Getting a new phone is like getting a pair of new socks—you can't wait to try them on and when you do, they feel totally awesome. Maybe that's just me, but for many customers that have already received their highly anticipated iPhone 5 in the mail, awesome is definitely not th ...more
Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with. Wardriving has been around since the '90s and combines GPS data and Wi-Fi signal data to create accurate, in-depth maps of any nearby Wi-Fi networks ...more
If you are wanting to learn how to perform small repairs to your car, then plastic repair is something you need to learn how to do. Cars are using more plastic now than ever before. With car required to increase fuel mileage, I don't see the use of plastic going away. In this ...more
If your new 2020 iPhone SE is frozen, unresponsive, or won't load the system, and a standard power down and up procedure didn't work, there are few more things you can try. Force-restarting the device may do the trick, recovery mode is a last-ditch option, and DFU mode is your ...more
During a recent press event, Corning revealed the latest generation of Gorilla Glass, aptly named Gorilla Glass 6. While the focus at the event was on the improvements to its scratch and impact resistance, Corning also revealed some exciting prototypes which change the texture ...more
It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?). SSLStrip and the HSTS Chronicles ...more
Enjoy the deliciousness of a peanut butter sandwich without the artificial chemicals that comes in store-bought jars. To make your own peanut butter at home, all you need are pre-roasted peanuts, peanut oil, and a little bit of salt and sugar. Roast the peanuts in the oven fo ...more
Unscrew chair and knock apart gently with a rubber mallet. To fix a broken stretch, use quick dry polyurethane glue, using plenty (better to have too much than too little) Wipe of excess glue. Leave to set for 10 minutes. Sand down the points that slot into the seat of the cha ...more
Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills. Wh ...more
Most wood furniture is long-lasting, durable, and resistant to great wear and tear over the years. However, set a single sweaty, wet cup or bottle on the surface of your favorite wood dining table, or your prominently placed wooden coffee table, and you'll end up with a round ...more
Update (March 18, 2014): Skype has issued an update to their Android app, and among other things, has "fixed" the runaway camera process issue by creating a workaround...and that's about all we know. No details were provided, but with the considerable uproar over the bug, let ...more
Sugru is some pretty versatile stuff. The company's slogan is "Hack things better," and for good reason. It sticks to aluminum, steel, ceramics, glass and plastics, it's waterproof and heat-resistant, and it can be molded into any shape you can imagine. Anything from your kitc ...more
Few things are more important than search engine optimization when it comes to increasing a brand's visibility online. Regardless of whether you're launching a new business from scratch or working as a marketing professional at a major corporation, you need to ensure that you' ...more
Even if you're lucky enough to not be injured in a car accident, it's rare to escape without some sort of damage to your vehicle. It goes without saying that there are some things you shouldn't try to fix yourself, but if it's just a scratch or dent, DIY can be a cheaper way t ...more
With warm weather comes bugs, and with bugs come bites, and with bites come itches. From ticks and spiders to mosquitoes and bees, insect bites come in sundry shapes and sizes, but they all commonly pull an itchy, red reaction out of our bodies. Once a bite fires up our immun ...more
However much you love your summer barbecue parties, you probably won't be going through your entire bag of charcoal briquettes anytime soon. So, take advantage of your charcoal excess by putting them to good use in other ways! Charcoal briquettes are great for removing excess ...more
Last week, I updated VirtualBox on my computer since I had skipped a few versions, then I could no longer copy text or paste text from my Kali virtual machine to my host OS and vice versa. Installing the Guest Additions didn't seem to do anything, and the bidirectional shared ...more
Food can smell great before, during, and after cooking. A pot of stew simmering away on the stove will tantalize you all afternoon, and there's nothing better than the smell of fresh-baked cookies lingering in the house for hours. One place you don't want to smell food? On yo ...more
It can be extremely frustrating when you've forgotten the pattern you use to lock your smartphone, and even more so if someone has managed to prank you by changing it. Luckily, there's an easy fix if you know the username and password for the Gmail account you used to set up t ...more
If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning e ...more
Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the ...more
Ever see those cars so covered in dirt, dust, and grime that someone writes "Wash me" on it using their finger? Well, for those cars' sakes, as well as cases less extreme, a word of advice: procrastination is not a solution — it can only compound the problem. Self-cleaning car ...more
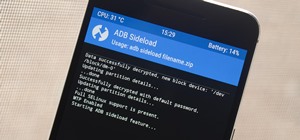
OnePlus phones are easy to root, but that also means they're easy to brick if you get trigger happy with your superuser privileges. If you find yourself in this situation, you'll quickly realize the OnePlus firmware download page doesn't provide files you can flash in Fastboot ...more
Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your sys ...more
After SquareTrade tested out the Samsung Galaxy S8 and found it to be the first phone to shatter on all sides after only one drop, it's nice to know we may have a solution for this $500 problem. If you drop your Samsung Galaxy S8 and you don't have a case, be prepared to pay ...more
If your company has already released some popular and addictive game and you're thinking about creation a sequel, this article is just what you need. We gathered the main tips and advices that will be useful for the building a strategy and a sequel itself. Check out the follow ...more
If you've ever had issues charging your iPad, iPhone, or iPod touch, like most other Apple products, the culprit to blame is usually a frayed or damaged cable. It's a common design flaw due to the thinness of the cords and the weak sheath surrounding them — but that's not alwa ...more
You must have seen some expensive mp3 players and CD players which have LEDs fixed on them and they dance to the tune looking really pretty. Imagine you could make your own LEDs and configure them to dance to Daft Punk or Swedish House Mafia. I’m going to tell you how it can ...more
TWRP won't be ready for the Pixel 4 and 4 XL until months after release. But since you can already root with Magisk and tinker with the OS, you might find yourself in a situation where your phone won't boot, yet you don't have a custom recovery installed to fix it. Luckily, th ...more
Phones these days are expensive. The iPhone 11 Pro is presumed to start at $999, following the iPhone XS and iPhone X's leads. One way to bring down that cost is to trade in your old iPhone, but there isn't one clear-cut way to do that. You could trade your iPhone into a parti ...more
We're nearly done getting our Mac set up for hacking. If you haven't checked out previous tutorials, I'd recommend you do so first before diving right into this one. While macOS is a powerful POSIX-compliant operating system, some of our Linux tools do not work out of the box ...more
Withstanding an attack from a motivated hacker is one of the most important responsibilities a system administrator must undertake. This is especially true for websites that may contain sensitive customer information and a high volume of users. So it's important for a sysadmin ...more
We were really rooting for you this time, BlackBerry! With the phone company having minimal success in the past with smartphones, the BlackBerry KEYone was extremely promising. That is until YouTube Reviewer JerryRigEverything discovered a fatal flaw, the phone's screen popped ...more
When you were unboxing your Galaxy Note7, you probably wondered why a little metal claw tool was included in the packaging. Then, if you looked closer, you saw there were five plastic sticks included with the claw tool that came in two different colors. Well, these pieces are ...more
Tricking your eyes into seeing 3D images isn't all that hard in movies or even in virtual reality, but when you start projecting holograms into the physical world, you run into some difficult problems. Microsoft obviously figured them out with their HoloLens, but how? The proc ...more
Every once in a while, we stumble across something food-related that makes us stop and do a double take. Frozen lemonade pie definitely takes the cake—or shall we say, pie—for a dessert that intrigued us upon discovery and totally lived up to its hype. Its filling uses only th ...more
No doubt you internet-savvy folks have seen the incredibly beautiful rainbow bagel going viral all over the country—and if not, let me educate you on its multicolored brilliance. Crafted by the brilliant bakers at The Bagel Store in Brooklyn, this cheery creation has actually ...more
Boxed brownie mixes advertise their convenience compared to homemade brownies—with only a few ingredients, they promise a moist, chocolatey crumb. However, these "instant" mixes still require fresh ingredients and a baking time that matches that of homemade brownies. When you' ...more
Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system. Note: A lot of what I am going to say is directly based off of this article by Patrick Mosca. Please give him your gratitude and leave mine at the door! Step 1: Reverse S ...more
Planning a Super Bowl party, or any football-themed party for that matter, can be fun for even the most craft-adverse host, as almost anything brown can turn into a football with just a little decoration. With a little planning, you won't be serving up any Pinterest fails this ...more
As I've said before, slowing down is not an option for me. At one point, I realized that there were plenty of files on my Mac that I didn't need any more, but too many to delete individually. In other cases, your Mac can be experiencing some major malfunctions: constant crashi ...more
The debate over whether to deep-fry or roast a Thanksgiving turkey can get pretty heated. Both have their merits, but it's hard to argue with that crispy, golden brown skin and moist texture that the fryer gives. But what's better than a deep-fried turkey? An entire deep-frie ...more
The USB Rubber Ducky is a famous attack tool that looks like a USB flash drive but acts like a keyboard when plugged into any unlocked device. The Ducky Script language used to control it is simple and powerful, and it works with Arduino and can run on boards like the ultra-ch ...more
If you ever want to root your OnePlus 6, install TWRP, get Magisk and Xposed, or flash a custom ROM, the first thing you'll need to do is unlock your bootloader. Your bootloader is a piece of firmware that loads up the operating system on your phone. Normally, it's programmed ...more
Spotify is one of the most popular music streaming services available and allows you a high degree of control over the way you experience your music. Included in that is the album art for your playlists. While not an option ingrained in the mobile app itself, changing a playli ...more
To please those of us who love to mod and root our Androids, OnePlus has made both the OnePlus 5 and 5T relatively easy to customize — so much so that the 5T topped our list for the best phones for rooting. Unfortunately, unlocking the bootloader and using root to modify the f ...more
Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to id ...more
The Xposed Framework is an incredibly powerful tool. But because of this power, there's a chance that something could go wrong when installing a broken or incompatible module, which can cause bootloops or even soft-brick your phone. Depending on how bad the situation is, the ...more
RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices. I initially covered RouterSploit on Kali Linux and macOS (OS X), but this tuto ...more
Because of Android's new SafetyNet system, certain apps can now block rooted users or prevent you from accessing them altogether — but at least for now, there are still ways around these restrictions. You can pass most of SafetyNet's checks with Magisk and systemless root, bu ...more
The modern age of techno-dating has made an interesting landscape for social interactions when there is some modicum of romance (or lust). For those of us born before the internet evolved into the prolific monster it has become, we first met our love interests face to face. To ...more
During my time living in dorm rooms and small apartments, I would find myself in need of many different appliances—a food processor for making hummus, a blender for vegetable smoothies, or even a mortar and pestle for muddling mojito-bound mint leaves. Luckily, there was one t ...more
Windows 95, which introduced the Start menu to the world, recently celebrated its 20th birthday! The feature was an instant hit, becoming a core component of Windows operating systems. Well, it was removed in the mistake that was Windows 8, but you should know by now that the ...more
Google's Chromecast is quite literally one of my favorite inventions of the past five years, allowing me to kick back, relax, and enjoy the various forms of streaming entertainment it has up for grabs. Don't Miss: How to Use Your Chromecast Without Wi-Fi But as awesome as it ...more
There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distributi ...more
Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pen ...more
After more than a decade, iPhones are finally getting widgets on the home screen. They even have that Apple aesthetic that many people crave, with their uniform, squircle appearance. But fret not, as with pretty much any iOS feature, you can get them on Android with a tiny bit ...more
Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target. Thanks to a pair of recon tools coded in Python, it takes just seconds to research how a website or server might be vulnerable. No matter what platform ...more
If you have a modern iPhone, you have an excellent video recorder at your disposal. Every iPhone since the 6S has the ability to shoot in 4K resolution, and each new iteration has brought new capabilities to the table. But even the best mobile shooter can use a little extra he ...more
One of the most powerful features when editing videos with Enlight Videoleap is the keyframe tool, which allows you to add custom transitions, animate text, granularly adjust audio, move video clips across the frame, supplement effects, and more. If you want your video to chan ...more