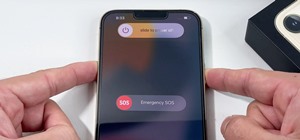
Apple has released the third beta of its iOS 7.1 software to developers, just a few weeks after their second beta introduced us to button shapes, a new calendar list view toggle, a hidden Car Display control and several other tweaks and performance improvements. Update: iOS 7 ...more
It has been 7 long years since the PlayStation 3 was released, which makes it no surprise that over 1 million gamers purchased the new PlayStation 4 this weekend. One of the coolest new features on the PS4 is its all-in-one video and screenshot editor. Recording your gameplay ...more
Welcome to this short and easy tutorial on hacking and DDosing (is that even a word I don't know) anyways lets get started First of all DDos means distributed denail of service attack, and yes i don't know what the HELL it means either. but anyway DDosing is where you spam a ...more
One of the first things most people ask for when staying with a friend is the password to the Wi-Fi network. Even if you trust your friends to the end of the earth, a super secure password can be a pain to share with them, especially if it's just a bunch of random characters. ...more
There is nothing more refreshing than an ice cream in a hot summer day. And even though, here in Australia, summer is "just" a couple of months away, I still like to have a scoop or two every now and then. However, I like to make the ice cream on my own. In this way, you can m ...more
One of the very first Photoshop skills we learned in my tenth grade photojournalism class was cropping the background out of images. I hated it. It was extremely time consuming, and the magnetic lasso tool never seemed to want to cooperate with me. Nearly a decade later, the ...more
When I was moving into my current apartment, I had to store some of my things in my ex-roommate's garage for over a month while I was getting settled. One of those things was my dresser. Upon moving it into my new place, I realized something was horribly, horribly wrong—none o ...more
In any project management career, there is no such thing as a person who knows everything for each project. Many times, those who got too much confident with their jobs fail because they were not able to make things clear before and during the project implementation. Be certa ...more
There are so many things in life I wish I could've canceled without any repercussions, and I'm mostly talking about text messages. But nothing is more annoying than cancellation fees. Booking a hotel in advance is usually a good way to save some money and make sure all things ...more
Did YOU know...that African Americans have the highest rate of colorectal cancer, and that it is more likely to be advanced at diagnosis? The age for colonoscopy in ACG guidelines dropped to 45 for African Americans in 2009. This digestive ditty about colon cancer screening in ...more
Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms. First, I covered embedding a listener in ...more
Last year, Lytro released their first light field camera to help photographers have more control over focusing. This innovative and revolutionary camera allows users to change the depth of focus of a photograph after the picture is taken. Video: . These depth-of-field-changeab ...more
There is no better example of a risk-versus-reward scenario than jailbreaking your iPhone or rooting your Android phone. While both jailbreaking and rooting undoubtedly has its advantages, this possibility of something going wrong and you ending up with a 500-dollar doorstop i ...more
With the microwave oven transformer (M.O.T.) salvaged in a previous project, a simple electrical circuit can be rigged to get high voltage arcs to fly outward and upward along a "V" shaped spark gap. You can look, but don't touch! These arcs of plasma are lethal enough to kil ...more
If you've ever logged on to the popular music application Pandora, your password is saved onto that computer in the local storage...for good. So for everyone reading this article, you should change your password to a throwaway one that's only used for Pandora, because if you ...more
The iPhone 5 will be here in no time. Pre-orders started at 12:01AM PST this morning and it's expected to start shipping in about two weeks. Verizon, AT&T, and Sprint are all handling unlimited data plans differently, so if you currently have an unlimited plan and are going to ...more
With the release of Windows 8 right around the corner, if you plan on buying it (or just want to see what it's all about), it's a good idea to take advantage of the free trial before you shell out any money. If you're an Apple user who doesn't have a deep-seated disdain for Mi ...more
Facial recognition software is being more widely used with every passing day. Your local law enforcement is probably already using it, and it will be even easier for them now that the FBI handed out its own facial recognition software to state authorities. Even the fine folks ...more
Mountain Lion (OS X 10.8) is out today, available in the Mac App Store for just $20. Unfortunately, installing Mountain Lion requires that you already have a Mac running Snow Leopard (OS X 10.6) or Lion (OS X 10.7). If you're currently running a Leopard system, you're out of l ...more
Everyone loves using their cell phones for everything except actually making phone calls. Whether it's watching streaming video, listening to music or playing video games, it would seem that calling people is almost an afterthought to cell manufacturers in this day and age. U ...more
Popsci has posted 2009's most amazing scientific images, and there's quite a few great ones in there. A few of our favorites below, click through for all 62. In short, Cow Farts. "Scientists measure methane at the source: In a lush pasture near Buenos Aires, this cow and its ...more
There seems to be no end to all the viral TikTok sound bites and trending TikTok songs, and there's a good reason why they are ingrained in the fabric of our pop culture. TikTok's short audio clips can evoke laughter, tears, and a wide range of other emotions, and many of them ...more
Aside from the addition of bedtime sleep schedules five years ago, Apple's Clock app has largely been ignored with each new iOS software update. But that just changed with Apple's iOS 17 software update. With the updated Clock app, you can finally set more than one timer to ru ...more
There's a feature that every Apple Watch owner should know about — one that makes navigating menus, tapping tiny icons, and interacting with complications, among other things, much easier on the small display. The little-known feature gives you complete control of your Apple ...more
You can play background sounds on your iPhone to help you focus, stay calm, or fall asleep, giving you a personal sound machine wherever you go. Even better, there's a way to set each of your apps to play one of Apple's six ambient soundscapes automatically. When you open the ...more
Downloading content from TikTok is relatively easy, even if the video is protected, but the same can't be said of Reels, Instagram's version of short-form videos. Instagram doesn't make it easy to download content unless it's your own, and that's especially true with Reels. Ho ...more
A man-in-the-middle attack, or MitM attack, is when a hacker gets on a network and forces all nearby devices to connect to their machine directly. This lets them spy on traffic and even modify certain things. Bettercap is one tool that can be used for these types of MitM attac ...more
Apple's iMessage is one of the main reasons to use an iPhone, and there's a lot you can do in chats without being overly complicated. But there's one issue that continues to drive people nuts, and that's the blue typing bubble indicator with the moving ellipsis (•••). Can you ...more
I always keep my iPhone's Portrait Orientation Lock on so that my screen doesn't randomly rotate while I'm lying down. However, there are certain apps that I do turn it off for. It's kind of a pain since you have to swipe down the Control Center and toggle the orientation lock ...more
Do you want to know some quick tricks for improving tech processes at your company? How about equipping yourself with skills that will land you a new job or promotion this year? Becoming a cloud computing expert will make it happen, and right now, The 2021 Cloud Computing Arch ...more
ADB and Fastboot are powerful tools that have always required a computer. But with the right setup, you can now send commands to a phone using another phone. The ADB and Fastboot Magisk module, by osm0sis and Surge1223, will turn your phone into an ADB terminal using root acc ...more
Amazon Web Services (AWS) offers over 200 services, including networking, computing, storage, analytics, blockchain, mobile, and developer tools. Not surprisingly, numerous companies rely on AWS's massive infrastructure. Instead of building their own server farms, they rent sp ...more
3D printers allow hackers and makers alike to create something from nothing. They're an incredible technology that lets you build protective cases and covers for gear such as a wardriving phone and Raspberry Pi-Hole. 3D printers can even help you out in a bind when something b ...more
Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a ...more
It feels like just yesterday Apple unveiled iOS 13 to the world, introducing game-changing features like system-wide dark mode and enhanced editing tools in Photos. But WWDC 2020 is rapidly approaching, which means iOS 14 is as well. As it turns out, we don't need to wait for ...more
Individually addressable LEDs, also commonly called "NeoPixels" after the popular Adafruit product, are a bright and colorful way to get started with basic Python programming. With an inexpensive ESP8266 or ESP32 microcontroller, it's easy to get started programming your own h ...more
While its competitors are concentrating on building out AR cloud platforms to give advanced AR capabilities to mobile apps, Ubiquity6 is taking a step in a different direction. On Monday, the company opened its Display.land tool to the general public, following its "early acc ...more
What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system. Understanding the Attack Whi ...more
Mobile gaming has exploded in recent years, with experts predicting 2.4 billion global mobile players by the end of 2019. It already accounts for 47% of the worldwide gaming market, besting console and PC. No wonder we've seen the rise of gaming smartphones, a class of phones ...more
Phone specs get better and better each year, and multiplayer mobile games are right there with them. Instead of playing solo, jump into some real-time gameplay with co-op and player vs. player modes, and battle friends, family, and strangers from around the world. But which mu ...more
Your phone's keyboard is one of the most commonly used apps. Whether you're typing out status updates, sending private messages, or just bombarding everyone in sight with as many emoji as you possibly can, you probably couldn't get by without a good keyboard app. Since Androi ...more
Traveling abroad can be a hassle. Between the flight, hotels, food, and the languages barriers, it can be a lot to manage. There's one tool you have that can help with all of this — your smartphone. Fortunately, nowadays, you don't have to change your carrier to continue using ...more
Some of the big guns developing augmented reality technology fired shots at their competitors with announcements and leaked plans this week. Enterprise augmented reality software and hardware makers were served notice by Microsoft when the company strengthened its own offerin ...more
It doesn't matter how cool or groundbreaking a particular technology is, if it doesn't offer the promise of big returns on investments, you'll have trouble drawing interest from both Silicon Valley and Wall Street. That's why we're increasingly seeing existing augmented realit ...more
Forget the rise of the machines. Tardigrades are set to outlive everything — even the bots. When the last echo of a whisper in a cell phone has long dissipated into space, the water bears will still be hanging out. In Hollywood, there is a never-ending march of movies set in ...more
If you want to appreciate the value of microbes, look no further than a chunk of cheese. Because cheese roughly traces back to the Neolithic Era, we might say the earliest cheesemakers were the first humans to manipulate microbes—without even knowing it. Now, thanks to microbi ...more
Hello people, I'm back for Part-3. In this part, as promised, we are going to create a client program and then we are going to test it with our server program made in Part-2. Much of the code that we are going to use in our client program as already been explained in Part-2 w ...more
This is the second installment of the short series on how to remove user passwords in Windows. Once again this has only been tested on Windows 7. If I can find some time between two jobs and school I'll test all the ways on Windows 10 and Windows 8/8.1. Step 1: Startup Repair ...more
Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... ...more
Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator. In earlier posts in this series, we examined registry fi ...more
Historically, battery life has not been a strong suit for machines running Windows. Poor decisions by hardware manufacturers combined with the resource-hogging behavior of Windows are to blame. However, Microsoft is trying to resolve this issue, once again, with the release of ...more
Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requi ...more
Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the inf ...more
April Fools may be over, but any day is a good day to prank someone, and the best time to do it is when everyone's eyes are glued to the television. Turning off a TV during a climatic moment is the best way to prank a TV-obsessed sibling or friend, but it's even more hilariou ...more
Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics. I applaud each of you for your concern, as the last thing I ...more
Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot ...more
In a previous article, I demonstrated an Arc Welder made using parts from old microwave ovens. Video: . Here is part 1 of 2 on how that arc welding machine was made, and how you could make one too! This is the first of two parts on building it, focusing on the modification of ...more
First off—Happy Independence Day! Since it's the 4th of July, let's make this week's roundup short and sweet, so you can all get back to your holiday festivities. Things to Do on WonderHowTo WonderHowTo is a how-to website made up of niche communities called Worlds, with top ...more
Your iPhone is fairly secure by default, but Apple's Lockdown Mode takes it to Fort Knox levels of protection. If you're a high-value target for spyware, phishing attempts, and other sophisticated cyberattacks, it's an essential feature. But for almost everyone else, it's an e ...more
In less than a month, WWDC, Apple's Worldwide Developers Conference, will reveal the company's plans for the upcoming iOS 18 and iPadOS 18 software updates. But we already know what accessibility features will be hitting iPhones and iPads later this year, and many of them will ...more