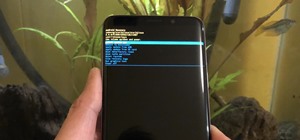
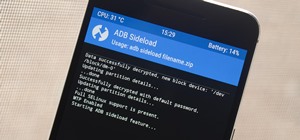
If you still have time left on your warranty, taking your HTC One in for repairs can be a serious pain if you've modified it in any way. To avoid the chance that they'll reject your phone because it's been tampered with, you'll have to return it to stock condition. To Do This ...more
As you may have noticed, many of our tutorials cover topics that require you to have root access. When your phone is rooted, backing up apps doesn't require you to connect to your computer, and installing custom ROMs lets you get more useful settings. Rooting also lets you get ...more
Cell phone jammers, a DIY endeavor for the darker crowd. I'm pretty sure we've all considered having one at some point: whether the obnoxiously loud woman next to you is announcing private bedroom stories to a crowd on the subway, or your kids are grounded from using the phone ...more
Anyone who has rooted their Android device has likely used a tool called Android Debug Bridge, better known as ADB, at some point during the process. For most, that is their only interaction with the ADB, but to be a true Android power user, you need to really know the tools a ...more
Apple released the iOS 8 Gold Master build to developers shortly after their WWDC event ended on Sept. 9th, which is jam-packed with tons of new features for iPad, iPhone, and iPod touch. The public version comes out on Sept. 17th, but if you can't wait to test out iOS 8, you ...more
There's a whole world of wallpapers out there. Apple always includes a selection of stock wallpapers, some unique to every iPhone model you have. Of course, sometimes, stock wallpapers don't cut it. Sometimes, you want to add your own style to your home screen and lock screen. ...more
Only so much data can be passed through the network and to your computer's networking interfaces. This is limited by the amount of bandwidth you have. The more bandwidth you have, the faster your network connections will be. Not only this, but your transfers will be more paral ...more
Originally made as portable convenience locks, padlocks are known for their cheap, simplistic and relatively secure design. Their construction is made up of a body, shackle and locking mechanism, with the shackle typically assuming a "U" shape to be easily linked to things lik ...more
Microsoft has had a pretty bad wrap with their Xbox 360 gaming console. Right from the start, the console has suffered a multitude of different hardware failures and design flaws. These problems cause the parts to get too hot and become faulty. I'm sure everyone who's had an X ...more
When Google released Android 4.2, a new feature was introduced for tablets that allowed for multiple accounts to be used on a single device. In order to create a unique experience for each user, apps and personal data were kept separate, and switching between users became as s ...more
Often times when staying at a hotel or anywhere for that matter, you'll whip out your laptop and check the local area for Wi-Fi. I know you've all been in my shoes when you find an unsecured network that appears to be public Wi-Fi belonging to the hotel or airport, and you con ...more
It's the icing on top of your cake (or whipped cream on top of your Android Pie) of despair. You may have not had the easiest time rooting your device, but you feel like you overcame all of the obstacles. Only now to discover that those very apps and mods you were rooting for ...more
The digital pen on the Surface Pro 4 and Surface Book is an indispensable tool for serious note-takers and artists alike. Out of the box, the Surface Pen is pre-programmed to do some pretty wonderful things. For example, the eraser can be single-clicked to open Microsoft's On ...more
Google's strategy for updating its apps with dark mode options is apparently "one at a time" and "as slow as possible." Even after the company added a dark theme to many of its apps for Android and iOS, such as Calendar, Chrome, Keep, and Photos, Gmail seemed to remain "light" ...more
Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. While mining is a basic aspect of Minecraft, it is often overlooked. Every adventure requires iron and diamonds and other ore and if you're playing in hardcore mode then you need al ...more
Have you ever forgotten your password and didn't know how to get back on your computer? Or ever had an annoying roommate you wanted to play a trick on to teach them a lesson? Or perhaps overly religious parents who think the internet is of the devil and won't let you read onli ...more
With portable devices being a necessity in modern everyday life, they may be subject to overuse, improper charging, or normal wear and tear. For those people who carry around their smartphone or iPod with them all of the time, how many times have you been out and about just to ...more
I can't believe it, but I've actually read about dozens of people getting their iTouch, iPhone, or iPad stuck in a bricked recovery loop and then going out to buy a new one. This is overly unnecessary. When it gets stuck in the recovery loop, some people mistake themselves by ...more
There is a vast amount of knowledge out there on computers! In fact, it is so vast that no single person could ever possibly ever learn everything there is to learn about hacking or computers in general. People usually specialize in a certain field: cryptography, computer secu ...more
You'll see a lot of Linux action going down here at Null Byte. We use Linux for hacking-related stuff because it provides a more relaxed programming environment, making it easy to write exploits and tools. Linux has many features Windows is lacking, such as full control over t ...more
If you've ever heard software piracy terminology being discussed, I'm sure the term KeyGens came up. KeyGens is short for key generator, which is a program that exploits algorithmic faults in software by generating software license keys that appear to be genuine. Normally used ...more
Samsung does a good job of making their devices fairly open, and the Galaxy S3 is no different. There are numerous way to root a device, but sometimes the jargon and steps can be a little intimidating for new rooters, and even pro rooters. XDA Elite Recognized Developer Adam ...more
Theming and modding are a big part of the softModder community, but there are endless ways to customize our Android devices. Which ones should you download? Which ones should you avoid? It's extremely frustrating to find them all—and pick and choose. Now, thanks to developers ...more
When we're dead tired but need to stay awake, we humans can do many things to make the drowsiness go away, from taking a cold shower to downing energy drinks or coffee to acupressure. Unfortunately, our Android devices don't have as many options for staying awake, or the luxu ...more
Besides having an awesome name, widgets are nice little additions that help make your phone more functional and customized. There are plenty of Android widgets available in the Google Play store and from other third-party sites and developers, but XDA forums member Roymam deci ...more
Much like Xposed or Cydia, Magisk has an official repository that makes it easy to download root-level tweaks. These tweaks are called modules, and they can do anything from changing your emojis to installing high-level audio mods. But as it stands, a large number of Magisk mo ...more
Haven't you ever wanted to live in a futuristic home? I think that homes are headed towards an era where they will be controlled by our computers and smartphones. No longer will you have to find your keys to unlock your door, or wait until you get home to monitor your security ...more
I feel like doing a bit of chemistry today, how about you? To my knowledge, thermite is the hottest burning man-made substance. Thermite is a pyrotechnic composition of a metal powder and a metal oxide that produces an exothermic oxidation-reduction reaction known as a thermit ...more
JavaScript is the language of the internet. It is what allows us to create dynamic, interesting webpages that are fast, web-based applications and so much more. The primary use of JavaScript is to write functions that are embedded in or included from HTML pages and that intera ...more
Hello, multicolored-hat hackers! Today I am going to show you how to use the wordlists that come preinstalled with Kali Linux to crack those annoying hashes that contain our passwords. I'm sure that at some point in all of your lives, you have attempted to crack a password by ...more
Lock picking is defined by locksmiths as "the art of opening a lock without the key". There's many ways to accomplish this, but I'm specifically interested in using a lock pick set. Since locks vary in shapes and size, it's better to stick with just one kind of lock at first. ...more
The first few times I posted on some of the Android forums out there, I asked things like "Does anybody how I can make my phone do this or that?" Without fail, the responses to these types of questions were always one word—Tasker. If you're not familiar with it, Tasker is an ...more
In this Null Byte, I'm going to teach you about Null Byte Injections. Null Bytes are an older exploit. It works by injecting a "Null Character" into a URL to alter string termination and get information or undesirable output (which is desirable for the malicious user). All l ...more
There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distributi ...more
The internet is a scary place, and if you're like me, you don't want anyone tracking you or learning your search habits. It's a blatant invasion of privacy for companies to do this, but at least we have methods of fighting back—one of which is Tor. Tor stands for The Onion Ro ...more
This Null Byte is the first part in a mini-series on the art of Social Engineering. I will be teaching you how to effectively defend yourself against it. What is Social Engineering? Social Engineering is the art of hacking humans. It's when a person is manipulated into doing ...more
Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. And don't miss this weeks Weekly Workshop! If you're anything like the typical Minecrafter, then you've got a few secrets to hide. Maybe it's valuable commodities like diamonds, ore ...more
As we near the one-year anniversary of its release (and the inevitable unveiling of its successor), the Samsung Galaxy Note 3 remains a device that packs quite a punch when it comes to hardware. It boasts a 2.3Ghz CPU and was the first mobile phone ever to house 3GBs of RAM. S ...more
In my last article, I explained why text adventure games are some of the most Steampunk computer games out there. I even shared a free Steampunk text adventure game that I'd made myself! Now, I grew up playing text-based games (which are now known as interactive fiction) such ...more
Hey wizards! I've compiled a list of all the Sun, Moon and Star spells you can learn, who to learn it from and what level is required to use it. Sorry, no pics. Scroll down to the bottom for links.Solar Spell List Enchantments Cloak - 0 pips Effect: Cloak a Ward or Charm Locat ...more
Nearly two years ago, Peter Chou, CEO of HTC, confirmed that the company would no longer be locking bootloaders. Whether or not they've actually lived up to this claim is debatable. Any phone bought from a wireless carrier comes locked. Only the new HTC One Developer Edition s ...more
Last Friday's mission was to accomplish solving HackThisSite, realistic 2. This second mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend take down a racist hate-group ...more
File recovery on Linux is a bit different than Windows. It requires different software than the Windows counterparts because every OS has their own file system. Windows uses NTFS, or FAT file systems, while on the other hand, Linux uses ext-based file systems. I personally use ...more
Welcome to part three in a series about steganography, the art of hiding things in plain sight. We are practicing steganography because it can be a useful skill if you don't have access to encryption software, or need a quick solution to make sure the sender and recipient are ...more
Paying for web hosting isn't ideal in most situations. If you have your own website, hosting it yourself is very acceptable and easy to do, assuming your internet bandwidth permits. Most people want to run a personal site, nothing crazy, so hosting from home on low-bandwidth i ...more
Keyloggers are a must-have tool in your arsenal. Hardware keyloggers have the advantage of being undetectable through anti-virus or other protection programs. They also capture keystrokes before the OS even boots up, so they are pretty handy tools. The only issue with these t ...more
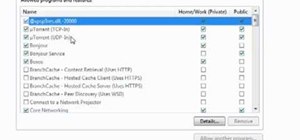
Warning Don't torrent things that you do not have the rights to torrent. Everything I torrent, I have a physical copy of, and just want a copy on my computer without causing wear-and-tear on my DVD drive's laser. Piracy is naughty. I used to get extremely frustrated with Bit ...more
With the mass arrests of 25 anons in Europe and South America, and the rumors of an FBI sweep on the east coast of America floating around, times look dicey for hackers. Over the past few days, a lot of questions have been posed to me about removing sensitive data from hard dr ...more
Last Friday's mission was to accomplish solving HackThisSite, realistic 1. This is the first in a series of realistic simulation missions designed to be exactly like situations you may encounter in the real world. This first mission, we are asked to help a friend manipulate th ...more
There are many impressive accomplishments in Minecraft, too many to name in fact. Sprawling builds, complex machines, and massive servers are the hallmark of Minecraft and things keep getting bigger and better. No one doubts the epic scale Minecraft has reached, but every once ...more
Technology in computers these days are very favorable to the semi-knowledgeable hacker. We have TOR for anonymity online, we have SSDs to protect and securely delete our data—we can even boot an OS from a thumb drive or SD card. With a little tunneling and MAC spoofing, a dece ...more
Last Friday's mission was to accomplish solving HackThisSite, realistic 3. The third mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend restore a defaced website about ...more
Yes, I understand some people may consider this a repost. However, I have been searching for this answer for 3 weeks and after reading numerous reddit post, Kali Forums post and Null byte post I finally have gotten it to work for me. I would like to compile and share this info ...more
You might be sitting there thinking that I'm crazy, but the truth is you're only partially right. You can get free text messaging for life, all for a cheap, one-time fee. But, how can that be possible? An exploit in AT&T's prepaid GoPhones is the culprit behind this sweet, oh- ...more
Update: The installation process for Xposed Installer is now dead simple—check out our updated guide! Xposed is a framework created by XDA developer rovo89, which allows the end user to customize their stock or custom ROM without having to modify any system applications or fi ...more
If you're interested in bypassing Windows and Linux passwords, there is a great tool from the good people at Kryptoslogic. Have you ever forgotten your administrator password? Have you ever bought a used computer with a password on it? Well, Kryptoslogic have created a boot-di ...more
Encryped traffic and tunneling is a must when away from home to keep you and your information safe. SSH tunnels can be slow, and are heavily encrypted. VPNs are an all port solution, and proxies are just not what we need in most cases. Then, there is Tor. Tor runs your traffi ...more
Let's say today is your birthday. You've just put those boisterous, vicenarian times behind you, reaching the first big step to your upcoming midlife crisis—30 years old. Maybe this is your midlife crisis. After all, if you're not where you want to be in life when you join the ...more
Let's say that you've got the look down, and you have your Steampunk props all ready to go. Congratulations! You're a Steampunk! But now what do you do with yourself? You can sit there, patting yourself on the back, but that gets lonely after awhile. Your props will look nic ...more
There are some calls you really don't want to miss. Whether it's "I'm going into labor" or "We have some questions about your résumé," not being able to answer or respond to certain messages can cause some serious problems. No matter what the case may be, missing a call or fo ...more