned with. The app has been completely redesigned with easier navigation and more useful features that can compete with other task managers. After giving the new Remi ...more
Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP wit ...more
Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed ove ...more
By now, you've probably already installed 10.10 Yosemite, the newest version of Mac OS X, on your computer. While you most certainly noticed the visual changes, you might have missed some of the really cool additions. We've spent the last few days getting to know it, and let ...more
Apple includes a lot of helpful features for iCloud email addresses, but one of its best-kept secrets will give you total control over organizing your inbox like a pro. So, what's the big secret? Subaddressing, also known as plus addressing, tagged addressing, email address ...more
A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us ...more
So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone i ...more
Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file. The vulnerability was discovered by Filippo Cav ...more
Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detec ...more
If you use the Google Assistant on your Android device, you can easily send a text message to any one of your contacts. But even though that same Assistant is powering the Google Home, you can't use the smart speaker to accomplish the same task — at least, not without some tin ...more
Malevolent hackers can divert your incoming calls and texts to any number they want, and they don't need to be a criminal mastermind to do it. Even friends and family members can reroute your incoming calls and messages so that they know exactly who's trying to reach you, and ...more
There are many things Apple doesn't tell you about its products, and that's definitely the case when it comes to its Messages app. Hidden features lurk in your SMS and iMessage conversations just waiting to be found, and we've unearthed some of the most secret ones. Instead o ...more
Update (Fall 2020): Samsung's version of Android 11 is already in its testing phases! One UI 3.0 is expected to hit recent flagship Galaxy devices towards the end of this year, so check out the new list of features: New Version: All the New Features & Changes in Samsung's One ...more
Data can be injected into images quickly without the use of metadata tools. Attackers may use this knowledge to exfiltrate sensitive information from a MacBook by sending the pictures to ordinary file-sharing websites. Continuing on the topics of DPI evasion, payload obfuscat ...more
OpenBSD implements security in its development in a way that no other operating system on the planet does. Learning to use the Unix-like operating system can help a hacker understand secure development, create better servers, and improve their understanding of the BSD operatin ...more
Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily act ...more
The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in r ...more
During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform O ...more
Some websites require you to perform a verification task so they know you're human and not a bot. It helps websites curb spam, abuse, unauthorized access, and cyberattacks but also adds an obstacle for anyone trying to visit their content. If you find it more of a nuisance tha ...more
With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassin ...more
If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a ...more
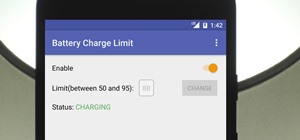
A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data. The ...more
In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM ...more
Apple released the second beta for iOS 15 on Thursday, June 24. The update includes FaceTime's "SharePlay" feature for the first time, a new Maps icon, updates to Focus mode, in addition to many other changes and bug fixes. SharePlay, one of iOS 15's most ambitious new featur ...more
Apple just released its iOS 16.6 update for iPhone on July 24. When you install the new software, it may look like there's not much to it since Apple doesn't include any features in the release notes beyond "important bug fixes and security updates," but a few new features are ...more
As we've seen with other tools and utilities, administrators typically use certain things to do their job more efficiently, and those things are often abused by attackers for exploitation. After all, hacking is just the process of getting a computer to do things in unexpected ...more
The latest software update for iPhone has a few new features you should know about, including an enhanced security feature to protect your Apple ID account from phishing and other attacks. Keep reading to see everything new that's included with iOS 16.3 for iPhone. The iOS 16 ...more
A man-in-the-middle attack, or MitM attack, is when a hacker gets on a network and forces all nearby devices to connect to their machine directly. This lets them spy on traffic and even modify certain things. Bettercap is one tool that can be used for these types of MitM attac ...more
Welcome to the first annual Next Reality 30, our list of people who've made the biggest impact on the augmented reality space in the last 12 months — and what a 12-month roller-coaster ride it's been. Apple introduced ARKit-powered apps last fall, Google launched ARCore for An ...more
Unlike the realm of virtual reality, augmented reality is less about losing yourself in some fantasy environment, and more about getting things done in the real world. So while we've seen some great games that capture the imagination on devices like the Magic Leap One and the ...more
Flight disruptions can cost billions of dollars, but most modern commercial flights rely on air traffic control systems that harbor serious vulnerabilities. The Federal Aviation Administration uses an infrastructure called NextGen, which relies on Automatic Dependent Surveilla ...more
Seventeen years ago, Apple released iPhone, the first mainstream consumer phone with a touchscreen as its main typing input method. Apple has been perfecting its onscreen keyboard for almost two decades, and it's built with some fantastic features that make typing faster and e ...more
While the iPhone came before the first Android smartphone, every new iOS version seems to include a wealth of features already existing on Android, and iOS 17 is no exception. Apple's currently beta testing iOS 17 with developers, with a public beta coming in July and a stabl ...more
Network enumeration is one of the essential phases of an attack, but it can take a lot of time and effort depending on the size. We've all been spoiled by Nmap and similar tools, and while there is a learning curve involved, they are extremely useful. But there's also GoScan, ...more
In a recent arbitrage tip, we showed you the secret to making money fast by buying and selling the same thing over and over again on eBay. But there's one thing you need to know about the buying part—get the lowest price possible! This article aims to show you some of the best ...more
There's a whole lot of brouhaha going on right now about the hidden plug-ins being installed unknowingly in the Mozilla Firefox web browser, with companies like Apple, Microsoft and even Google being named top offenders. Mozilla's own Asa Dotzler (pictured right) is fed up wi ...more
Ever since high school, I've been preparing my own taxes. Each year it gets more and more complicated, which results in me filing later and later, avoiding it until I have the time or just can't wait any longer. I even resorted to using TurboTax online to help do some of the g ...more
It's been done for ages, but for most of us, "regift" entered our vocabulary after the 98th episode of Seinfeld—"The Label Maker." In this episode, Elaine calls Dr. Whatley (played by Bryan Cranston) a "regifter" after he gives Jerry a label maker—the same label maker that Ela ...more
It seems like nowadays, whenever Facebook rolls out a new feature, it's immediately controversial. Social Ads put your name and face in the spotlight, Instant Personalization shared your information with partner sites, third-party apps were allowed to access your home address ...more
Handy technique for search & rescue, learn how to tie a hasty webbing harness with this knot tying animation. This animated knot tying tutorial is the best you'll find. With this knot tying how to, you can tie the Hasty Webbing Harness Knot fast or slow, or pause it at every s ...more
Facebook is at it again. First they invaded your privacy with Instant Personalization, now they plan to take it a step further with their controversial plans to share users' home addresses and mobile phone numbers with third-party developers and websites. Due to user feedback ...more
Make this Valentine's Day one to remember! Well... because you forgot. But don't worry, you can still make that heart pitter-patter for your love by saving face and getting some last minute Valentine gift ideas on the cheap. There's no reason to shop at Hallmark or buy expens ...more
Outside the realm of politics, where opposing sides are quite passionate and quite disagreeable, there are few areas in our society quite as divisive as Twitter. People who like Twitter love Twitter and are relentless in trying to co-opt the people they know into joining (this ...more
Thanks to online music services like eMusic and iTunes, compact discs are becoming a far distant memory, turning local music shops around the country into desolate wastelands. The once mighty movie rental store Blockbuster is now bankrupt because of online streaming services l ...more
It's that time of year again when pizza boxes line the room and buffalo wings stain the couch. When cases of beer sit in the cooler and the big screen TVs are fired up and properly calibrated. When two of the best football teams vie for the championship title and the Vince Lom ...more
This coming Friday, November 11th, 2011 is Veterans Day and everybody's celebrating! But only veterans and active military personnel can get the great deals being offered at restaurants and retail outlets across the country. If you need help locating some of those deals, below ...more
For me, the idea of a smartphone with internet access was overkill for a cell phone. Wasn't that what my computer was for? Do I really need immediate access to the web? Must I update my Facebook every hour, from the palm of my hand? Do I need turn-by-turn directions from Googl ...more
We all want a faster, more efficient web browsing experience. Some immediately flocked to Google Chrome as soon as it was released, because of its super fast speeds. Others restrained themselves and continued to wait for Microsoft and Mozilla to play catchup. And the time is a ...more
Super Mario Brothers! No, wait... Super Meat Boy! Yep, that's right. Meat. As in "cube" steak. As in a square piece of beef with eyes and a shitty grin, who just happens to be in love with a band-aid. I have no idea why. And no matter how shocked you are to see your dinner on ...more
Since its launch in 2001, Wikipedia has become the number one reference site on the web, used by anyone and everyone, written by anyone and everyone. With over 18 million collaboratively written articles, there's backgrounds and descriptions on practically everything—if it exi ...more
My girlfriend was going away for a few weeks, but where she was going, there was no easily accessible Internet. She works mostly on the web, so it was imperative that she have a decent Internet connection during her travels. So, tethering her phone was the only real possibilit ...more
Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episod ...more
This is a great solution if you need to get something off your computer, but you are not home. Want access to your files stored at home? How about hosting a home web server? Static IPs are expensive, if you can even get one. We set up Dynamic DNS instead! 'Back in the day' i ...more
While Google Maps is useful for finding addresses and calculating directions, it's not, strictly speaking, very fun. Unless, of course, you know how to hack it. This hacker's how-to from Tekzilla will show you how to access a number of Easter eggs and hidden features like a ge ...more
If there are words that you use often but Swype doesn't know them yet, you can easily add them to the database of your texting program. In this clip, learn all about adding uncommon or unique words to your Skype dictionary so that you can text even faster. You can even add web ...more
Replay AV is the newest software to come out for downloading steaming audio from the web. Replay AV allows you to download audio from different sources all over the web. You can even record radio broadcasts and set your account to record the station. This video will show you h ...more
It's Christmastime, so what better of a game to play than the winterized Icy Tower? And what better game to hack with Cheat Engine? This wintery video tutorial teaches you how to hack Icy Tower with Cheat Engine (06/12/09). This is really about hacking the floors on Icy Tower ...more
If you loved The Da Vinci Code by Dan Brown, then listen up— there's been a new discovery found hidden within Leonardo da Vinci's most famous painting— the Mona Lisa. An Italian researcher named Silvano Vinceti sparked a new controversy over the world's most famous painting w ...more
First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect. I've read quite a few books and ...more