This video tutorial shows you how to use a free program to customize the HTC Home plug-in for Windows Mobile touchscreen devices. You can use any Windows Mobile cell phone or other device for this hack. YOu can run applications like Streaming Media on your HTC Home site from y ...more
Tired of touch-tone hell? Get human with our cool phone hacks and cheats with the tips from this how-to video. Become a life hacker - we'll show you how to find phone numbers, cheat the computer and hack the call center system with our hacking tools. Watch this video tutorial ...more
Thanks to the advances in technology, never get out of touch with the internet. Most mobile phones, like the Palm Centro, have web-surfing capabilities. Watch this video cell phone tutorial and learn how to connect to the internet anytime, anywhere with a Palm Centro. Connect ...more
Want to stay up to date with the emails in your inbox? Most mobile phones, like the Samsung Instinct, have an email feature and internet capability to keep you connected. Watch this video cell phone tutorial and learn how to send and receive email on a Samsung Instinct. Check ...more
Directions are simple to get from the built-in navigator in a Samsung Instinct mobile phone. Never get lost again, as long as you've got a fancy phone on you. Watch this video cell phone tutorial and learn how to get directions from the GPS, global positioning system, navigati ...more
Capture photographs on the go, as long as you've got your mobile phone with you. Take pictures, send them via email, or upload them to your favorite social networking site. Watch this video cell phone tutorial and learn how to use the camera on a Samsung Instinct. Take picture ...more
Mobile phones these days keep you connected anytime, anywhere. The Samsung Instinct is no exception, as it comes fully equipped with web-browsing on the go. Watch this video cell phone tutorial and learn how to connect to the internet on a Samsung Instinct. Connect to the inte ...more
Bluetooth devices hook up a mobile phone to a computer, headseat, or even a car. Every LG Rumor comes equipped with Bluetooth capabilities. Watch this video cell phone tutorial and learn how to use a Bluetooth device on an LG Rumor. Use the Bluetooth device on an LG Rumor cell ...more
Test messages are a fast, discreet way to keep connected on a mobile phone. Sending SMS messages on an LG Rumor are easy with a QWERTY keyboard and predictive text. Watch this video cell phone tutorial and learn how to send an SMS text message on an LG Rumor. Send messages on ...more
Upload up to 4000 songs from a computer onto an LG Rumor cell phone. No need to get a separate mp3 player or iPod as long as you've got your mobile phone. Watch this video cell phone tutorial and learn how to listen to music on an LG Rumor. Listen to music on an LG Rumor cell ...more
Surf the web, regardless of the weather or where you are. Your LG Rumor cell phone comes internet capable and ready. Watch this video cell phone tutorial and learn how to use an internet browser on an LG Rumor. Use the web on an LG Rumor cell phone. Click through to watch this ...more
Maybe you've never seen a mobile phone before, or the touch screen on the Samsung Instinct is freaking you out. Whatever the reason that you're finding yourself unable to even make a simple call, this how-to video has got you covered. Watch this video cell phone tutorial and l ...more
Sometimes you can't just pick up that mobile phone. Text messages keep you connected without making a sound, and are as quick as the flick of your fingers. Watch this video cell phone tutorial and learn how to send and receive SMS text messages on a Samsung Instinct. Send and ...more
The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized ...more
A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists righ ...more
If you have a smartphone with a good camera, chances are you don't think it's good enough. There's always something that can better with your mobile pics, and for me, that something is closeup shots. I love macrophotography. The finer things in life excite me, finer meaning t ...more
Attention folks—the Samsung Galaxy S4 is coming soon to a cellular provider near you. Though the official release date for the GS4 here in the states has been closely guarded, a recent leak from a Staples store training document has revealed some possible days that the GS4 cou ...more
Hello my fellow hackers, it's been a while since my last post, I can't get the time now-a-days for the posts but can manage to tend to comments. Welcome to my 9th post, this tutorial will explain how to extract and decrypt WhatsApp database from the Victim's android system. ...more
Former Google employee Tristan Harris claims there's an easy way to combat phone addiction without installing any new software. By enabling grayscale on your phone, checking your apps and notifications will be less appealing and thus stop you from obsessively checking your pho ...more
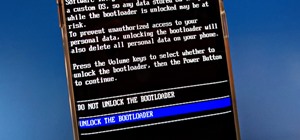
A landmark bill finally went into action this week that will allow American cellular customers to unlock their smartphones for free. The process of unlocking may vary between mobile service providers, but you can rest assured that you are now entitled, by law, to carrier-unloc ...more
A few days ago, Russian hacker Alexy Borodin found a way to get free in-app purchases on an iPhone or iPad. In-app purchases include things like items and power-ups for iOS games, as well as subscriptions and "premium" memberships for certain apps. The method is novel, not fo ...more
You will likely have a 5G-capable phone within two years. Each carrier is working hard to improve its coverage for the next standard in mobile networks, and though the technology is fairly new and only a handful of phones support it right now, this will change very soon. Curr ...more
Chrysaor, a zero-day spyware believed to have been created by the Israeli "cyber war" group NSO, is an even greater threat to Android phones than it ever was to iOS. Related to the Pegasus hack that recently affected iPhones, Chrysaor is malware that baits the user into insta ...more
This year, like every year before it, Black Friday sales are starting earlier than ever. A lot of stores will be opening their doors as early as 5pm on Thanksgiving to get a head start on the madness (and it really is madness). As we've discussed in the past, one of the keys t ...more
While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of i ...more
Security researcher Ravi Borgaonkar from Berlin has discovered that hackers can hide an 11-digit code in a webpage that can wipe out all of the information on your smartphone—contacts, photographs, music, applications, and anything else of importance. The attack takes no more ...more
If you don't smoke, your car's ashtray is probably either unused or, if you're like me, full of loose change. And if your car is older, unless you've installed one, it probably doesn't have a place for you to plug in your phone. This quick hack by Jalopnik's Jason Torchinsky w ...more
WhatsApp is a very popular messaging app on the Play Store, but unfortunately, tablet users have been left out of all the fun because WhatsApp only works on smartphones—until now. Tech wiz James Nakata wrote up a short guide over in our forum for porting WhatsApp onto a Nexus ...more
If you had a phone in 2004, there's a pretty good chance it was a Motorola RAZR. The iconic phone is the tenth highest-selling of all time, and it marked the height of the flip phone era. Now that the technology has caught up, Lenovo (Motorola's parent company) is bringing it ...more
Many people deal with motion sickness on a daily basis, and if you're reading this, chances are you're one of them. Kinetosis can make your stomach roll, your entire body sweat, and make you feel fatigued and dizzy at even the slightest movement, whether it's related to carsic ...more
With new iPhone models out, you'll have updated cameras to try out, a faster processor, and new colors to choose from. The only thing that could stop you from picking one up yourself is, well, your current iPhone. Here's how to check if you're eligible to upgrade to iPhone 11, ...more
I have the AT&T version of the Galaxy S5, so every time I start my phone I get the pleasure of hearing AT&T's lovely jingle. Actually, that's sarcasm—I absolutely abhor this sound. I haven't had the chance to play around with a Sprint, T-Mobile, or Verizon variants of this pho ...more
Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elli ...more
This week, California, like a growing portion of America is now 'handsfree'. As of July 1st, mobile phone use in cars became prohibited without the use of a headset. If you happen to choose a wireless Bluetooth over a wired option...beware. It is not a secure technology. At a ...more
It's a given that if you're driving, you or someone you know has Waze as a go-to on their smartphone. The Google-owned crowdsourced navigation app is one of the best for avoiding traffic, roadblocks, and even cops. But a new academic study and report from Fusion suggest that ...more
Hi guys, this is going to be kinda like a follow up to my previous post on hacking facebook with the remote keylogger. If you haven't seen that post I suggest you do. So like you can click here. Anyway let's move on. Even though people are the weakest form of security, some o ...more
Researchers at the University of California, Riverside and the University of Michigan announced recently that they have developed a hack that works 92% of the time on Google's Gmail system on Android, as well as with the H&R Block app. In addition, this hack worked 86% of the ...more
Samsung's Galaxy Note 4 is a beautiful device worthy of all the critical acclaim it has received thus far. But aside from the S Pen features, most of the Note's user interface has a great deal of overlap with the Galaxy S5 that we all know and love. So it's not an entirely fo ...more
The iPhone 5 will be here in no time. Pre-orders started at 12:01AM PST this morning and it's expected to start shipping in about two weeks. Verizon, AT&T, and Sprint are all handling unlimited data plans differently, so if you currently have an unlimited plan and are going to ...more
The OnePlus 5T was just released, and it's packing several new useful features. While many OnePlus 5 buyers are feeling frustrated with the quick release cycle, lots of fans are still clamoring to buy the new device. Aside from the larger screen, most of the buzz around the 5T ...more
Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account ...more
When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you ...more
LG's new KnockOn feature for the G2 wakes the phone up just by tapping on the screen twice, in lieu of using the power/lock button. This is something that would be equally as helpful on the HTC One, as it's sometimes a pain to use the power button, especially if it's worn out ...more
Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us. In this episode, Elliot is being blackmailed by the ru ...more
If you have seen the movie Fast and Furious 7, you know what "God's Eye" is. Well this might spark interest to you. If You Don't Know if you don't know what God's Eye is, basically it's a software that is able to access any phone, camera, microphone, anything that is digital ...more
In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux. With each Pi more powerful and cheaper than the last, the addition of the Pi Zero in 2015 too ...more
It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or ...more
When the Nexus 5 debuted, one of its coolest features was the fact that you could say "OK Google" any time you were on the home screen to launch a Google Voice Search. This feature was ultimately made available for other devices by way of the Google Now Launcher. Recently, Go ...more
It can be incredibly frustrating to take closeup shots with an iPhone camera—or any smartphone camera for that matter. Even if your phone's camera is top of the line, you'll still get a fuzzy picture if you get to close to your subject. To resolve this, you could always purch ...more
Apple is notoriously cryptic when it comes to the reveals of its new products, and as usual, they've kept us guessing about the release of the iPhone 5 (or "New iPhone?"). It's expected to be officially revealed on September 12, and rumor has it that sales will begin on the 21 ...more
If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs ...more
At $349, you won't find many smartphones that provide a better deal than the Google Pixel 4a. It has flagship-level performance, a headphone jack, and one of the best smartphone cameras on the market, all for less than $400. But if you act now, you can save even more. At Best ...more
Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in secur ...more
The integration of technology into automobiles is becoming more and more widespread each year. Tesla's Model S features a 17" display in the middle of the dash with navigation, music control, and even an Internet browser. Mercedes is working on incorporating Google Glass into ...more
Back in 2010, iOS developer Daniel Amitay developed a camera security app for iPhones that used an unlock screen almost identical to that of the iPhone. The app was removed in mid-2011 (though, it eventually reappeared in early-2013, still available in the iOS App Store today ...more
As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing ma ...more
With ultra competitive games like Fortnite Battle Royale and PUBG taking the mobile world by storm, gamers are looking for ways to get a leg up on the competition. One of the biggest advantages you can give yourself is the ability to aim and shoot while on the move, but that's ...more
Sorry, Galaxys S11–19, Samsung's jumping straight to Galaxy S20 this year. They're also going with essentially three base models before accounting for niche variants. Of these three models, it's clear which one's the best: the Galaxy S20 Ultra. We've rounded up all the specs ...more
RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices. I initially covered RouterSploit on Kali Linux and macOS (OS X), but this tuto ...more
PRL, or Preferred Roaming List, basically tells your phone which towers to connect to first. Changing PRLs can improve reception and data speeds, and in some cases even give you access to corporate/test towers. Because PRLs only operate on CDMA networks, this method only appl ...more