A Steampunk's Guide to Sex was the subject of a recent successful Kickstarter campaign, and I now hold the finished book in my hands. As such, I can say (mostly) unreservedly that you should buy this book. Allow me to tell you why, before I get into the nitty-gritty about the ...more
When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new ...more
A few days ago, Russian hacker Alexy Borodin found a way to get free in-app purchases on an iPhone or iPad. In-app purchases include things like items and power-ups for iOS games, as well as subscriptions and "premium" memberships for certain apps. The method is novel, not fo ...more
There are more than a few exciting new Home Screen customization options available in the iOS 18 and iPadOS 18 software updates, including some we've been waiting years for. Apple never mentioned a few of these new features and changes in the release notes, but you can see the ...more
Apple has revolutionized how we write with the introduction of its new Writing Tools, powered by Apple Intelligence. In beta on iPhone, iPad, and Mac, these tools allow you to select text and use intelligent features to summarize, proofread, or rewrite it until the tone and wo ...more
There's a powerful tool on your iPhone that can fine-tune your iOS experience based on what you're doing and when, and it's completely customizable. With it, you can control what notifications appear or are silenced, who can call you, which Home Screen pages you want to view, ...more
Emoji have taken over the world, so there's a good chance you regularly use (or overuse) emoji on your iPhone's keyboard just like everyone else. But before emoji were popular, there were emoticons, short for "emotion icons" — and iOS has a secret emoticon keyboard just waitin ...more
You see the status bar nearly everywhere on your iPhone, and it almost always looks the same. But you can use a few tricks to spice things up a bit — without jailbreaking your iPhone. The status bar's background on iOS is transparent, so you'll see different colors and gradie ...more
If you haven't been using Spotlight Search on your iPhone, we've got ten reasons for you to start. Apple's made some significant improvements to the search interface available on the Home Screen and Lock Screen, and it's more useful than ever. The new features and updates for ...more
When you open Safari for the first time after updating to iOS 15, you'll instantly notice its search bar is now at the bottom, and its Page Settings menu has moved with it. For tabs, moving between them is as easy as swiping on the Tab Bar or selecting one from the new grid vi ...more
On this platform, we talk a lot about the future of augmented reality, and we pay attention to what is being said elsewhere as well. Sometimes the future chatter is about the hardware. Even more frequently, in recent months, the discussion is about the future of the AR cloud, ...more
With fears over the COVID-19 pandemic subsiding, live concerts are returning. And Doritos wants to send music fans to a few of them via an augmented reality promotion. Dubbed "Mark Your Play," the campaign is centered on scannable posters, denoted by a Doritos chip displayed ...more
When you first open Safari after updating your iPhone to iOS 15, you might be a bit surprised by the design change. Apple attempted to make browsing the web on its smartphones more natural and cohesive, but it may leave you wondering just how to actually navigate your tabs. W ...more
Since bringing augmented reality features to Search and Maps, Google has made them arguably the most useful augmented reality products in its portfolio. On Tuesday, at Google I/O, Google unveiled some of its new AR capabilities for the pair of mobile apps. Don't Miss: Google ...more
Why are there no official Star Wars emoji in the Unicode Standard? We've got the "Vulcan Salute" from Star Trek, so where's the force choke hand gesture?! While you may never see Star Wars officially invade your emoji keyboard, there are ways to send Star Wars emoji and sticke ...more
The race for the future of AR wearables gained steam this week with several pivotal developments. First, Apple, the subject of numerous reports and rumors regarding its purported AR headset, is reportedly eyeing an in-person unveiling of the device for later this year, rather ...more
As businesses flocked to Zoom, Microsoft Teams, Google Meet, and other video conferencing platforms to bridge the gap, we wondered aloud -- why aren't more companies leaning even more heavily on augmented reality? Arvizio may have the solution to that shortcoming with an upda ...more
We all know that using a VPN not only has a ton of benefits but is essential in our digital age. But did you know that you can get access to your own industry-leading VPN for life with one one-time payment? Even better, we've found an amazing deal on one right now: for a limit ...more
Let's say that the screen on your iPhone is showing signs of discoloration, which makes the display annoying to use. You'll need a replacement display or a new iPhone as soon as possible. If you have one of the newer iPhone models, the cost to fix it might be more than your wa ...more
Since its release in 1991, Python has become one of the world's most popular general-purpose programming languages. From data mining and web programming to cybersecurity and game design, Python can be used for virtually everything online. When it comes to coding languages, Py ...more
The way you share a group of photos and videos on your iPhone is pretty simple; just select a few items, then choose a service or platform to send them through. Simplicity isn't always the best option, though, and in this case, there's a better way than letting those files sen ...more
You don't need to work in the accounting department of a Fortune 500 company to use and appreciate Microsoft Excel. Although primarily associated with a wide variety of functions pertaining to accounting and finance, Excel is actually an incredibly powerful and multifaceted pl ...more
Not all 5G is equal. Even if you dropped the cash on a true 5G phone and you see it's connected to 5G in the status bar, that doesn't mean you're surfing the web, streaming Spotify, and binging Netflix faster than your friends with LTE phones. The first thing you have to unde ...more
Even under normal circumstances, it's almost impossible to speak to a representative for a government agency or company in just one try. Many systems will put you on hold for long periods or ask to call you back when someone is available, but there are still some out there tha ...more
Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start som ...more
Dark mode is simply a way of life these days now that both Android and iOS officially support it. Most major apps now use the system-wide setting on Android and iOS, and many had their own dark themes in-app before Google and Apple got with the program. But the social media gi ...more
For the last three years, Apple has hosted its Worldwide Developers Conference at the San Jose Convention Center, but thanks to the COVID-19 pandemic, WWDC 2020 is now an online-only event. So what can you expect from the new virtual format and when and how can you watch the k ...more
When you have a personal Instagram account but also manage other profiles — like ones for work, your entrepreneurial startup, an alter ego, or your famous pet, to name just a few examples — how do you manage them all from the same device? Back in the old days, you'd have to r ...more
Sudo is a necessity on most Linux systems, most of which are probably being used as web servers. While the principle of least privilege is typically applied, sudo misconfigurations can easily lead to privilege escalation if not properly mediated. Which brings us to SUDO_KILLER ...more
UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, exa ...more
Apple's Mail app has always been a stylish yet simple way to check and send emails. Third-party apps up the ante with powerful tools and features to help keep junk and spam mail out of your eyesight. But with iOS 13, you don't need them since Apple gave the Mail app some much- ...more
Phone specs get better and better each year, and multiplayer mobile games are right there with them. Instead of playing solo, jump into some real-time gameplay with co-op and player vs. player modes, and battle friends, family, and strangers from around the world. But which mu ...more
Apple just seeded the fourth public beta for iOS 13 to software testers today, Tuesday, July 30. AppleSeed participants saw this beta one day early, alongside the release of developer beta 5. Now, developer and public testers alike are up-to-speed with the latest in iOS 13. B ...more
Beta testing for Apple's big upcoming iPhone update, iOS 13, is well underway. So far, each of the four beta versions we've seen brought new features and changes to the table, many of which were never even mentioned by Apple during WWDC in June. Now, it's time to do it all ove ...more
The updated Reminders app in iOS 13 makes productivity a little bit more seamless on the iPhone. The overhauled user interface makes it easier to find your reminders, the new Messages integration makes it simpler to remember to-dos regarding your contacts, and the new toolbar ...more
The wait wasn't so long this time. Apple released public beta 3 for iOS 13 on Thursday, July 18, just one day after the release of developer beta 4. For context, Apple took five days to seed public beta 2 after releasing dev beta 3, so it's a pleasant surprise that the latest ...more
We're pumped for iOS 13 and all of the fresh features and changes that come with it. Developer beta 3 came with new features in the double digits, including AR eye contact in FaceTime and mouse cursor size customization. Developer beta 4, released today, has a few more additio ...more
Staying alert to directions and changing the music you're listening to on your smartphone at the same time can be cumbersome, but Google Maps wants to fix that. One of the mapping service's features allows you to control music playing on Spotify, Apple Music, and Google Play M ...more
The third developer beta for iOS 13 has been out since July 3, and while devs have had fun exploring all the new features, those of us on the public beta have sat on the sidelines running the public version of dev beta 2. But we don't need to wait any longer, as Apple just rel ...more
On July 3, Apple pushed out iOS 13 developer beta 3 for iPhone, and there's a lot found hidden within. A new FaceTime setting, more Arcade details, full-page scrolling screenshots everywhere, a noise cancellation option in the Control Center, and a new markup tool — and that's ...more
Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an a ...more
UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, ...more
MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer neve ...more
SSH is one of the most common protocols in use in modern IT infrastructures, and because of this, it can be a valuable attack vector for hackers. One of the most reliable ways to gain SSH access to servers is by brute-forcing credentials. There are a few methods of performing ...more
In 2018, augmented reality went from the vague promise of interesting things in the near future to tangible developments in software and hardware, proving that immersive computing is indeed the future. Traditional mobile apps on smartphones continued to maintain user attentio ...more
Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers a ...more
With the list of available mobile apps for moviegoers constantly expanding and improving, seeing a film at your local theater has never been better. With the right apps for your iPhone or Android phone, you can research movies, find out if showings are sold out, reserve seats, ...more
Continuing our NR30 series this week, we focused on the leaders of the software development industry that make augmented reality experiences possible. In other news, two of the current leaders in making AR headsets, Microsoft and Magic Leap, are pursuing multiple verticals wit ...more
When BlackBerry first announced the KEY2 back in June, the biggest gripe we heard was about the price. It was reasonable criticism, as BlackBerry was asking a lot of its consumers at $650. Knowing this, BlackBerry went back, made some downgrades, and cut the price, creating th ...more
Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering att ...more
Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such f ...more
Yesterday, I talked about what I think is the most immediately mainstream-friendly app on the Magic Leap One is (Screens), and now we'll touch upon the runner-up: Helio. In short, Helio is how Magic Leap One users can browse the web in augmented reality, something we've seen ...more
For the second time in a row, Apple pushed out a new iOS 12 developer beta on a Monday, and for the first time this round, they've done it only one week after the last one. While the August 6 release of iOS 12 developer beta 6 doesn't contain a wealth of updates, there are sti ...more
Apple released the fifth developer beta for iOS 12 on Monday, July 30, only 13 days after the release of dev beta 4 and 12 days after public beta 3. Until this release, Apple kept a consistent two-week schedule for developer beta updates, so we were a little surprised to see t ...more
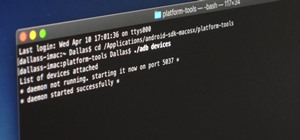
As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing ma ...more
Windows 10 and macOS have poor reputations when it comes to customer privacy and user policies. Our hacking Windows 10 and hacking macOS articles might make it seem like a reasonably secure operating system doesn't exist. But I'm here to tell you that there is a viable alterna ...more
There's a lot more to your iPhone's dialer screen than just entering phone numbers and hitting the green call button. It's not very obvious, but there are secret codes that you can enter on the dialer to find out information about your device, help troubleshoot issues, and mas ...more
According to Google at their 2018 I/O conference, Google Assistant is now available on over 500 million devices. Now that the assistant is available on iPhones as well, Google has to give iOS users a reason to switch to its assistant over the built-in Siri. Today, Google has e ...more
Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL in ...more
The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you n ...more