If you've ever traveled to a country where you do not speak the language, you know there are times you need to translate text. Or maybe you just ordered a foreign good that requires text translation. Google Translate can easily solve this with its camera translation feature. I ...more
While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. ...more
There are plenty of reasons the Pixel's Google Camera has become a must-have app for Android users. Google Playground AR stickers and Night Sight for low light photography are just the tip of the iceberg. Beyond those, the app comes with other, less-publicized options that add ...more
For me, there's nothing better than popping on a favorite show or new movie after a long day at the office — except when there's a friend or two I can talk to about that crazy ending. Netflix doesn't double as a social media app, so you can't chat about what you're watching th ...more
When Apple released its Downtime feature in iOS 12, it gave us an easy way to control how much time we spend on our iPhones — but it wasn't perfect. When setting Downtime, you' were forced to use the same time schedule for every day of the week, so your weekdays and weekends h ...more
While many of Facebook's tools are well received as they enhance the experience, one which is often complained about is the Marketplace. The Craigslist-like feature which offers a way to facilitate transactions between users can be a little overbearing with its alerts. However ...more
Whether it's an ex you can't stand, that annoyingly political friend of a friend, or good old fashioned trolls, the block feature on Facebook can be a great way to de-stress your feed. It will keep people from contacting you, and it will also prevent them from viewing your pro ...more
Instagram introduced a new feature in September 2018 that lets you share other users' Stories via Instagram Direct, the app's private messaging tool for solo and group messages. Problem is, it works both ways, so whenever you add to your ephemeral Story, everybody that sees it ...more
In this jam-packed October, the Huawei Mate 20 Pro has flown under the radar in the US. Due to Huawei's lack of presence in the States, many are unfamiliar with the second largest OEM in the world. Huawei has continuously put out amazing mobile devices, and this year they rele ...more
For some, the Galaxy Note 9's volume rocker doesn't have enough steps between silent and max volume. We all have different preferences for volume, and a higher number of steps would equal to more precise volume control. Good thing we can at least adjust this for the media volu ...more
The iPhone XR has touched down alongside the XS and XS Max, and it utilizes tried and tested materials found on the iPhone 8, while being molded in the same vein as the iPhone X. The budget-friendlier flagship comes with its own set of design elements to set it apart from its ...more
Starting November 1, 2018, Google will require that all new apps and updates to existing apps target Android 8.0 Oreo or higher. This move means the developers behind many of your favorite apps are now scrambling to get their software modernized, while others are considering a ...more
Maybe you prefer writing passwords in a notebook. Maybe you like creating your passwords yourself. Whatever the case, you don't like iOS 12's new automatic password generator, and you don't need it to pop up every time you enter a new password in Safari or a third-party app. L ...more
Google Photos integrates with Google's ecosystem to bring you awesome features like the ability to identify landmarks, track down products you've photographed, and so much more. Now, if you need to translate foreign words in any of your pictures, the app has you covered as wel ...more
The updates just keep on coming. Apple released the third beta for iOS 12 to public testers Wednesday, July 18, just after seeding the fourth iOS 12 developer beta to registered developers the previous day. This update comes thirteen days after the release of the second public ...more
One of the best parts of the BlackBerry KEYone and KEY2 is the iconic physical keyboard. There is one major downside, though: By default, the virtual keyboard appears on these devices even when typing on the physical keyboard. Luckily, there's a way to change that. By removin ...more
One of the best features in the Apple News app is the ability to save stories for later. If you see an interesting or important article but don't have time to read it right away, there's a good chance you'll never find it again unless you save it. Ever since News' birth in iOS ...more
While certainly faster than writing by hand, manually typing passages from a book or document can be slow and frustrating. But thanks to Google Assistant, this is no longer the case. Whether you need to quote text for an essay or need to win an online argument, all you need to ...more
It seems Apple has followed through on their promise. After the disastrous battery slowdown scandal in December, the iPhone maker has finally pushed new battery health information and controls to iOS 11.3. Now, if you have an affected battery, you can disable performance throt ...more
Apple released an iOS 11.2.2 update on Monday to iPads, iPhones, and iPod touches. The update comes as no surprise since news broke last week of a massive security vulnerabilities, named Meltdown and Spectre, which are found in smartphone chips throughout the industry. This up ...more
Hashtags are the backbone of Instagram. They connect photos from users all around the world and give visibility to users who don't have many followers. Now, Instagram has added more functionality to this indispensable tool, and this new feature lets you follow hashtags in your ...more
Just yesterday, Google announced that it is banning all apps that contain any form of lock screen ads. Today, they posted a list of the Best Apps of 2017 for the Play Store. Given the new policy of cracking down on apps with advertisements on the lock screen, you wouldn't expe ...more
So, your grandmother finally wants to ditch her flip phone for a shiny new smartphone? Congratulations. But helping her get used to her new device, even when it's an iPhone, is no small task. Grandma mastered checking her email in late-2012 and just recently learned there's a ...more
When you first use Kodi, it can be intimidating. The main menu has numerous options for the various types of media Kodi can play back, and the settings menu has a broad array of tools to customize Kodi to your needs. After poking around in theses menus, you might realize that ...more
Every now and then, an iPhone will freeze up and become unresponsive due to a software glitch. It can be a buggy app that somehow interferes with iOS or a software update that somehow didn't install properly. Whatever the cause, it's safe to say that no iPhone is immune to thi ...more
Crossfades are a great way to get from one scene to another. They bridge the gap between two video clips in a fresh, fun way. But can you even use this transition in a smartphone editor? You bet you can, and it's extremely easy. Adobe Premiere Clip, available for Android or i ...more
Snapchat is rolling out some awesome new features in their update today. The major update comes just two weeks after the company's premiere of backdrop, snap shopping, and voice clip features. They rolled out two new features this time, Multi-Snaps and the Tint Brush. The fir ...more
As we all know, and certainly have marked on our calendars, it's World Emoji Day! Considering that over five billion emojis are sent daily on Facebook Messenger alone, emojis deserve to be celebrated, and Apple's doing just that. On this monumentous day, the tech giant is gift ...more
Instagram Stories is one of the most flexible ways to share creative and original content with your followers. It allows you to alter text, markup images, and add cool graphics and stickers, along with other fun ways of expressing yourself. The way you can use Stories goes be ...more
A fairly hidden feature in iOS 10 let you turn websites and documents into PDFs, but thanks to the new Markup function in iOS 11, this process has become a lot more streamlined. Not only can you save webpages, notes, and other files as PDFs for easy sharing, but iOS 11 even l ...more
Update: Twitter user Benjamin Geskin (@VenyaGeskin1), known for his iPhone renders, tweeted on Monday alleging that the leaks are fake: This is glass made by Shenzhen manufacturers of protective glass. Fake. Not real iPhone parts. (But look is close to reality) — @VenyaGesk ...more
The Instagram Explore page is one of the most useful tools available to users. It's also one of the easiest ways to discover new content and, if you use it right, to increase your own follower count. There are a couple ways for you to dominate the Explore page. One way is to ...more
Though its necessity is less frequent compared to Android devices, iPhones still need to be shut down from time to time. Whether it's to help correct a buggy app, prevent overheating on a hot day, or conserve battery life in a pinch, the power button on any device is an indisp ...more
Replacing your iPhone fingerprint sensor has been one of Apple's most cruel tortures. It's a slow and painful process made worse last year when Error 53 messages started appearing on the phones of users who had tried to repair their sensors outside of Apple. The error rendered ...more
Snapchat hit back at its arch-rival Facebook this week with a number of new Group features, including custom stories. Facebook and Instagram both rolled out clone Story options this year, but Snapchat is obviously trying to up the ante in this arena. Snapchat's latest feature ...more
Depending on your device, when you lower your brightness slider all the way to the minimum, it may still emit a considerable amount of light. This is because manufacturers have the option of setting a minimum brightness value, and while 1 would be the true minimum brightness t ...more
There's nothing worse than driving up to your destination only to discover that there isn't a parking spot in sight — but thankfully, Google Maps will soon have you covered. Android Police reports that the latest beta version of Maps V9.5 will incorporate a number of handy to ...more
Reddit user Mr. Squishy recreated the entire Game Boy Pokémon Red Version game in Vanilla Minecraft, i.e., a Minecraft server without gameplay modifications. Instead of using mods, he used 357,000 commands blocks—blocks that execute commands in the popular sandbox game. How lo ...more
Here's another workday distraction for all you social media lovers out there: Pasted, launching out of beta today on iOS, is a simple collage and photo editing app mixing iconic '90s imagery with a love of the The Shins. Founded by Zeke Howard and Ben Fogarty of Spruced LLC, ...more
Dreaded are the days when you're working on a masterpiece, then all of a sudden, your Windows computer crashes, loses power, or an app just gets up and quits. Well, now there's an app for that. According to MakeUseOf, with an app called AutoSaver, you can automatically save t ...more
Facebook Messenger has now incorporated a live location sharing feature, one week after Google Maps revealed its own real-time location tool. On Monday, the social media giant announced the new feature, which will allow users to share their live whereabouts with friends at the ...more
Earlier last week, there were a number of fake five-star WhatsApp reviews to be found on the Google Play Store. Now, Gmail, Chrome, Messenger, and Firefox are all the latest victims to be saturated in five-star spam that wrongly refers to the word "game" in reference to non-ga ...more
During the last few months, WhatsApp's Google Play Store ratings have been tanking—all the way down to an average of 3.4 stars from the instant messenger's usual average of 4.1. Within the last week, though, WhatsApp has received thousands of seemingly fake 5-star reviews that ...more
Android 7.0 Nougat brought a lot of multitasking improvements along with it, but the most notable addition is a unified multi-window mode (which shines bright in Google's Pixel phones). This means that every Android device can now use the same split-screen interface, and the d ...more
It's no surprise that the Microsoft Kinect can provide far better motion tracking than the HoloLens currently can on its own, but at least one developer didn't want to wait for the company's own eventual implementation. Kyle G, founder and CEO of Wavelength Studios, projected ...more
Tender is the name of the game when it comes to cooking damn delicious meat, but achieving that succulent texture isn't always easy. Thanks to the folks over at Cook's Illustrated, though, we now know there's a simple, foolproof trick to take when tackling meat tenderness... ...more
We're all for heaping piles of shredded cheese on our tacos, but what if all that cheese could actually be the taco shell instead? Since this was perhaps one of the more profound food questions we've had in a while, we wasted no time getting to the kitchen and tackling this ch ...more
Pitting cherries is really annoying. There's no neat way to do it with a knife and, though they make a tool that does it, not everyone has space in their kitchen for a gadget that does so little. But fresh cherries are so delicious when they're in season... it's almost worth t ...more
Even for an avid egg enthusiast, a popular dish like scrambled eggs can get tiresome if it's on repeat in your breakfast rotation. For an unusual way to add some oomph to your œufs, consider adding a squeeze of lemon to your scramble. Read on to understand why this seemingly o ...more
You're better than a can of Reddi-wip, which is why you should always make fresh whipped cream at home. It's extremely easy to make, won't have all those nasty preservatives, is thicker and creamier in consistency (like cream should be), and tastes much richer. Don't Miss: 4 ...more
The biggest problem with plastic wrap is also its most useful trait: its incredibly clingy nature. Plastic wrap seems to stick to itself or you before you can get it over the plate, bowl, or food you're trying to preserve. And once you do manage to get it in the right position ...more
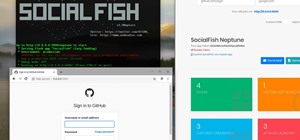
Since Ive started to learn about nmap and metasploit and other tools I was learning well but I had one problem, I had nothing to practice it on. As a result I asked someone about my problem and they told me about Vulnhub. It's a great way to practice. Its good beginners and pe ...more
By default, the Play Store app on Android is set to automatically update your apps in the background. This definitely makes it easy to ensure that you're always running the latest versions, but it does come with some downsides. For instance, apps will occasionally have update ...more
I don't know about you, but when I shoot a slow-mo video on my iPhone, I'd also like to have a regular speed copy of it, just in case slow motion doesn't fit the video right. Traditionally, converting slow-motion video required manually speeding the video back up in editing a ...more
Samsung makes some wonderful phones, but one thing I've noticed is that battery life can start to degrade over time, causing the phone to die a lot faster than it used to. If you've been experiencing this issue, and have asked yourself, "Why does my Galaxy S5 die so fast?" the ...more
Five Phases of Hacking:- The five phases of Hacking are as follow: Reconnaissance Scanning Gaining Access Maintaining Access Covering Tracks The Five Phases of Hacking Reconnaissance:- This is the primary phase where the Hacker tries to collect as much information as possib ...more
Before we dive into the world of frustration, I first would like to thank whoever of the admins and mods made the folder for Raspberry Pi in the How-To's, thank you. Now with that outta the way, this article is about Metasploit on Raspberry Pi (hence the title). I should say t ...more
Most people are familiar with the fact that vinegar adds sourness to a dish, in varying degrees from light acidity to puckering acid. However, vinegar can also be used in lieu of salt when seasoning the final touches to sauces, soups, and stews. Hold the Salt—Are You Nuts? I ...more
Hello, my fellow hackers. My name is cl0ck. I am a senior majoring in Computer Engineering with an emphasis is Security. I have been lurking the site for a while now reading and learning from the great minds that reside here. I, too, have some knowledge that I would like to s ...more
Google Maps, in conjunction with the Android operating system, is a powerful tool for navigation that is often underutilized. While it's no secret that it can get you to wherever you're going and back, some of you might not know that you can use Google Maps without even having ...more