To really personalize your HTC 10, you'll need to be rooted — but that can't happen unless you unlock your bootloader. Thankfully, HTC has made it relatively easy to unlock the bootloader on their 2016 flagship. Unlocking your bootloader will make it a breeze to install TWRP, ...more
The next-generation Audi A8 to launch in July is expected to be the world's first Level 3-capable production car to go on sale in retail channels. But aside from demo drives scheduled for journalists and analysts Audi plans to organize this month, the model's advanced driving ...more
Google Play Services has been near the top of every Android user's list of battery-sucking apps for years now. It's a core system app, so you'd expect some battery drain, but for many folks, it runs rampant. This is partly due to the fact that Google has exempted Play Service ...more
Earlier this year, Google rolled out the first developer preview build of Android O. The new version added tons of cool features, but the downside was the fact that you needed to use Fastboot to manually install the update if you wanted to try it out. Thankfully, things just g ...more
Deep down inside, Kindle Fires are actually Android tablets — the only trouble is, Amazon has layered so much of a skin on top of it all that you can't normally use Android's main app store, the Google Play Store. The Amazon Appstore, which comes bundled with Kindle Fire devic ...more
Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all ve ...more
The Snapdragon 820 and 821 were met with praise last year, receiving almost no complaints compared to their overheating predecessor, the Snapdragon 810. But now, all eyes are on Qualcomm to see what goodies they have in store for us this year, as their new SoC, the Snapdragon ...more
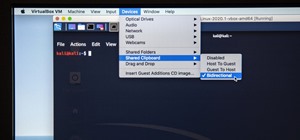
At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher. Previously: How to Create a ...more
Dutch filmmaker Anthony Van der Meer published his 2015 thesis short from Willem de Kooning Academy in South Holland online in December 2016. It's a brilliant piece of work that managed to be touching, alarming, and informative at the same time. His documentary, which already ...more
Looking past the obvious visual similarities between the iPhone 7 and Google's new Pixel phones, there are several indications that the search giant had Apple in its sights as they released their latest flagships. For once, this isn't an Android phone we're talking about, it's ...more
There's a new operating system on the horizon, and this one's so big that it may actually live up to its galactic moniker. Andromeda, a merging of Android and Chrome OS, has the potential to bring Google to the ubiquitous status that Microsoft's Windows enjoyed in the '80s and ...more
The new iOS 10 won't be released to the public until September 13 via an OTA update, but the Gold Master edition is available right now. Essentially, it's the same version that Apple will release on the 13th, but only for developers so they can get their apps up to snuff befor ...more
When the Samsung Galaxy S7 and S7 Edge came to market in 2016, they were universally praised as being the pinnacle of Android smartphone design, even topping Consumer Reports' smartphone ratings. Why? Well, for once, we finally had a smartphone, or in this case, a pair of sma ...more
Whether you're performing a factory reset to get your device ready for sale or trade-in, or you're wiping your device in the hopes of fixing software issues, there's a right way and a wrong way to go about it. Sure, it seems like a simple task on the surface, but if you're not ...more
On the list of problems with Android, manufacturer tinkering ranks near the top. Slow or nonexistent updates, poor performance, excessive bloatware apps—all of these things can be attributed to manufacturer skins like TouchWiz or Sense, and none of them are issues with unmodif ...more
Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems ...more
CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer. Head of Security: Well let me tell you something my good friend. Many companies we have today they are still getting attacked from hackers ...more
Emails sent from an iPhone, by default, are signed "Sent from my iPhone," which almost seems like a disclaimer in case the email has spelling or formatting errors. If your goal is to look professional while corresponding with coworkers or potential employers, then you're bette ...more
Cheap Chinese knockoffs have been around for ages, but recently, skyrocketing demand has led to a massive influx of counterfeit smartphones. Sellers on Craigslist seem to have no trouble getting ahold of these fake devices, then passing them off as the real deal and turning a ...more
Practically every smartphone comes with a built-in camera app, but these apps are generally created by the device's manufacturer. And let's face it, manufacturers are hardware companies first and foremost, so they don't always produce the best software. Luckily, though, Andro ...more
Smartphones have otherworldly specs these days, so it's relatively uncommon that you hear someone complaining about display resolution, build quality, or general speed and performance. At best, these are secondary concerns, with the number 1 issue almost unilaterally being bat ...more
FBI has taken down a notorious hacking forum called "darkode" where cyber criminals bought, sold and traded hacked databases, stolen bank accounts, and malicious software that steal information from other computer systems and helped each other to infiltrate other computers. Th ...more
When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android ...more
With all the stress that goes into booking flights and lodging, packing (and not forgetting) everything you'll need, finding pet sitters, and everything else that goes with a trip overseas, there's the added stress of staying connected while abroad. Don't Miss: 11 Tips to Mak ...more
If your iPhone is rebooting or your Messages app is constantly crashing, you might be the victim of an iOS exploit or just a buggy software update. While one problem sounds worse than the other, they both can get annoying real quick when you can't send any messages or even rea ...more
Welcome back, my tenderfoot hackers! Have you ever wondered where the physical location of an IP address is? Maybe you want to know if that proxy server you are using is actually out of your local legal jurisdiction. Or, maybe you have the IP address of someone you are corres ...more
I picked up my Galaxy S6 Edge on release day and have loved it ever since. Did I spend an extra hundred bucks for the mostly-aesthetic Edge display? Yup! Did I have buyer's remorse about my frivolous spending? Not even a little. But lo and behold, I found myself at Best Buy t ...more
Ever feel like you're receiving notifications way too late on your Android device? Many Android apps use Google's Cloud Messaging service to send and receive notifications, including Hangouts, Gmail, Pushbullet, Facebook, and even WhatsApp to an extent. To ensure that your ph ...more
Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits. As many of you know, soon after an exploit is found in the wild, software developers begin to work on ...more
Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all o ...more
With Safestrap bringing custom recovery functionality to the AT&T and Verizon Wireless variants of the Samsung Galaxy S5, it's high time we covered this process for all other versions of the GS5. If you're not familiar with the term "custom recovery", it's a piece of software ...more
Welcome back, my novice hackers! In a recent tutorial, I showed you how to use shikata_ga_nai to change the signature of a payload to evade detection by security devices (firewalls, IDS, etc.) and AV software. Shikata_ga_nai is an encoding module in Metasploit that XORs the ...more
Welcome back, my hacker novitiates! Recently, I demonstrated a hack where you could redirect traffic intended for one site, such as bankofamerica.com, to your fake website. Of course, to really make this work, you would need to make a replica of the site you were spoofing, or ...more
Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers). Flash ...more
Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look ...more
The new Windows 8 is set to launch on October 26th, and developers and early adopters are still getting used to the new interface. Windows 8 borrows a lot of its functionality and look from the touchscreen-friendly Windows phones. As with Windows phones, Windows 8 uses the now ...more
I recently picked up a Pixel Slate when Google had a deal going on. I'd been in the market for an Android tablet since the Nexus 7, and this was the closest thing to it. Unfortunately, I soon learned Chrome OS and Android aren't as integrated as I had hoped. What do you do if ...more
As paper forms become a thing of the past, it's becoming commonplace to fill out contracts, rental agreements, waiver release forms, and non-disclosure agreements online. You can easily fill out forms on your laptop, but how can you best do this using your iPhone or Android de ...more
Though many were hoping for it, a notification indicator around the Galaxy S10's front camera punch hole never came to fruition. Since then, we've been finding other uses for the camera cutout, from turning it into a circular battery meter to using creative wallpapers. Thankfu ...more
Great news if you're looking to upgrade to either the S10e, S10, or S10+. Samsung has a trade-in program that's offering potentially massive discounts of up to $550 if you preorder one of their flagships right now — but only for certain phones. You'll need to act quickly if y ...more
Windows 10 and macOS have poor reputations when it comes to customer privacy and user policies. Our hacking Windows 10 and hacking macOS articles might make it seem like a reasonably secure operating system doesn't exist. But I'm here to tell you that there is a viable alterna ...more
Android lets you sync your contacts across devices. The OS will use not only contacts saved on your phone, but also your Gmail. This choice can lead to a contacts list populated with entries that don't have a phone number, which can quickly add up. To mitigate this problem, th ...more
Buying an unlocked phone is usually the correct move. By doing so, you bypass a lot of bloat that carriers put on your phone, and you can also use that phone with another carrier should you decide to switch to a new one. However, a lot of carriers won't give unlocked devices a ...more
IFTTT is an application that allows you to automate certain tasks on your iPhone or Android. It can communicate with a myriad of apps and services on your phone by creating applets that perform actions automatically — actions you'd normally have to do manually. Finding those a ...more
Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about. Sometimes, if yo ...more
Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!) In several episodes, Elliot was seen sending ...more
This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/ In this post we will explore more about finding hacked accounts online, w ...more
Apple includes a lot of helpful features for iCloud email addresses, but one of its best-kept secrets will give you total control over organizing your inbox like a pro. So, what's the big secret? Subaddressing, also known as plus addressing, tagged addressing, email address ...more
People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want ...more
Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensiv ...more
Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem. ...more
Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as ...more
An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manuf ...more
While the Galaxy S10 is a beautiful phone, its software isn't for everyone. One UI makes huge strides toward undoing the mess known as TouchWiz, but for purists, it's still not quite on par with stock Android. Fortunately, the beauty of Android is you can change this with a fe ...more
The newly-announced Moto G7 Play offers some of the same upgrades as its sibling, the Moto G7, but at a much lower price. The upgrades are pretty significant when compared to last year's Moto G6 Play, taking this phone from the "only if you're on a strict budget" category into ...more
Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all beca ...more
When you unlock the bootloader on your Essential PH-1, you open your device to a host of new possible tweaks. One popular modification is a custom kernel, which can not only speed up your phone, but give you new features that wouldn't be possible otherwise. The kernel control ...more
Apple may pride itself on its commitment to user privacy and security, but it isn't invulnerable. We now know there is a bug in the latest version of iOS 12 and iOS 12.1 beta that allows those in the know to bypass your passcode and access contacts and photos. This applies to ...more
Although the Essential PH-1 got off to a rocky start, thanks to steady updates, it has slowly become one of the best Android phones to come out in recent years. For $499, the Essential Phone is a cheaper Pixel, receiving updates almost as soon as the Pixel lineup does. What's ...more
If you haven't heard, another big OEM has decided to drop the headphone jack. OnePlus, the hero of the people, has just announced that the OnePlus 6T will not have the popular port. With this decision, audiophiles and others are limited to just three big-name options. Since n ...more