Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc. Any time someone's computer seems to act ...more
Razer just released their first flagship Android smartphone, appropriately named the Razer Phone. While mobile gaming fans are sure to enjoy the Razer Phone, the buttery-smooth 120 Hz display makes this an appealing option for anyone in the market for a new phone. If you've ju ...more
Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself ...more
Over the years, Kodi (formerly XBMC) has become one of the most popular media players. It provides all the essential functionality needed for any home theater setup while remaining open source and free. However, Kodi is not limited to just your living room. With the Kodi app f ...more
In Fallout: New Vegas, you will eventually end up having to check out the other factions and tribes in the game. One of them happens to be the Boomers over at Fort Nellis Air Force Base, a clan of old vault dwellers who took over the base and have been making use of their heav ...more
Sometimes the idea of cooking fish, especially for a group of guests, can be intimidating. There's the fear of the fish not cooking right, or sticking to the pan or grill. And even if you cook it right and the fish doesn't stick, you're left with the inevitable fishy-smelling ...more
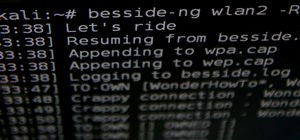
Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elli ...more
Jet engines combine oxygen from the surrounding air with on-board fuel to burn at very high temperatures and create thrust in the direction of the flame. Rockets, which we will learn about in a later post, are similar but carry oxygen internally and can therefore function in s ...more
I like to grow vegetables all year round, and I couldn't afford the big gas bulbs, or the power to run them. The big gas bulbs: can explode can burn you and your plants cost upwards of $50 a month to operate raise the temperature in your home, causing the air conditioning to ...more
What if the code you are trying to reverse engineer is obfuscated or somehow corrupted? What if no way is left? Here comes what I like to call (wrongly and ironically) the "brute force of reverse engineering". Before I even start, as always, I wanted to apologize for any uncl ...more
Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what appli ...more
How many times have you sent a message on Facebook Messenger that you immediately wanted to take back? Most email services have an unsend option, as well as Instagram Direct, and Messenger has caught on to this convenience with a take-back button for any chat you're in — even ...more
Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hid ...more
Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Real time redstone clocks are a marvel of redstone technology. Not only can they keep track of time, they are capable of powering other more complicated redstone machines. Regardles ...more
Like many smartphones nowadays, your Samsung Galaxy S4 comes bundled with a headset for you to listen to music, watch videos without disturbing others, and even make phone calls. I personally only use it for music, whether it's Play Music, Pandora, or streaming from YouTube. ...more
For years, smartphone makers have been caught up in a megapixel spec race to prove that their camera is better than the next guy's. But we've finally come to a point where even the lower-end camera phones are packing more megapixels than they need, so it's getting harder to di ...more
You probably already have a plethora of white t-shirts and plain blue jeans, and while having outfits you can lean on no matter the time of day or occasion, going with the same neutral tones and combinations gets a bit boring (not to mention visually dull) after a while. Spic ...more
If you're ever lost or hurt out in the middle of nowhere with a dead cell phone, you might be able to "flag" down help as long as you're near some railroad tracks. Some train tracks carry a small electric charge as a means of detecting other trains for signaling or for detect ...more
At last, what you all finally waited for! Hi! Fire Crackers, Welcome to my 7th post (Part-3), this tutorial will explain about some situations and how to make the Victim's Life like Hell! And fill his system with Malware. #1 Situation: After Exploiting... Go ahead and explo ...more
Welcome back, my fledgling hackers! Nearly every commercial enterprise worth hacking has an intrusion detection system (IDS). These network intrusion detection systems are designed to detect any malicious activity on the network. That means you! As the name implies, a networ ...more
The balanced and refreshing taste of a cocktail should always entice you into another sip. You'll know you're drinking something of quality when no specific ingredient, including booze, dominates its taste. A great cocktail can even mirror a great meal by exhibiting flavors li ...more
There are many great reasons to root your phone, but if you're not experienced with tools like ADB and Fastboot, it can seem like a daunting task. Fret not, because if you want to root your HTC 10, we're here to walk you through the process. Rooting is the only way to take fu ...more
In this video from ExtremeBartending, you can learn how to heat up and serve warm brandy, a classic drink, which is particularly nice to sip on a cold night. The video offers three separate ways to achieve your warm brandy, using hot water in a brandy snifter to warm the glass ...more
Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive. End ...more
Easter may have come and gone, but my love of hard-boiled eggs sure hasn't. Yet as much as I love hard-boiled eggs, I hate making them; I have to work in small batches to have consistent results, and they're always a little overdone, crumbly, and sometimes even green. Enter t ...more
Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resourc ...more
The following video demonstrates and explains a classic physics experiment called a vacuum cannon. Typically these cannons are made on a much smaller scale to fire ping pong balls, but I wanted to keep things interesting with this 4" diameter monster. Video: . Since this canno ...more
Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side sy ...more
These days, it's easy to cut the cord. Thanks to a new crop of streaming TV apps, you can get the same service offered by a traditional cable subscription at a fraction of the price. After some extensive testing, we believe we've found the absolute best apps for cord cutting. ...more
If you're quarantining with other people, consider yourself lucky — but it's not always easy. Staying in one space for so long with too many people can be challenging, so you need to find things to do to make the time go by (and to keep everyone sane). Our advice? Try out thes ...more
Maybe not water per-se, but with this simple technique you can turn one of the most abundant materials on earth into a highly explosive gas. WARNING: Ignition of an incendiary or explosive material may not be legal in your area, so check local laws before attempting. Use of t ...more
Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them. In each ...more
Coverage for the 88th Academy Awards, aka the Oscars, will air live this Sunday, February 28th at 4 p.m. PT (7 p.m. ET). The ceremony itself, hosted by Chris Rock, is set to begin at 5:30 p.m. PT (8:30 p.m. ET). This is the third year that ABC will be streaming the event onli ...more
Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all kno ...more
Perhaps one of the greatest embodiments of urban exploration lies in a disturbing and volatile mental health facility in Massachusetts, and its story starts with... Thomas Story Kirkbride. It's a name not many people know, unless you're a psychiatrist, or perhaps even an arch ...more
You can take an old, stainless steel refrigerator and turn it into a vertical smoker. Weld steel plates to make a fire box with a door and a removable ash tray, then reconstruct the frame to make yourself a new addition to your barbecue pit! Part 1 of 6 - How to Build an indus ...more
Gatorade: its popular red flavor can stain the whitest fabric, and its sweet taste is oddly refreshing after breaking a sweat. If you've ever participated in a sport, you probably spent halftime at games and practice breaks chugging the stuff. Though it made its name as a spor ...more
Sometimes you need a password to gain access to an older running Windows system. Maybe it's a machine in your basement you forgot about or a locked machine that belonged to a disgruntled employee. Maybe you just want to try out your pentesting skills. When you need to access ...more
This year, like every year before it, Black Friday sales are starting earlier than ever. A lot of stores will be opening their doors as early as 5pm on Thanksgiving to get a head start on the madness (and it really is madness). As we've discussed in the past, one of the keys t ...more
Just over a month ago, Google made its camera app available to all devices running Android 4.4 and higher. Originally exclusive to Nexus devices, the app got a UI overhaul and a new Lens Blur mode, but lost some features in the transition. A few weeks ago, Google began adding ...more
The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find ...more
I finally got around to trying out another one of Will's mad science experiments and found out that this one was actually more satisfying (and less frustrating) than my slightly uncooperative jar jet. There's something very pleasing about making potassium nitrate at home in th ...more
As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing ma ...more
A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of ...more
We all fall sleep in different ways. Some may require absolute silence, others need white noise, and some enjoy listening to a song or two to help bring on the sleep. If you're in the latter group, like I am, there's a problem. Fall asleep before the music stops, and a loud so ...more
Mr. G teaches you how to make a miniature jet engine by folding a piece of paper. Just make sure you don't set yourself on fire!
One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but lu ...more
Sodium (chemical symbol Na) is an interesting element. It reacts in contact with both oxygen and water, and several sodium salts are used to produce a yellow color in fireworks. The metallic form has limited uses in chemistry, and is too soft and reactive to be used as a buil ...more
Relays are simple redstone devices that allow you to switch between multiple outputs with only one input. They're incredibly useful in the right situation! There are many different types of relays, but I'll be showing you how to make two. One will switch power back and forth ...more
Minecraft never ceases to amaze, from programmable pianos to serial killers. But now someone has tackled M. C. Escher's famous Relativity lithograph from 1953 that depicts a world not bound by the normal laws of gravity. It's an amazing puzzle of a three-dimensional world trap ...more
Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes ...more
One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get ...more
PUBG is currently taking the mobile world by storm, and it's easy to see why. The game has breathed much-needed life to the multiplayer shooting genre, primarily by adding an element of sheer terror as you scavenge for weapons in a hostile environment. With new players continu ...more
By combining years of web search advancements, natural language processing, and even DeepMind's artificial intelligence, Google Assistant hopes to change the way you interact with your devices. If you're familiar with Google's previous services, Google Assistant is like Google ...more
Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Oh, the power of redstone! But, what good is any technology if it can't be harnessed for killing? Here's a redstone build for the mad scientist in each of us. Building the Death Ma ...more
This is a simple and easy tutorial, and anybody can build a hot air balloon out of a garbage bag by following the instructions in it. All one needs is a garbage bag, some stiff industrial wire and fire starter bars. The important thing, according to the author, is to judge how ...more
Trying to figure out which music streaming service to subscribe to can be a difficult task when the playing field is so crowded. Each has its benefits, as well as downsides, so finding the right one for your needs and wants can take a lot of overwhelming research. But we've do ...more
Your iPhone is full of features, many of which you might not even know about yet. Still, Apple keeps adding feature after feature with each new iOS update, and iOS 14.5 is no exception. The latest iOS version adds at least 69 features for your iPhone that you should be happy a ...more
Sinigang or Pinoy stew is one of the most famous and favorite meals among the Filipinos. It's also one of the most easiest to cook. Also, there are many ways to cook it, only the ingredients varies. The following tutorial is the most simplest form of cooking sinigang. This is ...more
Notch loves Halloween. He must, because he keeps putting scarier and scarier things into Minecraft around Halloween time! Today, Minecraft 1.4.2 was released, and it's a doozy. Versions 1.4 and 1.4.1 were actually skipped entirely, as lots of bug-fixes were patched between th ...more