Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons. Most hacker tools are developed in Linux (well over 90 percent). Linux offers us greater granulari ...more
Facebook makes it easy to show how much you appreciate a funny status, great picture, or cool news article using their iconic "thumbs up" button, but what about those terrible jokes and annoying baby pictures? Where's the "thumbs down" for that crap? I've been excited for a " ...more
Apple's iOS 7 is riddled with annoying features, and some of them can't be toggled off in Settings. For example, I really don't like having labels directly underneath my app icons, and there's no way to remove them. Sure, it may be nitpicky, but it's my device, and it should b ...more
The flexibility within Android is pretty amazing. Unlike iOS, you can make a lot of modifications with nothing more than a download from Google Play, but to really step up your softModder game, you'll need to go a little further. Rooting takes things a step deeper, allowing y ...more
So, you find an interesting article online, but there’s something you don’t quite understand about it and instinct kicks in. Open new tab. Go to Google. Enter keywords. Search. Find information. Understand. It really doesn't get much easier than that, right? Wrong. That's jus ...more
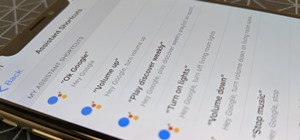
Communication is the key to any healthy relationship, and when I say any, I mean human and non-human. Previously, one of the biggest culprits for not understanding what you meant was Siri, but now it looks like it has some competition with the new Kinect system, which can cont ...more
This Video will Show you: How to Dye your hair at home from Start to Finsh on Natural hair. Enjoy! Pt.2 Dont Forget to Watch Part 1 Click on the Link to Watch: https://www.youtube.com/watch?v=gHZSNe-wQvA Thank you for Watching my Video. I would Love for you to Check out my Ne ...more
Video: . This Video will show you how to Dye your hair at home from Start to Finsh. Enjoy! Pt.1 To Watch Part 2 Click on the Link Below: https://www.youtube.com/my_videos?o=U Thank you for Watching my Video. I would Love for you to Check out my New FaceBook FanPage! Please Cl ...more
Unless you like paying exorbitant prices for out-of-contract phones, most of us are stuck with the one we already have for two or more years. The tech industry moves fast, and as new phones are released seemingly every month, your Samsung Galaxy S4 might start looking older by ...more
For new Android users, rooting an Android phone can often be an intimidating process, especially since there are so many different ways to gain root access, depending on your model and firmware version. I've previously covered a way of doing it for the AT&T version of the Sam ...more
There are definitely some very cool things about the new iOS 7, but it's also got plenty of downsides, one being the updated look of stock app icons. Apple drastically changed their glossy skeuomorphic icons for a flat, modern squircle look using their golden ratio grid. If y ...more
The shortest distance between two points is a straight line, but the shortest way to launch an app on an iPhone can be a much more complicated process. While Android users can practically drown themselves in home launchers and widgets for quick-launching apps, iPhone users ar ...more
We use ADB and Fastboot for so many things in our softModder tutorials, and to get them, you normally have to download the entire Android SDK and install them. But not anymore. shimp208 over at XDA Developers has made a minimal installer that we can download that'll only give ...more
Welcome back, my fledgling hackers! In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be. NOTE ...more
We've all been there. Your phone is on your nightstand, but you're on the couch in the living room browsing the web on your Nexus 7. Then you hear it—a faint sound for a new text message notification from the bedroom. Ugh. Don't you wish you didn't have to get off the couch. ...more
When you're at work or in class, there's nothing more annoying than sites that automatically play media. One minute you're happily distracting yourself, and the next, you're scrambling to hit pause while everyone stares at you. Not to mention now your boss knows you're slackin ...more
UPDATE: A patch to fix the exploit has been released. Download it here. A new vulnerability in Java 7 has been added to the BlackHole exploit kit and Metasploit that allows malicious software to be installed on Windows, Mac OS X, and Linux computers. So far, it has only been ...more
WordPress started in 2003 with a single bit of code to enhance the typography of everyday writing and with fewer users than you can count on your fingers and toes. Since then it has grown to be the largest self-hosted blogging tool in the world, used on millions of sites and s ...more
Safari's massive upgrade in Apple's latest iPhone software update includes new features you won't find in any other web browsers on iOS, from better ways to stay organized to enhanced security and further privacy protections. Apple's latest Safari improvements make web browsi ...more
Apple released the second beta for iOS 15 on Thursday, June 24. The update includes FaceTime's "SharePlay" feature for the first time, a new Maps icon, updates to Focus mode, in addition to many other changes and bug fixes. SharePlay, one of iOS 15's most ambitious new featur ...more
Apple's iOS 14 is here. With it, you'll see over 200 new features and changes hit your iPhone, including home screen widgets, inline replies in Messages, and cycling routes in Maps. Here's how you can get your hands on the brand new update. Apple released iOS 14 to compatible ...more
On an iPhone, it's easy to blur or cross out faces and sensitive information found in your images — just use Apple's Markup tool for all your obfuscation needs. Things aren't as simple when it comes to videos. There are no built-in iOS features to blur, redact, or otherwise ob ...more
Web applications are ubiquitous in the modern online world, and knowing how to attack them is an increasingly valuable skill. But the key to a successful attack is good recon since it's easier to be focused and efficient with the more information you have. There are many finge ...more
We use our smartphones every single day. They're a part of our daily routine, and as a result, we've gotten really good at using them — especially when it comes to typing very quickly. But just how fast can you type on your iPhone? Can you match your speed on a physical keyboa ...more
There are three tiers to Android customization: things you can do by default, things you can do with ADB, and things you can do with root. While root is still pretty tricky to get, ADB mods just got a lot easier. Back in Android 9, Google added a feature that allowed you to w ...more
For a built-in app, Notes works pretty well and can stack up against some of the best third-party note-taking tools. Apple continues to update it with each iteration of iOS, adding new features and improving existing ones to make jotting down your daily thoughts a smooth and e ...more
Wearing masks and social distancing doesn't sound like a fun movie night with friends, but you can still be comfortable and watch films together remotely. Services like Discord and Netflix Party make it possible to watch movies simultaneously from different parts of the U.S., ...more
If you keep your iPhone's home screen obsessively tidy, new apps are the bane of your existence. Hyperbole aside, they automatically fill the first available space on your home screen, starting on the second page, which can wreak havoc on your carefully planned layouts. With i ...more
Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available ...more
With more digital content than ever, the search feature on smart TVs is essential. But typing is such a terrible experience when you're forced to use voice dictation or peck around with the remote control. Thankfully, there's a better way. Most smart TVs support using your ph ...more
For the last three years, Apple has hosted its Worldwide Developers Conference at the San Jose Convention Center, but thanks to the COVID-19 pandemic, WWDC 2020 is now an online-only event. So what can you expect from the new virtual format and when and how can you watch the k ...more
The Galaxy Note 10+ is the pinnacle of Android hardware. You won't find many phones with a better combination of specs and design. But you may not love the software. Even with One UI on board, some users still want a more "stock" feel. Thanks to apps from third-party develope ...more
Apple has packed a lot of new features into the iOS 13 update, and practically no core app has gone untouched. The Messages app, in particular, got plenty of love, including new ways to dress and use your Memojis. Beyond the improvements and additions made to Memojis, Message ...more
One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get ...more
One of the most exciting things as an ethical hacker, in my opinion, is catching a reverse shell. But often, these shells are limited, lacking the full power and functionality of a proper terminal. Certain things don't work in these environments, and they can be troublesome to ...more
Switching from one popular music streaming service to another shouldn't have to be a hassle, but it is if you want to transfer all your favorite music over. No popular service offers a built-in feature to export or import playlists, so if you want to move your favorite Apple M ...more
The third developer beta for iOS 13 has been out since July 3, and while devs have had fun exploring all the new features, those of us on the public beta have sat on the sidelines running the public version of dev beta 2. But we don't need to wait any longer, as Apple just rel ...more
On July 3, Apple pushed out iOS 13 developer beta 3 for iPhone, and there's a lot found hidden within. A new FaceTime setting, more Arcade details, full-page scrolling screenshots everywhere, a noise cancellation option in the Control Center, and a new markup tool — and that's ...more
KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an a ...more
When it comes to digital security, one of the best ways to protect yourself is to use two-factor authentication. Most apps these days support it, including Facebook, a site where the more privacy you can muster, the better. However, of the two 2FA options available for Faceboo ...more
Switching phones has never been easier. Google backs up most of your app data on the cloud, which can then be restored onto your new phone. Sadly, Signal doesn't use this feature since it could compromise your security. Instead, Signal stores encrypted backups locally, requiri ...more
There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex e ...more
One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almigh ...more
When BlackBerry first announced the KEY2 back in June, the biggest gripe we heard was about the price. It was reasonable criticism, as BlackBerry was asking a lot of its consumers at $650. Knowing this, BlackBerry went back, made some downgrades, and cut the price, creating th ...more
With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative. Ruby is just one wa ...more
With iOS 12, Apple is making up for mistakes from the past, with iPhone batteries being no exception. The new update builds upon both battery health and performance throttling tools introduced in iOS 11.3 by offering users more information about your iPhone's battery usage tha ...more
As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing ma ...more
Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we ...more
Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even ...more
With ultra competitive games like Fortnite Battle Royale and PUBG taking the mobile world by storm, gamers are looking for ways to get a leg up on the competition. One of the biggest advantages you can give yourself is the ability to aim and shoot while on the move, but that's ...more
When it comes to streaming services, Google Play Music is one of the best options for both Android and iOS. Perhaps its single greatest feature is the fact that you can upload as many as 50,000 of your own songs to Google's servers, then stream your library to any device witho ...more
Apple just unveiled a red iPhone and iPhone 7 Plus, dubbed the iPhone 7 (PRODUCT)RED Special Edition, to commemorate the ongoing global fight against AIDS. Apple fans the world over are sure to swarm in and gobble up the initial stock shortly after the new color is released at ...more
Kodi, formerly known as XBMC, is one of the most versatile media players available. With it, you can play virtually any internet and media file in a large variety of formats, and it can be used on practically every single operating system out there, including iOS 10. Kodi, an ...more
Thanks to the Edge variants, Samsung's Galaxy S phones are just a few millimeters off in body size when compared to the Note series, and just 0.2 inches smaller when it comes to displays. Now that the two flagship models are almost identical in size—with matching curved displa ...more
Android Police reported that the upcoming Nexus phones would be getting an exclusive launcher this year, dubbed the "Nexus Launcher." This rumored home screen app was said to feature Google Now integration, a swipe-up app drawer gesture, and a few other finishing touches. Ama ...more
While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers di ...more
hello hackers,newbies and followers of this great community, after some research here in our community, I noticed that there is not even one tutorial that teach Web Development. We have a lot of tutorials on how to hack web site but many do not know exactly how a web site is c ...more
Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or ...more
As one of the most powerful Android apps for connecting your phone or tablet to your other devices in various ways, Pushbullet had always been a fan—and Gadget Hacks—favorite. However, ever since late last year, many of the app's popular and once-free features now require a c ...more
If you use Google Chrome as your default desktop/laptop browser, then Chrome OS will be pretty easy to get up and running if transitioning from Windows or macOS. Google has created an operating system that is fast, lightweight, and versatile enough to be adopted by pros and no ...more