Creating any object you want is as simple as point and click if you have a 3D printer at home. If you don't have one handy, there are a few companies that offer printing services online. But to help services realize your design in extruded plastic, you have to make a 3D comput ...more
WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most ...more
Social engineering is described as the clever manipulation of the natural tendency of human trust. All of the passwords, locks, and encryption in the entire world are useless against a good social engineer who can charm or trick you into giving it up. But what once started as ...more
Last Friday's mission was to accomplish solving HackThisSite, realistic 2. This second mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend take down a racist hate-group ...more
Math Craft admin Cory Poole provided quite a few recipes for sonobe models in his blog, and I followed one to make the pentakis dodecahedron here. I wasn't that happy with my first result because the colours kept on coming out wrong—i.e. two of the same colour next to each ot ...more
Cheers to another completed Community Byte project! Things went well regarding timeliness and being friendly to the other coders and students. If you've got ideas for our next mission, or an idea for a tutorial, submit them to me. Friday, our mission was to take out HackThisSi ...more
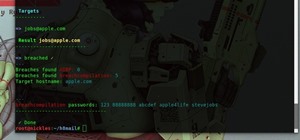
Our mission for this week's Community Byte was to create a Python program to crack web-based passwords, like the ones you would see on an email or router login. I wanted it to be universal in the sense that it could be easily modified and adapted to another website just by cha ...more
Permanently deleting files is something that a lot of people aren't aware of. Actually, most people think that once a file is deleted, it is gone forever. This is not the case. Hard drives write to the disk via magnetic charges, positive and negative correlate to 1s and 0s for ...more
In Linux, all password hashes are normally stored using the MD5 hashing algorithm in the /etc/shadow file, but MD5 is algorithmically weak due to collision vulnerabilities. The new recommended standard are the higher level SHA-2 hashing algorithms, SHA256 or SHA512. As a frien ...more
Leaving your wireless router at its default settings is a bad idea. The sad thing is, most people still do it. Once they've penetrated your network, hackers will change your router settings so they'll have an easy way back in. This allows them to change your network into a she ...more
Welcome to Math Craft World! This community is dedicated to the exploration of mathematically inspired art and architecture through projects, community submissions, and inspirational posts related to the topic at hand. Every week, there will be approximately four posts accordi ...more
Like the recent XSS 0day exploit found in the Mac and Windows versions of Skype, a similar one has been found in the Skype app for iPhone. The vulnerability allows an attacker to send a message that contains malicious JavaScript code in the "Name" parameter. This code can stea ...more
If you work in the film industry, are currently in film school, or have aspirations of being involved in the movie making process in some way, shape or form, you're probably very familiar with a certain set of books published by 411 Publishing that are commonly referred to as ...more
You may not do it in public, and you might not admit to it among your friends, but you do it. We all do it... sing. We sing when we're alone in our cars, at home when no one's listening, and when we've had a little too much to drink and don't care anymore, all inhibitions asid ...more
Circles. They are both the best thing and worst thing about Google+. They're great because they allow you to fine-tune who you're following and who you want to keep in touch with, making it easy to keep your family and friends separate from each other. On the other hand, they ...more
Google started culling Google+ accounts. There are two main targets: businesses and those who are using pseudonyms. For businesses, Google is promising to provide their own version of Facebook Pages, which will be released later this year. For those who use pseudonyms, they ar ...more
After the media outcry of Google Buzz's privacy issues, Google has set its goals on making the privacy parameters of Google+ simple to learn and as explicitly manageable as possible. No small feat. The approach has been to make the process of organizing your friends, contacts ...more
Google recently unveiled the start of their new social network Google+, which is set to compete with Facebook and fix the awkward, broken aspects on online sharing they claim exist. It's currently only open to a limited number of Googlers during its "field trial," and if you w ...more
Earlier this month, game developer David Braben and his Rasberry Pi nonprofit foundation revealed a $25 USB PC. The computer can connect to an HDMI monitor on one end, and a USB peripheral on the other (such as a keyboard or a USB hub). You can use the USB hub to connect multi ...more
Everybody loves Oprah Winfrey. Maybe it's because of her philanthropy. Maybe it's her onscreen personality. Maybe it's the fact that it was a rags to riches story. Or maybe it's because she likes SCRABBLE... The iPad SCRABBLE App by Electronic Arts had made it onto Oprah's Ul ...more
Why settle on just pork chops or ribs when you can string up the entire pig? Serious Eats posts an great slide show on roasting a whole pig, from materials to the process to the perfect pig roastin' sauce. Warnings PETA members should probably exit this page right about now. ...more
New Levels! Levels 70-90 released. You will get your 20 farm cash if you skip straight to 90 because you had enough xp, or the appropriate amount for however many levels you've completed. Game changes No more pink 'ready' dots all over when taking farm photos. Wheat is now ...more
This tutorial is in response to mail to Facebook. Scott Wilde leads you through the process. You can start by creating a brand new profile page. In this case, Mr. Wilde created a profile page for his dog Java Wilde so he could have a fresh new page without having to alter his ...more
Step 1 In the Adobe Flash program, select “Flash File (Actionscript 3.0)” from the “Create New” menu. Switch the workspace layout by clicking on the dropdown menu in the upper left of the top menu bar, and selecting “Designer.” You can adjust the size and color of the document ...more
Need a way to keep the kids busy on a rainy day? Making a pop-up card is quick, easy, and will entertain them for hours! Watch this video to learn how to make a pop-up card. You Will Need * Imagination * Colored construction paper * A pencil * A ruler * Safety scissors * Mar ...more
I loved The Amazing Adventures of Kavalier and Clay for so many reasons. For its fantastical sense of adventure, set against the real world action and tragedy of the Jews in Europe during World War Two. I loved the opening chapters of Josef in Prague – a city I spent several m ...more
This article is all about creating content and using it to build links to your website. Content, meaning articles, videos, and even podcasts is now really the new advertising. That’s because people go to the internet to look for information, not look at advertising. So you nee ...more
Have you ever forgotten your password and didn't know how to get back on your computer? Or ever had an annoying roommate you wanted to play a trick on to teach them a lesson? Or perhaps overly religious parents who think the internet is of the devil and won't let you read onli ...more
Eventually, we plan on doing some root the box competitions here at Null Byte, but we're still looking for a server to play on. Anyone want to donate one? You won't regret it. Root the box is like 'king of the hill', except you have to hack a server and maintain access. Each s ...more
We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no ne ...more
Here's something fun for the Null Byte community to do—a coding competition! This week, I wanted to get everyone involved by offering you all a nice library of possible program types to choose from and try to code. At the end of this competition, all of the submitted programs ...more
The community tore up the first realistic mission last week. You've applied the techniques learned in the basic missions to a real scenario, so I'm pretty content. The realistic missions are where the learning gets intense and where we can apply real knowledge to extremely rea ...more
Today I will show you how to create a simple keylogger in Visual C# Sharp, which will start up hidden from view, and record anything the user types on the keybord, then save it into a text file. Great if you share a PC and want to track what someone else is writing. You Will ...more
Yesterday, I started receiving emails from Google+ that looked like this: I was really confused. I was confident that I had already gone through my personal Google+ account notification settings, and turned off all email notifications. I noticed that there was a link at the b ...more
Welcome to the eighth Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to asp ...more
Welcome to the seventh Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to as ...more
Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educate ...more
Welcome to the sixth Community Byte for coding in Python and beating the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and essentially grow together. Everyone is welcome, from novice programmer ...more
Although most religions have inspired a variety of art, Buddhism seems to have a special relationship with the arts. Something about the endless circle of birth and rebirth seems to intrigue the minds of artists. Of course even if the art is not directly related to Buddhism, t ...more
"Google+ is dead." How many times have you read that in the past few weeks? It seems like I can't get away from this notion that Google+, as a social network, is a total failure. Don't feel too sorry for them, though. +Bradley Horowitz isn't worried. In an interview with Ventu ...more
Bokeh (which translates to "blur" in Japanese) is a photography technique referring to the blurred areas of a photograph. Basic bokeh photographs often have one point of focus, while the background falls away into a dreamy, blurred haze. The technique can be taken even furthe ...more
Fractals and stars are two of the most beautiful and complicated-looking classes of geometric objects out there. We're going to explore these objects and how to carve them on a pumpkin. Unlike the last one on carving polyhedral pumpkins, where we used the entire pumpkin to car ...more
Having a custom Linux distro can be the coolest thing ever. Most of you will probably be satisfied with any particular Linux distribution, but I know I'm not the only one out there who wants it to have custom configurations and programs preloaded while leaving the bloatware be ...more
Cross-Site Request Forgery (CSRF, pronounce "sea-surf") is a common web exploit. However, for unknown reasons it's not used very often. It plays on a given website's trust in a web browser by executing another website's form action, for example, sending money to another person ...more
Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills. Submit your best shot to our weekly competition for a chance to win an awes ...more
Since PDF files are so popular in both our daily life and work, we see them everywhere. And sometimes we find there are terrfic images or text in the PDF files and we want to save them as seperate files for future use, such as in a presentation or post. Here's the question: ho ...more
It's been an eventful week for Google+. Facebook decided to up its game and start rolling out several major updates intended to address privacy concerns. We got a glimpse into the future of Google+ via an insightful discussion between +Bradley Horowitz and +Tim O'Reilly. And G ...more
Games like Minecraft and Braid have proven that there is money to be made in the indie game marketplace, which means more and more designers are following suit, one being Zeboyd Games. The two-man indie design team released two excellent JRPG spoofs on the Xbox Live Indie Game ...more
Do you know how you are perceived by your peers? In real life and online? In the physical world, you could be seen as intelligent, thoughtful and hard-working, but on the Web you could be looked at as irrational, selfish and slothful. There's just something about the Internet ...more
Photoshop. It’s like a mountain to climb. You can chug up to the top, working hard, never letting up, or you can just go part way up and scoot around the side of the mountain and still get to the other side. Not everyone needs to be a Photoshop guru, or ninja pixel punisher. T ...more
Fads, Fiascoes and Good Stuff in FrontierVille This Week The second in a series of weekly columns. Fads first It’s still St. Patrick’s Day in FrontierVille, but it looks as though its days are numbered. I give it 'til the end of the month. Trees are in full summer leaf and ...more
This is a guide showing you how to get Java games onto your Samsung Tocco F480 phone via USB—for free! You don't need Samsung PC Studio, but you do need a few things... Download Required Applications and Drivers... Download and install these applications. I have included li ...more
This tutorial will walk you through the steps required to install the Ubuntu 9.10 operating system (Karmic Koala) on your computer. I have a Suzuki Kuiper 1411 HKS notebook computer with 2.1 GHz Intel Dual Core processor, 4GB RAM and 320GB hard drive. It has a dedicated 256MB ...more
INTRODUCTION If you are a part-time blogger and owns a blog which is hosted on blogger, then the first thing which you could want to do is to convert your blog layout to a professional looking website. You can either edit the XML file yourself or you could choose to use a tem ...more
Today Farmville updated some of the user interfaces for crafting and farmers market! Changes Enter each building separately if you have more than one. Cannot get to Crafting Building from Farmer's Market. Recipes listed in no particular order. New interfaces (see explanat ...more
You may want to create a list of certain friends so that you can post certain status updates, photo albums, links, or application posts for just them to see. I'll show you how to set up lists Select 'edit friends' from the top right corner of the screen under 'account'. Crea ...more
I have prepared a stable stuffing how-to for you! For more information about stuffing see this article. (There isn't any sound) Read along then try it yourself!. Clear some space on your farm and EMPTY your stable. You want to have a bunch of horses on the ground getting read ...more
In our media-enriched world, past and present, SCRABBLE has made a name for itself, whether deliberately, subconsciously, or influentially. You may have a read a book that had the popular word game within a chapter, watched a movie that showed your favorite characters bringing ...more
We've talked about the deep web before, but we never really covered the details of what's out there. It occurred to me that a nice list of resources would be very helpful to all of you anons out there. Think of this like a helpful brochure to the hidden web. However, I should ...more
Download the Software Go to the Antiprism downloads page. Download and install Antiprism 0.20. Run the Programs You need a method of running programs on the command line. In Windows, that could be a DOS box, on other systems a terminal emulator (e.g. xterm). Start this up. ...more