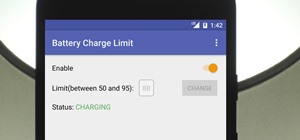
Need a unique gift idea for the techy person in your life? Look no further than that phone they always have in their hand. There are plenty of great accessories, apps, subscriptions, and other smartphone-related goodies that will improve their quality of life, and thoughtful g ...more
Apple has revolutionized how we write with the introduction of its new Writing Tools, powered by Apple Intelligence. In beta on iPhone, iPad, and Mac, these tools allow you to select text and use intelligent features to summarize, proofread, or rewrite it until the tone and wo ...more
Samsung has a cool security feature built into One UI that has an interesting side effect, one that lets you have two separate copies of any Android app on your Galaxy phone. And that's not the only integrated Samsung tool for cloning apps. Some mobile apps have built-in acco ...more
Apple's iOS 13 has been available for beta testing since June, and the stable release pushed out to everyone on Thursday, Sept. 19. To help you make the most out of iOS 13 for iPhone, we've rounded up everything you'll want to know, whether a colossal feature, small settings c ...more
Prank Calls, Masked NumbersWho is calling your phone or your child's? Pranksters use a lot of tricks to make sure they can get on your nerves. Being able to trace prank calls is important because you're not going to learn much from your Caller ID, since most prank callers use ...more
Over the years, I have enjoyed playing with Asterisk. I have found Asterisk to be extremely powerful and fun to play with. There are several books and many scattered how to articles out there, but most are outdated and the information required to build Asterisk from beginning ...more
Whether it's the new iPad Killer or not, one thing's for sure—the Motorola XOOM is hackable. Just hours after its release last week, Verizon's new Android-based tablet (running Honeycomb) was rooted by hacker Koushik Dutta, which seems easy enough. "Since it’s another Google ...more
WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling. First, U.S. Senator Joe Lieberman swayed Amazon's decision to stop hosting WikiLeaks. Then, Tableau Software removed graphs from th ...more
The Kinect is sure to swarm the homes of Xbox 360 gamers this holiday season. Even though some of us are amazed at the hands-free gaming capabilities it offers, others feel it to be frustratingly limited. Adafruit Industries is one of them. They recently held a competition wi ...more
iChat is gaining steam as a mainstream online chat program. Fortunately for you, you little prankster, it is exceptionally easy to change someone else's iChat away message to whatever hilarious thing you want from your computer! This video will show you exactly how to do it, w ...more
ChickHen R2 is the most popular PSP hacking software out there, but getting it to work on the many different version of the system is tricky. This easy-to-follow video will show you how to install ChickHen R2 on any PSP with firmware version 5.03. This will allow you to play b ...more
Using infrared (IR) light pens and the Wii Remote, it is possible to create very low-cost multi-point interactive whiteboards and multi-point tablet displays. Johnny Chung Lee, Carnegie Mellon University. The software can be downloaded at http://johnnylee.net
Are you getting that nasty "Application access set to not allowed" error on your Nokia 5300 cell phone? Unfortunately, it's a problem for most Nokia 5300 owners, ones who wish to use 3rd party applications on certain carriers, like T-Mobile, who restricts the uses for branding ...more
Been hacked once? Twice? Maybe more? You thought abc123 was the only password that is both 6 characters wide and easy to remember? I have some suggestions in store for you. Just read on... An Introduction There are passwords that look tremendously sexy (as opposed to gibberi ...more
ios249 is a sweet little hack for the Wii that allows you to play backup burned copies of games on your console. Pirated games will work too, although we DO NOT condone piracy. This video will walk you through the whole rather elaborate process of installing it on a hacked Wii ...more
Flashing the disc drive on the XBox 360 is the first step of truly hacking your XBox 360, enabling it to run whatever discs you like but also putting you at risk for being banned from XBox Live. Microsoft has used several different kinds of drives in the console over the cours ...more
Hacking the PSP is a complicated process, and there has been some demand for a software tool that would make the process easier. This video has that solution. It explains how to use a program called PSPtool to create the magic memory stick and Pandora's battery much more easil ...more
If you move around a lot, you may notice that you can't play the same DVDs from country to country. The world is separated into different regions, and not all movies will play in all places. There are ways around this security measure, however, if you follow this tutorial. Th ...more
Get your dose of the coolest Adobe Lightroom tutorials, tips, time-saving shortcuts, photographic inspiration, and undocumented tricks with Matt Kloskowski from Photoshop User TV. Photoshop Lightroom is the leading photo management software solution. See what leading photograp ...more
Join the Pilot program and learn how to fly! But you're not going to be flying airplanes in this Pilot program, you'll be trying your hands at Google's first laptop computer. It's called the Cr-48, a black notebook wh ich runs an extraordinary operating system— Google Chrome. ...more
There are several different kinds of disc drives that come in different iterations of the XBox 360, and each one has to be hacked a little differently. This video will show you how to flash the ms28 drive used in some systems, the second part of the video will show you how to ...more
So you've watched this video, done your research, and decided that you want to flash the firmware on your XBox 360 with a LiteOn DG-16D2S rev. 7485 disc drive. Good for you! This video will walk you through the whole process. Be very careful, as messing up in small ways at any ...more
Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episode ...more
Some of you may stick with your iPads, but for those looking for a similar Android version, you finally have a winner. To master your new Motorola XOOM from Verizon Wireless, check out the product support page. There, you'll find interactive walkthroughs for getting started, ...more
General Electric isn't known for their Christmas lights, but maybe they should be, because their GE Color Effects are pretty awesome. Especially the LED Color Effects G-35 String sets. And especially when someone named Darco hacks them. Darco, whose real name is Robert Sun Qu ...more
It's 1976. The hottest arcade game on the market is Blockade (or Blokade), an 8-bit maze game for 2 players. You and your opponent must move your characters around the screen in 90-degree angles, leaving a solid line behind them. Whoever runs into one of the solid lines first, ...more
Your BIOS, or Basic Input Output System, is the firmware on your motherboard responsible for initializing your computer's hardware when it is first powered on. It probes for video adapters, RAM, the whole works. The BIOS provides a small library of basic input/output functions ...more
It's remarkable that a gaming device (from Microsoft, no less) designed for geeky gamers has incited broad innovation in medicine and robotics. But that Kinect has captured the imagination of hackers-with-MBAs-in-mind is downright amazing. Below, six videos demonstrating a va ...more
Do you own a hacked XBox 360? Do you want to burn some games for it? Well, in this video, the viewers will first be taught how to download games using peer-to-peer software, such as uTorrent. Then, with a combination of software, such as IMGBurn and abgx360, the viewers will l ...more
Hallelujah, a miracle tool has been released to the world. This Windows/Mac tool is called Spirit and it enables you to jailbreak any iPhone, iPod Touch or iPad quite easily. And Gizmodo is all over it, with an in-depth guide on exactly how to do it. Some of you may be hackin ...more
Your IP (Internet Protocol) address is your unique ID on the internet. It's synonymous with your home address. Anyone in the world can contact your computer through its IP address, and send a retrieve information with it. I'm sure at one time or another you've heard that hack ...more
Sparky is a wireless, web-based video-chat robot from the Gomi Style crew. You can learn how to make your own Autonomous Telepresence robot using spare computer parts, some old toys and a bit of custom software (that we provide at gomistyle.com). This robot is operated with a ...more
This is a terrible prank to pull on a friend. Destroy their iPhone software with a couple of quick hacks.
Cheers to another completed Community Byte project! Things went well regarding timeliness and being friendly to the other coders and students. If you've got ideas for our next mission, or an idea for a tutorial, submit them to me. Friday, our mission was to take out HackThisSi ...more
Six months ago, 1.3 million registered users of Gawker Media had their passwords compromised when the site was hacked by Gnosis. The passwords were encrypted, but 188,279 of them were decoded and made publicly available for all to see. Just three weeks ago, Sony Pictures was h ...more
Our hacked Kinect series has demonstrated amply how the Kinect is changing the worlds of business, art, medicine and robotics. But where does it go from here? That will be determined by the thousands of dedicated DIYers out there doing work like you've seen here over the last ...more
If you know anything about search engine optimization and online marketing then you know that having as many links going into your site from good sources is very important. And if you’re not really experienced at building links or SEO in general then you might not know the bes ...more
Do you want to hack your PS3? Are you tired of different videos sending you all over the place to find all of the necessary steps? Look no further. This three-part video offers detailed, step-by-step instructions for hacking your PSP, including making a Pandora's battery, a ma ...more
This is kind of scary! This video demonstrates just how easy it is to hack into an iPhone to access the data on it - including recovering deleted photos. You only think you've deleted those naughty photos you sent to your girlfriend.... Fortunately, there is a way... However, ...more
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to boot Wind ...more
Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and r ...more
Social engineering is described as the clever manipulation of the natural tendency of human trust. All of the passwords, locks, and encryption in the entire world are useless against a good social engineer who can charm or trick you into giving it up. But what once started as ...more
WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects. Thanks to all of our moderators and contrib ...more
Computer viruses are terrifying. They are undetectable, dangerous, and operate constantly right under your nose. For the average computer user, there are only a few repair options. You could buy expensive antivirus software that causes more problems than it fixes, you can wipe ...more
Ever since kernel 2.6.xx in Linux, a lot of the internet kernel modules for wireless interfaces ended up becoming broken when trying to use monitor mode. What happens commonly (to myself included) is a forced channel that your card sits on. No good! For users of airodump and t ...more
Security awareness seems to be a hot topic these days on the web, with developers making apps and devices that can hack networks and machines with just a few clicks. But these applications aren't only exploiting security flaws in systems and networks, they're being used by ama ...more
Okay, stop me if you've heard this one. You have a document that you want your co-workers' advice on. You attach said document onto a mass email. The first reply comes back with an edited version of the document. You begin to make changes, but another email comes in, with yet ...more
As a kid, my favorite thing to do at the Natural History museum was a midday stop, when my family strolled past an antiquated looking vending machine in the museum's musty basement. The Mold-A-Rama machine was oddly shaped, George Jetson-esque, and spewed out made-to-order, br ...more
This is a how-to –video on using hydra 5.4 to crack FTP passwords. This video is intended for educational purpose only. It reveals the basics of hacking a FTP server using dictionary search technique. Here are the steps involved. 1) Download the software hydra 5.4 form the ...more
Make your own custom characters for Icy Tower! It's as easy as drawing stick figures, believe it or not. Only stickman don't look as cool, unless of course it's a stickman that you want to use as your Icy Tower character. This wintery video tutorial teaches you how to make cu ...more
Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to extract W ...more
As many of you know Windows is not the most secure Operating System in the world, but then again no OS is really secure if the user doesn't know how to protect themselves. Later I will show you how to lower the risk even more on your (the user's) end. Well onto the real stuff ...more
The already robust and ingenious Nmap tool has received a whole slew of new scanning scripts that can be used to do all sorts of naughty endeavors. Notably, the SQLi module, since it is a necessary evil that we must cover here at Null Byte. This major update is going to fuel t ...more
This is the Windows OS counterpart to my tutorial on how to burn the new XDG3 formatted games on Xbox 360. Microsoft invented a new disc format system to trump piracy, it's called XDG3. XDG3's standard is to burn a whole extra gigabyte of data to the disc, to allow more conten ...more
It's been a long time coming, but Microsoft has finally released a software development kit (SDK) for the Kinect on Windows 7 PCs. The word "hacking" is no longer needed, thanks to the free beta download available at Microsoft Research that allows anyone with a Windows compute ...more
Video games and art have somewhat of a sticky relationship. Many video games have large teams of talented artists doing amazingly creative work, and yet the art community is only just beginning to utilize video games as art (sometimes). Perhaps if video games were shown not ju ...more
This might be so '2 weeks ago' but I've been away, oh well. In a few short words: The PS3 has finally been hacked via a USB device! Sure it can be possibly used for piracy, but let's not go into that topic. Instead read this nice intro into what an open PS3 can do for you (v ...more
Lifehacker posts an article on the art of cracking weak passwords, courtesy of Internet standards expert, CEO of web company iFusion Labs, and blogger John Pozadzides. Pozadzides certainly knows a thing or two about password logic. (Note: this information is not intended to ha ...more
http://www.texturemind.com/post463/ TypingRobot is an artificial intelligence studied to increase your points record with the Typing Maniac game on Facebook. It can recognize several labels because it uses a powerfull OCR system (tesseract) and some principle of word correcti ...more
There is a vast amount of knowledge out there on computers! In fact, it is so vast that no single person could ever possibly ever learn everything there is to learn about hacking or computers in general. People usually specialize in a certain field: cryptography, computer secu ...more