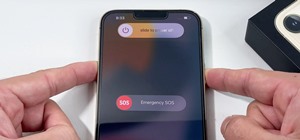
Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you alre ...more
To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purch ...more
MoviePass was once the best subscription service on the market for getting cheap movie tickets. For the price and the number of films you could see and save money on, it was unbeatable, but recent changes to the service have made it less enticing. While it still works well for ...more
After poor sales of the Pixel 3 and Pixel 3 XL, Google needs to reinvigorate its Pixel lineup, devices it's been pushing heavily over the last couple years. On May 7, Google had the eyes and ears of the technology industry at its Google I/O keynote, making it the perfect time ...more
Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to snif ...more
The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each ty ...more
People say that money makes the world go 'round. And it's no different in the world of augmented reality. If there are any doubts about the future of the AR industry, it doesn't seem like many venture capitalists or corporate investors share those doubts. According to Digi-Ca ...more
Apple's latest mobile operating system for iPhones, iOS 12, was released to everyone Monday, Sept. 17, and it's the same exact build that developers and public beta testers received as the "golden master" on Sept. 12, the day of Apple's 2018 special event. Install it to start ...more
In a surprising twist of expectation management, Magic Leap managed to not only ship but deliver the Magic Leap One I ordered on Wednesday by 4 p.m. PT on the same day. After spending about an hour with the headset running through set up and poking around its UI and a couple ...more
| Updated Aug. 22, 2019 with new phones. When will my phone get Android Pie? For the first time since Android's inception, this question shouldn't have an answer that lets you down. That's because Android Oreo introduced Project Treble, a new low-level arrangement that makes ...more
One of the most exciting additions to iOS 12 for iPhones is called Shortcuts, a tool integrated with Siri to help you get things done faster. While there are a few recommended shortcuts available to you in Siri's settings in iOS 12, the Shortcuts app brings the functionality o ...more
Ever since 3D Touch's introduction in iOS 9 for the iPhone 6S and 6S Plus, a little-known trick for moving the cursor around and selecting text was built into Apple's stock keyboard. On iOS 12 or later, it works for all iPhone models with or without 3D Touch or Haptic Touch ba ...more
Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, w ...more
In our last ARKit tutorial, we learned how to measure the sizes of horizontal planes. It was a helpful entryway into the arena of determining spatial relationships with real world spaces versus virtual objects and experiences. This time around, we'll dive into a slightly diff ...more
The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company ...more
Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attack ...more
TouchWiz might not be the Android skin of choice for hardcore aficionados, but the Galaxy's OS still has a ton of great features up its sleeve that help provide one of the most enjoyable smartphone experiences out there. Many of these are relatively hidden and overlooked featu ...more
Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a b ...more
After testing a series of Android 8.0 builds, Essential hit the reset button and jumped to Android 8.1 Oreo. The beta program didn't last long, as Essential has now released the official 8.1 update to the masses. The features from the 8.0 betas are all still there, plus a few ...more
While iOS 11.3 doesn't have as many new features as iOS 11.2, there's still a lot to love about Apple's latest update for iPad, iPhone, and iPod touch, even if some of the best features we were expecting didn't make the cut. Apple released the iOS 11.3 beta on Jan. 24, and ju ...more
There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distributi ...more
The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems ...more
Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopp ...more
Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutoria ...more
If you've never used the Home button shortcuts on your iPhone before, you've been missing out. And no, I'm not talking about opening up Siri. By clicking the Home button three times, you could quickly pull up tools such as Magnifier, VoiceOver, Zoom, and Assistive Touch, but t ...more
Kylo Ren, conflicted villain of the new Star Wars trilogy, will surely be a major presence again this Halloween, with The Last Jedi fast approaching. His costume, all black and layered, complete with dark-side helmet and crossguard lightsaber, seems quite perfect for Oct. 31 — ...more
Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeO ...more
Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and ho ...more
PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's comput ...more
Word games fit perfectly with the on-the-go nature of mobile gaming. They're easy to pick up whenever you feel like exercising your brain, but they're also fairly easy to put down when you need to get back to the real world. The main draw of word games is that they're great f ...more
Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with. Wardriving has been around since the '90s and combines GPS data and Wi-Fi signal data to create accurate, in-depth maps of any nearby Wi-Fi networks ...more
In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hea ...more
WWDC 2017 is right around the corner, where Apple is expected to reveal iOS 11, the newest version of their mobile operating system. There have been many rumors floating around about what iOS 11 will have in store for us, but not all of those features will end up in the final ...more
Apple's default browser for iOS, Safari, has a ton of useful features, and there's so many that it's impossible to know everything you can do to browse the web more efficiently. One you may not know about brings the Command + F keyboard shortcut right to your mobile browser so ...more
Throughout this NR50 series, we have talked about the incredible growth the augmented and mixed reality space has seen in the last year. More devices, software, developers, and use-cases seem to arrive daily. For this growth to have occurred, it took the work of many people, f ...more
In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux. With each Pi more powerful and cheaper than the last, the addition of the Pi Zero in 2015 too ...more
Right now is that magical time of year when the general public decides to embrace their inner fattie and get baking in the kitchen. Hello, pies and cakes and cookies and everything carbs. Goodbye, diets—see you in the next year, when you cripple us with unbridled guilt and lon ...more
Codenamed "Nougat" after the sugary stuff that fills your Snickers bar, Android 7.0 is living up to its name with tons of sweet features. There's almost too many changes over Marshmallow to cover in one go, with new functionality ranging from a revamped Doze Mode for battery s ...more
Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-d ...more
Windows 10 is officially here, and frankly, there's a ton of new features in Microsoft's latest operating system. From the return of the Start menu to the new Edge browser, Windows 10 can take some getting used to. Luckily, we've done a lot of the leg work for you, and what f ...more
There is much to be learned about Apple Music and the revamped Music application introduced in iOS 8.4. Throwing their hat into an already competitive field with other companies like Spotify, Tidal, or Rdio, this is a bold move on Apple's part. So, before you consider signing ...more
NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!! Hello Guys, Welcome to my first tutorial and in this tutorial we are basically going to create a port scanner in python ( I guess without external librarie ...more
While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos. Mac OS X does have FileVault as a good security option, which uses XTS-AES 128- ...more
Apple Pay has been available to use in stores, as well as in select apps and websites, ever since its first appearance in iOS 8.1. Now, with iOS 12, there are currently 13 different iPhone models that support Apple Pay functionality without the use of an Apple Watch, and the l ...more
Telemarketers can be as terrifying as a villain from a horror film. Your phone rings with an unknown 800 number, and you immediately fill with a sense of dread. There's no way to get them to stop calling; you imagine the number appearing on your phone at all hours of the day a ...more
It may sound irrational, but I bet a lot of you actually avoid doing any work at work—but not on purpose. You might be simply struggling with motivation, or you might just be overdosing on the caffeine. Whatever the issue, getting focused takes lots of time and effort. But we ...more
As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of ...more
Over the past several weeks, I’ve had the pleasure of test driving Samsung’s next big thing, the Galaxy S4. After putting the GS4 through its paces, I have a clear picture of what this device is capable of. I’ve covered the features of the device before, and now I’ll tell you ...more
Notch loves Halloween. He must, because he keeps putting scarier and scarier things into Minecraft around Halloween time! Today, Minecraft 1.4.2 was released, and it's a doozy. Versions 1.4 and 1.4.1 were actually skipped entirely, as lots of bug-fixes were patched between th ...more
Recording phone calls has always been tricky due to legal, ethical, and technical considerations. With iOS 18.1, Apple brings your iPhone a native call recording feature that simplifies this process while addressing privacy concerns. There are a few things to know about call ...more
The devices in the new iPhone 16 series lineup have one feature no other iPhone models have: a physical Camera Control button. If you use your iPhone to take photos or record videos, the Camera Control speeds up the process and gives you immediate control over adjusting settin ...more
If you're an AirPods user, things are a lot better with iOS 18 and iPadOS 18. If you're not, it may finally be time to grab yourself a set of AirPods, especially if you're into privacy and gaming. Apple's iOS 17 and iPadOS 17 gave AirPods new features like Adaptive Audio, Con ...more
Speech-to-text technology can be seen on your iPhone in various places, from the Dictation tool to Apple's new behind-the-scenes, auto-created transcripts for podcast episodes. Your iPhone also has some pretty impressive text-to-speech capabilities. With them, your iPhone can ...more
Whether it's everybody or just a specific contact you can't hear during audio and video calls when wearing headphones, your iPhone has hidden, little-known tools to help you catch every word they say in the conversation. Even if you can normally hear everyone during calls, cus ...more
Collaboration is available in many different Apple apps, from Notes and Reminders to Photos, Freeform, and even Files. Now you can add to the list Apple Music, which will let you collaborate on playlists with friends. While it wasn't ready for Apple's major software releases ...more
A new feature in Apple's latest big iPhone software update lets you personalize how you appear on other people's incoming call screens and even customize individual contacts on your own incoming call screen if they don't have a preferred style to show you. It's called Contact ...more
Thanks to rapid advancements in the field, generative AI can do some amazing things already, from generating text, images, and video with just a prompt to automating tasks and developing new products and services. Now, artificial intelligence can even help you craft emails dir ...more
Whenever you're on a FaceTime call, you can use SharePlay on your iPhone or iPad to screen share, watch TV or movies together, work out with each other, and even listen to the same music at the same time. SharePlay also recently received a new skill that turns FaceTime into a ...more
The screenshot tool on your iPhone can come in handy in various ways, but it may be even more helpful than you realize. So if you thought you knew everything there was to know about your iPhone's screenshot tool, it's time to put your knowledge to the test. Many of these hidd ...more
Despite its name, the Frequently Used section on your iPhone's emoji keyboard features both frequently and recently used emoji, and it may contain emoji you've never even touched. If you want to remove all of those recommendations, there's an easy way to reset what you in Freq ...more