It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time. Both Facebook and Gmail ...more
Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV so ...more
Researchers at the University of California, Riverside and the University of Michigan announced recently that they have developed a hack that works 92% of the time on Google's Gmail system on Android, as well as with the H&R Block app. In addition, this hack worked 86% of the ...more
When you sign up with Gmail, Google gives you both an "@gmail.com" address and an "@googlemail.com" address. You can take advantage of this fact to reduce the amount of spam you receive. And this video tutorial from the people at CNET TV will show you how. Regain control of yo ...more
With this video tutorial, you'll learn how to hack demo versions of applications such that they'll run indefinitely. You'll just need to modify the date and time on your computer. Learn how to use trials of programs without them ever expiring instead of buying the real thing w ...more
Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a smal ...more
Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there ...more
Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look ...more
Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms. First, I covered embedding a listener in ...more
Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero- ...more
Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to c ...more
Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a mal ...more
Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have ...more
Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, a ...more
Welcome back, my hacker wannabees! Since nearly all hacker tools and platforms are developed in the Linux/Unix operating systems, this series of tutorials are for those of you who want to be hackers, but are unfamiliar with Linux. We've looked at numerous basic commands in th ...more
These days, it seems new phones get announced every other week. We've grown accustomed to glossing over the specs, looking at some press renders, then moving on to check out the next phone. If you had done this in September 2008, you might have overlooked what would become one ...more
Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use ...more
Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial ...more
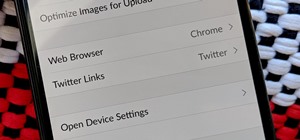
Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long ...more
This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this. Thank You: First thank you for wanting to become a hacker, it is not an easy path. Becoming a hacker, at least in the way that I s ...more
Google just bought a huge chunk of HTC for $1.1 billion. They're bringing in around 2,000 employees, mostly from the hardware division, and these folks will presumably work under hardware chief Rick Osterloh. There's a massive patent portfolio involved, too, so stop me if you' ...more
It wasn't long ago Apple released iOS 13.2 to the masses. The second major update to iOS 13 included 22 new features and changes that added a significant layer of depth to an already feature-filled experience. Apple isn't ready to stop the fun, however, as iOS 13.3, released D ...more
Shatter glass with your mind!… Um, no… with speakers! This little video shows you how to shatter wine glasses with your own speakers. Yep, those normal, everyday home speakers that you have can break a wine glass just like a jackhammer. You will need some audio editing softwa ...more
What if you could have a secret hard drive connected to your computer that only you could activate? You can! Samimy shows you how to hack a remote controlled toy car and make a super secret hard disk drive in your computer, accessed via a secret activation key. This hidden eme ...more
RSBot / powerbot is a great piece of software for hacking Runescape and making it more fun, but it can be difficult to use sometimes. If you're having loading issues with version 2.16+, watch this video for a fast guide to fixing it..
Take a look at this instructional video and learn how to hack into your iPod's firmware on a Mac. In order to hack into the 5.5g iPod's firmware, you need to download the Alterpod, a firmware editing software. With this program, you'll be able to download themes onto your iPod ...more
Enjoying the many benefits of Facebook Places? But what if you want to check in somewhere you're not? Your smartphone can automatically detect your geographical location, preventing you from just checking in just anywhere, but like all technology… it's a long way from perfect, ...more
Oh how we love open source software. If it wasn't for Open Office, we never would have been able to write that seven-page English paper while on our friend's Microsoft Office-lacking laptop during an impromptu road trip to Mexico. And Ubuntu, an open source secure operating sy ...more
Watch this instructional video to learn how to use Google Hacks. Google Hacks is a collection of software that explores Google's search function. Hacks is meant in this definition. "A Hack is a modification of a program or device to give the user access to features otherwise w ...more
So, a lot of people seem to be having trouble rooting their Motorola Droid X smartphone from Verizon Wireless using ADB (Android Debug Bridge). Well, there is an alternative for those having problems with the ADB version. You will need to have a Wi-Fi or Bluetooth widget handy ...more
Trucha Bug Restorer is a powerful piece of homebrew software that you can use on your Wii to make sure that it is formatted properly in order to play burned games and use other hacks. This video will show you how to use it to set up an installation of cIOS on your Wii, which i ...more
The PSP has never had the software support that it needed to be a really commercially successful system. Since Sony blew it already, you may as well go the extra mile to make this expensive little thing you bought more useful right? This video will teach you how to hack a PSP ...more
Windows 7 has hit the streets. If you've got Windows Vista or XP, and you are preparing to do the switchover to WIndows 7, check out this video! This video covers everything you need to know before going to Windows 7, from what files to back-up, software that will help you mo ...more
Social Profile Change the privacy settings on your social profile (Facebook, MySpace, Friendster, Twitter, etc.) so that the following information can't be found by a random person who you didn't accept you as a friend: Birthdate E-mail address Hometown Pictures A hacker ca ...more
If you'd like to have access to all your files at home without the hassle of spending money on expensive file hosting services or installing foreign software on your computer that could potentially harm it? Well Google has the answer for you, taking over the world one more com ...more
Before, eReaders were only used to read eBooks. Not anymore. As tablet computers become more and more advanced, eReaders like Amazon's Kindle, Sony's Reader and Barnes & Noble's Nook are forced to expand their capabilities beyond the basic bibliophilic needs. And the first to ...more
Read This Must Need flash player 9!! Hex code for Money: B045110FF2AC5D89 Hex code for Paw Point: 840FFF85C12A0FF2 Web site for the code generating: http://patiniox.blogspot.com/ download Mozilla FireFox 3 http://www.mozilla.com/firefox/ Cheat Engine 5.5 http://www.cheat ...more
With FarmVille being one of the hottest Facebook games on the market, it's no wonder it's the primary target for scams and virus downloads. Anyone playing FarmVille is at risk, but the primary targets are those looking to improve their gameplay and build their farms and neighb ...more
So you've got a Blackberry 8830 or 9530 Storm, but you are not down for the default service provider that comes with the phone. Using this simple software hack, unlock the your Verizon phone to work with Cricket, Metro PCS, or any other CDMA provider.
While the PlayStation 3 is great at playing BluRay discs, if you want to play back downloaded videos, it can prove to be quite problematic. Use this software hack to unlock the Play Station 3 for video playback, whether it be from a hard drive or streamed off the internet.
Want to be the master of your domain? Make zombies and other monsters spawn where you want them. This tutorial shows you how to use the free software NTB edit to hack MineCraft and alter the spawn points for monsters.
You can use the free software program Cheat Engine to hack nearly any game, whether online or off, to alter your scores, inventory and experience points. Always make sure you are using the most current and up to date version of Cheat Engine! Part 1 of 2 - How to Change your sc ...more
This music production software tutorial describes a hack to allow you to trigger an instrument or effect when you RELEASE a key in Reason 3 or 4. This is useful for guitar strums, Hi-hats, mutes or delays, or vinyl scratch effects. With this trigger trick you can create back b ...more
Take a look at this instructional video and learn how to load virtual console games onto your Nintendo Wii. You'll need the Twilight Hack and an SD card for this process. The Twilight hack allows you to run unofficial software through the SD (Secure Digital) card inserted into ...more
As advanced gaming systems continue to evolve, older classics like the Nintendo Entertainment System (NES) are one step closer to extinction. They're rotting in the basements of gamers. They're gathering dust at the local pawn shop. Or worse... being thrown out in the trash li ...more
How to hack a network by sniffing passwords with Ettercap software.
If you're trying to hack someone's wifi, a useful bit of software you may want to try is called Wireshark. Wireshark is a wifi packet sniffer, which is an essential step in actually breaking into someone's wireless system. Of course, this is illegal, so make sure you're only d ...more
Description: Admit it, having thousands of valid email Ids give you the power to do anything! Such as adding thousands of friends to your Facebook, MySpace, Twitter, etc profiles or promoting your article or blog in just a single click and much more! But how do we do it? I se ...more
Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords. Visit us at bleedingedgesecurit ...more
Learn how to hack your 1.1.2 and 1.1.3 iPhone with Ziphone (zibri) software for Mac or Windows. No technical skills required!
Take a look at this instructional video and learn how to install the Twilight hack for you Wii. The twilight hack is an exploit that reads a elf file off the root of your secure digital (SD) card. To start up this hack, you'll need to load the Zelda: Twilight Princess game bef ...more
Are you a ... Windows Developer? Interested in ... testing the vulnerabilities inherent in your own operating system? If so, you're in luck. This video tutorial demonstrates a simple hack that will allow you to remove the Windows Genuine Advantage Validation software. For step ...more
What's cuter than a puppy? Not much, especially when you omit all the peeing, barking and furniture chewing, as Remedie Studio did with this sweet time-lapse homage to their beloved pup. Below, watch Dunder the German Shepherd grow from 8 weeks old to 1 year in 40 seconds. Ins ...more
Iowa firefighter Pete Lilja has modded the software of a Canon powershot to record images of Earth, from as high as 85,000 feet! Lilja's hack requires the following: 1 basic point-and-shoot consumer camera attach camera to a GPS transmitter (+ a phone number just in case the ...more
Got 3D glasses leftover from the Superbowl? Time to break them out! You will need cheap 3D glasses from television promotions or you can grab them off eBay for this demonstration. Or you can simply make your own 3D glasses red and blue or yellow and blue cellophane. NOTE: Get ...more
In this hacker's how-to, you'll learn how to softmod your old Playstation 2 to enable you to run third party software and how to use CogSwapLoader and HDLoader to backup your PS2 games and play them either from a burned DVD or off your hard drive. This will let you hack the PS ...more
Need the newest copy of professorial design and photography software but cannot afford it? Find out how to crack Adobe photoshop without having to use a serial number.
Make your own 3D movie with this easy camera hack: record with two cameras simultaneously. Next, use video software to overlap the images, making it viewable through 3D glasses. Very clever (and cheap) concept by Ron and AmyJo Proctor. Check out their site for more details. T ...more
If you're struggling to get your PSP hacked after downloading the required software (ChickHEN and CFW), check out this video for a helpful walkthrough on how to get things started. This video shows you how to install ChickHEN R2 and boot Custom Firmware 3.60, allowing you to a ...more
This past Tuesday, Amazon pushed a big software update to Kindle users the world over. While the update introduces a host of great new features—secondary page numbers that allow readers to reference real-world editions, for example—, it also takes something away. What? Well, ...more