A development team in Silicon Valley is nearing early access release of a new hardware-independent augmented reality platform called Phantom AR. Compatible with Android and iOS-based headsets, as well as the Microsoft HoloLens and Meta 2, Phantom AR runs the entire augmented ...more
These days, if you walk through Best Buy, you will see an entire area designated to smart home technology. Thanks to the interest and growth of the Internet of Things (IoT), this exciting new technology has finally entered the mainstream. Appliances, thermostats, and even the ...more
If print is a dying media, you might as well destroy books in the most beautiful way possible. Guy Laramée is a Montreal-based interdisciplinary artist who turns old books, such as the Encyclopedia Brittanica, into intricately-carved works of art using mostly a sand blaster a ...more
You may remember my post from a couple weeks ago here on NextReality about the magical scaling ratios for typography from Dong Yoon Park, a Principal UX Designer at Microsoft, as well as developer of the Typography Insight app for Hololens. Well, his ideas have been incorporat ...more
The rumor train for Samsung's upcoming flagship phone is now running on full steam, and some of its cargo (or lack thereof) might not be warmly welcomed by many when it finally pulls into the station. Here are some notable potential omissions on the new Galaxy S8. Don't Miss ...more
Fighting fires has always been a dangerous and noble venture, even with the proliferation of aerial firefighting. But things are looking to get a lot safer for firefighters with the help of the Boeing and mixed reality. Boeing, now with 100 years of experience under its belt ...more
Metasploit is an extremely popular pentesting tool capable of enumeration, exploitation, and injecting shell code, and is a part of almost every hacking toolkit. So there's no way I could leave this out of our series on getting your Mac set up for hacking. Luckily for those o ...more
Copying files from a computer to your Android device has always been pretty straightforward—just connect the two devices with a USB cable, open your desktop file explorer, then move the files over. But what if you didn't need any wires at all? A new app from developer AppCube ...more
Since the dawn of time—well, that maybe a slight exaggeration, but let's roll with it—sly entrepreneurs have been swindling the general public with inferior products for the sake of saving a few cents. Nothing is sacred when it comes to saving money: caviar, cheese, or even ba ...more
Starting with Marshmallow, Android added a built-in theme engine called "Runtime Resource Overlay," or RRO. This theme engine was intended to be used only by smartphone manufacturers, not end-users, so unlike Cyanogen's CM Theme Engine, owners can't use it to change the look a ...more
We've explained the differences between mixed, virtual, and augmented reality through old-fashioned text and infographics, but in a rapidly-changing environment that leads to even more terms, it's best to think of all these realities in one simple way—as a continuum. Video: . ...more
When was the last time you restarted or shutdown your Mac? In the post-iPhone era, most devices are now powered on almost constantly. For better or for worse, the computing landscape has accommodated this "always on" trend, but you still need to periodically restart your devic ...more
Augmented and mixed reality experiences attempt to break us out of windowed computing experiences and allow us to place software anywhere in the room. But that software doesn't have to take a rectangular form—theoretically, the web doesn't have to restrict itself to a page in ...more
Our brains do a magnificent amount of work to process visual stimuli, but they aren't difficult to fool. Optical illusions can trick our minds into believing what we're seeing is real, even if it's not—and virtual and mixed reality technologies take advantage of this little lo ...more
Since the days of flip clocks, alarms have always had one function—make a bunch of annoying racket early in the morning to ensure that you wake up in time. And this simple MO has stayed in place while technology advances at a breakneck pace, almost in spite of the fact that to ...more
Summer is a sensational time for barbecues of all sorts, and sausages always seem to be in the limelight. From backyards to ball parks and picnic tables, crafting the best barbecued sausage is an art well worth mastering. Don't Miss: 14 Hacks You Need to Know for Grilling Se ...more
If you're standing in a foreign city, surrounded by signage in a language you don't understand, you won't suddenly be able to read it. But with a clever feature in Google's Translate app, your smartphone can. The app began as Word Lens, an augmented reality (AR) project by Qu ...more
While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows. Blue Coat is notor ...more
Peanut butter cookies may not have as big a fan base as their chocolate-chip counterparts, but their distinct flavor is loved by many a cookie enthusiast. Don't Miss: 10 Tips for Making Perfect Chocolate Chip Cookies Peanut butter cookies do have one giant advantage over cho ...more
I often read ebooks on my iPhone while I walk, but being glued to my screen is a good way to get run over or cursed at. To save my physical and social hide, I use this trick to get my iPhone to read ebooks and articles out loud, turning my whole text library into de facto audi ...more
When Apple wanted to bring their Notification Center to Mac OS X, I loved the idea. But after using it since its integration in Mountain Lion, it's been more annoying and distracting than anything. More and more apps incorporate notifications, so I'm constantly getting sound a ...more
Vacuum sealers keep food fresher longer by first removing the air from plastic food preservation bags and heat sealing the bag to keep air out. They have rapidly become a popular way to keep your frozen food fresh. They have one big problem, though. Vacuum sealers can get qui ...more
You're only as smart as your communication skills allow you to be, as other people will simply never know your inner genius if you can't effectively express yourself. Regardless of the medium—be it a Facebook post or even a simple text message—this fact remains true. When it ...more
This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to ...more
Dried fruit makes a great snack or salad topping, but after a while, they tend to become fossilized, rock-hard versions of their former selves. At this point, most folks probably just toss them out, as they're unpleasant to chew on when eaten raw and even more unpleasant to ea ...more
We're so used to seeing things in particular ways that anything different just doesn't make sense to our brains. Culturally, we like to read things from left to right, and from top to bottom. Change that and our brains struggle to adjust. On social media sites like Facebook a ...more
Note: a bug was found in the Insertion Sort implementations. The bug was corrected in each language. Please refer to the pastebin links for the most up-to-date versions of the sample code. Any screenshots may be behind. More about the bug can be found here. Hello World! Today ...more
Live wallpapers have dipped in popularity lately, with many users favoring a single, static image as their home screen background. But this is generally due to still photos offering a more sophisticated look, while traditional live wallpapers can sometimes seem a little less a ...more
Hey guys I am starting this Series because I thought there was a lack of post about Hacking from Android. In This series I will tell you about That your Android can really be used for hacking just like your other systems. So in the first of the many posts I will be telling ho ...more
LG got in on the action at Mobile World Congress in Barcelona by unveiling its new G5 handset on Sunday, February 21st. It will be the first publicly available modular smartphone by a top tech giant. Video: . The Magic Slot The highlight of the G5 is undoubtedly the "Magic Sl ...more
For the past couple of years, random internet dwellers have embarked on an ambitious quest to see just how useless a box can be in hopes of earning sweet, sweet internet points. Welcome to the world of useless machines. On the surface, these machines are fun little contraptio ...more
It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc. Kismet Although there are many tools that can grab and capture network pa ...more
T-Mobile's "Binge On" service for streaming videos has received mixed reactions so far. On one hand, it gives any T-Mobile subscriber unlimited access to popular streaming video services like Netflix and Hulu without having to worry about going over their monthly data cap. On ...more
If Android is all about options, then iOS is all about new features. Every year without fail, Apple announces a cool software component that brings something new to the table, and this year was no different. The headlining feature to go along with the iPhone 6s is called "Liv ...more
Hi guys, this is going to be kinda like a follow up to my previous post on hacking facebook with the remote keylogger. If you haven't seen that post I suggest you do. So like you can click here. Anyway let's move on. Even though people are the weakest form of security, some o ...more
We're near the end of a productive year for Apple, one that introduced a new Apple TV, the iPad Mini 4 (in conjunction with the Apple Pen), the iPad Pro, and the iPhone 6S and 6S Plus, as well as iOS 9. Now, the second major update to iOS 9—version 9.2—has just been released t ...more
Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to ...more
Screenshots are an indispensable tool when it comes to relaying information about what's currently showing on your monitor. Whether you need help troubleshooting an issue or you just want to save and share a protected image, screenshots are often your best bet. Don't Miss: 45 ...more
Microsoft's Windows 10 has proven to be a solid release by Microsoft, with faster adoption rates than its predecessor builds. The seamless integration of cloud services and tweaks both major and minor make using Windows easier than ever now. And it's almost enough to forget yo ...more
Greetings null-bytians. Firstly, I would like to apologize for the no images thing. I guess I can't upload them. If you have watched the documentary titled "In the Realm of the Hackers", the one about two Australian hackers, Electron and Phoenix, you will know that it was a g ...more
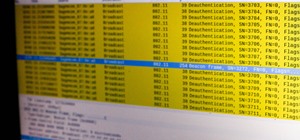
Greetings null-bytians. Say you have been able to penetrate your neighbour's AP, and of course you had spoofed your MAC address. Now you go on and test to see with excitement if the password really works and the MAC is still spoofed. You login successfully and you browse the w ...more
Frosting, for many, is the best part of the cake. There's not much to dislike about it, after all—there's a type of frosting for every person. Whipped frostings for those who like it light, dense buttercream for indulgent sugar fans, cream cheese frosting for the tangy crowd.. ...more
NANDroid backups are one of the best reasons to root your Android device and install a custom recovery. They're essentially a snapshot of your phone's entire operating system and all installed apps, so if you ever screw something up when installing a flashable ZIP or custom RO ...more
For reasons unknown, Microsoft decided to change the way the Guest account feature in the new Windows 10 operating system works. In previous versions, the Guest account feature allowed you to set up a limited account for other users so they don't have access to your important ...more
Piracy, it can be argued, is the scourge of the internet. But when it comes to music, sometimes it's best to give a listen to a track or album before deciding to spend your hard-earned money on fully supporting it. Unfortunately, there are few good ways to do this without exp ...more
In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to ...more
OneDrive, formerly known as SkyDrive, is a free online storage solution developed by Microsoft. If you're a fan of using cloud-based storage systems, then OneDrive offers you plenty of benefits. It's also heavily integrated into Windows 10, including the new File Explorer, in ...more
Modern versions of Windows have revamped the lock screen to make it a lot more useful. If you're coming from Windows 7 and older versions of the OS, this lock screen is both new and useful (though you can turn it off if you just don't want it). Don't Miss: Everything You Need ...more
If you have some photos, videos, and documents that you want to keep completely hidden and encrypted on your Android device, Andrognito is the app you need. We showcased this app in the past, but since then, CODEX has rebuilt it from the ground up with new and improved feature ...more
If you've updated your iPhone 4S or iPad 2 to a version of iOS 7, iOS 8, or even iOS 9, you've probably noticed that its performance is a little more sluggish than it was back when it had iOS 6 and lower on it. Now, thanks to a tutorial from tihmstar, you can downgrade the op ...more
When setting up a new Mac, there can be a bunch of settings that need to be changed in order to get the system running the way you like it. That usually involves going through tons of System Preferences panes and app settings—but it doesn't have to. If you'd rather get everyt ...more
Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring.... How It Works MITMf (if you don't already know) is a man in the middle attack framwork. MITMf literally stands fo ...more
Like most food lovers, I adore sushi. And like anyone who is a living, breathing human being, I'm a pretty big fan of sriracha sauce. I guess you can see where this is going. Yes, sriracha sushi, which I've decided is my new favorite thing. I discovered how to make sriracha s ...more
Sometimes our information important. So important that we have to encode it to keep it away from criminals. What better way to encode information than to make our own encoder with Python? In this tutorial, we will cover the basics of cryptography in hopes to make a "gibberish ...more
Besides obvious features like a touchscreen and biometric sensors, the modern smartphone comes with an array of state-of-the-art hardware in the form of various sensors that help your device sense the environment around it. And if you have a Samsung handset, chances are, you h ...more
At its core, grilling is the simplest form of cooking. You create extreme heat, you put a piece of food on top of the heat, and then you sit back and watch the magic happen. Yet despite the inherent simplicity in grilling, there are a million ways to make it more complex, more ...more
Carriers like to distinguish their Android phones from the competition by making small changes to the interface here and there. This practice is so common that Android now has a built-in system for managing these small tweaks. A series of XML files known as CSC (customer soft ...more
Hi there, Crackers, Welcome to my 7th post (Part-1), this tutorial will explain about the basics of Batch Scripting. Why Batch? Batch is a really easy and interesting scripting language, it is used for malicious purposes, i.e. how can you exploit the victim's PC/life, furthe ...more
Both bObsweep Standard and Pethair models have two bumper sensors inside their covers. Whenever Bob runs into an obstacle, the sensors tell Bob to back away. If bObsweep does not change direction after bumping into something, the following guide may help you fix this. Video: ...more
Android Debug Bridge (or ADB for short) serves as a remote terminal interface for executing shell commands on any Android device. Put simply, ADB lets you send commands from your computer to your phone or tablet, some of which would require root access if they were performed o ...more